Unprivileged users can export other user profiles
-
I need to allow pfSense users being able to download their own OpenVPN profiles. No access to other webConfigurator areas.
- I've configured user access as shown below:
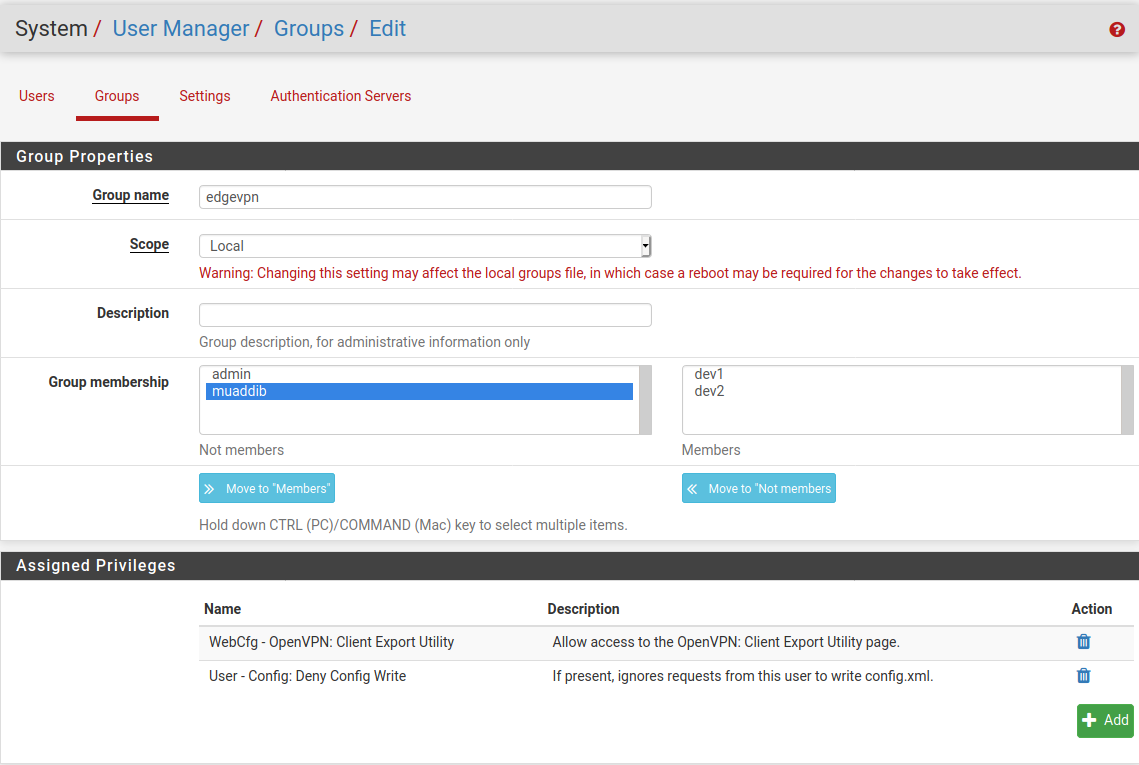
- VPN users can login into webConfigurator, unable to to change export page settings but able to see and download other users VPN profiles.
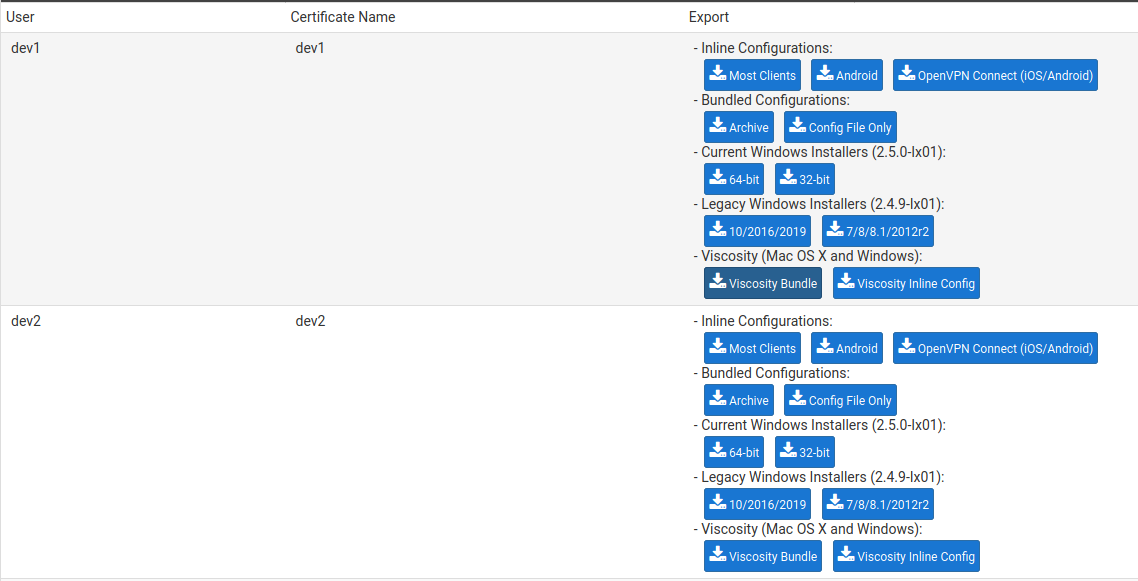
I think it's a serious security issue - non-admin users should not be able to download other user's VPN profiles. I believe it's a very simple change in the webConfigurator code, since profile filtering mechanism is already present on the page.
-
@capitanblack said in Unprivileged users can export other user profiles:
I think it's a serious security issue - non-admin users should
Isn't the one level higher : non-pfSense admins have access to pfSense ?
If a password for a VPN access needs to be changed, what about :
Change it on pfSense and communicate it using a save channel to the VPN user, as there is no need to send over a new opvn config.
Does that happen a lot : a user wants to change its password on it's own initiative ?
Mine do not have that need ...Btw : password s ? And what about the far more secured cert access ? Access to the cert list and generation too ?
I understand that you want a VPN-Client-Export page accessible, so that users can download their own VPN stuff from pfSense.
The client-export package was (probably) written with an 'admin only' access in mind. Not as being part of a multi user system. -
@gertjan said in Unprivileged users can export other user profiles:
@capitanblack said in Unprivileged users can export other user profiles:
I think it's a serious security issue - non-admin users should
Isn't the one level higher : non-pfSense admins have access to pfSense ?
Yes, but only to download their VPN profiles and maybe changing their passwords.
I say maybe because I'm implementing AAA system and pfSense VPN server will be using an LDAP database for authenticating. Password change will be done via an internal Web site not pfSense. So, pfSense-based password changing for VPN user is not a critical, but "nice to have" feature for us.If a password for a VPN access needs to be changed, what about :
Change it on pfSense and communicate it using a save channel to the VPN user, as there is no need to send over a new opvn config.
I believe pfSense webConfigurator is safe and secure enough to let people download their VPN profiles.Does that happen a lot : a user wants to change its password on it's own initiative ?
No very often but it might happen if user thinks that password might be compromised. In a properly designed network environment, admins shouldn't handle anyone's passwords. Users must be able to change them directly whenever it's is necessary.Btw : password s ? And what about the far more secured cert access ? Access to the cert list and generation too ?
We use Remote Access (SSL/TLS plus User Auth) OpenVPN server mode.I understand that you want a VPN-Client-Export page accessible, so that users can download their own VPN stuff from pfSense.
The client-export package was (probably) written with an 'admin only' access in mind. Not as being part of a multi user system.I agree but that's wrong. pfSense is a very universal tool and some of its parts might require a non-privileged access.
-
What you are attempting is not supported and won't be supported. It's an insecure practice that downgrades security for users. See many previous discussions on the topic on the forum and elsewhere.
-
@jimp said in Unprivileged users can export other user profiles:
What you are attempting is not supported and won't be supported. It's an insecure practice that downgrades security for users. See many previous discussions on the topic on the forum and elsewhere.
As a matter of fact what I'm attempting is ALREADY supported - i.e. users can login and download their own OpenVPN profiles. I only asked to make the profiles export page page a bit more secure.
No problem - I'll make my own patch.
-
What you are attempting to lock users into downloading their own profiles only, which is not supported. Demonstrably. Or you wouldn't be posting.
You can make your own patch, sure, but it won't be secure. It's an awful practice. Your VPN is only as secure as your weakest link, and allowing users to download the VPN config using only their username/password nullifies any other security factors you have configured (TLS keys, certificates, etc).