Allowing only specific DNS server through firewall
-
Hi all,
I wrote a longer post regarding my goals, but my firewalling question was embedded in a question about the cron package, which means it might have wound up in the wrong section to get a good answer from firewalling experts, so I figured I'd try again here.
I have one VLAN on my network (using interface ix1.5) which I am trying to do some DNS based family filtering on.
I decided to try the free OpenDNS family Shield DNS servers (208.67.222.123, 208.67.220.123). I added them to the DNS list in the DHCP server configuration for just that VLAN:
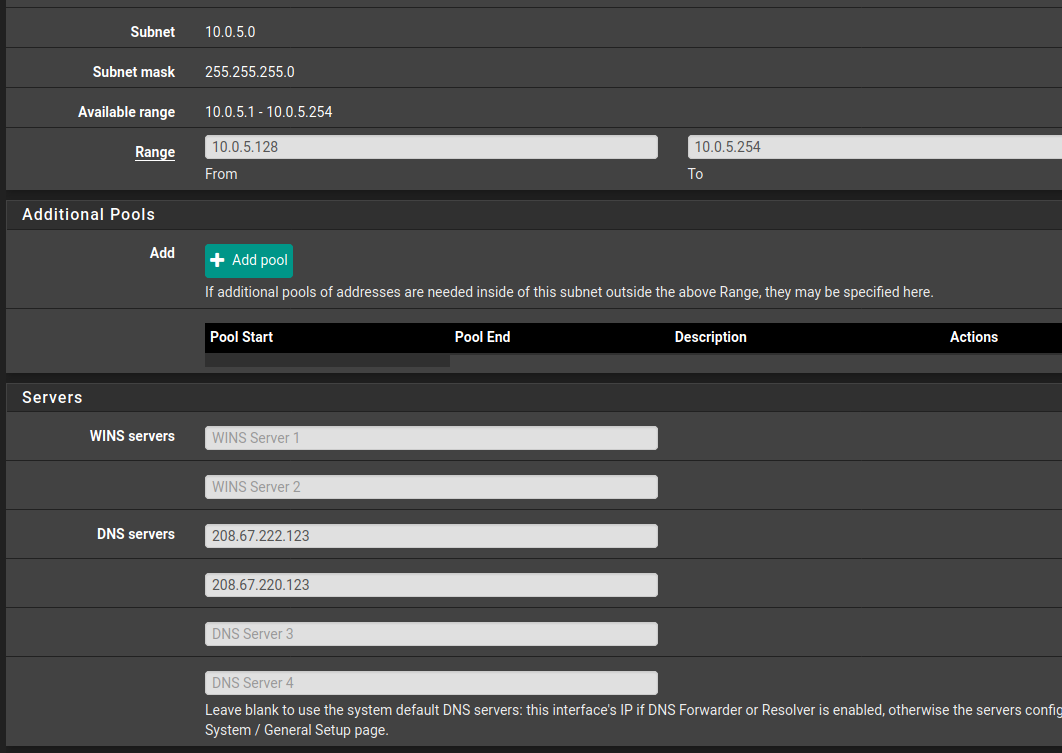
This works beautifully. Devices on that specific VLAN that pull an IP via DHCP show the correct thwo DNS servers locally and use the DNS filter as intended.
There is nothing to stop it from being circumvented by changing the DNS server though. I tried to fix this by adding a few firewall rules, first one each that explicitly allow the above two IP addresses on port 53 (DNS) then one directly below those that blocks ALL port 53 attempts, as screen capped below:
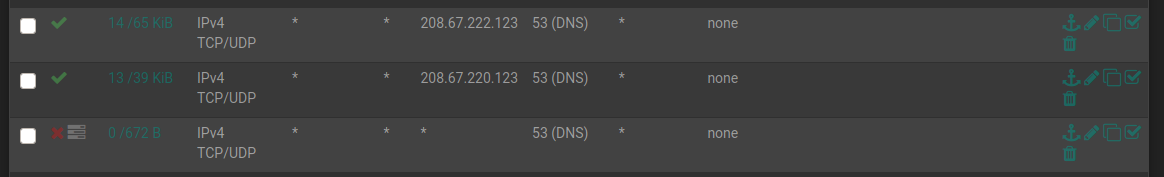
This - however - did not work. After adding these three rules, making sure they were in the correct order, saving and refreshing rules, the VLAN promptly lost all access to DNS.
So, something is wrong with my firewall rules.
I'd appreciate any suggestions on what I might try to get this working as intended.
Thanks,
Matt -
@mattlach
Obviously these pass rules have already handled some traffic as the states and bytes counter are showing.
Do you also have other rules in place to allow upstream traffic? -
@viragomann said in Allowing only specific DNS server through firewall:
@mattlach
Obviously these pass rules have already handled some traffic as the states and bytes counter are showing.
Do you also have other rules in place to allow upstream traffic?I appreciate the reply!
Hmm.
When you say "upstream" where would they be?
The subnet for this network is 10.0.5.0/24 with a gateway at 10.0.5.1.
The only other upstream place I think they could be would be on the WAN interface.
Do DNS servers typically need to be explicitly allowed on the WAN? I don't think I've ever had to do that before.
The only real rules on my WAN interface are the standard ones (block Bogon and Private networks) and a few port forwards for my server.
Appreciate your thoughts.
-
@mattlach
No, on exactly the same interface you need additional pass rule to allow any traffic apart from DNS, like HTTP. -
@viragomann said in Allowing only specific DNS server through firewall:
@mattlach
No, on exactly the same interface you need additional pass rule to allow any traffic apart from DNS, like HTTP.Oh, OK. Thank you I understand what you mean now.
Here is the whole shebang for this network in it's current working state:
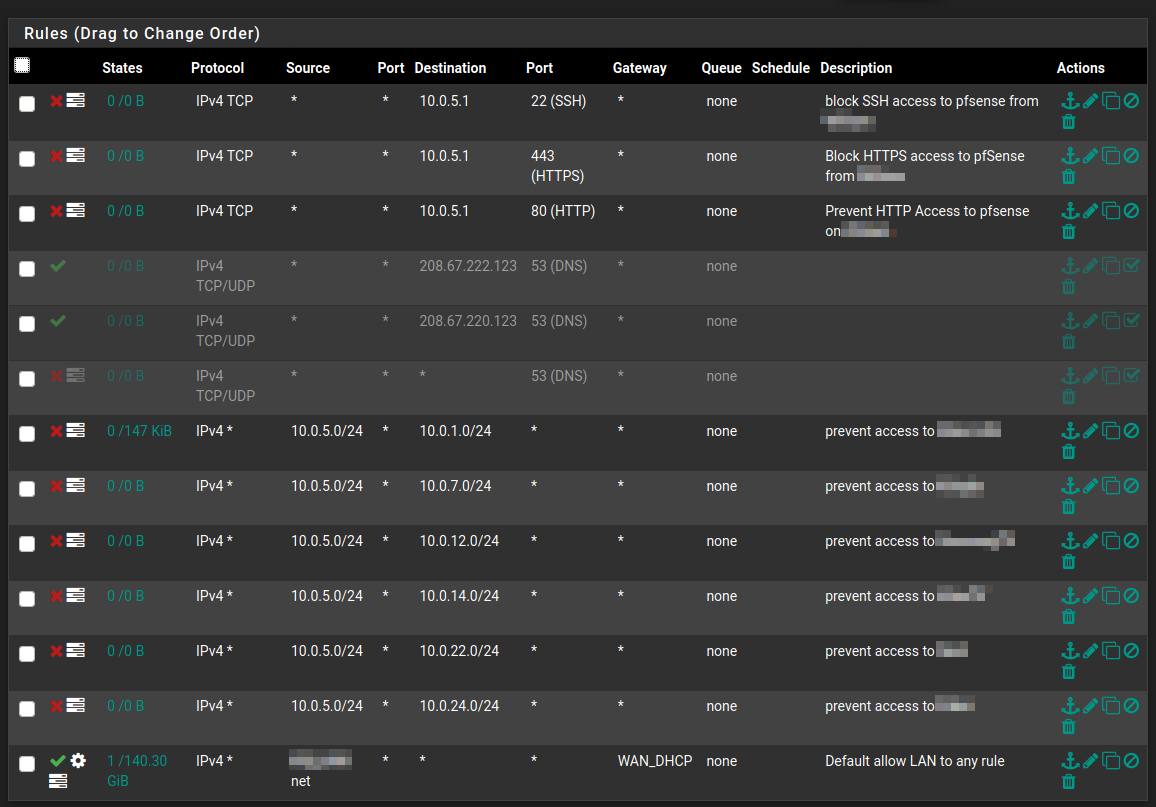
What you are looking at here us first three rules blocking this network from logging on to pfsense via http, https or ssh.
Nerxt are the three rules that cause trouble, currently disabled, so things are working. First the rules that allow access on port 53 to the two specific IP addresses, followed by the rule that blocks all other requests via port 53.
Next are six rules that block access to all of the other Subnets on their separate VLAN's, and last is the default allow any rule.
So, as mentioned, in its current state it works, the local clients are using the desired DNS and have their content filtered, but there is nothing to prevent the change of DNS server on the local machine to circumvent the content filtering.
As soon as I enable those three greyed out rules, the network loses all DNS. I can still ping outside IP addresses on the internet, but without DNS I can't really do anything.
Each of the two "Allow" rules look as follows:
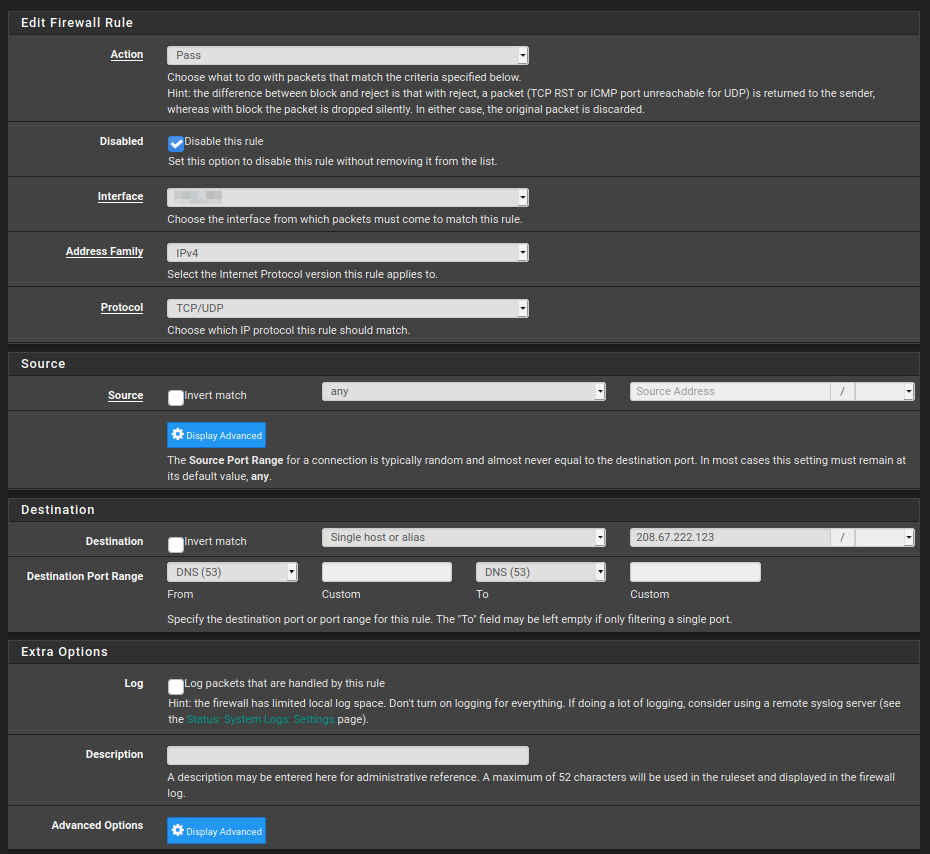
The only difference between them is the target IP address.
The block rule looks like this.
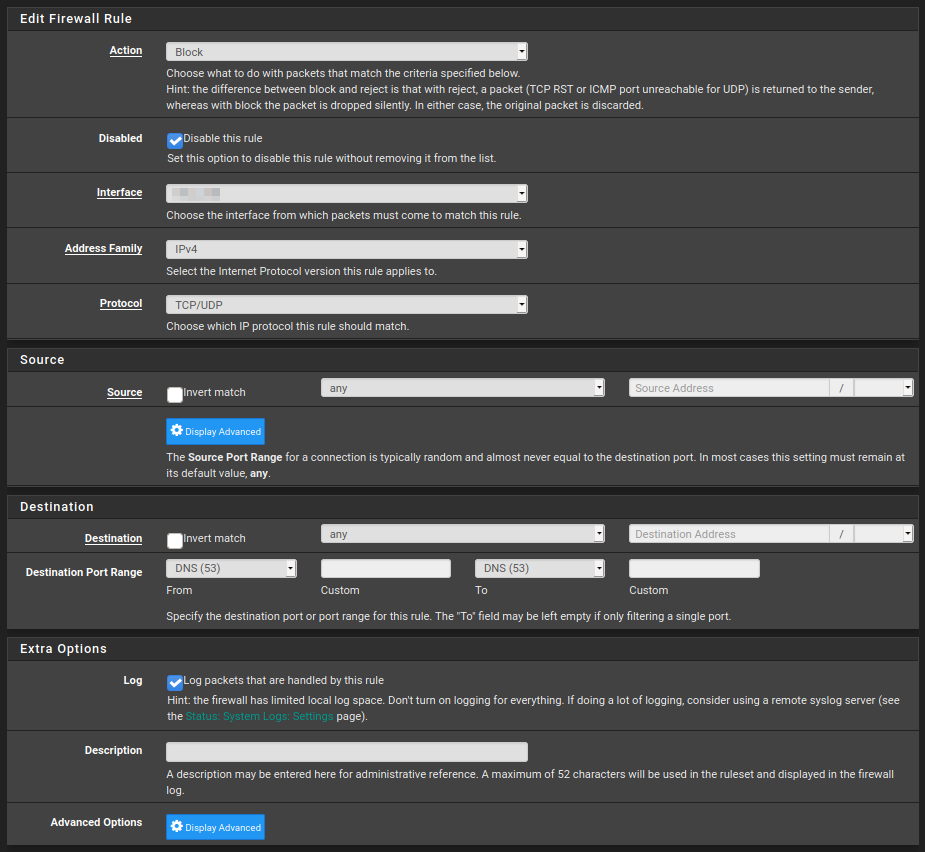
From my limited understanding (I'm trying to learn) of firewall rules, this really ought to work. It's puzzling me that it isn't.
I'd appreciate any suggestions you or anyone else may have!
-
@mattlach said in Allowing only specific DNS server through firewall:
What you are looking at here us first three rules blocking this network from logging on to pfsense via http, https or ssh.
To achieve that, it's better to use "This firewall" as destination. This covers all pfSense IPs, otherwise it may be possible to access another interface IP of pfSense.
The rules look well indeed and should work this way.
I suspect, that the client isn't really using the allowed DNS servers. You may use the Packet Capture tool in the Diagnostic menu on pfSense GUI to investigate that.However, a more reliable way to achieve what you want may be natting any DNS traffic from that subnet to the external DNS servers. A NAT portforwarding rule with destination address any and port DNS and redirecting to the external server should do the job.
You may also add the two DNS servers to an alias and use this one for redirecting, so pfSense sends request alternately to the servers.With the NAT rule the client my think he is accessing his preferred DNS server while the requests are effectively redirected to the server given in the rule.
However, also consider the possibility of using DoH today. -
The rule with a red line in front of them :
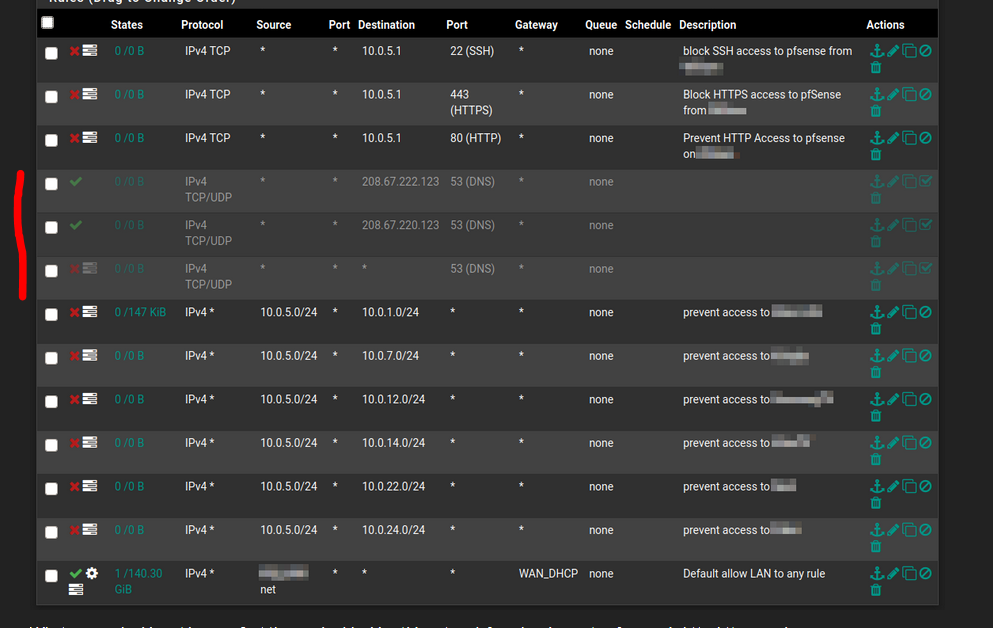
are disabled right now.
-
@viragomann said in Allowing only specific DNS server through firewall:
@mattlach said in Allowing only specific DNS server through firewall:
What you are looking at here us first three rules blocking this network from logging on to pfsense via http, https or ssh.
To achieve that, it's better to use "This firewall" as destination. This covers all pfSense IPs, otherwise it may be possible to access another interface IP of pfSense.
The rules look well indeed and should work this way.
I suspect, that the client isn't really using the allowed DNS servers. You may use the Packet Capture tool in the Diagnostic menu on pfSense GUI to investigate that.However, a more reliable way to achieve what you want may be natting any DNS traffic from that subnet to the external DNS servers. A NAT portforwarding rule with destination address any and port DNS and redirecting to the external server should do the job.
You may also add the two DNS servers to an alias and use this one for redirecting, so pfSense sends request alternately to the servers.With the NAT rule the client my think he is accessing his preferred DNS server while the requests are effectively redirected to the server given in the rule.
However, also consider the possibility of using DoH today.I like the NAT forwarding idea. I will try that. Thank you for the suggestion!
-
@gertjan said in Allowing only specific DNS server through firewall:
The rule with a red line in front of them :

are disabled right now.
Yes,
Thank you for taking the time to reply.
As I explained in my post, they are temporarily disabled because when I turn them on, DNS on the network stops working.
What I am trying to accomplish is for DNS to work once these are enabled.
I am going to try the NAT:ing suggestion above.