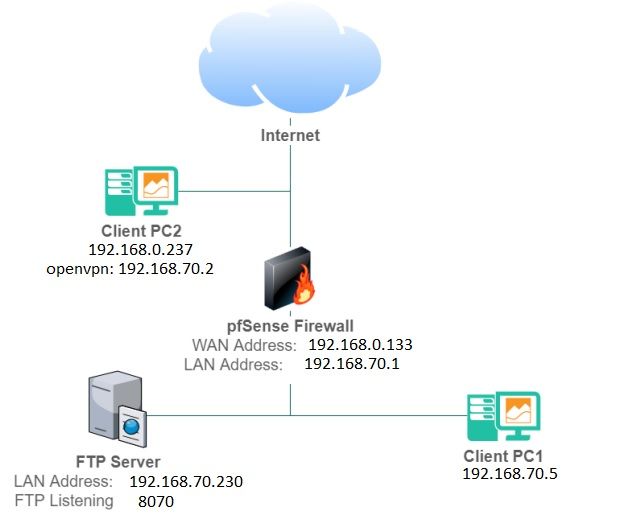
Connect external client to internal client with OpenVPN through pfSense Firewall
-
@viragomann The server can ping PC1 and Firewall(internal IP) but not Client2
Client 1 can ping Firewall (internal IP) but not server or PC2. But can connect to server via FTP.
Client 2 cannot ping anyon, event with vpn address.
Firewall cannot ping anyone.So i am not able to troubleshoot why.
I understand that in the moment PC2 get (using VPN), the same IP address range as server and PC1, they should be able to communicate (via FTP) , or ping each other at least -
@bostongeorge --Update --
I did this: took down firewall in client 1 and server, now internally all can ping each other but from client 2 (external) i get this ping answer which say packets received but host unreachable?
what does that mean`?
-
Your drawing screams asymmetric traffic flow. Why is Client 2 connected to pfSense WAN and not behind pfSense (LAN)?
-Rico
-
@rico Client 2 is an external client. Is not part of the internal network,
I neet to simulate client 2 can connect to server on ftp port 8070.
Client 1 can connect to server on ftp port 8070 (but they are on same lan segment so yeah).Client 2 has to request to the firewall the possibility to go to server.
So firewall must allow that. -
Consider while testing....connecting a Client to pfSense WAN RFC1918 is not the same as a Client connecting from the Internet.
If you really want to test your local installation, use something like a mobile connection.-Rico
-
@rico I understand that. I am testing all using VM
At the moment internally all devices can ping each other and external device can ping internal ip of firewall, but cannot ping internal server or internal pc1.
-
@bostongeorge Don't make your OpenVPN subnet the same as the internal LAN. Begging for issues and problems there. Make it completely different, then add a firewall rule to access whatever you need in the 70-subnet.
-
@tsmalmbe you mean that the problem could be here?
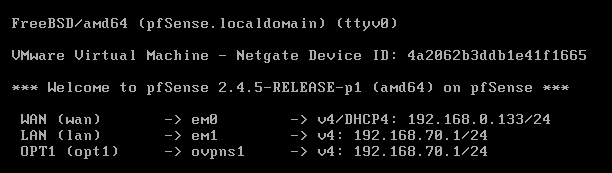
-
@bostongeorge That will surely screw up your setup.
-
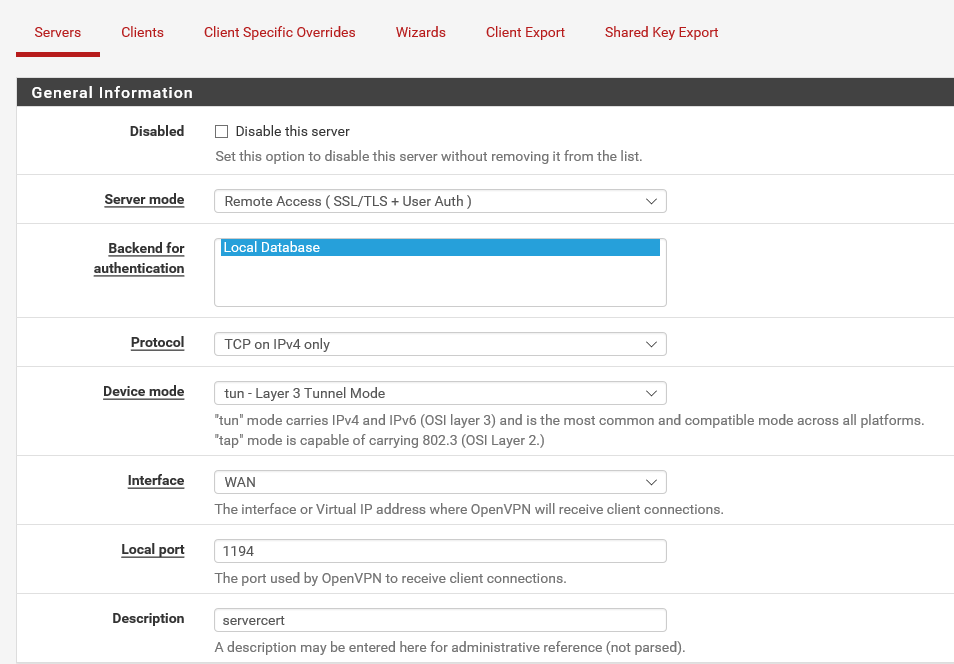
@tsmalmbe I am now using this setup and all is working. I have followed a guide. so for the one interested let me know if you are in same problem (not sure i can post the link here).

I have follow this:
CONFIGURATION VM
pc real 192.168.0.0
FW bridged +Vmnet2 (host only)
Server custom Vmnet2
Client 1 custom Vmnet2
Client 2 bridgedIP ADDRESS
FW WAN 192.168.0.133
FW LAN 192.168.70.1
Client1 192.168.70.5
Server 192.168.70.230
Tunnel 192.168.60.0
Client2 192.168.0.137
Client 2 vpn 192.168.60.2CONFIG ISNTALLATION
- Create CA authority
- Create server ceritficate
- Create User
- Create user certificate
- Enbable interface
- Openvpn wizard
-
You should probably somehow mark this thread as "solved".