Routing between VLAN and parent interface
-
I've setup several VLANs on my network to segment traffic. When I first setup the VLANs it correctly put the right traffic on the right network but the different vlans could still route between each other (i.e. the networks were defined but not separated).
I then setup firewall rules so each network was blocked from routing to the other networks. This worked great creating the isolation I need.
I never setup any rules to block the vlan from accessing the network of the parent interface but despite this, traffic cannot route from any vlan to the any machines on the parent interface. In general this is what I want (again isoltation) but there are limited situations where I do want to setup a rule to allow certain machines to the real lan as that network is where the actual switch and AP are.
I never setup any sort of block rule I'm not sure how to do that. I tried an explicit "allow" rule but that didn't work. How can I route select traffic from a vlan to the non-vlan network?
-
In order to use the parent interface , you have to assign a pfSense interface to it (handling untagged packets) on that port.
Then you have to assign an ip address & submet mask to the new pfSense interface ... Now you have something to use for the firewall rules.If you don't assign a L3 interface to the parent vlan interface , you have the most "excellent" separation , as pfSense won't handle (route) L2.
/Bingo
-
@bingo600 - Thanks for responding.
A pfsense interface is assigned to that port. It has an IP address and subnet masks. The problem is when I create a VLAN with that interface as the parent the VLAN traffic and untagged traffic on the pfsense interface cannot communicate. Maybe I'm missing what you are saying?
-
What rules did you put on the vlan interface after you created the vlan?
-
@johnpoz - For each VLAN interface the final firewall rule was already there which allows traffic from and to anywhere. I added rules before that to deny to each other VLAN. For example:

As you can see there is not a deny to the LAN destination but despite that I cannot contact any device on that parent LAN interface. My goal is generally to deny traffic to that parent LAN interface but I plan to allow certain machines. But as you an see I don't have anything denying it yet and despite that I cannot route from a VLAN to a device on the parent interface.
-
What do the rules look like on the parent interface?
-
Can also see that none of those rules have any hits.. Not even your allow. All of them show 0/0 so nothing has triggered any of those rules.
So your either looking at the wrong interface, or your vlan tagging is messed up and that interface is not seeing any traffic. Your any any rule should show something.. Or at least one of your denys should be sitting hits..
-
@johnpoz - Sorry, a bad example screenshot. It was my "Guest" VLAN and with COVID I haven't had any guests since I set this up :) Here is my "IOT" VLAN which is similar setup but actually being used:
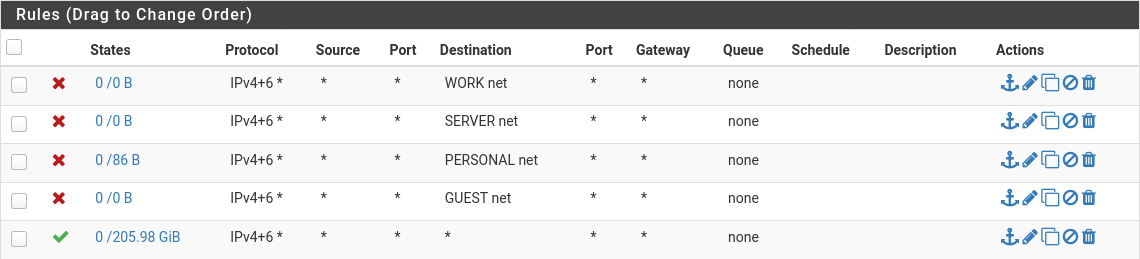
@marvosa - The parent interface is still the default that came with pfSense:
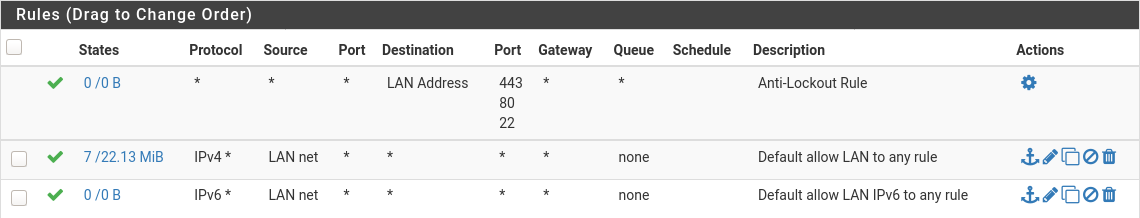
Doesn't seem like anything should deny connecting between a VLAN and the LAN parent interface.
-
@8b2b86ac said in Routing between VLAN and parent interface:
Doesn't seem like anything should deny connecting between a VLAN and the LAN parent interface.
In whatever interface that is - your right it should allow access from that vlan to lan net. But what about the firewall on whatever your trying to talk to in the lan net?
Doesn't matter if pfsense firewall allows it or not, if the host firewall your trying to talk to says no. Users always forget that..
-
@8b2b86ac said in Routing between VLAN and parent interface:
I never setup any rules to block the vlan from accessing the network of the parent interface but despite this, traffic cannot route from any vlan to the any machines on the parent interface. In general this is what I want (again isoltation) but there are limited situations where I do want to setup a rule to allow certain machines to the real lan as that network is where the actual switch and AP are.
I never setup any sort of block rule I'm not sure how to do that. I tried an explicit "allow" rule but that didn't work. How can I route select traffic from a vlan to the non-vlan network?Here are my rules for my guest WiFi:
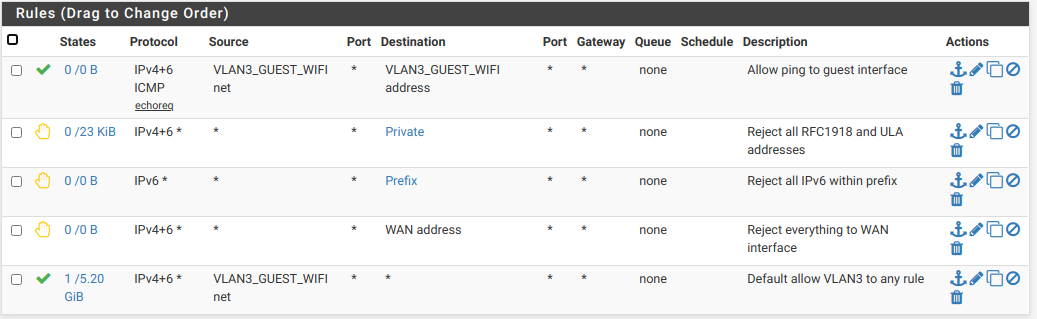
"Private" is an alias for all RFC 1918 IPv4 addresses and IPv6 Unique Local addresses
"Prefix" is an alias for my entire /56 IPv6 prefix.
With these rules, the only things the guest can do is ping the interface and access the Internet.
-
@johnpoz - It's not the device I'm trying to route to as I can create a NAT rule to re-route the traffic and that works. But I'm trying to understand why direct access doesn't work since no rules prevent it.
-
Nevermind. I figured it out. It was something on my own computer blocking it. Thanks for the advice and the help anyway!