Best practice for setting up OpenVPN Client/Server with pfsense HA
-
Hello,
first, this is my current setup:
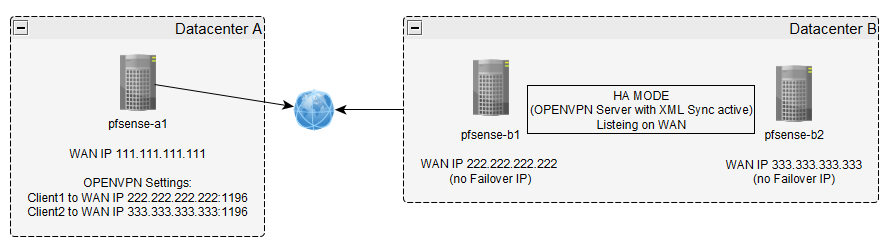
My issue with this, if pfsense-b1 goes down and pfsense-b2 goes into Master Mode, the openvpn traffic from pfsense-a1 can't reach the lan behind Datacenter B anymore. I am using the Peer to Peer Shared Key Mode.
I was trying nearly everything by allow more multiple connections, setup outbound NAT and also disabling the HA-OpenVPN XML Sync and setting up an openvpnserver for each of the cluster pfsense with no luck.
So I want to start from new and I want to know your opinion how you would set up the openvpn client/server.
1.) Should be pfsense-a1 the Server or should provide pfsense-b1 and also b2 a server? (I don't plan to setup additional pfsense in the future)
2.) Would it be a better option to use ipsec instead of openvpn here? I don't need any openvpn features, I just used it because it sounds more simple for me.
I think the issues I have is because my both pfsense on Datacenter B don't use a failover WAN IP and each of them has its own WAN IP.
Thanks a lot!
-
@ephi said in Best practice for setting up OpenVPN Client/Server with pfsense HA:
I think the issues I have is because my both pfsense on Datacenter B don't use a failover WAN IP and each of them has its own WAN IP.
That's not a real HA mode!
If two pfSense are in HA sharing a CARP IP, the VPN services on the primary are stopped and activated on the secondary in case of a failover, either servers and clients.
Not clear how your setup should ever work for any connection through the both firewalls at B.
-
Thanks for your reply.
Yes you are right.
The reason why I want to use two pfsense is, because my vps hoster is performing maintenance multiple times per year and I need to make sure that everything runs 24/7.
They do provide failover IPs, but they want 5€ per month for it with a contract period of 12 months which is too much for the moment. I don't know how long my projects needs to run.
But is there no way other way to get it work?
-
@ephi
I have no idea how the WAN-failover should work actually. Are the LAN interfaces in CARP mode?
You need a single IP on LAN devices used as default gateway. -
@viragomann
Yes, LAN Interfaces are in CARP Mode and works great.In general, all services behind Datacenter B (with the both pfsense) works fine if I turn off one of them. The issue happened if something on Datacenter A wants to talk to a server on Datacenter B in case the master pfsense is down.
The openvpn connection from Datacenter A pfsense still trys to reach the master pfsense. It doesnt understand that it needs to switch to the backup/slave pfsense then.
-
@ephi said in Best practice for setting up OpenVPN Client/Server with pfsense HA:
The openvpn connection from Datacenter A pfsense still trys to reach the master pfsense. It doesnt understand that it needs to switch to the backup/slave pfsense then.
Even if the master isn't reachable?
How did you configure the client at site A? -
Yes it looks like.
Edit: Did a mistake here. The cant reach services on Datacenter A but of course they can talk to the world through its own WAN interface.On Site A I have configured two openvpn Clients.
One Client which points to WAN IP 222.222.222.222:1196 and one Client which points to WAN IP 333.333.333.333:1196.
In a previous try, I also tried to setup 2 openvpn Clients and 2 openvpn servers. They both used their own tunnel network. But it has makes no difference for me from what I saw so I switched back to 2 Clients on Site A and only one Server on Site B.
-
@ephi
That's not a proper setup for using multiple server IPs.Just go with only one client and ensure that both servers are configured identically apart from the IP. The port and the protocol may also differ if needed.
Configure the running client to connect to the one IP and add a second remote line into the advanced options box like
remote 333.333.333.333 1196 updSo if the one server IP is not reachable, the client tries to connect to the other.
-
Thanks, it looks much better.
After ~1min the pfsense openvpn of Datacenter A can successfully connect to the backup/slave pfsense on Datacenter B!However, now I have a new issue. If I turn back on the "master" pfsense, the pfsense on Datacenter A still tries to connect to the backup/slave openvpn Server.
So something needs to say him "ok you are not the master anymore, now you need to reconnect to the "old" master. Mhm...
What helps is to restart the openvpn client of Datacenter A. Then it connects back to the right "master". But this needs manual intervention.
Maybe its better to remove HA functionality and set up these two pfsense on Datacenter B with identical settings except the wan ips?
-
@ephi
That's true, the client stays connected as long as the remote node is reachable.I think, the simplest way to go with such HA setup would be to move the server to Datacenter A and setup two clients at B.
However, if the client on b1 isn't shutdown when b2 gets master as the server isn't as you say, this is also no solution for you.
So the only way, I can think of, is to insert an additional router (pfSense) between the two pfSense and the LAN and set up a Multi-WAN configuration with monitoring a public IP on both, so it would failover the connections to that one that have internet, while you have again a separate OpenVPN connection to each public WAN.
-
Thanks a lot.
I will think about to setup a third pfsense, maybe this really could work.
Interesting for me is the question, whether the same issues comes when using ipsec instead of openvpn. Maybe I should check this before setting up a third pfsense.
-
@ephi said in Best practice for setting up OpenVPN Client/Server with pfsense HA:
Interesting for me is the question, whether the same issues comes when using ipsec instead of openvpn. Maybe I should check this before setting up a third pfsense.
I cannot tell you. Maybe you should ask this in a new thread in the IPSec section.
-
Mhm. Haven't get it running so far.
Is there a name for what I am trying to get running there?
Are gateway groups maybe what I am looking for?
So - I don't need a real HA. I just need a second pfsense on the "Datacenter B" that starts to work in case of one of them fails / is down. I can create the firewall rules on both, its not that much that I need the XML Sync / HA functionality.
-
@ephi
Got an idea. May seem a bit crazy, but I think, it will work.Configure both OpenVPN servers at site B to listen on the LAN CARP VIP and add a NAT rule to both pfSense boxes to forward the OpenVPN traffic to the LAN VIP.
This way pfSense should turn off its OpenVPN server when it goes into backup mode. So only the master should have an active VPN server and the client can only connect to the master. -
Uh, this sounds interesting. You could be right. I will try this the next days.
Thanks for your help!
-
@ephi
Driving an OpenVPN server on LAN VIP works definitely. I did that already. The only part, I'm not familiar, is your "special HA setup" with CARP on LAN only.