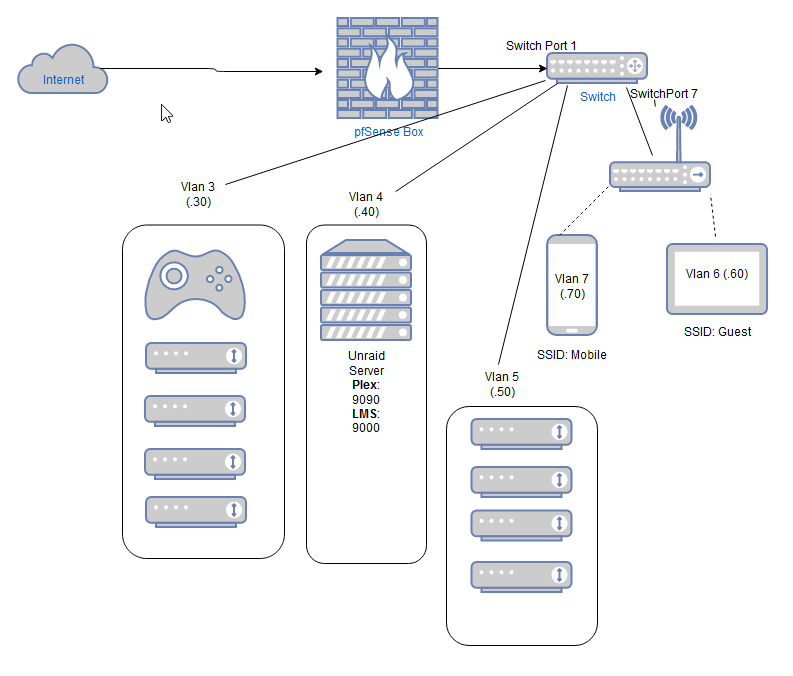
Vlans and firewall rules
-
Let me rephrase that....
In vlan3 I have one device(AVR) that doesn't need access to anything.My Iphone just needs access to it to control it from an App.
-
@cburbs The idea would be the same.
Firewall rules goes from top, to bottom.Just block the DVR to access all other things, this rule must be in the top.
Your phone, that I'm assuming that is in other VLAN, you create a firewall rule in this other VLAN allowing the iphone to access the DVR, then you block other devices to access the other vlans, and finally the internet rule allowing everything.
In case iphone and DVR are in the same VLAN, they wouldn't communicate through the firewall, it would go directly through the switch.
-
Drawing it out as it helps me sometimes
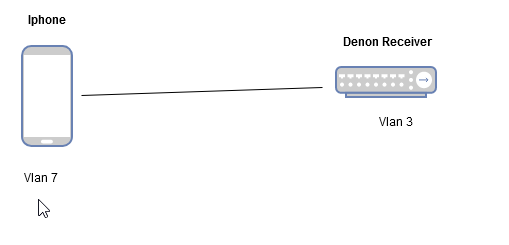
So my Iphone which is on Vlan7 needs to talk to my Denon Receiver on Vlan3.
You mention creating the rule in Vlan 7 to talk to the device in Vlan 3.
Could you also do it the other way around and create the rule on Vlan 3 to allow the Iphone in?
Is one way better than the other? and why?
-
@cburbs Creating the rule in VLAN3 wouldn't work.
The interface where the packet is coming from, needs to allow that flow in first place, otherwise the firewall would drop the packet.
pfsense is a stateful firewall, which means that if the packet is allowed to enter, the return of the packet would work, even without a rule.
So, for an example, you can create a rule blocking everything in VLAN3, so all VLAN3 ip addresses would be blocked to enter the firewall.
But, if you come from VLAN7, and if there is a rule allowing this flow, the return traffic from VLAN3 would work, even with a block everything rule.
-
@cburbs
My Onkyo Remote APP won't play if my phone/Ipad isn't on the same Vlan.
The Phone (App) simply won't detect the AMP.Bloody sw devs
Considering to trace a bit on the APP , and maybe try this package, if it fits the need
https://forum.netgate.com/topic/155698/how-can-i-get-this-udp-relay-package-for-casting-across-vlans
-
So if I setup the "Block to firewall" rule like you have in the one post but I have no internet access when it is enabled? Am I missing something ,,
Isn't that just blocking access to anything on the pfsense box?
-
@cburbs That is not how it works.
The packet has a source, and a destination.
When the packet goes to the internet, the any is the destination, let's say google DNS for an example, so the destination is this case would be 8.8.8.8;
The firewall would see a packet going to 8.8.8.8, and not to the firewall itself.That "Block to firewall" rule, is to block users from reaching the firewall itself, and not to block users to go through it..
If the firewall is the destination of the packet, the pfsense GUI for an example, that "Block to Firewall" rule would block it
-
Ok I looked at one of your earlier posts -
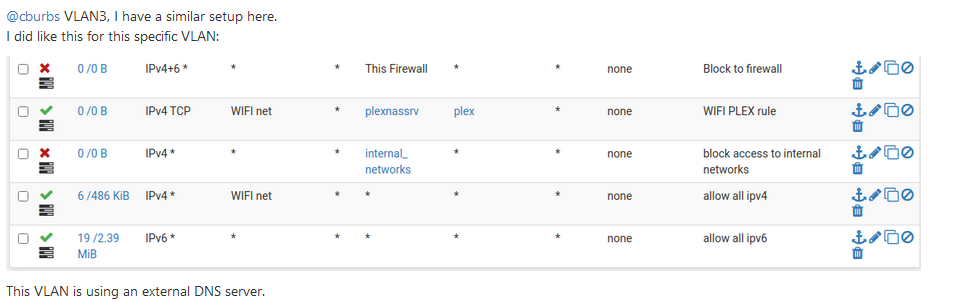
Saw your note about DNS - That was my issue no DNS being used.
So let's back track for a moment -
These items I want on Internet Only Vlans I still want to protect them in a sense.- would still like to use the DNS resolver I am using on the main Lan
- Still want them also hitting pfblockerng as well
- Can't access other lan/vlan
Doable, strange, silly, odd?
-
@cburbs It would be like this:
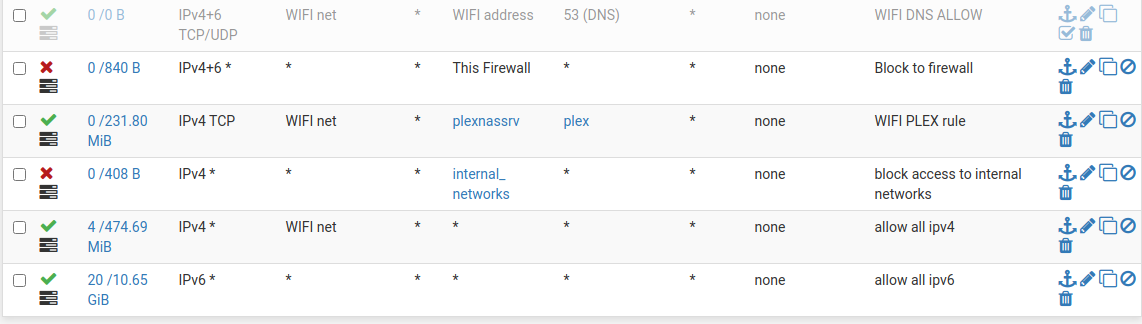
First rule is the DNS, in my case, it's disabled, but its only to show you, in your case, you would need to enable it.
First rule allows DNS to pfsense.
Second rule block everything to the firewall itself.
Third rule allows Plex from WIFI_NET to the plexnassrv in another vlan
4th rule blocks everything from this vlan to the other vlans
5th rule Internet allow ipv4
6th rule Internet allow ipv6 -
Wow way too much time spent on this lately but finally getting it to where I want it to be.
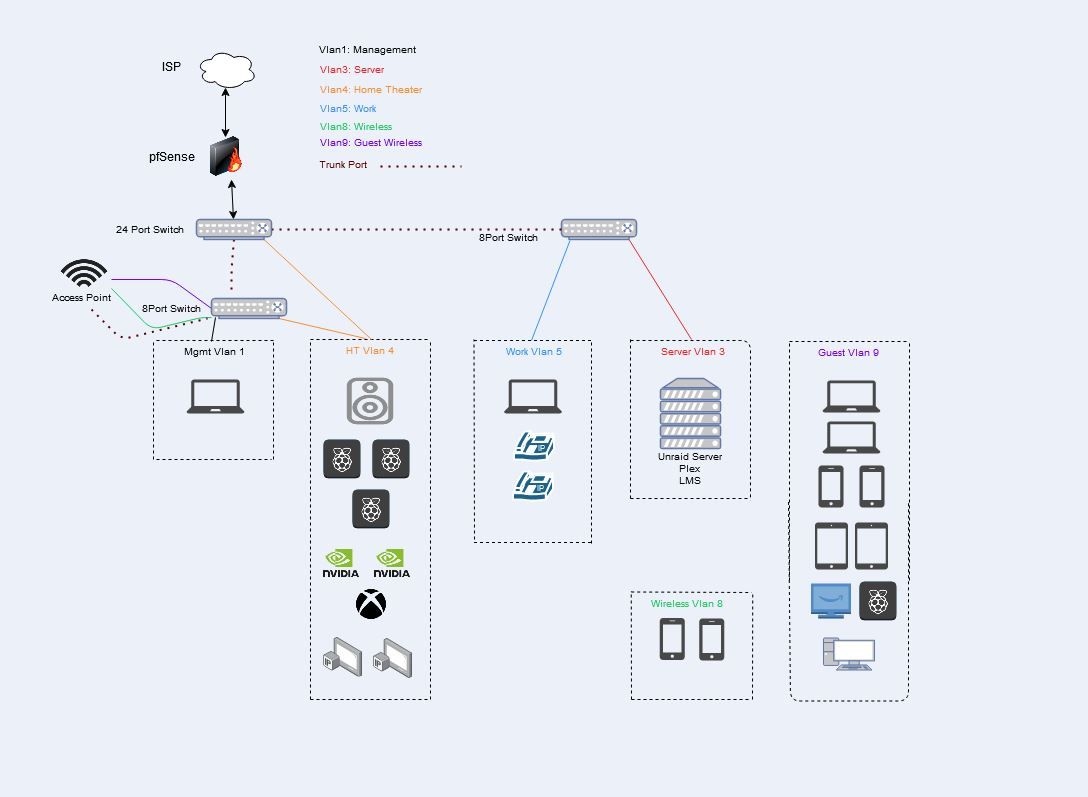
Vlan1: Management
This is the Lan off the pfsense firewall. It has access to pfsense gui, all switches, ap, vlans.Vlan3: Server
Unraid server running plex, LMS, a few other things
Allowed: pfBLockerNG, DNS, Plex to HDHomeRun tuner on Vlan4, Internet
Blocked: Firewall & Internal communication.Vlan4: Home Theater
Denon Receiver, (3) piCorePlayers, (2) Nvidia Shields, Xbox, (2) HDHomeRun Tuners
Allowed: pfBLockerNG, DNS, Plex players to Plex on unraid, piCorePlayer to LMS on unraid, Internet
Blocked: Firewall & Internal communication.Vlan5: Work
Work laptop, (2) VOIPs
Allowed: pfBLockerNG, DNS, Internet
Blocked: Firewall & Internal communication.Vlan8: Wireless
(2) Iphones
Allowed: pfBLockerNG, DNS, Internet
Blocked: Firewall & Internal communication.Vlan9: Guest Wireless
(2) Chrome books, (2) iphones, (2) kindles, PicorePlayer, roku, PC
Allowed: pfBLockerNG, DNS, Internet
Blocked: Firewall & Internal communication.Equipment:
Pfsense box: HP Intel(R) Core(TM) i5-2400 CPU @ 3.10GHz, 16 gigs of ram, HP 4 port ethernet card - Packages running: aprwatch, iperf, nmap, ntopng, pfBlockerNG, RRD_Summary, Status_Traffic_Totals, TelegrafAccess Point: Netgear R7800 running Openwrt
Switches: TP-Link TL-SG1024DE, (2) TP-Link TL-SG108PE
Server: ASRock X99 Extreme3, CPU 2GHz 12 cores(24 HT), 32gigs ram
Unraid
Parity Drive: 4tb
15TB HD Space
Cache Drive for Dockers
Unassigned drive for VMs (Windows, Hassio, Linux)Things still testing:
Iphone control while on Vlan8 to items in Vlan3(plex), Vlan4(Receiver, PiCorePlayers, Shields, Roku).Verify anything in Vlans 3+ can't get to pfsense box, switches, APs, Server.
I am sure I am forgetting something.