LAN Interface not replying to ICMP Request from WAN Network
-
Hello,
i've having an issue whereby i cannot ping my pfsense box from my WAN network.
My topology is as follows:
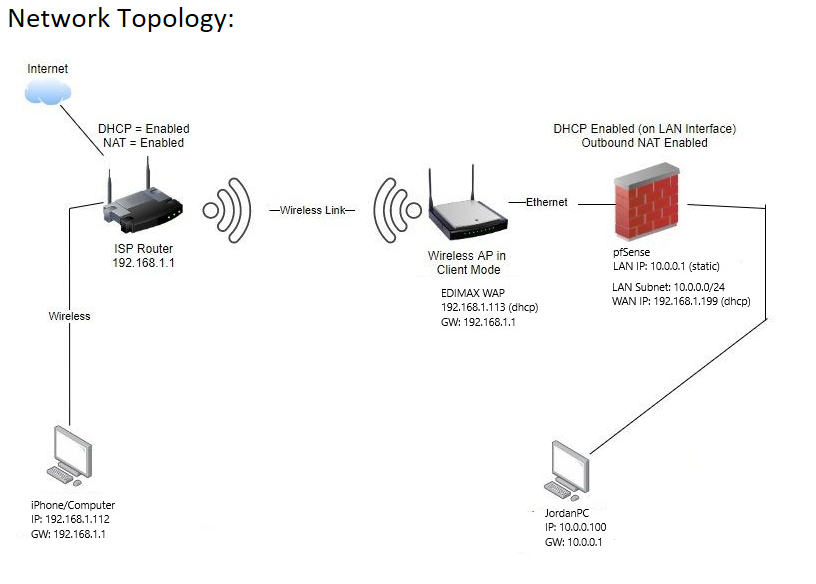
im trying to ping from 192.168.1.112 to 10.0.0.1
I can ping from 10.0.0.100 to 192.168.1.1
i can ping from 10.0.0.100 to 192.168.1.112
i can ping from 192.168.1.112 to 192.168.1.199
however:
i cannot ping from 192.168.1.112 to 10.0.0.1Packet capture shows that ICMP request is reaching the IP 10.0.0.1 but there is no reply from 10.0.0.1.
Firewall rules are as follows:
WAN
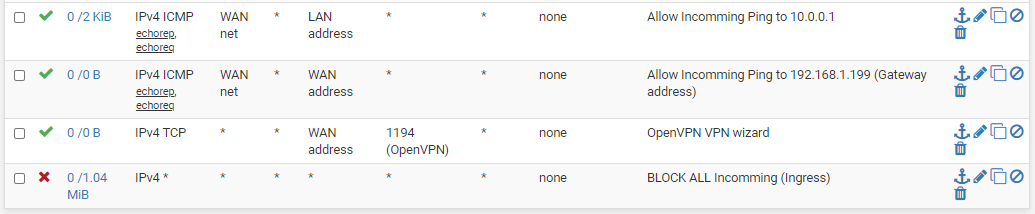
LAN

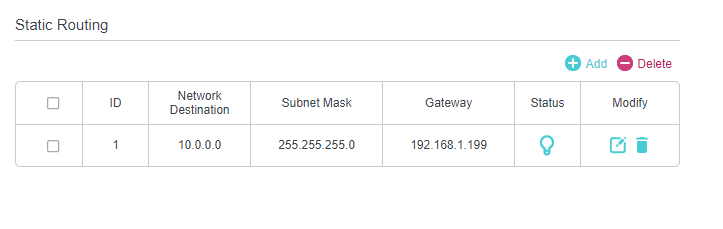
I have a static route setup on the 192.168.1.1 router to route traffic to 10.0.0.0/24 subnet to 192.168.1.199 gateway
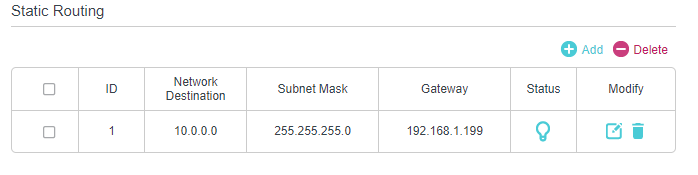
I cannot figure out why 10.0.0.1 will not reply to the ICMP request.
further more: if i connect into the pfSense router via my OpenVPN network (172.16.0.0/24) - i am able to ping 10.0.0.1 successfully.
Automatic outbound NAT is enabled.
Your help and expertise is greatly appreciated!
-
@tgwaku Any reason why you’re running NAT on your pfSense device, all the addresses are RFC1918?
It means you need to port forward on the pfSense device.
-
I probably have Outbound NAT enabled due to a lack of understanding of how NAT works :(
i think in a previous confiuration i was unable to make my topology work without auto NAT enabled - but i've turned it off now and my internet seems to be working on the 10.0.0.0/24 network so i will leave it disabled, thanks :)
I have port forwarded anything that i can think of to try and get the pinging to work but still not working :(
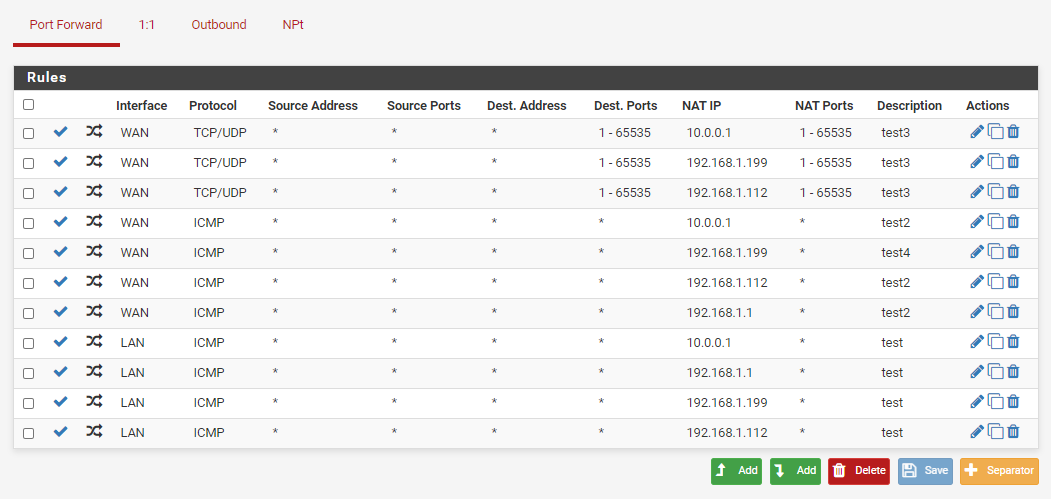
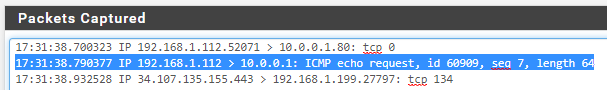
still no ICMP reply atempts showing packet capture:
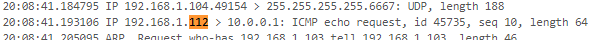
-
@tgwaku Do a packet capture on the pfSense LAN interface, filter on ICMP.
Do you see ICMP packets when you ping 10.0.0.100 from 192.168.1.112.
It could be 10.0.0.100 is blocking ICMP from any non local subnet.
-
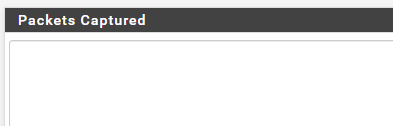
Packet capture on LAN interface with ICMP Protocol filter
Not seeing ICMP packets when pinging 10.0.0.100 from 192.168.1.112 - (Packets Captured is blank)
On WAN interface packet capture ping from 192.168.1.112 to 10.0.0.100 yields no reply attempt again. (only echo request)
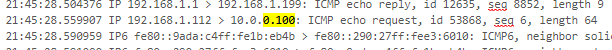
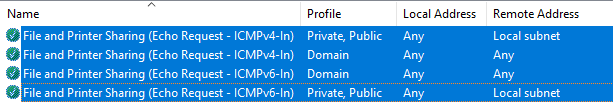
There is definitely a firewall rule in windows that only allows ICMP request on the Local Subnet for Private and Public network profiles. Looks like domain profile connections can traverse subnets?
-
So outbound nat is disabled and the port forwards have been deleted ?
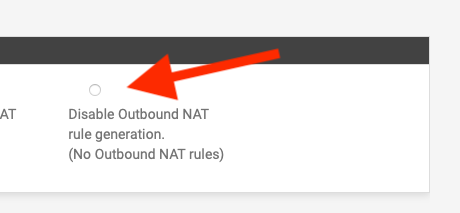
If so it should work as 192.168.1.0/24 and 10.0.0.0/24 are directly connected.
-
Yep, Port forwards have been removed:
NAT is disabled:
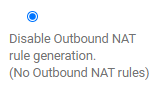
But still cannot receive reply from 10.0.0.1 (or 10.0.0.100) from 192.168.1.112
-
Also, with NAT disabled my 192.168.1.1 router page gives:
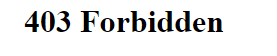
-
It's talking to your router:-
The HTTP 403 is a HTTP status code meaning access to the requested resource is forbidden. The server understood the request, but will not fulfill it due to client-related issues. IIS defines non standard "sub-status" error codes that provide a more specific reason for responding with the 403 status code.
-
I have a feeling the 403 error is because the router doesn't like to accept connections from ip's on a different subnet. with auto nat on it connect to the router page under the gateway ip of 192.168.1.199 which is accepted. or at least this is my best guess at what is going on there.
still unable to ping my setup however :(
-
@tgwaku Its not a feeling, its reality
Shitty isp routers only accept connections from connected lans.
It might be possible to allow access, if the settings permit, and you will also need a static route on the isp router pointing at the pfsense gw for your pf lan spaceNot always the case that you can do that.
For the scenario at hand, all nat sessions are handled by the isp router, which usually becomes problematic whith many sessions.
Also inbound filtering is limited to the capabilities of the isp router.Consider putting the isp router in bridge mode
and also eliminate the wireless connection to pf, for gods shake. :) -
@netblues said in LAN Interface not replying to ICMP Request from WAN Network:
@tgwaku Its not a feeling, its reality
Shitty isp routers only accept connections from connected lans.
It might be possible to allow access, if the settings permit, and you will also need a static route on the isp router pointing at the pfsense gw for your pf lan spaceNot always the case that you can do that.
For the scenario at hand, all nat sessions are handled by the isp router, which usually becomes problematic whith many sessions.
Also inbound filtering is limited to the capabilities of the isp router.Consider putting the isp router in bridge mode
and also eliminate the wireless connection to pf, for gods shake. :)^^ This
-
So basically, my setup is trash and i need to rethink my topology?
fair enough.
Ideally I would never have had it set up this way but I'm in a share house and it seemed like the most anti-social way to do it so i didn't have to have a conversation with my house mates about messing with their ISP router

-
@tgwaku Enable nat and pop an access-point behind your pfSense router.
You may have problems with double nat, but all your equipment would be on the same lan segment.
You could get rid of the WiFi bridge using two ethernet over power gadgets.
-
@tgwaku If you know what you are doing, your housemates will love you about the performance...
-
@tgwaku said in LAN Interface not replying to ICMP Request from WAN Network:
it seemed like the most anti-social way to do it so i didn't have to have a conversation with my house mates about messing with their ISP router
You can for sure do it that way.. With the AP as a client bridge wireless connection to the house network.
But you need to give pfsense wan an IP on this network, just use dhcp should be your best choice there. Let the house dhcp server give it an IP on that 192.168.1 network.
Yes double nat, leave pfsense default for nat (auto). Then setup pfsense lan to be something other than 192.168.1 or anything that over laps that, 10.0.0/24 would be fine for you pfsense lan.
This isolates you from the house network. If you do want to get access to something behind pfsense to the lan, then you would need to setup a port forward.
But I concur I would classify such a setup with a wireless connection like that as "trash" no offense ;) But yeah sometimes you have to work with what you have.
-
Thank you John for giving me to confidence to keep persevering with this issue! I am not one to give up easy, so after adding every firewall rule under the sun.. Trying hybird nat with manual rules, port forwarding everything i could think of... Nothing was working..
Then I just started trying random things. and one of those things was to delete the ARP Cache entries for a few ip's (can't remember which one's, probably for 192.168.1.112). I deleted on both the pfSense router and on the ISP TP Link router ARP Tables. Then tried to ping again from 192.168.1.112 to 10.0.0.1...... and it... worked...

Does this make any sense why that would fix the issue? is it a thing like, arp cache gets too full or something and ping requests get dropped in one direction?
Full head scratcher!!! but it's working now which is good. I'm gambling that in a week it may break again so I will put a reminder on my phone to test the ping, and if it's not working I'll delete the ARP Table entries again (this time paying more attention) so i can confirm that this was indeed the nail in the coffin.
Thanks everyone for your help troubleshooting! @NogBadTheBad @netblues @johnpoz
-
At a complete and utter loss to why you think you should be able to ping the lan IP of pfsense from such a setup..
Your .112 client has no clue how to get to 10.0.0.1, so it would send it to its gateway. That router has no clue how to get to some 10 network, so best case it would just drop the traffic because its rfc1918 - but it would most likely send it onto the isp gateway.
I have no idea what you think is going on, or what you have actually clicked or configured. But as drawn - there is NO Possible way for .112 to be able to ping 10.x -- unless you setup a route on it?? To point to pfsense wan IP to get to 10.x network..
-
-
That is a asymmetrical mess.. And your going to have nothing but problems with it. For a downstream router you would need a transit network. Or is asymmetrical.. If you were going to route then it would be done on the .112 box directly not the isp router.. To make sure the traffic is not asymmetrical.
Dude - double nat, and port forward for whatever services you want something on the 192.168.1 network to get to behind pfsense.
I gave you the solution to how to do this.. And pinging behind a nat is problematic, and your only ever going to setup 1 port forward for icmp if you wanted to ping pfsense lan IP or something behind pfsense.
Just ping pfsense wan IP to validate connectivity..