Suricata Config Advice for Multi VPN
-
I watched the video from Lawrence Systems re configuring Suricata.
In the video he recommends not setting configuring to use it on the WAN ports because of the noise generated and the default blocking that exists anyway.
In my config, my pfsense is connected to a cable modem (used in a router config with internal 192.x).
I have two VPN redundant connections out from the pfsense.I previously used snort on configured on the WAN and VPN connections (but not on the LAN/VLANs) and saw lots of blocking. Particularly from the internal network of the VPN provider, but also from the 192 modem and 192 pfsense addresses.
Recently, i tried to config auto-dos on my netgear switches, but they keep shutting ports down connected to the wifi access points and my linux box. I had to disable this to remain functional.
I am out the point to install Suricata with the objective to try and stop/find what is causing the auto-dos ports disablement and will add the LAN/VLANs.
My question is;
in view of the recommendation from lawrence,
if i do not add the WAN interface, should i still add the OpenVPN interface, or treat that like the WAN and not include as well?cheers
-
@gwaitsi said in Suricata Config Advice for Multi VPN:
My question is;
Hi,
Use the package maintainer's recommendation @bmeeks (Snort / Suricata)
https://forum.netgate.com/topic/141743/best-rules-to-best-protection-in-wan-and-lan-interface/2

-
@daddygo thanks for that, i will follow that, but i am still unclear about how to handle the OpenVPN client connections to my provider.
The WAN interface has the Block Bogon & Private Networks enabled.
-
The VPN interface does not have Block Bogin & Private Networks enabled (should i have it enabled?)
-
should enable suricate on the VPN interface (depending on answer to 1 - i guess)
-
-
@gwaitsi
Let's look at the answers in a row:
Okay then you already understand that using WAN IPS is unnecessary in terms of IDS test maybe if you are a developer and you are looking at internet noise, etc.
@gwaitsi "The WAN interface has the Block Bogon & Private Networks enabled."
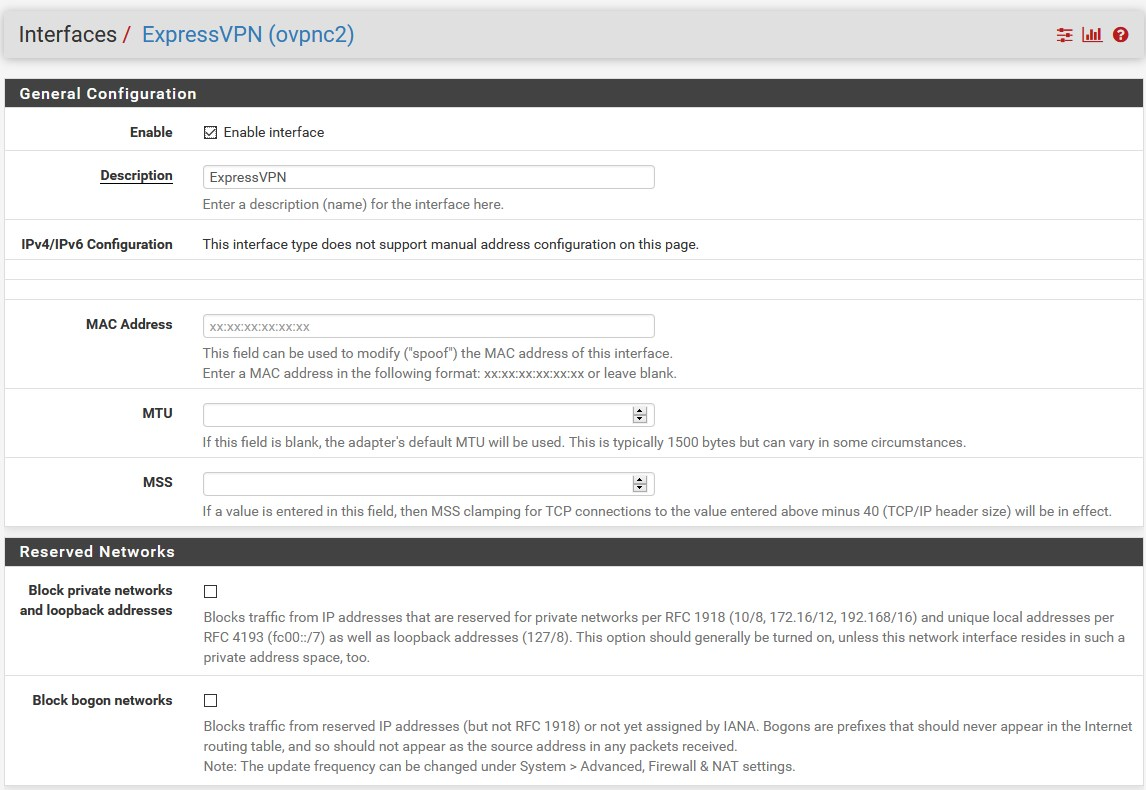
that's okay - Since this is the WAN interface, I think you also connect to the VPN provider through thisThe VPN (client) interface is NOT a WAN interface - it is best to use it as a gateway (GW)...
in this case, you can "route" anything through itin my example:
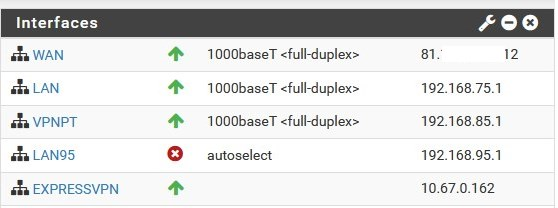
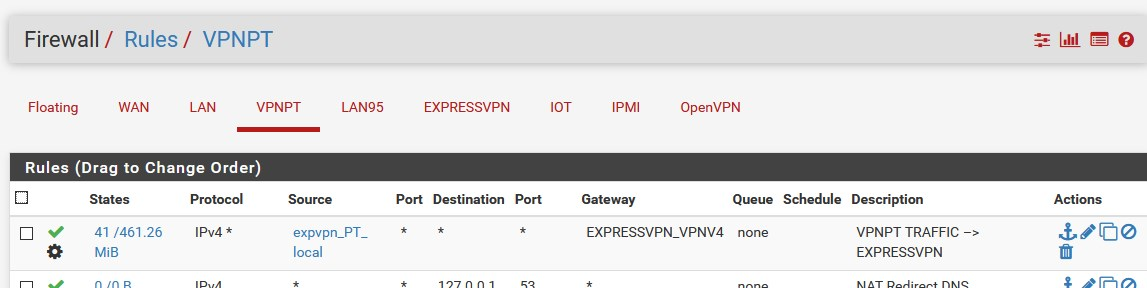
- I have an internal interface configured just for things going through the VPN (VPNPT) - GW ExpVPN interface (client)
-I have an internal interface configured for things without VPN (LAN95), its gateway to the WAN DHCP to ISP
-The original (LAN) interface is for internal management purposes only, on this I configure pfSense or with Remote OpenVPN (this is important)
I show PRTSCs:

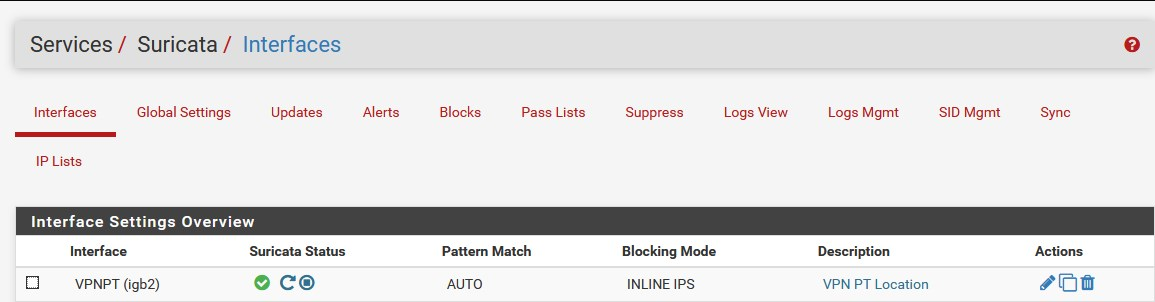
and the Suricata:
+++edit:
with this, Suricata examine all traffic which passing through the VPNPT physical interface, regardless of what the upstream GW (ISP or VPN) is -
@daddygo thanks, super example - i'm also using Express ;-)
Only difference is, i route all traffic over the VPN and bypass by exception and i have enabled block bogons on the VPN.
So, now i just need to tune for a week or so and then switch on blocking.
last question if i may.
my cable modem has the option to switch from "routing" to "modem" state.
In either case, devices connected to the 4 LAN ports work.In modem state, they obtain and address from the ISP. 17x.
In router state, they obtain a 192.x address.I tried switch to modem state, but then had no internet from pfsense.
I will connect a 2nd ISP to the pfsense.Is it better to connect both in modem state, or using the routing state?
-
@gwaitsi said in Suricata Config Advice for Multi VPN:
my cable modem has the option to switch from "routing" to "modem" state.
I strongly recommend the modem mode (alias bridge), then you can avoid the double NAT problem
see your ISP's description for what to use on your WAN in "bridge" mode
usually it is DHCPhowever, after switching to bridge mode, unplug your (from eletricity - power cycle) ISP CPE for a 30-minute period, this will help
+++edit:
@gwaitsi "by exception and i have enabled block bogons on the VPN."
this is completely unnecessary and can cause problems as it has already happened on the WAN interface
the top upstream is the WANyou can see that the VPN IP on the pfSense is an internal range (private) - RFC1918 10.x.y.z
-
@daddygo awesome. thanks for the advice. will try switching to bridge again tonight.
-
@daddygo FYI
- i created an interface for the LAN and all my VLANs.
- I noticed all the alerts appear on both the VLAN and the LAN interfaces,
so it looks like it is not necessary to have one for the VLANs.
I disabled a couple of the VLANs and i see the alerts for their dst IPs is being caught in the LAN (Lagg interface to he main switch)
-
@gwaitsi said in Suricata Config Advice for Multi VPN:
I noticed all the alerts appear on both the VLAN and the LAN interfaces,
this of course works like,.... because the parent interface is the LAN

-
@daddygo hi, sorry, I come back to this topic again. Actually, i am also using expressvpn too.
What i don't understand.
- vpn is not a wan interface
- outsiders on the same vpn access point, can probe the pfsense no? especially as bogon/
private networks are not blocked.
don't we want to have visibility to attacks from th expressvpn network? Isn't that what Suricata helps out with?