VLANs, What am I doing wrong?
-
I've got my PFSense box connected to an old Cisco Catalyst, connected to an old UniFi UAP:
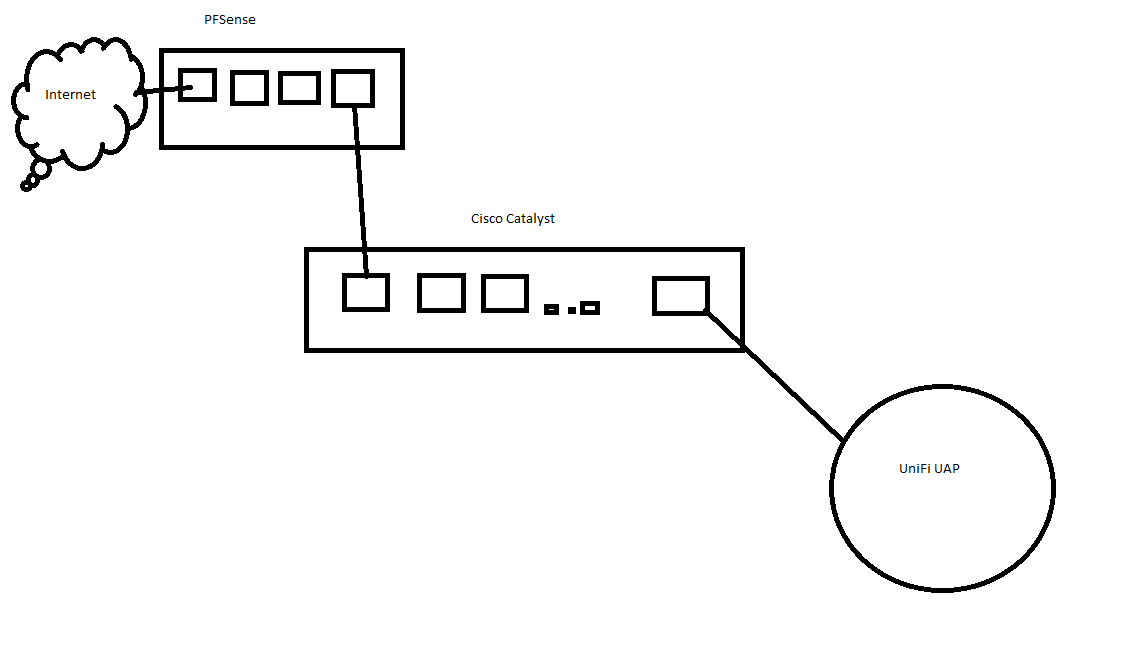
My goal with this is to learn how to use VLANs, but apparently I'm just an idiot or something and can't figure them out.
As far as I know, the switch is set up correctly (confirmed this on the Cisco forums), but the problem I'm running into is the VLANs don't work, period.
I have 3 set up in PFSense:
VLAN 10 - IOT (192.168.10.1/24)
VLAN 20 - Guest (192.168.20.1/24)
VLAN 99 - MGMT (172.16.1.1/24)
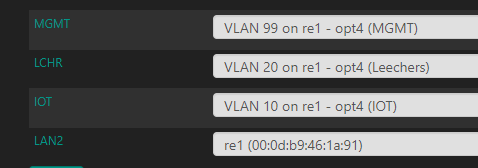
I also have an additional physical interface assigned as well - LAN2 (10.10.100.1/24). I'm using LAN (10.10.10.1) for my main network with an HP switch and a newer UniFi AP so I can play around with the second NIC on the PFSense without fear of taking my network offline.
For simplicity, I set up the 2 ports on the switch to Trunk mode and included all VLANs (which the Cisco forum confirmed was technically correct).
For testing, I connected my laptop and assigned it an IP in each subnet (x.x.x.10) but it refused to connect for all VLANs. LAN2 worked fine though.
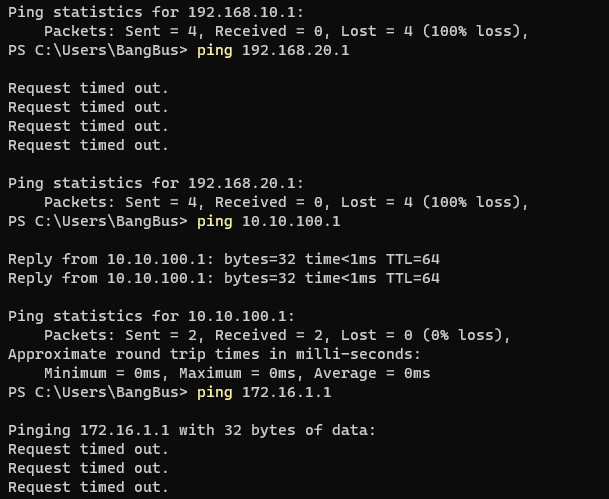
I know the switch works because I even assigned the Cisco ports to access mode and just used VLAN 99 and LAN2. LAN2 works, VLAN 99 does not.
Everything in PFSense is set up correctly as far as I know, but it appears I'm missing something?
Each VLAN has it's own DHCP Server:
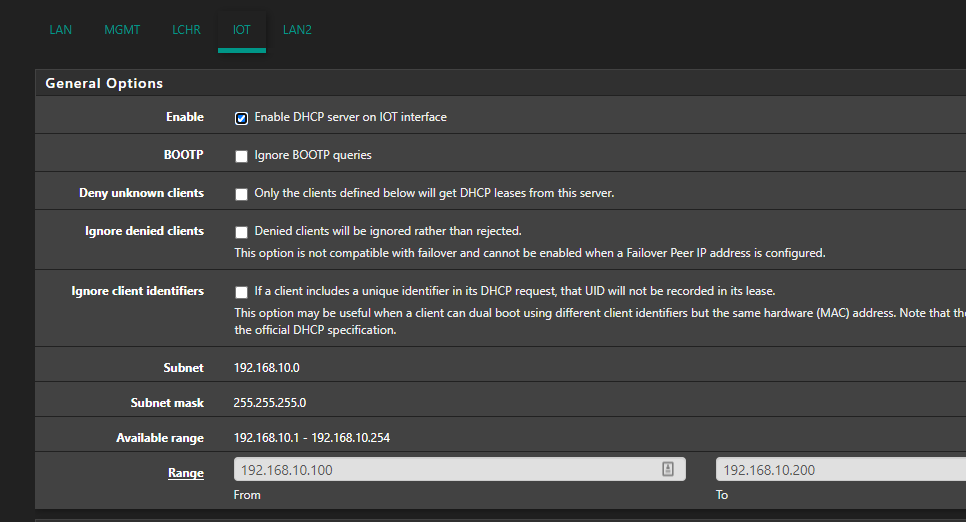
I don't have the access locked down so the firewall rules are set to Pass IPv4 * (VLAN10/20/99) Net -> * :
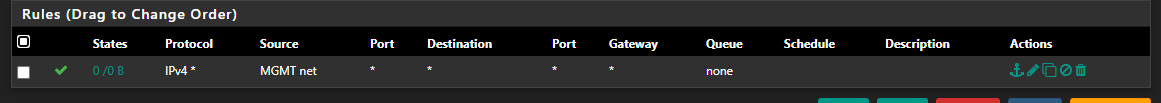
What gives? It seems like theoretically this all should work, and yet it doesn't..
-
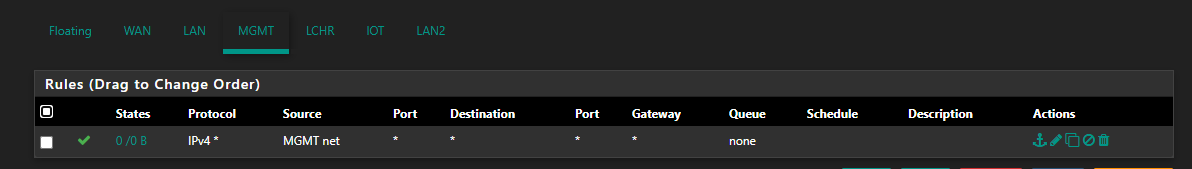
What interface is that rule on where mgmt net is the source? It shows no hits.. So is your device even talking to pfsense?
If all your vlans have rules allowing the net they are attached to any any.. Then they should be able to ping IPs of that vlan, and any other pfsense IP. And they should be able access the gui even.
If you have that rule on valn 10, 20 and 99 interface then no that would never work.. The source would be the net the interface is.. mgmt net would never nor could never be source of the traffic into vlan 10 or 20
The only source into an interface would be from the network its attached too.. Unless you had downstream networks using that network as a transit?
Rules are evaluated top down, first rule to trigger wins.. no other rules are evaluated.
If you have vlan 10, say 192.168.10.100 trying to talk to some IP 172.16.1.1 for example... Its source would be 192.168.10.100 and dest would be 172.16.1.1.. So how would your rule on vlan 10 ever allow that traffic? If your rule is say source has to be 172.16.1/24
-
@johnpoz VLANs and LAN2 are all on re1. LAN2 is the only interface that's talking to pfsense through the switch, none of the VLANs are successfully able to make any connection to anything, not even their default gateway.
I'm not sure I understand what you're saying about firewall rules. Do you mean to say I have them backwards? I should either select the Invert Match box, or set the subnet as the destination instead of the source?
LAN2 has the same rules as all the VLANs and it works just fine:
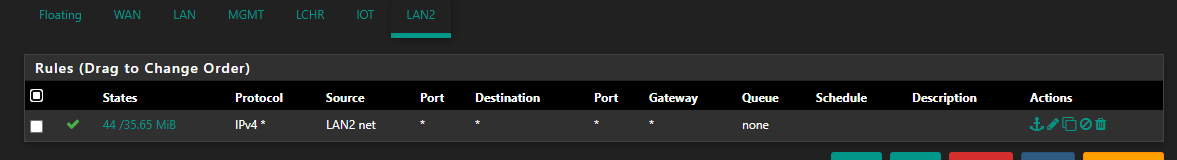
Ultimately, at this point, I don't really care if the subnets can talk to each other. My main goal at the moment is to just get the VLANs to work, period. Once they work, I'll start adding routing rules to restrict traffic.
-
@apathia Either post all your rules, or put an any source to any destination allow on all interfaces.
(or temporarily disable filtering all together)
Your vlans seem correct too.
Do check your trunk and access settings on switch. -
Post up your switch config.. That is a pretty basic setup.. But if you can't even ping your pfsense IP in the vlan, with those rules.. You have a issue.
Lan2 working - but its not a "vlan" its untagged..
The port connected to pfsense off your switch needs to be tagged. Please post up the switch config showing your vlans and port configs.
example. Here is switchport connect to my pfsense that carries vlans. And has an untagged vlan on it.
interface gigabitethernet5 description "sg4860 WLan and vlans" switchport trunk allowed vlan add 3-4,6-7,19 switchport trunk native vlan 2 -
You did create the VLANs on the switch didn't you ?
FWIW here is my config of a 2960x 28 POE switch I've been playing with.
! Last configuration change at 21:18:36 UTC Wed Jan 4 2017 ! version 15.2 no service pad service timestamps debug datetime msec service timestamps log datetime msec service password-encryption ! hostname switch ! boot-start-marker boot-end-marker ! enable password 7 XXXXXXXXXX ! username admin privilege 15 password 7 XXXXXXXXXX aaa new-model ! ! ! ! ! ! ! ! aaa session-id common switch 1 provision ws-c2960x-24ps-l ! ! ! ! ! ! ip domain-name network.local ip name-server 172.16.1.1 vtp domain network vtp mode transparent ! ! ! ! ! ! ! energywise domain cisco security shared-secret 7 XXXXXXXXXX ! ! ! spanning-tree mode rapid-pvst spanning-tree extend system-id ! ! ! ! vlan internal allocation policy ascending ! vlan 2 name USER ! vlan 3 name GUEST ! vlan 4 name IOT ! vlan 5 name DMZ ! vlan 6 name VOICE ! vlan 7 name TEST ! vlan 9 name NORD ! vlan 11 name SECURE ! vlan 998 name BLACKHOLE ! vlan 999 name LAN ! lldp run ! ! ! ! ! ! ! ! ! ! interface Bluetooth0 no ip address shutdown downshift disable ! interface FastEthernet0 no ip address shutdown ! interface GigabitEthernet1/0/1 switchport access vlan 2 switchport mode access power inline never spanning-tree portfast edge spanning-tree bpduguard enable ! ! snip snip ! interface GigabitEthernet1/0/24 switchport access vlan 4 switchport mode access power inline never spanning-tree portfast edge spanning-tree bpduguard enable ! ! snip snip ! interface GigabitEthernet1/0/28 switchport trunk allowed vlan 2-999 switchport trunk native vlan 999 switchport mode trunk ! interface Vlan1 no ip address shutdown ! interface Vlan999 ip address 172.16.1.5 255.255.255.0 ipv6 address 2A02:XXXX:XXXX:1::5/64 ! ip default-gateway 172.16.1.1 ! no ip http server no ip http secure-server ip ssh time-out 60 ip ssh source-interface Vlan999 ip ssh version 2 ! logging host 172.16.2.10 logging host ipv6 2A02:XXXX:XXXX:2::A ! ! ! ! ! line con 0 line vty 0 4 session-timeout 60 exec-timeout 15 0 logging synchronous transport input ssh transport output none line vty 5 15 session-timeout 60 exec-timeout 15 0 logging synchronous transport input ssh transport output none ! ntp server 172.16.1.1 ! end switch#Just noticed your using a Realtek ethernet port.
-
From the thread he linked to.. He doesn't have the one port in trunk
"OP also indicates that desired configuration is to trunk both ports (meaning Gi0/2 is misconfigured as an access port, as shown in the show interface status output posted above)."
So yeah could see how he is having problems..
That switch is 10/100 - ugghhh... Dude get a 40$ 8 port gig switch that does vlans.. And doesn't seem like you need all the ports.. From that thread all your other ports are off..
If you want to test if your trunk is working connected to pfsense, then wire something to one of the ports on your switch and put that port in access mode in the vlan you want to be in.
-
@johnpoz said in VLANs, What am I doing wrong?:
interface gigabitethernet5
description "sg4860 WLan and vlans"
switchport trunk allowed vlan add 3-4,6-7,19
switchport trunk native vlan 2A couple of things:
- Your screen shot shows you've created VLAN's 10, 20 and 99, but you're only allowing VLAN's 3, 4, 6, 7, and 19 over the trunk, which is why nothing's passing.
- A trunk needs to have the same native vlan on both ends. Since it can't be changed on the PFsense side, you'll need to remove the "switchport trunk native vlan 2" line.
- Also, I don't see the switchport mode set, so it's unclear whether the port is even acting as a trunk at this point.
Here's the config you're looking for:
description "sg4860 WLan and vlans"
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 10,20,99
switchport mode trunk -
@marvosa said in VLANs, What am I doing wrong?:
switchport trunk encapsulation dot1q
If the switch is that old the encapsulation would be ISL, good spot @marvosa
-
From the thread he linked to the g2 port he has connected to pfsense is access in vlan 1
Gi0/2 connected 1 a-full a-1000 10/100/1000BaseTX SFPSo yeah no wonder only thing working is the untagged network..
@marvosa I suggest you re read the thread, and who is having an issue.. I sure and the F am not ;) And I have the vlans I want on that trunk ;) hehehe
What I posted was an example for the OP ;)
-
lol I just looked at the post on the Cisco forum and a guy I work with replied to it.
-
@nogbadthebad good spot to @marvosa ?? Maybe both of you need to reread the thread.
I do not need to call out dotq in my config on the port.. Please reread and pay attention that my post for a config was an example.. Trying to get the OP to post his config.
-
@johnpoz said in VLANs, What am I doing wrong?:
@nogbadthebad good spot to @marvosa ?? Maybe both of you need to reread the thread.
I do not need to call out dotq in my config on the port.. Please reread and pay attention that my post for a config was an example.. Trying to get the OP to post his config.
Wasn't saying an issue with your config, it may have been an issue with the OP.
I don't have switchport trunk encapsulation dot1q in my config either.
-
Read @marvosa post - he is highly confused to what is going on ;)
He is confusing the OP stuff and my "example" post ;)
-
@johnpoz Bah... I was going to say the bottom line is the OP has his trunk port misconfigured, but after re-reading the thread, I noticed you posted that... and not the OP... smh.
Either way, re-verifying the config on his trunk port is still a valid step. I would also verify the config on the access ports, which we could help with if we could see the config as @johnpoz suggested.
-
From the link he posted - yeah the port connected to pfsense g2 is just access.. So no vlans are going to work.. And not sure how he would even be getting any ips via dhcp that is for sure.. Not from pfsense.
-
For simplicity, I set the ports to only use VLAN 99:
cisco#show vlan VLAN Name Status Ports ---- -------------------------------- --------- ------------------------------- 1 default active 10 IOT active 20 LCHR active 99 MGMT active Fa0/2, Gi0/2 100 BLACKHOLE active Fa0/1, Fa0/3, Fa0/4, Fa0/5 Fa0/6, Fa0/7, Fa0/8, Fa0/9 Fa0/10, Fa0/11, Fa0/12, Fa0/13 Fa0/14, Fa0/15, Fa0/16, Fa0/17 Fa0/18, Fa0/19, Fa0/20, Fa0/21 Fa0/22, Fa0/23, Fa0/24, Gi0/1 1002 fddi-default act/unsup 1003 token-ring-default act/unsup 1004 fddinet-default act/unsup 1005 trnet-default act/unsup VLAN Type SAID MTU Parent RingNo BridgeNo Stp BrdgMode Trans1 Trans2 ---- ----- ---------- ----- ------ ------ -------- ---- -------- ------ ------ 1 enet 100001 1500 - - - - - 0 0 10 enet 100010 1500 - - - - - 0 0 20 enet 100020 1500 - - - - - 0 0 99 enet 100099 1500 - - - - - 0 0 100 enet 100100 1500 - - - - - 0 0 1002 fddi 101002 1500 - - - - - 0 0 1003 tr 101003 1500 - - - - - 0 0 1004 fdnet 101004 1500 - - - ieee - 0 0 1005 trnet 101005 1500 - - - ibm - 0 0 Remote SPAN VLANs ------------------------------------------------------------------------------ Primary Secondary Type Ports ------- --------- ----------------- ------------------------------------------cisco#show ip int br Interface IP-Address OK? Method Status Protocol Vlan1 unassigned YES manual up down FastEthernet0/1 unassigned YES unset administratively down down FastEthernet0/2 unassigned YES unset up up FastEthernet0/3 unassigned YES unset administratively down down FastEthernet0/4 unassigned YES unset administratively down down FastEthernet0/5 unassigned YES unset administratively down down FastEthernet0/6 unassigned YES unset administratively down down FastEthernet0/7 unassigned YES unset administratively down down FastEthernet0/8 unassigned YES unset administratively down down FastEthernet0/9 unassigned YES unset administratively down down FastEthernet0/10 unassigned YES unset administratively down down FastEthernet0/11 unassigned YES unset administratively down down FastEthernet0/12 unassigned YES unset administratively down down FastEthernet0/13 unassigned YES unset administratively down down FastEthernet0/14 unassigned YES unset administratively down down FastEthernet0/15 unassigned YES unset administratively down down FastEthernet0/16 unassigned YES unset administratively down down FastEthernet0/17 unassigned YES unset administratively down down FastEthernet0/18 unassigned YES unset administratively down down FastEthernet0/19 unassigned YES unset administratively down down FastEthernet0/20 unassigned YES unset administratively down down FastEthernet0/21 unassigned YES unset administratively down down FastEthernet0/22 unassigned YES unset administratively down down FastEthernet0/23 unassigned YES unset administratively down down FastEthernet0/24 unassigned YES unset administratively down down GigabitEthernet0/1 unassigned YES unset administratively down down GigabitEthernet0/2 unassigned YES unset up up@johnpoz The reason why this is a 10/100 is because a) it was free, and b) it's strictly for IOT shit that doesn't need anything faster. I'm using it to learn with. I have a second gbe switch that I use for my actual network. I've also swapped the AP for my laptop and VLANs still refuse to work, so either the switch config is wrong or PFSense is configured wrong. But from what I can tell, everything is correct (as I did set Gi0/2 to trunk mode after posting in the Cisco forum)
@NogBadTheBad What's wrong with Realtek? I understand that they're not great, but according to the PFSense docs, re# NICs should work with VLANs:
Ethernet interfaces with VLAN hardware support:ae(4), age(4), alc(4), ale(4), bce(4), bge(4), bxe(4), cxgb(4), cxgbe(4), em(4), igb(4), ixgb(4), ixgbe(4), jme(4), msk(4), mxge(4), nxge(4), nge(4), re(4), sge(4), stge(4), ti(4), txp(4), vge(4)
It also looks like you set the IP address/default gateway for vlan999. Stupid question, but is that for SSH access? When I started messing with VLANs on this switch, SSH stopped working so I've been having to use a console cable..
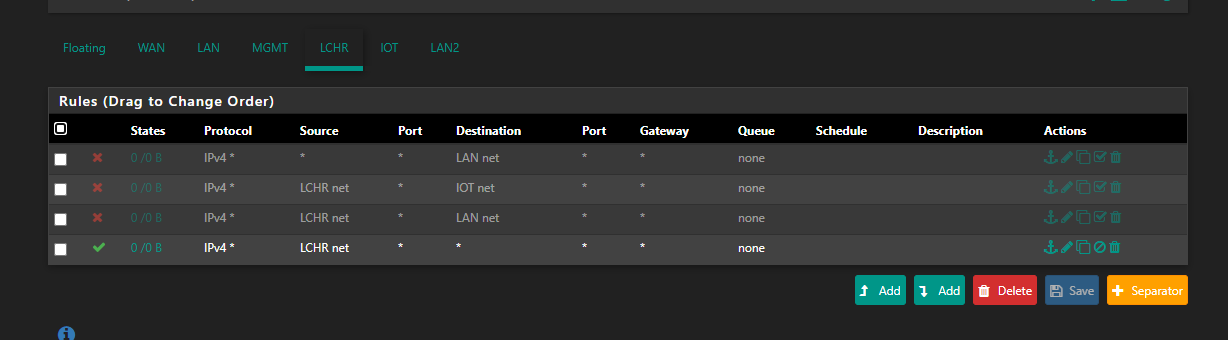
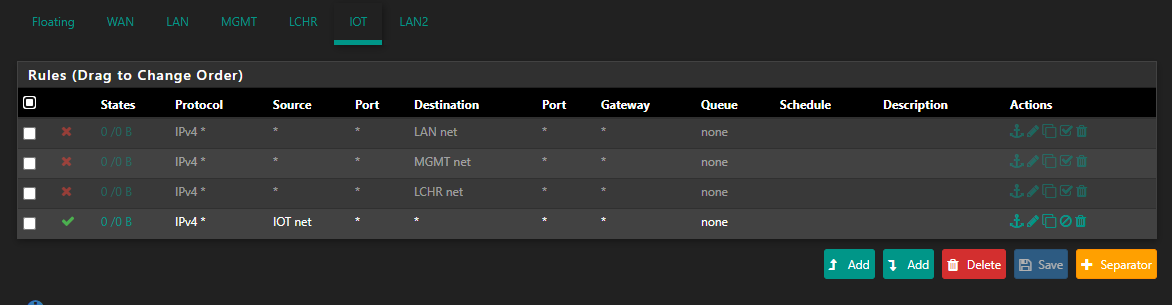
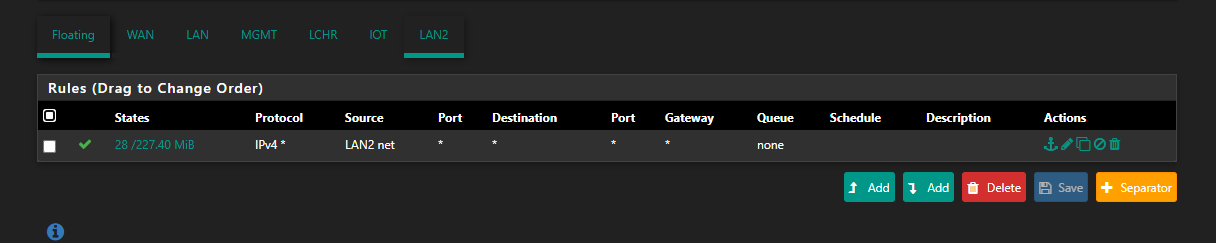
@netblues I only posted the firewall rules for one of the NICs because they're all the same:
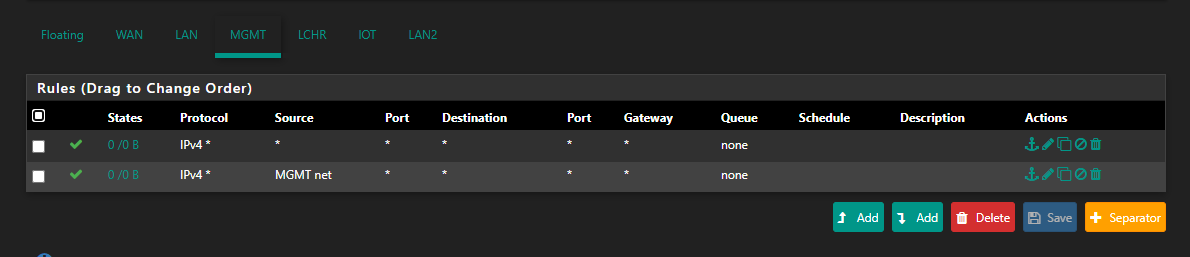 (I added the * -> * rule before reading your post but after making my post with the rules to see if it would make any difference. Spoiler alert, it doesn't.)
(I added the * -> * rule before reading your post but after making my post with the rules to see if it would make any difference. Spoiler alert, it doesn't.)
-
How do you think anything would work for vlans if you don't have the port connected to pfsense in trunk?
For vlans to work on pfsense. To talk to the other vlans. They have to be allowed on the port that is connected to pfsense.
I take it that is g2? Where is the config showing its trunked, and allowing the vlans you want to use?
From your latest showing - only vlan 99 is allowed. Which seems to be native untagged, so pfsense would see it on the native interface.
So sure your laptop in also in vlan 99, fa2 I take it.. Would be able to talk to any vlan IP on pfsense with your rules.
Does your laptop get an IP? Please post the config of the interfaces F2 and G2..
-
@johnpoz Here's a super basic image of my actual network:
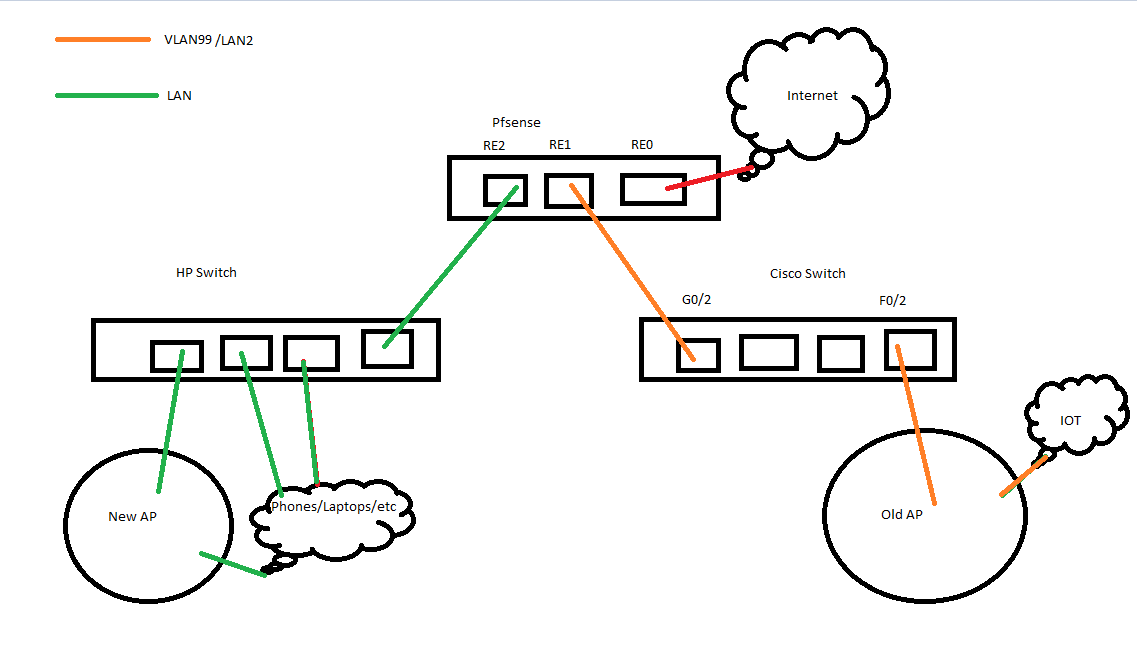
I do I have VLAN99/LAN2 (RE1) connected to G0/2 on the Cisco switch and F0/2 connected to the AP (or my laptop when I'm testing whether DHCP works or not).I think that answers your questions? Everything is wired up correctly, LAN2 is only active because it's the only interface in Pfsense I can get to work.
I don't fully understand tagged/untagged, or what you're referencing when you say native. This is what I'm trying to learn.
cisco#show running-config interface g0/2 Building configuration... Current configuration : 170 bytes ! interface GigabitEthernet0/2 switchport access vlan 99 switchport trunk encapsulation dot1q switchport trunk allowed vlan 1-99,101-4094 switchport mode access end cisco#show running-config interface f0/2 Building configuration... Current configuration : 156 bytes ! interface FastEthernet0/2 switchport access vlan 99 switchport trunk encapsulation dot1q switchport trunk allowed vlan 99 switchport mode access endPosting this now so I can edit in a few to see if DHCP works for my laptop.
Update: I disabled LAN2 and it DHCP failed to work.
-
@apathia said in VLANs, What am I doing wrong?:
switchport access vlan 99
switchport trunk encapsulation dot1qThat is wrong.. Which is it access or trunk?
Its either a trunk port, that carry vlan (tags).. Or its an access port that is not tagged or native.
Since your trying to use your re2 port with untagged vlan (your vlan 99 I believe).. Then your configuration should be trunk, with a native vlan set.. See my above example..
interface gigabitethernet5 description "sg4860 WLan and vlans" switchport trunk allowed vlan add 3-4,6-7,19 switchport trunk native vlan 2This carries vlans 3,4,6,7 and 19 as TAGGED, ie vlan in pfsense. And untagged.. The native interface.. So for example here are my interfaces from pfsense where I am currently using some of those vlans. (4 and 6)
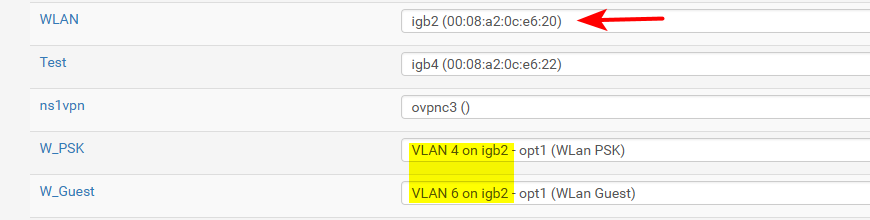
In this case traffic that is in vlan 4 or 6 is tagged, and pfsense sees the tags on my igb2, and knows that traffic is for vlan 4 or 6. While any traffic that is untagged.. in my case on the switch that is vlan 2.. Pfsense just see that traffic for the interface igb2 directly.. It is still a vlan on my switch.. Its just pfsense doesn't know that it is, and its just native traffic (untagged traffic)..
You can run many vlans on a port that are tagged. Cisco calls this a trunk port. If you also want to carry upto 1 vlan that is untagged, that is a native vlan for pfsense on a trunk port.
On a port in cisco where is is not tagged traffic, that would be a access port.. And the device connected that port doesn't see any tags.. This is where you would connect say a pc, or laptop or iot device. When you send traffic to your AP.. That will have say different SSIDs on different vlans. Then those are tagged, ie a trunk port.