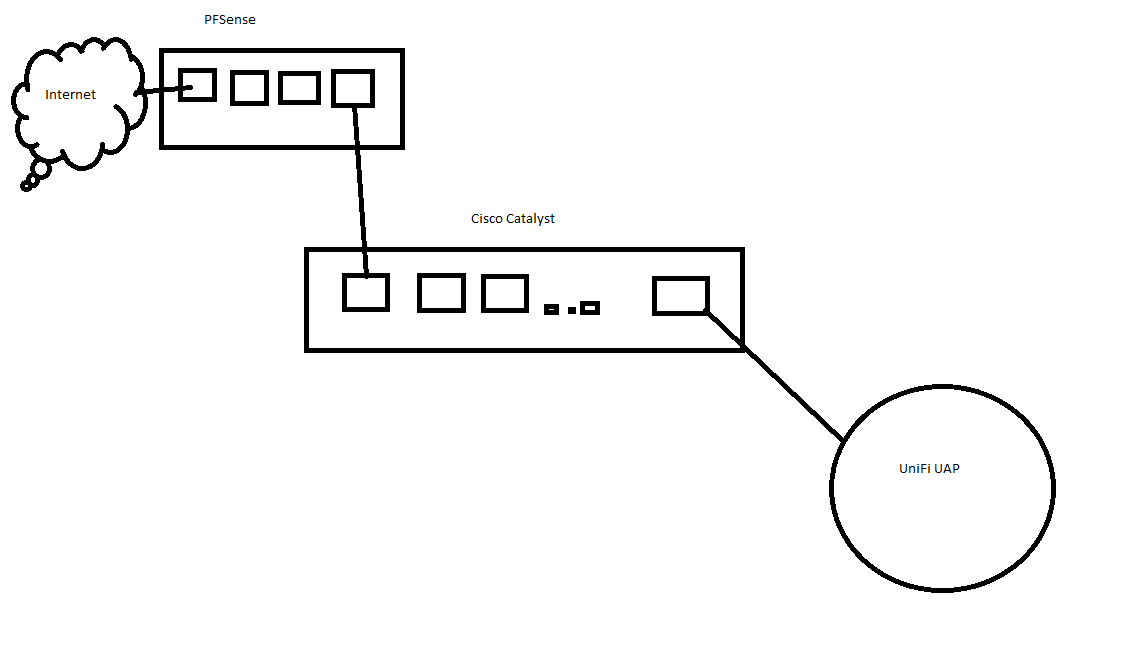
VLANs, What am I doing wrong?
-
While that would allow vlans to work... Are you using vlan 1 as native?
You seem to be allowing everything but vlan 100.. Even 1.. Which is never really tagged. This is the default vlan of switches.
I would change your allowed to be only vlans your actually using.. Or will use shortly.
But if you want to talk the network you have on re1, lan2 - you need to set that as native (untagged).. If your saying everything is working, I take it that is just whatever your using as vlan 1 on your switch?
Another option is just not use any untagged network on this interface. Set lan2 to be a vlan.. But unless you have gotten deep into the weeds with unifi, AP management IP needs to on a untagged vlan. They support vlans - I find it highly unlikely you have set that up.
Here this might help on what I mean by native
https://networklessons.com/switching/802-1q-native-vlan-cisco-ios-switchSince you seem to be using a different physical switch for network attached to re2, vlan 1 as your native is ok. But you need to make sure you understand tag vs untagged, and when they are and when they are not tagged.
-
Agreed. If you're essentially going to allow all VLANs, I would just remove the switchport trunk allowed command altogether.
Although, best practice is to only allow the VLANs that are in use over the trunk.
-
@johnpoz I think I get it now. LAN2/RE1 is on the physical interface so it's "untagged". The switch throws this on VLAN1 as that's the default VLAN for anything without a tag?
So essentially, the switch acts as if every packet is tagged, either explicitly or not. Non-explicit packets are thrown on the Native VLAN?
If that's what it means then that does make sense. I also only used sw tr all vlan all because I was initially having issues with adding specific VLANs although that may have been due to having g0/2 misconfigured as access instead of trunk.
Now that I have VLANs working, my AP is working just fine and assigning devices to the correct subnets.
Thanks for all the help!
My current config, btw:
cisco#show running-config int g0/2 Building configuration... Current configuration : 159 bytes ! interface GigabitEthernet0/2 description "rooter" switchport trunk encapsulation dot1q switchport trunk allowed vlan 10,20,99 switchport mode trunk end cisco#show running-config int f0/2 Building configuration... Current configuration : 154 bytes ! interface FastEthernet0/2 description "Wlan" switchport trunk encapsulation dot1q switchport trunk allowed vlan 10,20,99 switchport mode trunk end -
Yeah that looks better.. And is fine if your using vlan 1 as native.
I don't personally use vlan 1, this is habit from corp experience where vlan 1 is always disabled. And management lan is set to some other vlan.
But there is really nothing technically wrong with doing that. But if your going to say at some point connect your other port into the same physical switch.. And run a network on the physical port along with vlans as well on that other port.
You will need to understand how to change the native vlan on a trunk port, along with also understanding what pvid is. This where you set what vlan a switch puts untagged traffic into when it sees ingress into the port.
Your old school cisco for sure can help you with understanding these concept. Cisco terms might be a bit different than other makers.. In general if you know what a tag or untagged vlan, and how the switch handles ingress traffic without a tag you will be cooking with gas ;)
Glad you finally got it working how you want.
For your next assignment ;) If you choose to accept it ;)
Figure out how to put your AP management IP onto a tagged vlan..
And how to change your native vlan g2 to something other than vlan1.. -
Figure out how to put your AP management IP onto a tagged vlan..
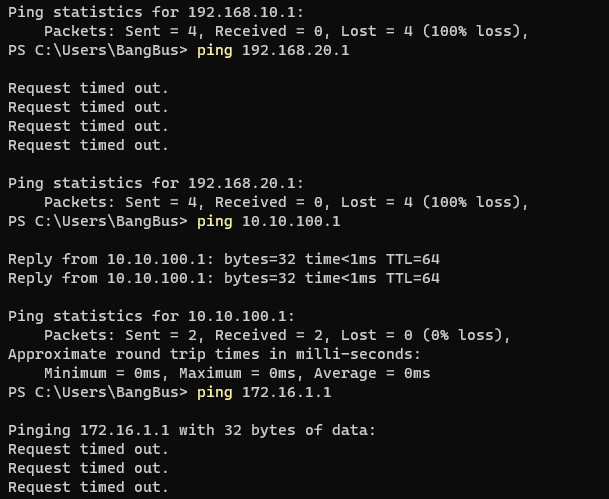
You mean this?
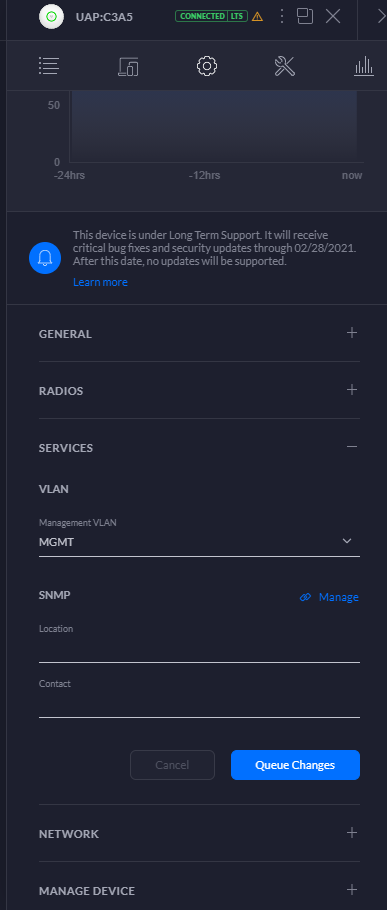
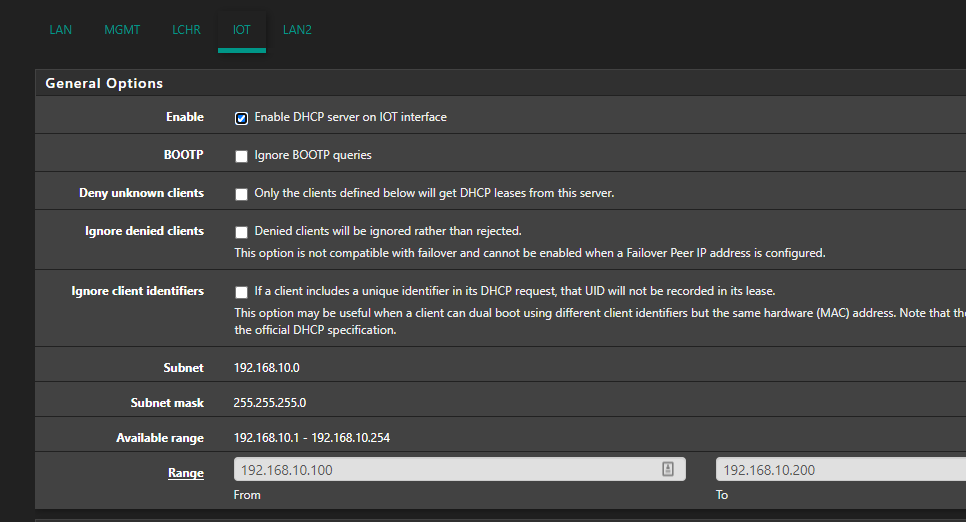
It was why I created the MGMT VLAN in the first place lol.. Once I figured out how to actually get the VLANs across the switch, the rest was relatively easy. Took me a bit to figure out why the AP would keep going offline when I switched it to the MGMT VLAN but I quickly clued into the PFSense rules, which again is what my plan was in the first place.
And how to change your native vlan g2 to something other than vlan1..
cisco#show running-config int g0/2 Building configuration... Current configuration : 191 bytes ! interface GigabitEthernet0/2 description "rooter" switchport trunk encapsulation dot1q switchport trunk native vlan 2 switchport trunk allowed vlan 10,20,99 switchport mode trunk end cisco# -
Do you have a vlan 2? Did you create one? ;)
Or just copy that command from my example ;)
But see how fast it clicks into place once you get what tagged and untagged mean.
Welcome to the world of vlans! Now you just need a switch that isn't 20 years old, and does gig on all its ports ;) I would go insane with 100mbps.. Be like watching paint dry trying to move files around.. Gig is even a bottleneck, I connected my pc to my nas via 2.5gbps so could move the files back and forth when I work on them.. ;)
But that switch is great for a lab.. How much juice does it draw? You might not want to leave it on 24/7 - those old things use to suck up some juice for sure.. 100w?
-
@johnpoz
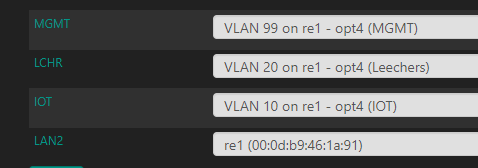
I do now:
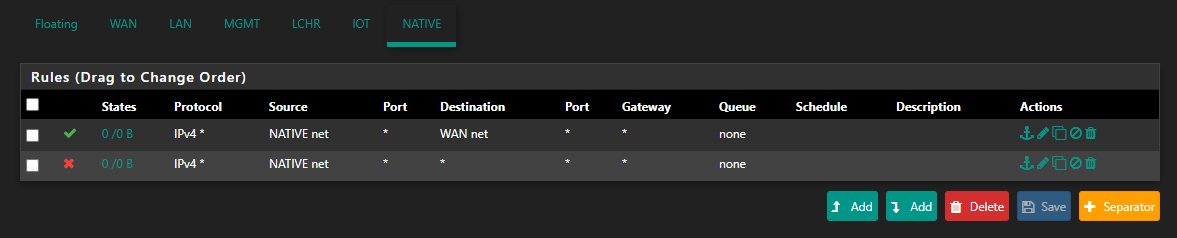
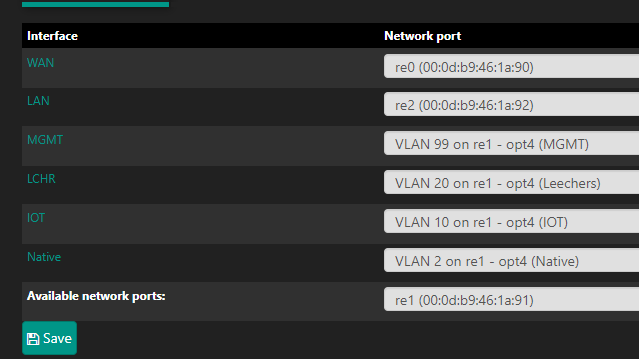
This I presume means that if I enable another port on the cisco, remove it from the BlackHole VLAN, and plug something in then it'll default to VLAN 2?
RE2/LAN is connected to an HP 2920-24G-PoE+ Switch. Not new, but not 10/100 either. This is what I use as my main network. I plan on getting VLANs set up on it too, but I also don't want to accidentally take myself offline when I mess things up so I want a decent handle on VLANs before I do anything with it. My "file server" is currently my media center PC so I don't have to worry about network transfer speeds too much as I play everything off it anyway. I do have an actual server (Intel something, can't remember which), but that thing not only sounds like a jet engine, but it also drastically increases my electric bill.
I don't think either of the switches suck up much juice, the HP switch is currently reporting ~10W from 3 POE devices connected to it so I can't imagine it's too much. Last months electricity bill was surprisingly on par with the previous years, despite me now working from home and having these two switches. I will say though, the Cisco is whisper quiet compared to the HP.
I might eventually chain the switches, Router --> HP --> Cisco, but I want to get a good handle on the VLANs and configuring things before doing that.
-
Does your HP also do vlans? If not I would do it that way I would do
router - cisco - hp
You can put a dumb switch downstream of a smart switch, and just everything on that dumb switch will just be 1 vlan.
What specific models of these switches? Can look up watch the cisco pulls. Is it 2950T-24, those are not all that bad only 30W max..
edit:
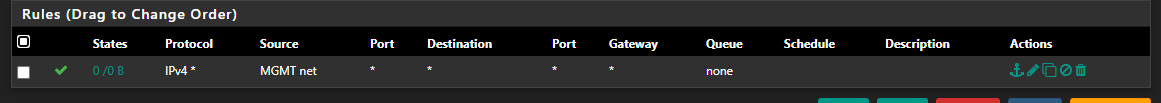
What do you want that rule to do? Your only going to be able to go to wan net, that doesn't allow you to do really anything.. Your not even allowing that network to query pfsense for dns.wan net is not the internet, its just the network your wan is attached to..
-
Is that a Unifi AP? If so, you can select an interface or VLAN when you configure it, though you can also move between one or the other later, as I had to do recently, when my pfsense firewall died. On my AP, the management interface is on my main LAN.
-
@johnpoz It's a WS-C3560-24PS-E, so looks like it it's 400+ W. The HP is an J9727A 2920-24G-PoE+ Switch, so it's also a managed switch. I think combined, they pull 800W max/
My goal with that rule was to restrict traffic, I was lazy and didn't want to add a separate rule restricting to the different VLANs but I guess that's not a thing.
@JKnott Yeah it is, I initially had it set up with defaults but now that I have a management VLAN, I've been moving appropriate devices over to it.
-
Well power MAX can for sure be misleading..
Great device to add to your tool belt, if you have any care to what devices draw.. Is a kill-a-watt meter..
Or a smart plug with power reading.. So you can plug a device in, and see what it actually draws.. Say leave it on the plug for 24 hours min.. And try and atleast use it a bit like you think you normally would..
Cost of elect can vary quite a bit.. But at the national average of like 12cents per kwh.. A 100W will cost you 100 Bucks a year. Not counting delivery cost of the elect as well, and taxes on that etc.. so going to be 100+ a year to run something that sucks 100w if left on 24/7/365
I have gotten pretty into how much something draws, even before I went solar.. So Im the blue line - guess when I went solar ;)
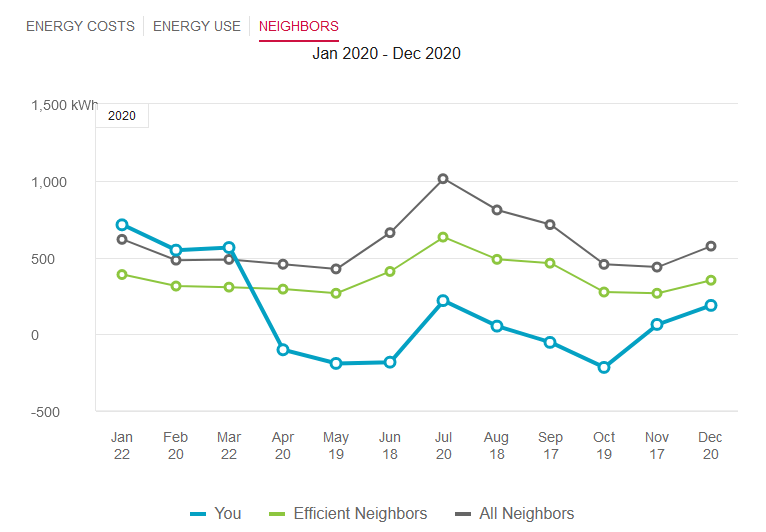
I always use to be above even my non efficient neighbors (all the networking/computer toys) ;) The part I like the most is where I am under the 0... This is where I produced more than I used.. Which is the goal..