OpenVPN Unable to contact Deamon, Service not running
-
Dear Netgate Experts,
i have installed PFSense Version 2.4.5, then i created OpenVPN Server after im done with the configuration i found the following error.
{error} Unable to contact Deamon
0 Service not runningi checked the System Logs and found the following
Jan 22 00:30:37 openvpn 70012 Options error: Unrecognized option or missing or extra parameter(s) in /var/etc/openvpn/server1.conf:45: 10.49.1.0 (2.4.9)
Jan 22 00:30:37 openvpn 70012 Use --help for more information.
i appreciate any support to solve the problem.
Thank you so much in advance. -
@ali-ghabsha said in OpenVPN Unable to contact Deamon, Service not running:
solve the problem
Can you show it ( /var/etc/openvpn/server1.conf ) first ?
-
@gertjan excuse me might you guide me how to do that, i don't really have experience with the command line in PFSense.
Thank you
-
i have disabled the openvpn server that i have perviously created then i created a new one using the Wizard which it has also created the appropriate firewall rlues, after that i deleted the old server that i disabled with the associated rules in the firewall, and i got the following in the system logs of the openvpn
Jan 23 02:18:26 openvpn 6363 TUN/TAP device ovpns2 exists previously, keep at program end
Jan 23 02:18:26 openvpn 6363 TUN/TAP device /dev/tun2 opened
Jan 23 02:18:26 openvpn 6363 /sbin/ifconfig ovpns2 172.16.1.1 172.16.1.2 mtu 1500 netmask 255.255.255.0 up
Jan 23 02:18:26 openvpn 6363 /usr/local/sbin/ovpn-linkup ovpns2 1500 1621 172.16.1.1 255.255.255.0 init
Jan 23 02:18:26 openvpn 6363 UDPv4 link local (bound): [AF_INET]192.168.0.2:1194
Jan 23 02:18:26 openvpn 6363 UDPv4 link remote: [AF_UNSPEC]
Jan 23 02:18:26 openvpn 6363 Initialization Sequence Completed
Jan 23 02:19:53 openvpn 23852 OpenVPN 2.4.9 amd64-portbld-freebsd11.3 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on May 4 2020
Jan 23 02:19:53 openvpn 23852 library versions: OpenSSL 1.0.2u-freebsd 20 Dec 2019, LZO 2.10
Jan 23 02:19:53 openvpn 23961 WARNING: using --duplicate-cn and --client-config-dir together is probably not what you want
Jan 23 02:19:53 openvpn 23961 GDG: problem writing to routing socket
Jan 23 02:19:53 openvpn 23961 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Jan 23 02:19:53 openvpn 23961 TUN/TAP device ovpns2 exists previously, keep at program end
Jan 23 02:19:53 openvpn 23961 TUN/TAP device /dev/tun2 opened
Jan 23 02:19:53 openvpn 23961 ioctl(TUNSIFMODE): Device busy (errno=16)
Jan 23 02:19:53 openvpn 23961 /sbin/ifconfig ovpns2 172.16.1.1 172.16.1.2 mtu 1500 netmask 255.255.255.0 up
Jan 23 02:19:53 openvpn 23961 /usr/local/sbin/ovpn-linkup ovpns2 1500 1621 172.16.1.1 255.255.255.0 init
Jan 23 02:19:54 openvpn 23961 UDPv4 link local (bound): [AF_INET]192.168.0.2:1194
Jan 23 02:19:54 openvpn 23961 UDPv4 link remote: [AF_UNSPEC]
Jan 23 02:19:54 openvpn 23961 Initialization Sequence Completed
Jan 23 02:28:10 openvpn 23961 event_wait : Interrupted system call (code=4)
Jan 23 02:28:10 openvpn 23961 /usr/local/sbin/ovpn-linkdown ovpns2 1500 1621 172.16.1.1 255.255.255.0 init
Jan 23 02:28:10 openvpn 23961 SIGTERM[hard,] received, process exiting
Jan 23 02:28:10 openvpn 34420 OpenVPN 2.4.9 amd64-portbld-freebsd11.3 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on May 4 2020
Jan 23 02:28:10 openvpn 34420 library versions: OpenSSL 1.0.2u-freebsd 20 Dec 2019, LZO 2.10
Jan 23 02:28:10 openvpn 34755 WARNING: using --duplicate-cn and --client-config-dir together is probably not what you want
Jan 23 02:28:10 openvpn 34755 NOTE: your local LAN uses the extremely common subnet address 192.168.0.x or 192.168.1.x. Be aware that this might create routing conflicts if you connect to the VPN server from public locations such as internet cafes that use the same subnet.
Jan 23 02:28:10 openvpn 34755 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Jan 23 02:28:10 openvpn 34755 TUN/TAP device ovpns2 exists previously, keep at program end
Jan 23 02:28:10 openvpn 34755 TUN/TAP device /dev/tun2 opened
Jan 23 02:28:10 openvpn 34755 /sbin/ifconfig ovpns2 172.16.1.1 172.16.1.2 mtu 1500 netmask 255.255.255.0 up
Jan 23 02:28:10 openvpn 34755 /usr/local/sbin/ovpn-linkup ovpns2 1500 1621 172.16.1.1 255.255.255.0 init
Jan 23 02:28:10 openvpn 34755 UDPv4 link local (bound): [AF_INET]192.168.0.2:1194
Jan 23 02:28:10 openvpn 34755 UDPv4 link remote: [AF_UNSPEC]
Jan 23 02:28:10 openvpn 34755 Initialization Sequence Completed
Jan 23 02:32:13 openvpn 34755 event_wait : Interrupted system call (code=4)
Jan 23 02:32:13 openvpn 34755 /usr/local/sbin/ovpn-linkdown ovpns2 1500 1621 172.16.1.1 255.255.255.0 init
Jan 23 02:32:13 openvpn 34755 SIGTERM[hard,] received, process exiting
Jan 23 02:32:13 openvpn 51755 OpenVPN 2.4.9 amd64-portbld-freebsd11.3 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on May 4 2020
Jan 23 02:32:13 openvpn 51755 library versions: OpenSSL 1.0.2u-freebsd 20 Dec 2019, LZO 2.10
Jan 23 02:32:13 openvpn 51887 WARNING: using --duplicate-cn and --client-config-dir together is probably not what you want
Jan 23 02:32:13 openvpn 51887 NOTE: your local LAN uses the extremely common subnet address 192.168.0.x or 192.168.1.x. Be aware that this might create routing conflicts if you connect to the VPN server from public locations such as internet cafes that use the same subnet.
Jan 23 02:32:13 openvpn 51887 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Jan 23 02:32:13 openvpn 51887 TUN/TAP device ovpns2 exists previously, keep at program end
Jan 23 02:32:13 openvpn 51887 TUN/TAP device /dev/tun2 opened
Jan 23 02:32:13 openvpn 51887 /sbin/ifconfig ovpns2 172.16.1.1 172.16.1.2 mtu 1500 netmask 255.255.255.0 up
Jan 23 02:32:13 openvpn 51887 /usr/local/sbin/ovpn-linkup ovpns2 1500 1621 172.16.1.1 255.255.255.0 init
Jan 23 02:32:13 openvpn 51887 UDPv4 link local (bound): [AF_INET]192.168.0.2:1194
Jan 23 02:32:13 openvpn 51887 UDPv4 link remote: [AF_UNSPEC]
Jan 23 02:32:13 openvpn 51887 Initialization Sequence Completedhowever im still unable to connect the client onto the mobile phone openvpn connect shows the following:
EVENT WAIT
Server Poll Timout, Trying next remote Entry
then it keeps reconnecting. without any successful attempts. -
Hi,
Your WAN is 192.168.0.2, right ?
There is a firewall rule on the WAN interface let permits incoming traffic on port 1194, protocol UDP, like :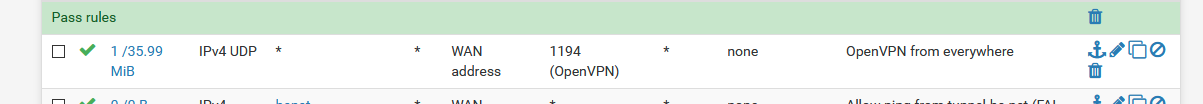
And, because you use an upstream router, this router should have a NAT rule that routs traffic from it's WAN (your real Internet IP) to the WAN IP of pfSense (again, using port 1194 - if thats the one you use for your client, protocol UDP) ?
Did you check the real Internet IP you have ? http://checkip.dyndns.com Is this the IP your OpenVPN client is using when connecting ?
Most of the connection issues can be checked with packet capturing on the WAN interface of pfSense. And no surprise, again, use UDP and port 1194 as a filter for the capturing. It should show traffic you connect your phone.
While testing, at first, shut down the Wifi of your phone.
Btw : when you restored the connection, take care of the warning in the OpenVPN log. They are pretty self explaining.
-
@gertjan thank you for replying.. Let you give a full information please might that helps.
I've a Router at my house which is configured to forward the traffic of openvpn so i configured to forward the port 1194 udp from the Wan to my pfsense which is behind the router (192.168.0.2) , I have tried the following
I've created two virtual machines and installed on them two different versions of pfsense, the first is with 2.4.3 and the second 2.4.5, and I've configured both exactly the same. Then If I try to using the 2.4.3 the openvpn works if I turn off this one and then use the one with the new version, the openvpn doesn't work, so it's a version issue, why the old version works but the new one not... Why if I upgraded from the old version to the new version the openvpn works but users behind pfsense can't access the internet.
If we check the logs we find there's an error related to the Wan interface regarding the openvpn then if we deleted the rule in the Wan related to the openvpn and created a new one the same options the users can access the internet and there won't be any more errors in the log, however no more openvpn. The openvpn will stop forever. -
@ali-ghabsha said in OpenVPN Unable to contact Deamon, Service not running:
2.4.3 the openvpn works
Be careful : when you export a config ( with the OpenVPN client EXE in the config if you use that one also ) you change the OpenVPN version used. Mixing OpenVPN client software on client and or server side can have issues.
@ali-ghabsha said in OpenVPN Unable to contact Deamon, Service not running:
the openvpn doesn't work, so it's a version issue, why the old version works but the new one no
What do you mean by doesn't work ?
I can only find this in your log :@ali-ghabsha said in OpenVPN Unable to contact Deamon, Service not running:
GDG: problem writing to routing socket
This https://community.openvpn.net/openvpn/ticket/688 ?
I don't have that GDC message :
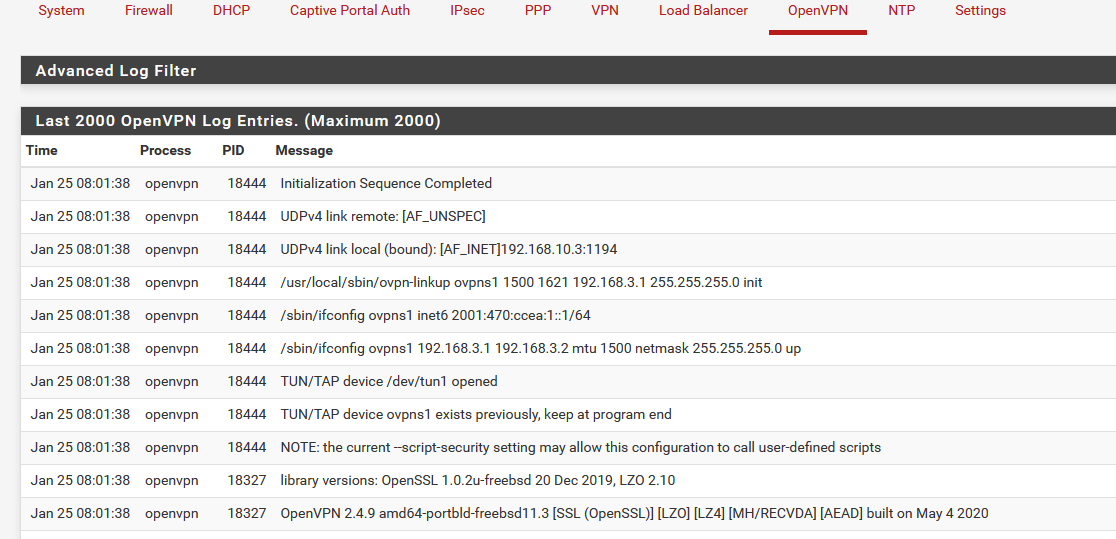
You can see it starts to listen on :
UDPv4 link local (bound): [AF_INET]192.168.10.3:1194
192.168.10.3 is my WAN interface - WAN IP - I have an ISP router in front of my pfSense.The start up shown is a clean start up of OpenVPN
This is the WAN firewall rule :
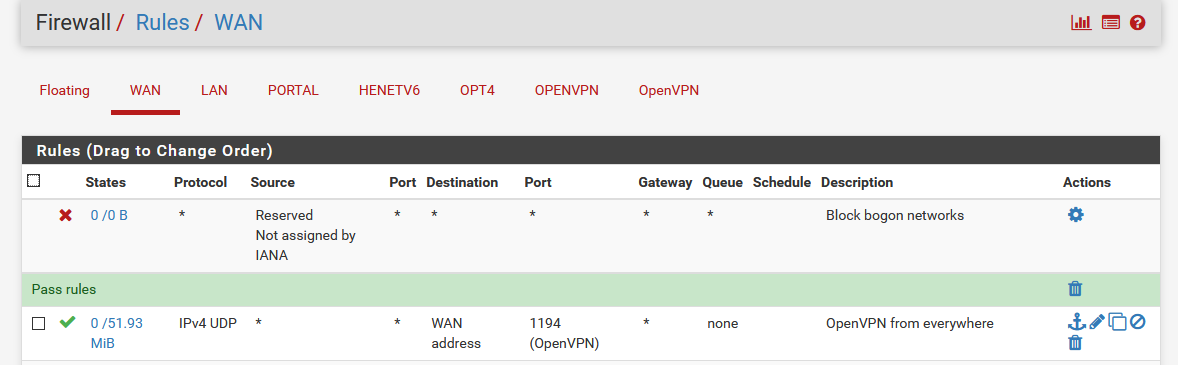
@ali-ghabsha said in OpenVPN Unable to contact Deamon, Service not running:
If we check the logs we find there's an error related to the Wan interface regarding the openvpn ....
and what about showing these errors ?
@ali-ghabsha said in OpenVPN Unable to contact Deamon, Service not running:
Why if I upgraded from the old version to the new version the openvpn works but users behind pfsense can't access the internet.
So, OpenVPN starts, there is a related firewall rule on your WAN, and devices on LAN do not have any Internet access any more.
I'm curious how you set up your system.
Adding the OpenVPN firewall rule on WAN doesn't implicate at all LAN's Internet access - OpenVPN server running, or not.
Running OpenVPN server with or without the firewall rule on WAN doesn't change OpenVPN behaviour (no messages or warnings). Without the firewall it just isn't accessible. This will not alter anything for devices on your LAN.