VPN up Gateway up - No Internet
-
@apsis-im said in VPN up Gateway up - No Internet:
@vmac right on... I thought it was worth a mention... I literally did it to myself an hour before I came to read the boards. I deleted one of the LAN to TUN firewall rules that I actually needed and mistakenly built it from one of the existing rules that had the tagging and ended up blocking unintended traffic.
NAT's there the LAN>WAN / LAN>VPN rules are as they should be; it "should" work.
Let's try to establish a known good. When these devices you're adding now aren't added to your LAN>VPN Rule are those devices able to get out? I'm assuming they are.
If this is the case I'd say it's worth taking a look at your LAN>VPN Rule (or all that's applicable o those IPs) They may have an unintended setting OR those IPs match another rule that applies before the pass rule you're expecting the IPs to use.
v/r,
JG
Edit:
You did mention the known good; sorry. just stepping through it in my head... again, I'm not that savvy.So they way I have this setup is that I created an Alias "VPN_Devices". When I want to add a device to go out of the VPN I add it's IP address to the Alias. When I do that it will reload the filter. After that is done I can then verify it is going out the VPN by doing a quick bounce to what is my ip. The devices work perfectly fine prior to me adding them to this alias. Once I add them to the alias the Internet immediately drops. Don't know if that answered your question though. It looks like this:
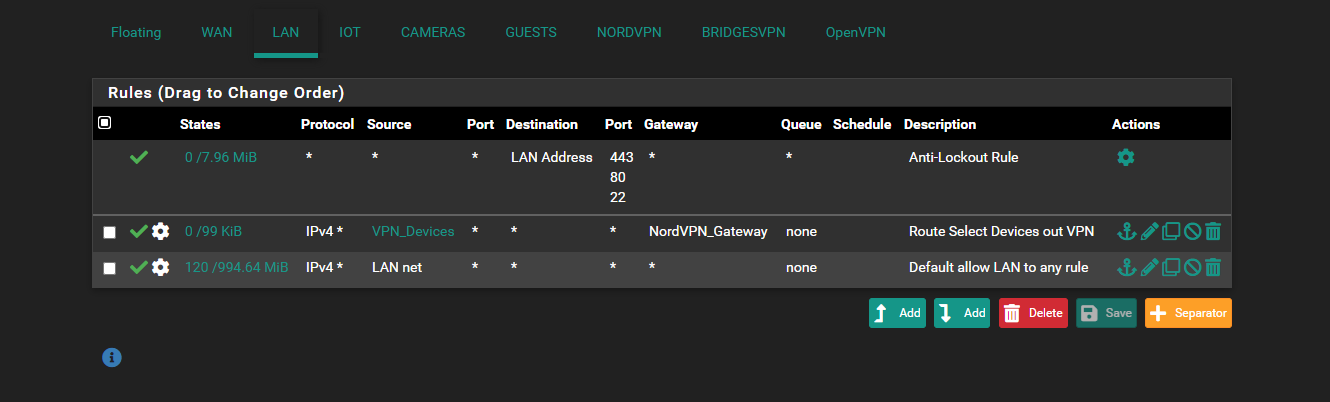
Also to you other post, no I don't have Load Balancing checked.
-
@vmac my configuration is similar (naming aside), just with a couple more tunnels and aliases to bypass/utilize the different tunnels ...
There are fewer rules than I imagined. So, with only one rule to contend with and no sticky connections we can move on...
Does your DNS lookup/Resolver/Forwarder continue to function for the VPN traffic when those devices are added to your alias? That would hamstring the test scenario you described.
does whatsmyIP simply not load? I'm going to try and recreate what you're seeing...
edit:
I'm at a loss, lol! Are we certain that the vpn_devices firewall rule is set to pass and pointed at a gateway that exists/is up? I deleted a gateway to rename it earlier today and the LAN>VPN rules that used it were set to "default"; that hosed me for a while.
-
It should. I have the DNS resolver working on all interfaces.
yes it doesn't load when I try it. Nor can I ping any IP (ex. 8.8.8.8)
I don't know what firewall rule other than the above would be necessary. The gateway that should pass it is showing up and green. Nevermind the 3rd gateway which shows down but works fine smh...
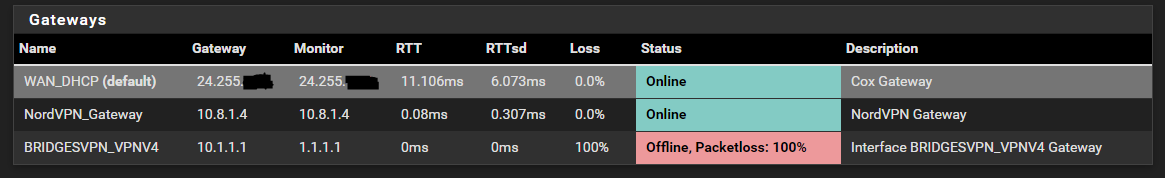
-
@vmac said in VPN up Gateway up - No Internet:
I don't know what firewall rule other than the above would be necessary. The gateway that should pass it is showing up and green. Nevermind the 3rd gateway which shows down but works fine smh...
None should be... I'm just biased by my configuration and I wanted to make it clear that that's why I had even expected more.
This is weird... your rule has states and you're not getting rejects in the logs.
I was unsuccessful in breaking my configuration in a way applicable to your situation. Someone's having a similar problem on another new post. They're not using NordVPN (wireguard), but they suspect the VPN isn't up as all the statuses indicate. They tore their configuration down to the barebones to test and still can't pass traffic.
this discussion is here if you want to follow:
https://forum.netgate.com/topic/160378/wg-not-routing-or-sending-traffic
What does the traffic shaper do? Would it play a role?
edit:
Wait; there are no states... Hmmm... gonna google stuff, lol
and his issue is not similar in anyway... wireguard isn't an openvpn service...
-
@vmac said in VPN up Gateway up - No Internet:

This does show the gateway up...
Have we verified that this is the gateway VPN _Devices rule is set to?
edit:
Duh you have... sorry.
-
Do you have alternate servers you can try? maybe there's an issue with the one your client is connected to?
-
@Apsis-IM
Yes tried multiple. -
@vmac is your traffic shaper configured? Perhaps considerations for your tunnel need appropriate configurations.
v/r
JG -
@apsis-im
I removed the shaper on both the WAN and NORDVPN and it still is blocking.
I'm at a loss too, was hoping someone had some insight on what i might need to try. -
@vmac seems we both took L's last night... I failed miserably at my little project for 10 hours straight. There's a lot of action on these boards... Someone may come through and grace this thread with some knowledge.
-
@vmac may try seeing how this plays out?
https://forum.netgate.com/topic/160257/lan-connection-drops-when-openvpn-client-connected/4
There are several apparently informed individuals helping this person out. The problem seems similar to yours.
-
@johnpoz @viragomann
Can either of you help here? -
@vmac
I don't know, how you've configured the DNS on the affected machines, but since your LAN rules don't allow DNS requests to internal servers, they can only access external ones, but must be configured to do so or you do some forwarding to an external server.
So check if you can resolve hostnames on a computer which belongs to the VPN_devices alias. -
@viragomann I'm confused what you are stating here.
Here is a copy of my current LAN rules. Doesn't the last rule allow access from any device on my LAN vLAN to any device?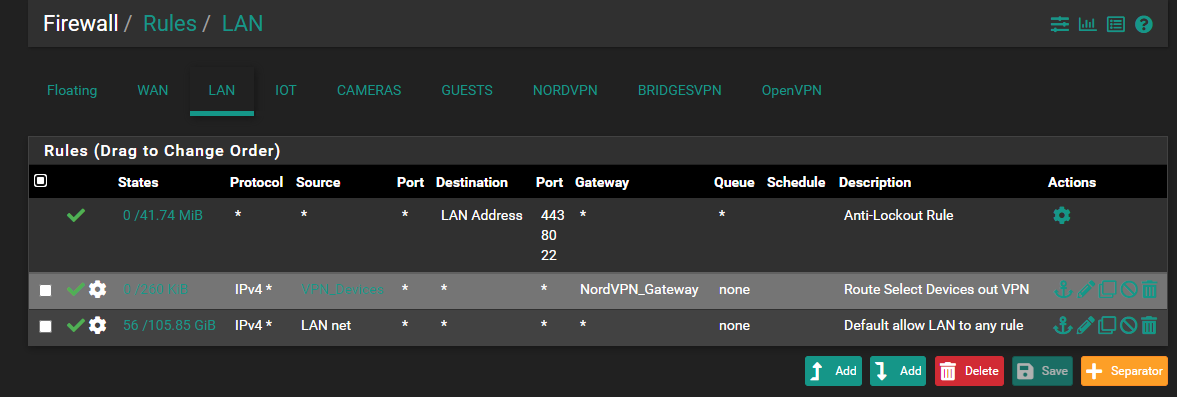
Are you stating that I need to add another rule to allow DNS traffic?
-
@vmac
Yes, it does. But this rule will never be applied, since that one above matches to any traffic and directs it to the vpn gateway.Rules are processed from the top downwards. If one matches it is applied and other rules are ignored.
Still don’t know, how you do DNS resolution. But assumed it“s done by pfSense, add a pass rule to the top of the rule set for TCP/UDP, dest. „This Firewall“, port DNS. So this ruhe only is applied for DNS access to pfSense, all other traffic is still directed to the vpn.
-
@viragomann
I'm confused as to what you mean about the order. since VPN devices would only match specific devices. However, I made the change and still can't get any Internet when VPN connected: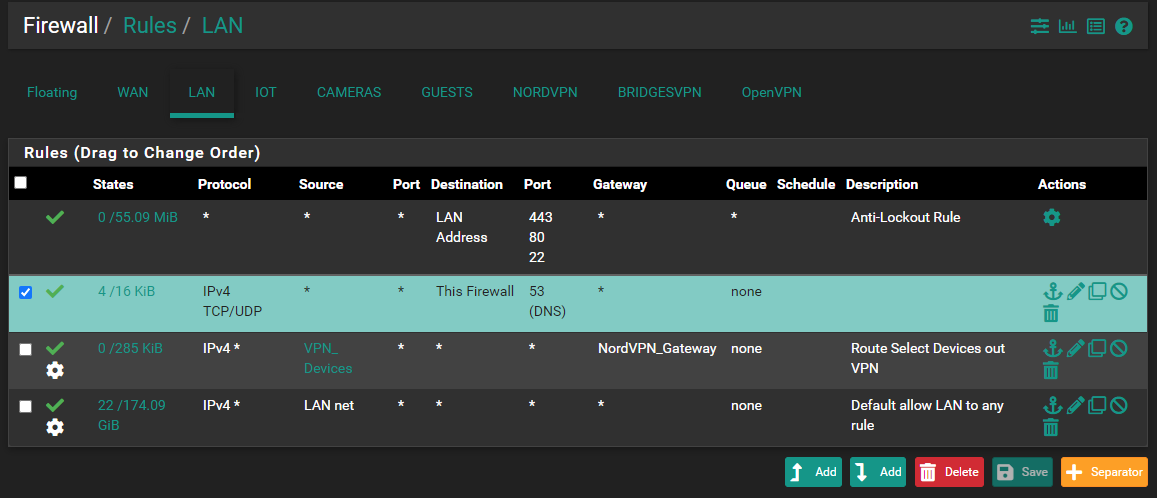
To answer your other question, I have my pfSense resolving all DNS queries:
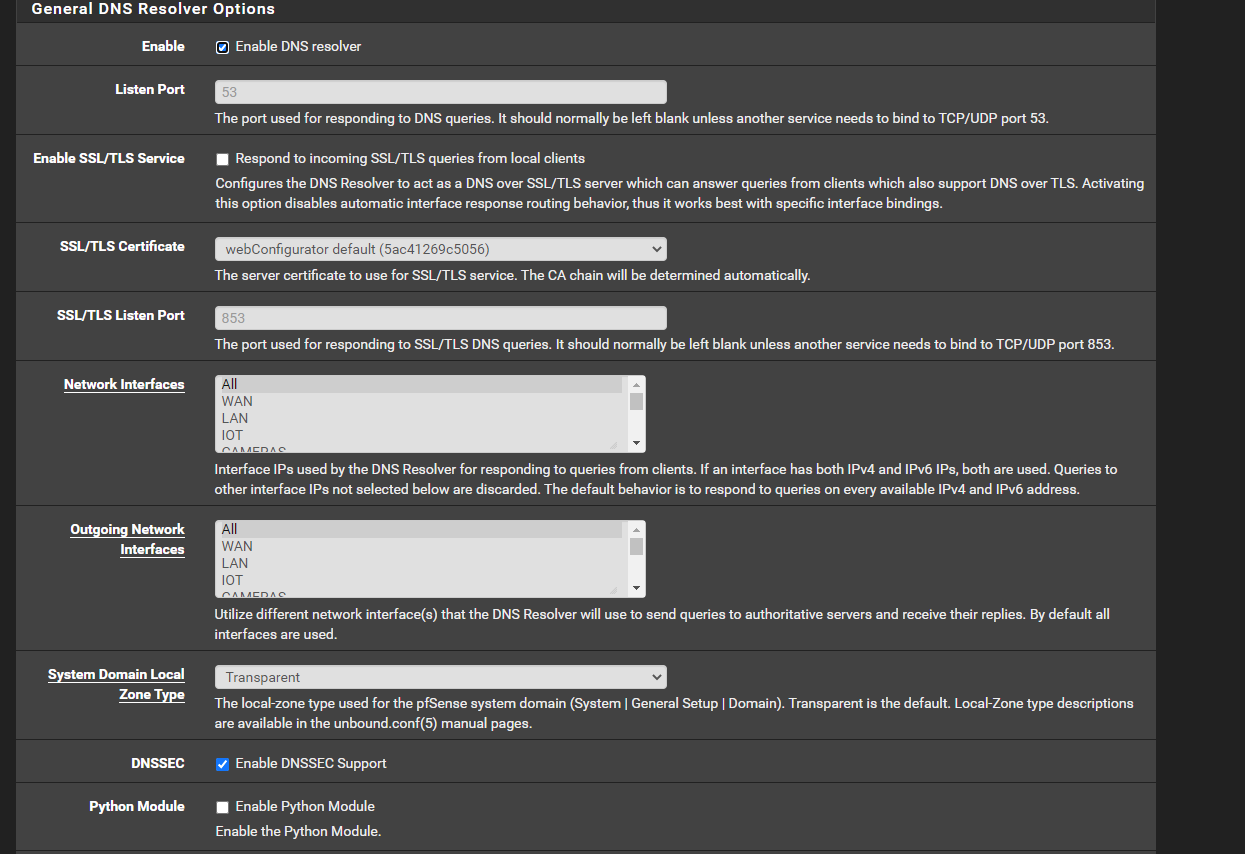
-
I'm starting to wonder if it has something to do with the Automatic Outbound NAT not working.
When I check the OpenVPN logs I see this noted:
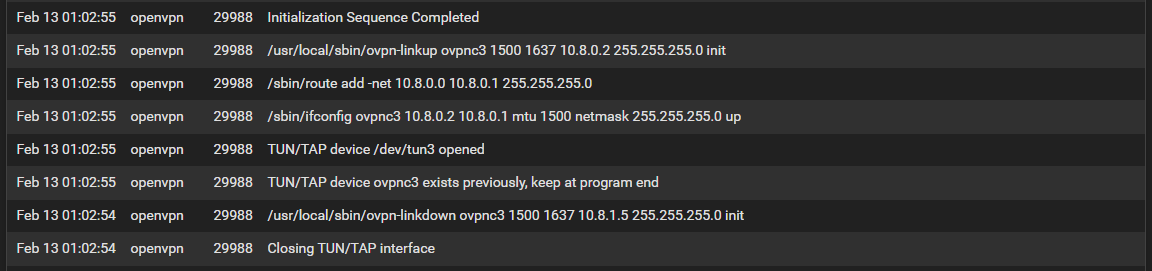
When I go to Outbound NAT I don't see this interface in the "automatic" generated outbound.
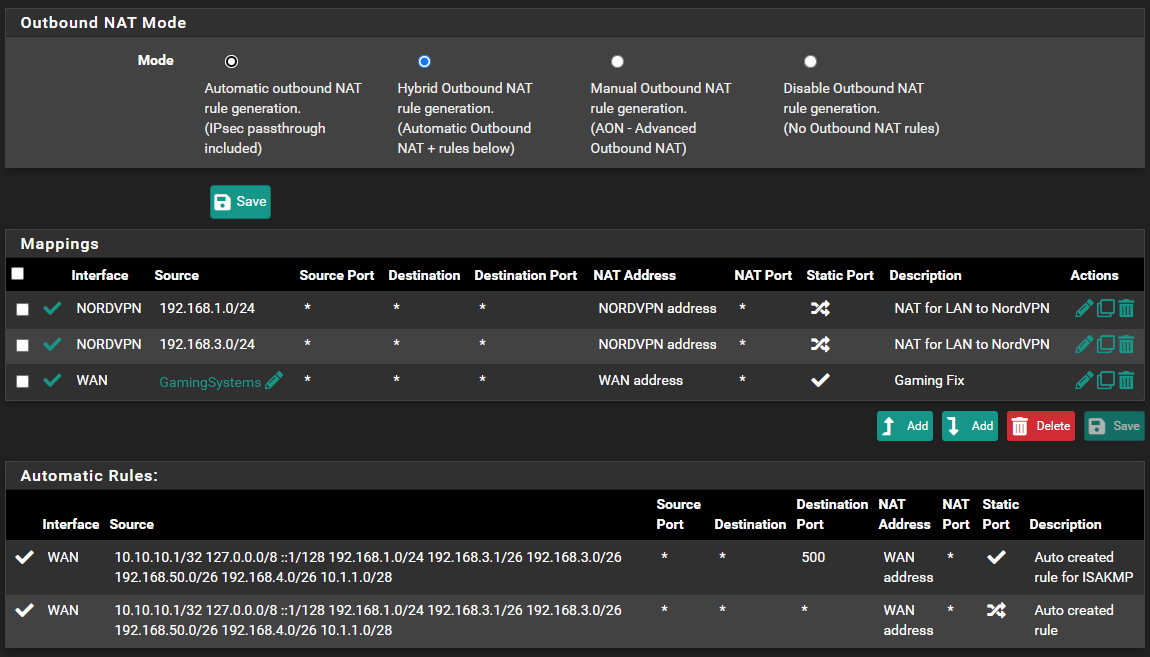
Could this be the issue?
-
@vmac said in VPN up Gateway up - No Internet:
I'm confused as to what you mean about the order. since VPN devices would only match specific devices. However, I made the change and still can't get any Internet when VPN connected:
To answer your other question, I have my pfSense resolving all DNS queries:
The question is if your VPN devices are configured to resolve host names. If they are set to use pfSense you need this rule, otherwise DNS requests are directed to the VPN provider, while the destination address is pfSense and resolution fails.
Since the rule shows some matches I assume the devices are set to use pfSense for DNS resolution.@vmac said in VPN up Gateway up - No Internet:
I'm starting to wonder if it has something to do with the Automatic Outbound NAT not working.
When I check the OpenVPN logs I see this noted:When I go to Outbound NAT I don't see this interface in the "automatic" generated outbound.
I cannot find what's really wrong there. The virtual interface port is ovpnc3. This one you should have assigned to NordVPN in interfaces > assignments.
The only weird thing in the outbound NAT is in the automatically generated rules: 192.168.3.1/26 and 192.168.3.0/26. No idea where the .1 is from.
Your VPN devices may be in 192.168.1.0/24 and 192.168.3.0/24? However, the latter may not really be defined on your system, since it isn't shown in automatic rules.
-
@viragomann
Well I'm at a loss.Yes the devices are set to use pfSense for DNS.
That is correct ovpnc3 is assigned to NORDVPN.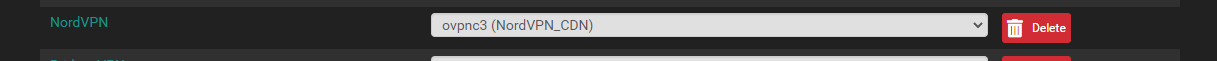
I'm assuming this is where the 192.168.3.1 comes from Interfaces->IoT:
Yes I have some devices that I want to use the VPN that are in my IoT vLAN, and I have ones that are regular LAN vLAN that I want to use the VPN. The device that I'm testing right now is on the LAN vLAN and still can't hit the VPN. I just tried the IoT vLAN and same issue.
The really weird thing is nothing has been changed except me adding a traffic shaper. Before my config has worked for literally 2-3 years.
-
I just updated to 2.5.0 RC and have the same problem.
NordVPN used to work perfect, now I don't get internet through it. The interface comes up with an IP but when I look at the traffic graph I only see outgoing traffic (no incoming).
It was a straight upgrade, I made no changes to the pfSense config.