RFC1918 "attacking" me
-
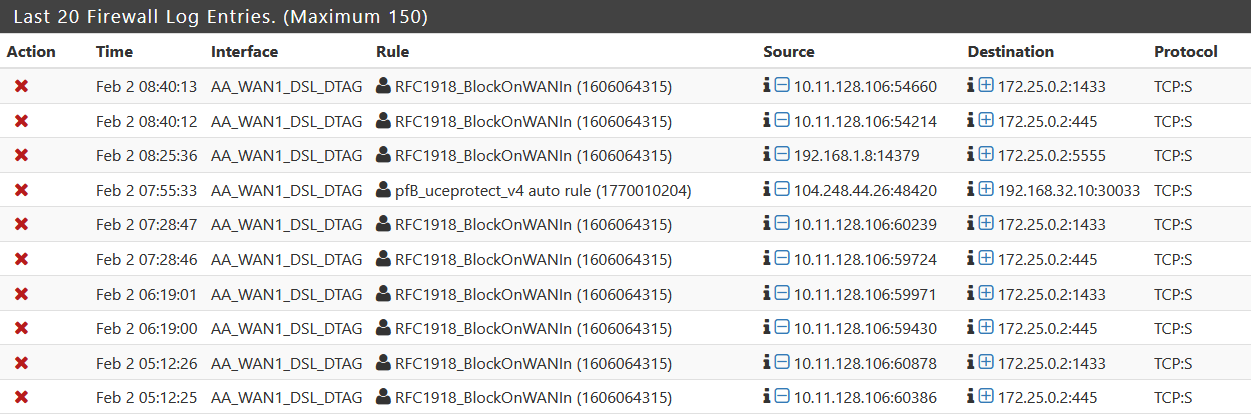
Hi guys, something that is making me nervous since I switched my ISP are these connections.
My pfSense is running behind another router, so I couldn't use the "Block private networks"-option in interfaces. I recreated this kind of block with floating rules.
On my WAN-port of my "first" router, I have a public IPv4. This router is only doing the internet connection and telephony and, other then pfSense, there are no devices connected to it.
Who is able to make those connections shown in the log in the first place?
I am particularly nervous because for example in my email-server, I can define trusted IP-ranges, which don't have to authenticate as thorough as others, and I defined that range broader. But if I hadn't recreated this RFC1918-block rule, I could face a problem with that.
Shouldn't the ISP block such traffic in the first place or are they behind it...
Edit: Now that I am looking closer at my own post, I even can see 192.168.1.8, which would be from my current LAN, but there is no host with that IP on it... really disturbing.
-
@bob-dig
What/who is, for example, 172.25.0.2 ? A local LAN ?
Also 192.168.1.0/24.@bob-dig said in RFC1918 "attacking" me:
I even can see 192.168.1.8, which would be my current LAN, but there is no host with that IP on it
So this is LAN to LAN traffic blocked by a floating rule ? Can we see the rule ?
You can see what this rule "1606064315" really is. Look at /tmp/rules.debug
True, a 192.168.1.8 that doesn't exist, in relation to an interface called AA_WAN1_DSL_DTAG ... I don't get it.
I don't think it is related to your new ISP or upstream router. What is the pfSense WAN network ? An RFC1918, right ?
Just a wild shot :
Do you have pfBlokcerNG installed ? What is the Virtual IP Address ? What is the Web Server Interface ?@bob-dig said in RFC1918 "attacking" me:
my email-server, I can define trusted IP-ranges, which don't have to authenticate as
Don't bother. Everybody authenticates. Especially those you think you know.
-
@gertjan pfblocker is using 10.10.10.1.
Even looking at the ARP Table, there is no 192.168.1.8 on my LAN (192.168.1.0/24). 172.25.0.2 is pfSense behind the first router (172.25.0.1).Here is this rule:
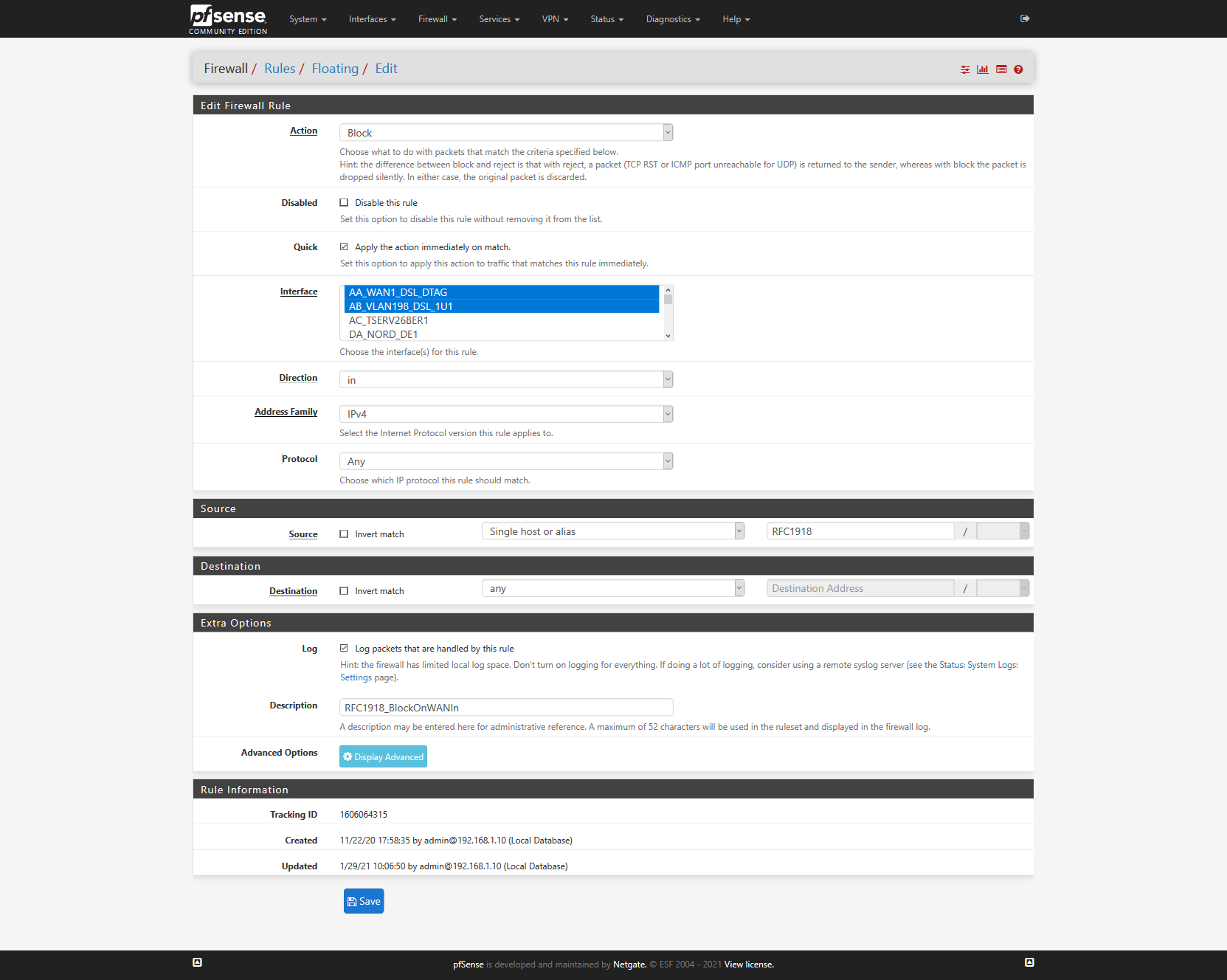
The other WAN shown there is turned off by its connecting device (Bridge) and would use 192.168.178.0/24 if it would be on.
-
@bob-dig said in RFC1918 "attacking" me:
pfblocker is using 10.10.10.1.
..... What is the (pfBlokcerNG) Web Server Interface ?
Humm.
I'll join you.
This is something between strange and scary. -
@gertjan Placeholder IP Address is 127.1.7.7. Couldn't find any other IP-address.
I mean there were others scanning our public IP before, eBay did.But if my ISP is doing it like this, there would be a very thin line between securing their network and eventually spying or fulfilling court orders. This ISP (Deutsche Telekom) is the formally run by the german state ISP, which still runs all their stuff for all the agency's etc and is also germanys biggest ISP I guess.
-
So it looks like my ISP is scanning some ports on a regular basis.
But especially the IP looking for port 5555 is looking ugly to me.
I made a dump of another connection attempt from 10.11.128.106 later this day, if you are interested @Gertjan .
-
@bob-dig : what about blocking everything, no logging.
This is the default after all.
If 'they' want to test the firewall, see it as a service. Let's say : you pay for it ^^