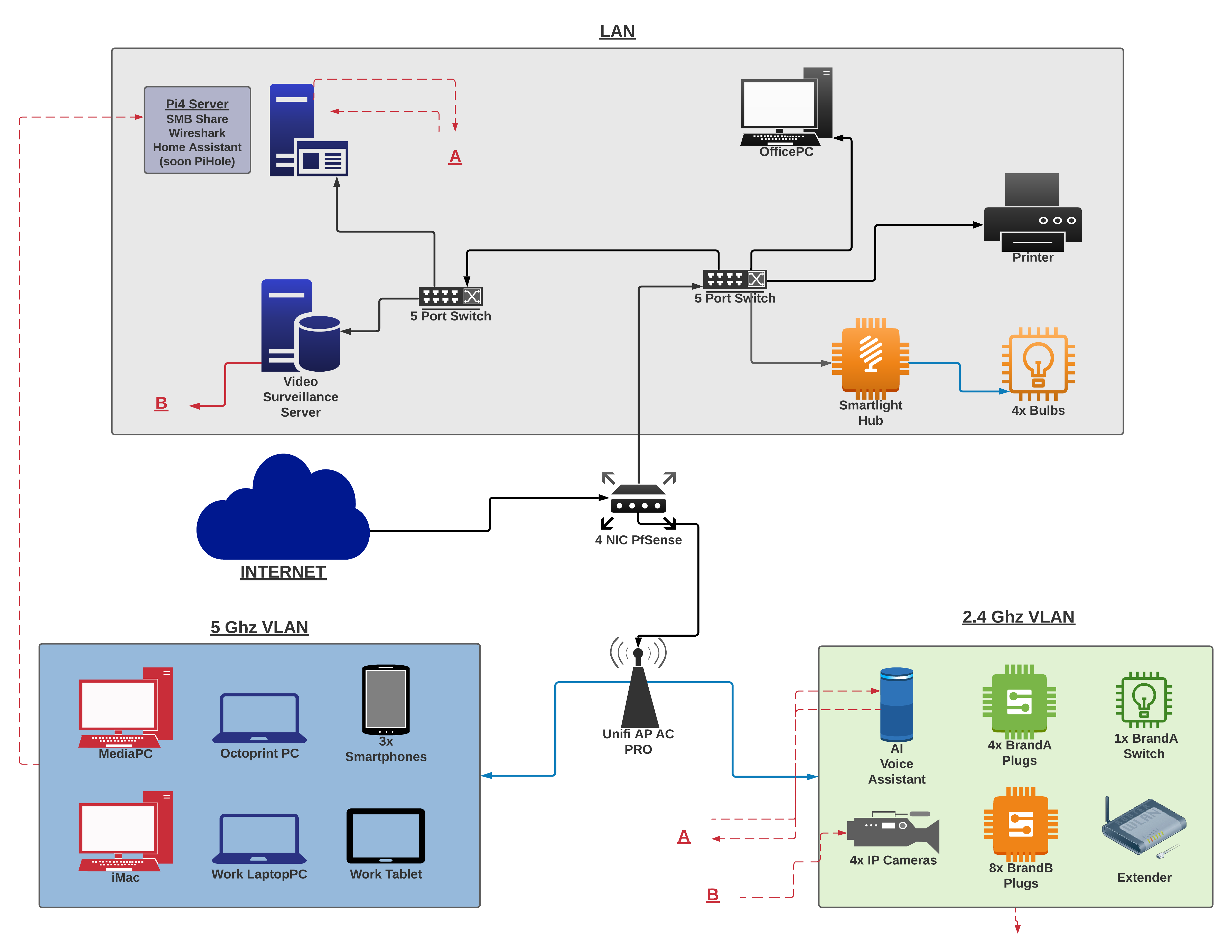
Am I thinking this topology through correctly?
-
EDIT: Apparently I am limited on how long I have to edit a post. The little red line coming out of the 2.4ghz box shouldn't be there...
Thanks to both of you. The purpose for separate VLANs was just a security idea. In case of an obscure threat on the 5ghz, it won't be able to pass over to LAN, which is the primary area of above the line services and hardware. The 2.4ghz must be on a VLAN (so I've read) because I have way too many IOT devices now. I am not concerned about devices connecting between the two bands, nor do I want them to be able to.
The extender only connects to 2.4ghz and runs DDWRT converting the connection to ethernet. It only exists as a way to hardwire connect a device I am building/ tinkering with to Internet on my shop table. Otherwise, it is actually NOT an extender....I didn't think of any other way to label it.
Please keep in mind guys that I have no attic :(. Running cables around the house isn't very Feng Shui.
I might not have explained myself very well on the switches. The two I plan to replace are on the LAN (ie. hardwired for my sake) side of the network. I need a few firewall rules in place so that a limited amount of traffic on the VLANs can pass over to my little Pi4 server and Video Server (on the LAN). I read unmanaged switches will drop the VLAN tags, so $30 Unifi managed switches are completely fine with me. LAN will not be set up as a VLAN (unless I'm not thinking this through correctly). I just want the switches to not drop the route from a device on VLAN1 or VLAN2 when I try to connect it to the servers.
-
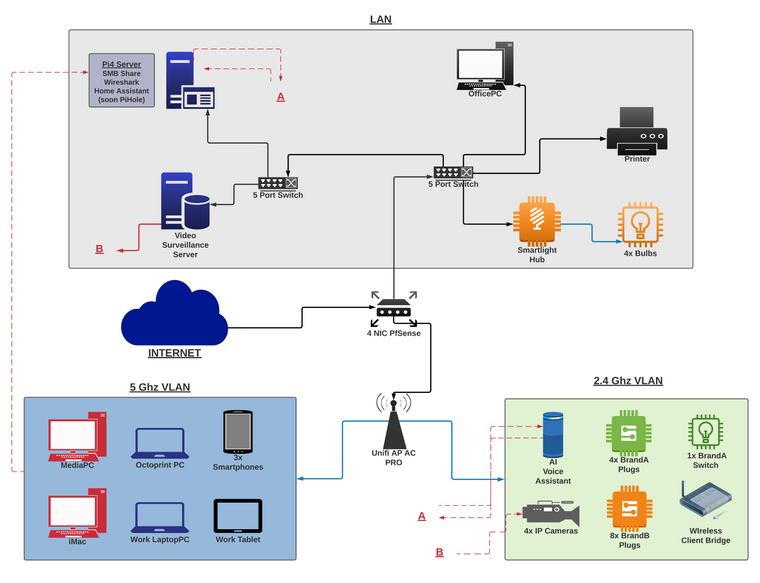
Updated drawing to correct mistakes...
-
@nerlins said in Am I thinking this topology through correctly?:
The extender only connects to 2.4ghz and runs DDWRT converting the connection to ethernet.
That is not an extender then that is a "wireless client bridge". If that is the case then sure that is fine.
As so you looking at the little mini ones from unifi for $29 - yeah those would work.. I would personally prob go another route.. But those would work.
The term vlan can be a bit confusing sometimes if you haven't worked with them a lot. Pretty much anyone that works with multiple segmented networks a vlan is just another network. Be it tagged or not. Vlan just means another network segment, isolated L2 doesn't have to be tagged. Tags are really only used when you carry multiple vlans on the same wire.
While dumb switches may or may not strip tags, it most likely they wouldn't strip the tag.. But they don't understand them either. So broadcast traffic would go everywhere - your not really isolating L2 with a dumb switch.. You end up just running multiple layer 3 over the same L2.. While that could be used in a pinch if that is all you had and you needed to move some tagged traffic over it as an extension or something.. But do yourself a favor and get smart switches if your going to be running vlans over them.. If you want some access switch somewhere and everything is going to be in the same vlan then ok.. But again smart switches get you way more than just the tags.. Its well worth spending the few dollars to get a smart switch.
Maybe for your switch before pfsense, get a 8 port smart switch.. Or even 16 so you have some room for growth at your core..
-
Thanks @johnpoz
I know enough to get my tongue tied. I'm apt at sitting here on a Saturday, all day, amassing knowledge then implementing it. I have updated again to correct for the Wireless Client Bridge:)
I doubt there will be much more growth here. The left side switch would theoretically handle a couple more devices on my 'server shelf', and I think I maxed out my personal limit for IOT devices. In truth, I feel like all the stuff I have is currently all I need, sans another Pi running Pi-Hole by itself, or another IP camera.
-
@nerlins said in Am I thinking this topology through correctly?:
I think I maxed out my personal limit for IOT devices.
You say that now ;) I just added 10 more light bulbs.. Just bought a new washer and driver.. Those could of been wireless.. But didn't go with that model ;)
I got a 28 port switch couple years back to replace my 10 port on my desk.. Like how and the F going to fill that up ;) Guess what.. Its pretty full..
-
I am going to build the network this weekend, and have already made adjustments to my topology.
I am thinking that maybe my map has just confused anyone reading and posting to this thread. That was my first network topology map to draw out. I contacted Netgate and spoke to Sean.
Shout out to Sean for being so awesome and helpful!!!
He understood what I was trying to do. Once I put it all together I'll post back, then also update the map to hopefully be more 'readable' for people who are looking for industry standards from a home diy guy...
-
@johnpoz said in Am I thinking this topology through correctly?:
While dumb switches may or may not strip tags
Why would a dumb switch strip a VLAN tag? The only significant difference between a VLAN frame and any other is the contents of the Ethertype/length field. Given that switches are supposed to pass all Ethernet frames, it's a bit much to ask of a dumb switch to strip off that tag.
-
JFC dude - give it a break... READ WHAT I POSTED...
"it most likely they wouldn't strip the tag."
He is the one that brought it up about stripping, I stated they most likely wouldn't - and that has nothing to do with should you buy a smart switch or not..
Lets put it this way.. DO NOT BUY A DUMB SWITCH!!
The point that should be taken away from this is - even when they don't strip them.. They do not understand them.. If you passing vlans over a dumb switch your doing it WRONG!!!
Since they do not understand them - you might as well strip them when it comes to broadcast traffic..
-
@jknott
802.11q adds 32bits to the ethernet frame.
some of the older switches just dropped those frames. (most likely pre-jumbo frame era)I recently had todo a temporary hack with dumb switch in between 2 smart switches ... it worked as far as i could tell, but still didn't like it
-
Yep, it would have to be pretty ancient gear. Frame expansion arrived over 20 years ago and jumbo frames after that. Back in the late '80s I hand wired a couple of Ethernet controllers, for Data General Eclipse computers, which were unlikely to handle the larger packet sizes.
Sorry, @johnpoz, I didn't mean to target you, I should have replied to the OP. This notion that unmanaged switches can't pass VLAN frames just rubs me the wrong way. These days switches can pass frame sizes of several KB and won't choke on something greater than 1500 MTU, as might have happened back in the dark ages.
-
This post is deleted! -
UPDATE: I was having a hard time seeing the Unifi devices on my LAN network controller when they were plugged into the OPT ports on my Protectli router.
Everything works now. I can see any Unifi device plugged into the OPT ports. I created a bridge between dummy interfaces (created on each OPT port) and the LAN interface with DHCP on the dummies, not static IPV4. I also DID NOT assign that bridge as an actual interface. It’s just a dumb bridge and I can now see and manage Unifi crap.
Also, the VLANs all work as well. Three VLAN interfaces on OPT1 (as wifi SSIDs) and 1 on OPT2 (for a VLAN on one of the flex mini switches). All VLANs created in PfSense match VLANs/ Networks created in the Unifi controller. All devices connected to them receive proper subnet IPs, and internet access. I turned on IGMP snooping inside the Unifi network controller on each network (ie., VLAN) just in case. I can now play around with rules and network discovery.
-
@nerlins said in Am I thinking this topology through correctly?:
I created a bridge between dummy interface
Dude you come here and ask - and then just do it completely wrong..
Get a SWITCH!! If your creating a bridge on pfsense and then putting vlans on them? Clearly thought wasn't any part of that decision..
-
You have already stated that I can run VLANs on the AP, connected straight to the OPT1 port on PfSense, where I created interfaces for each of the VLANs. I did this, but couldn't see Unifi devices in the network controller.
The VLANs are not part of any bridge. The bridge is a connection of a separate interface on each of the OPT ports and the LAN interface. I created that bridge so I could see Unifi devices on my Unifi Network Controller hosted on LAN.
If I remove the bridge everything still works, but I lose the ability to see the devices in the controller. I don't understand where you read that I connected the VLANs to the bridge.
I might go ahead and put a switch in-line to always see the Unifi devices, but creating a fake bridge was an interesting way to see the flex mini switches and AP from different subnets. I could use set-inform for the AP to point it to the controller, but the flex switches don't have ssh.
-
@nerlins said in Am I thinking this topology through correctly?:
I did this, but couldn't see Unifi devices in the network controller.
Well your only going to see unifi devices when they are in the same L2 network, unless you did L3 adoption..
I even brought up putting wireless and wired in the same vlan, etc. Which is why you would want a switch.. Bridging interfaces is NOT a switch..
As I suggested from the get go - get a switch to put in front of pfsense so you can do whatever you want with putting anything you want in any specific vlan.. If your going to connect a AP that has multiple vlans on it directly into a port on pfsense, you would have no way to add wired devices to any of these vlans.. Without the nonsense that is bridging..
Spend the $40 and get a vlan capable switch to connect all your different devices together.. Then either use multiple uplinks or setup lacp into pfsense so it can route between the networks at L3..
Or get an appliance that has actual switch ports on it, like a 2100 or 3100