OpenVPN Site-to-Site Routes
-
@m4xm0rris
The log shows your public IP. You'd better hide this.But there is no entry of adding routes on the client and on the server it obviously failed.
For getting closer, please post the OpenVPN configurations of both site (with public IPs hidden) and the routing tables of both, when the VPN is down.
-
@viragomann said in OpenVPN Site-to-Site Routes:
ng closer, please post the OpenVPN configurations of both site
Thanks for the heads up, have yet to consume my 3rd coffee for the day

When you say "When the VPN is down", do you mean connected but unroutable (as it is now) or after disabling the connection's daemon?
-
@m4xm0rris
When the connection is disabled, to see the origin routing table. -
@viragomann Any black boxes indicate the Primary Sites WAN IP, as the Secondary Site has a WAN connection on another private subnet I have not censored this. Also I may have forgotten to mention, the Primary Site also has a OpenVPN Remote Access server on 10.1.1.0/24 so you may see this on the Route table. Let me know if you need anything else

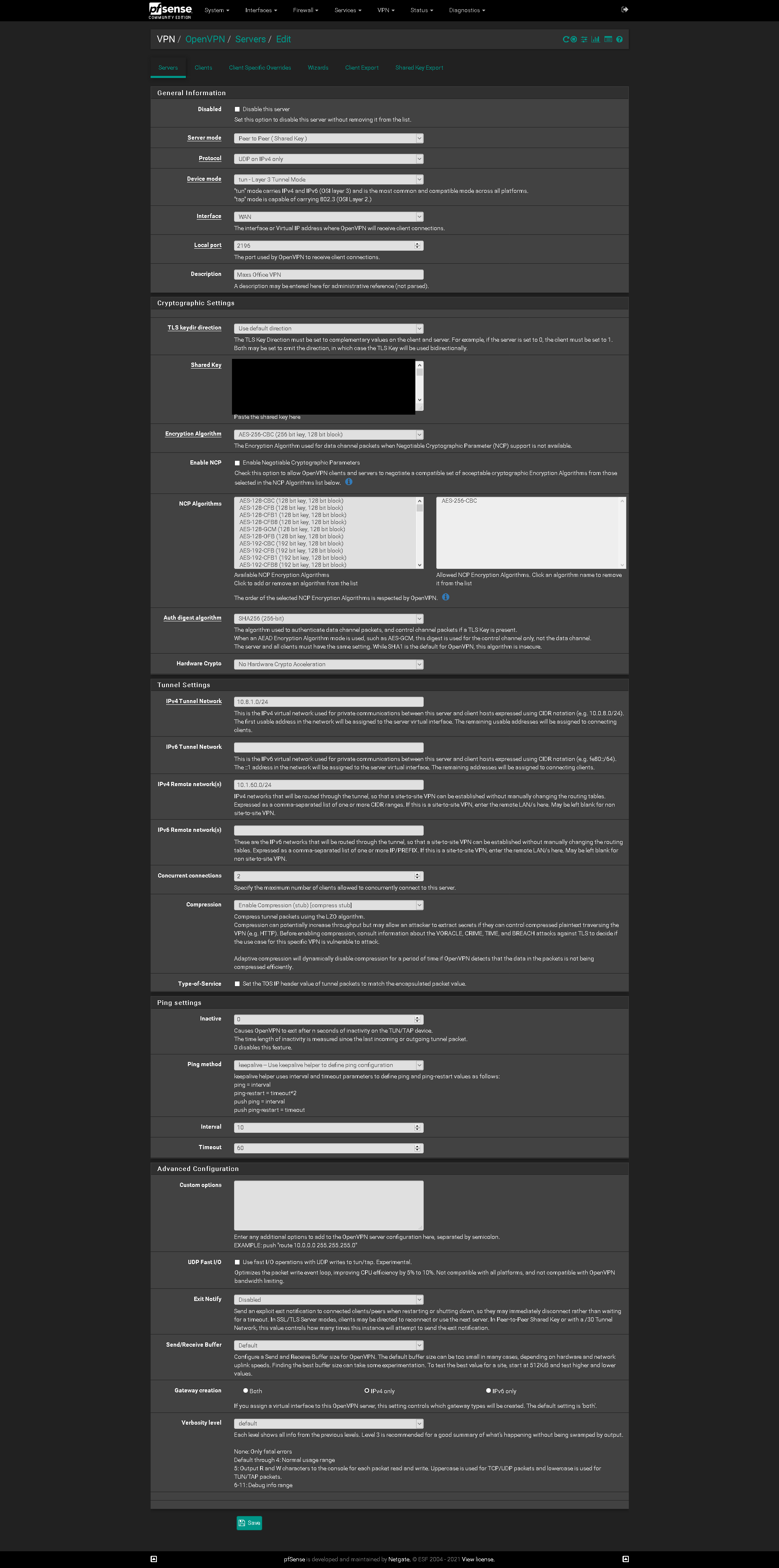
Primary Site VPN:
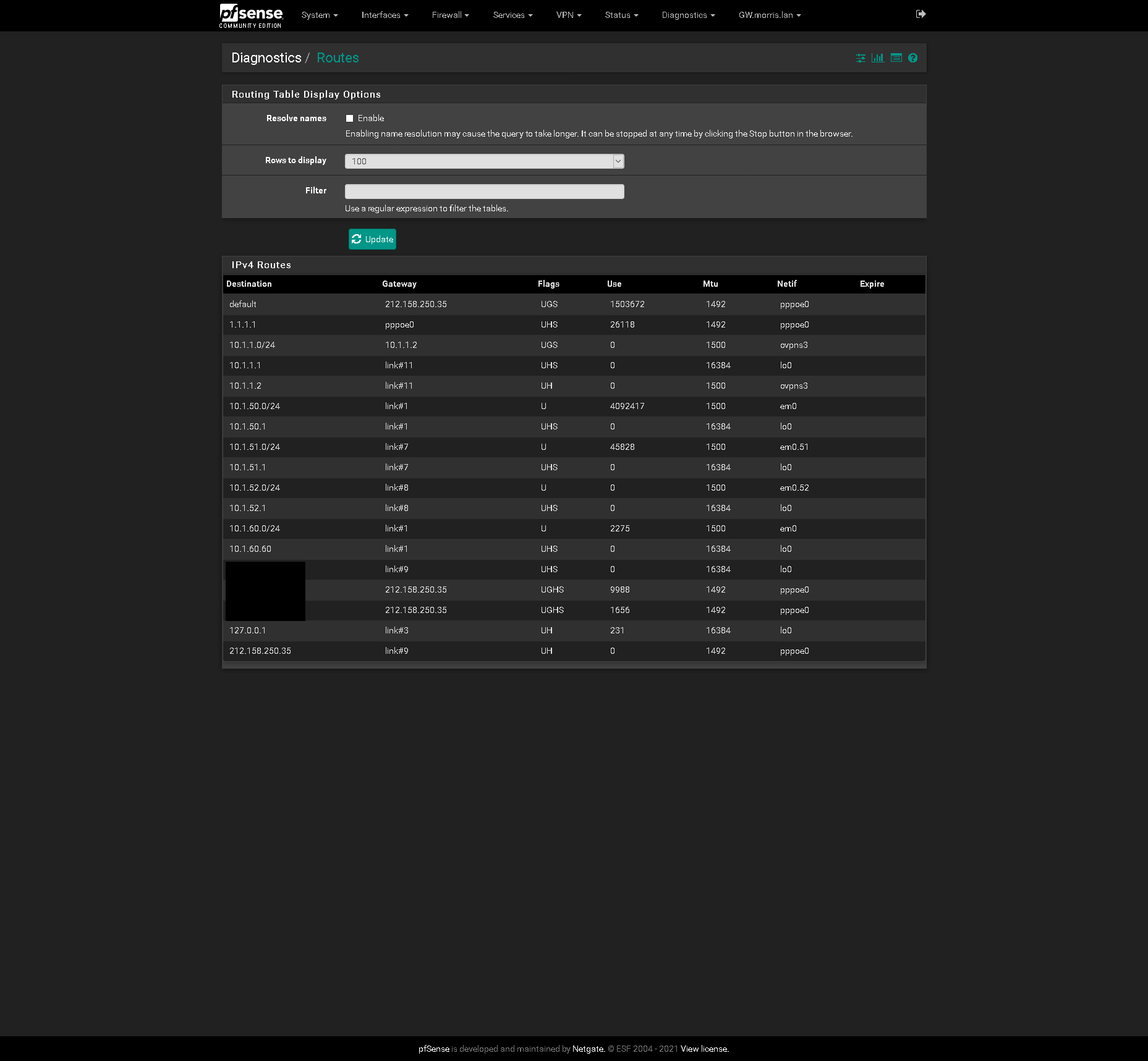
Primary Site Routes:
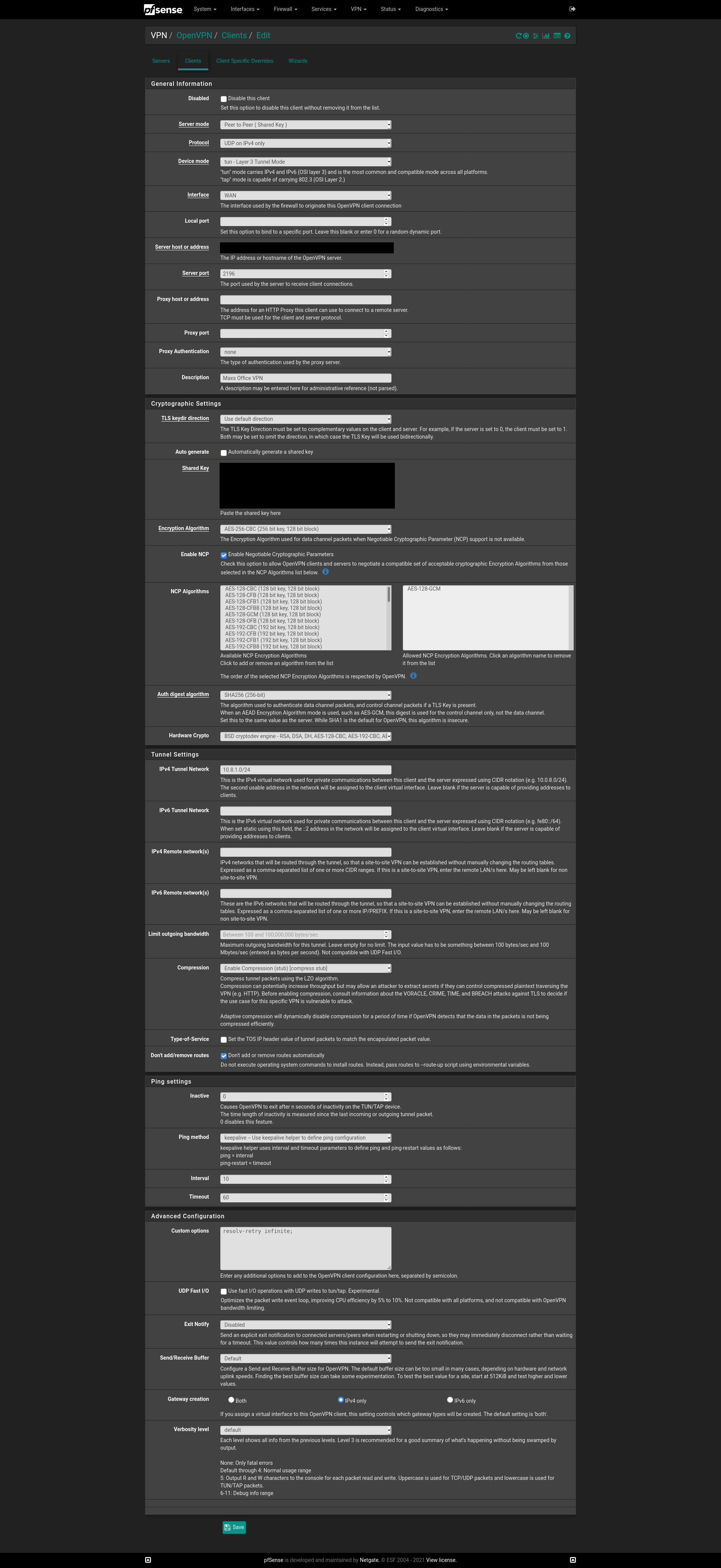
Secondary Site VPN:
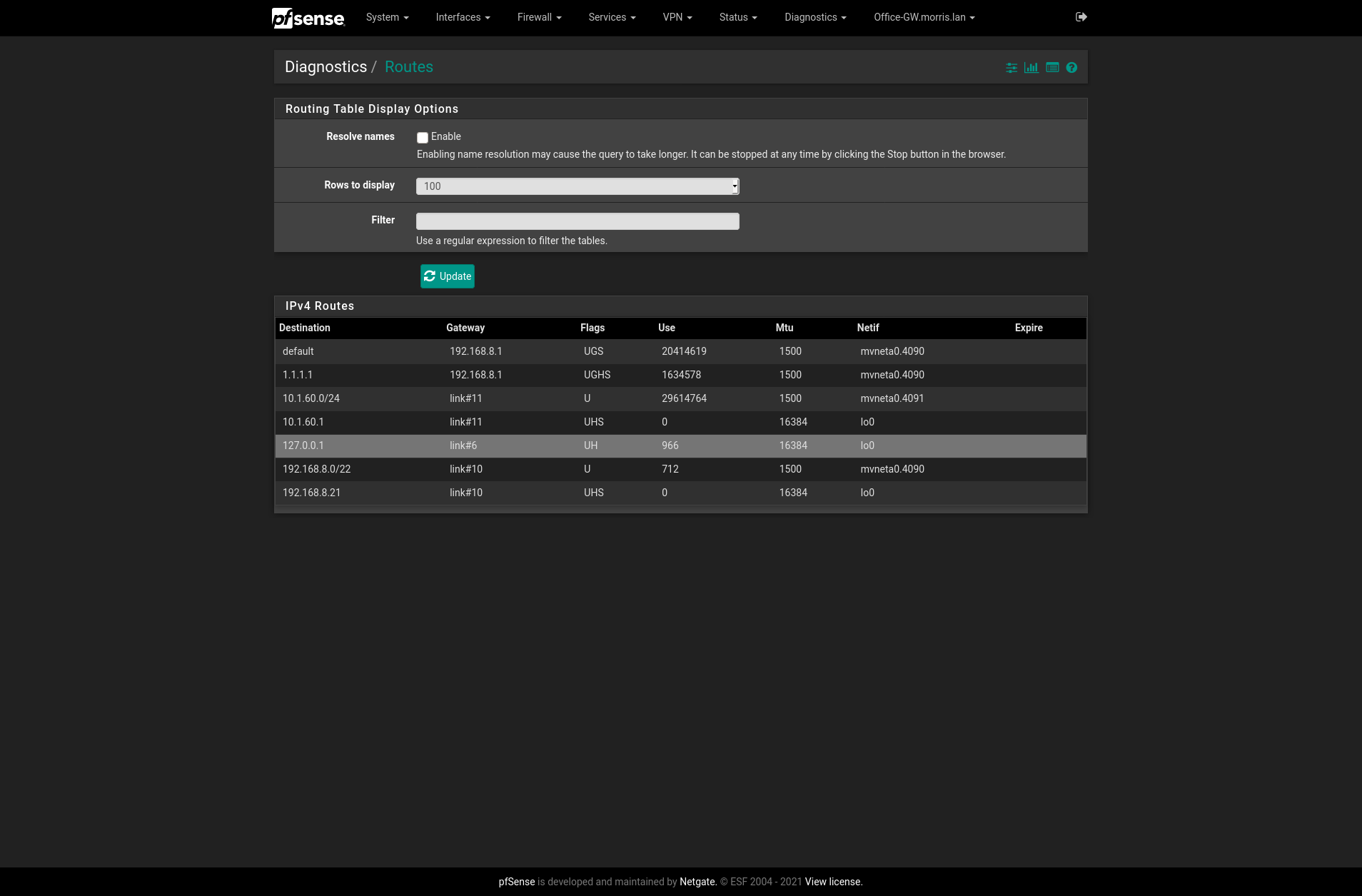
Secondary Site Routes:
-
@m4xm0rris
The subnet 10.1.60.0/24 is defined on both sites.
On primary it is assigned to em0, the same as 10.1.50.0/24 and pfSense has the IP 10.1.60.60.

-
@viragomann Why this is appearing as this I have no idea. There are no interfaces, nor have there ever been any assisgnmnets on the 10.1.60.0/24 network on the Primary site. Only interfaces assigned at primary are the LAN (10.1.50.0/24), an IoT VLAN (10.1.51.0/24) and a Guest VLAN (10.1.52.0/24). Can you think as to why this would be the case?
-
@viragomann
I've just noticed in the Auto Rules in Outbound NAT on primary, there are listing of the 10.1.60.0/24 network. I have very little knowledge of how these work, does it help?
-
@m4xm0rris
Its there, cause its assigned to an interface.
Check the virtual IPs and the interface settings. -
@viragomann Well I'll admit I've rarely felt stupider than that. Indeed there was a Virtual IP setup for 10.1.60.60, think I must have created it at some weird point for some weird reason.

Having said that, I have deleted it now and restarted the OpenVPN service on both ends of the tunnel and Reset States, still the issue persists. -
So after deleting the Virtual IP, clearing the "IPv4 Remote Network(s)" fields on both of the OpenVPN configs and adding in Static Routes for the remote subnets, it seems this is now working and the Static Route persists between tunnel reconnects. For some reason it still doesn't seem to work without defining a Static Route for the remote subnets to route over the VPN Interface gateway, but nonetheless, it works!
Would have never even considered to look in the Virtual IPs, thanks for your help @viragomann
