XG-7100 inter VLANS traffic
-
Hey ... I am a beginner with PFSENSE and also with VLANs. My problem is : I have two VLAN 200 and 4091, VLAN200 (192.168.2.1/24) is for medical devices and VLAN4091 (192.168.0.1/24) is for computers, from medical offices. All VLANS works fine ... i can access internet from them. Medical equipment and computers from offices, must communicate with each other, and i dont know how to do it. Can anyone help me how to configure XG-7100? Pls.
Here is switch config :etherswitch0: VLAN mode: DOT1Q port1: pvid: 4090 state=8<FORWARDING> flags=0<> media: Ethernet autoselect (1000baseT <full-duplex>) status: active port2: pvid: 200 state=8<FORWARDING> flags=0<> media: Ethernet autoselect (1000baseT <full-duplex,master>) status: active port3: pvid: 4091 state=8<FORWARDING> flags=0<> media: Ethernet autoselect (none) status: no carrier port4: pvid: 4091 state=8<FORWARDING> flags=0<> media: Ethernet autoselect (none) status: no carrier port5: pvid: 4091 state=8<FORWARDING> flags=0<> media: Ethernet autoselect (none) status: no carrier port6: pvid: 4091 state=8<FORWARDING> flags=0<> media: Ethernet autoselect (none) status: no carrier port7: pvid: 4091 state=8<FORWARDING> flags=0<> media: Ethernet autoselect (none) status: no carrier port8: pvid: 4091 state=8<FORWARDING> flags=0<> media: Ethernet autoselect (1000baseT <full-duplex>) status: active port9: pvid: 1 state=8<FORWARDING> flags=1<CPUPORT> media: Ethernet 2500Base-KX <full-duplex> status: active port10: pvid: 1 state=8<FORWARDING> flags=1<CPUPORT> media: Ethernet 2500Base-KX <full-duplex> status: active laggroup0: members 9,10 vlangroup0: vlan: 1 members none vlangroup1: vlan: 4090 members 1,9t,10t vlangroup2: vlan: 4091 members 3,4,5,6,7,8,9t,10t vlangroup3: vlan: 200 members 2,9t,10tThank you very much. Best Regards
-
Can pfsense see devices on both VLANs? If so, it's a filter issue. You have to ensure traffic is allowed between VLANs.
-
@jknott I can ping from PFSENSE router console, to hosts from both VLAN's 200 and 4091. I also have rules in firewall to allow traffic ... but i can not ping from a PC witch is on VLAN200 to a PC witch is on VLAN 4091 ,and vice versa ... I get a "replay timeout".
Thank you.
-
Routing is automagically enabled between subnets in pfsense. That leaves firewall rules. Maybe you could post your rules here.
-
@jknott Hey , i changed the configuration , i split the integrated switch into 8 discrete ports. My configuration is:
Assigned Interfaces
Integrated Switch Ports
Integrated Switch Vlan's
VLAN's
LAN rules
Medical Devices Vlan 4083 rules
... no luck ...Vlans tagging is "not for me" :( i can't ping devices conected on port 3 (VLAN 4083 IP Class: 192.168.2.1/24) from devices conected on port 8 (VLAN 4088 LAN IP Class : 192.168.0.1/24) and vice versa ... "Request timed out". From VLAN 4083 (Medical Devices) i can ping gateway of WLAN 4088 (LAN) and vice versa. Please help me.Best Regards
-
At the pfsense end, there's nothing special about VLANs. Just think of them as another interface. However, your switch has to be configured appropriately.
-
@jknott Can you tell me what i'm doing wrong, or what is wrong on my switch .... i beg you.
Thank you.
-
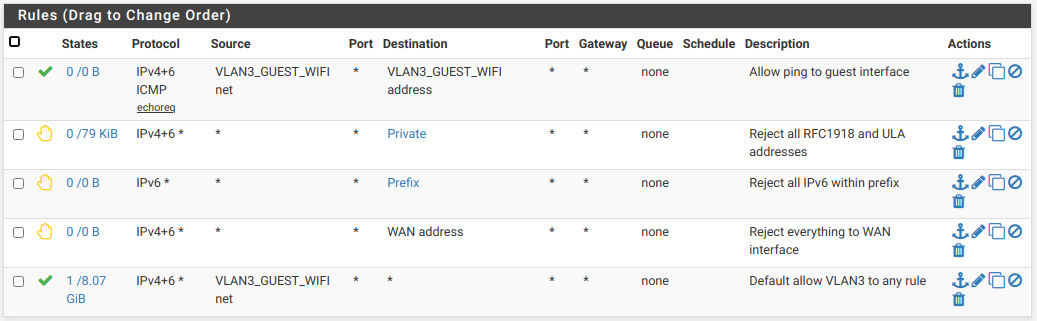
I can't tell you about your switch. What I can do is tell you about what I have here. I have a guest WiFi, which uses a 2nd SSID and VLAN. I have configured pfsense to put VLAN 3 on my main LAN. I then configured my switch to have the main LAN and VLAN 3 on the ports connected to pfsense and my AP. However, unlike you, I set up my firewall rules to block guests from accessing my local network. In your case, you'd have to set up an allow rule on the VLAN to wherever you want it to communicate with. Since all interfaces are on the same pfsense box, additional routing is not needed.
Here are my rules. As I mentioned, they block VLAN 3 from accessing anything other than the Internet, but you may get some ideas from them.
-
@jknott Thank you .... ill try to inspire from your hint. Thank you again.
