Netflix Issues over WireGuard
-
And FYI, I just tried a traceroute to netflix.com sitting on the same subnet as pfSense (i.e. right behind the firewall), and it looks very much like above. So not sure traceroute is really telling the whole story? I am able to get to the web site

Thanks!
-
And one more thing - digging in to this, it may be nothing, but in case it means something to someone else (i.e. more than me ... LOL!). The error I see in Chrome is
ERR_HTTP2_PING_FAILED.Not sure yet what HTTP2 is, and if this is for some reason not getting across the WG link (or through routing).
Thanks!
-
FYI, I did also check the routing tables (on OpenWrt / the client side), using WG or OVPN - they are a bit different. OVPN uses two "sub entries", to be more specific for preference reasons (more info here) => so I changed 0.0.0.0/0 on the client side to 0.0.0.0/1 and 128.0.0.0/1 ... no difference (assuming I don't need to restart WG on pfSense for this). Dang it!
Just to keep you in the loop.
Thanks!
-
@arrmo
Your trace is ok - remote OW LAN is able to route to pfsense 192.168.253.1 for Netflix access. We also see that pf is routing is correctly to the WAN_DHCP. Now the only few things preventing Netflix (assuming that your IP is not detected as a VPN by Netflix) is- Set a lower MTU on the WG tunnel. Google how to do that - start with 1400 or 1380
- Check to make sure you are not blocking anything in pfBlocker NG or other packages
- Check to make sure OW LAN is using the same DNS servers as the pfLAN
-
@ab5g said in Netflix Issues over WireGuard:
assuming that your IP is not detected as a VPN by Netflix
I don't think so, could be wrong, but internet IP check seems clean.
@ab5g said in Netflix Issues over WireGuard:
Set a lower MTU on the WG tunnel. Google how to do that - start with 1400 or 1380
Check to make sure you are not blocking anything in pfBlocker NG or other packages
Check to make sure OW LAN is using the same DNS servers as the pfLANWill try those, thanks! On them,
- Changed MTU, but had to reboot OW - and as it's remote, I need someone to reconnect to the router to check. Will be tomorrow to confirm that one, sorry!
- I don't think so
 . No packages installed that block any traffic (that I can see at least).
. No packages installed that block any traffic (that I can see at least). - Yes, pretty sure that's clean also - nslookup to machines on the pfSense subnet resolves / returns, so thinking that is good as well.
I'll get back to you on #1, once I can check it. Thanks again.
-
A bit more data ... and a "fix" (not really, but a data point
 ). Let me explain.
). Let me explain.To the questions above, I did check the MTU - no change. Packages ... don't think that's it, will explain below.
So I did some poking on pfSense, noticed one difference (OpenVPN vs. WG) - I did not have an interface assigned for OpenVPN (mistake perhaps, but that's for another day ... LOL!). But I did have a "pass all" rule for OpenVPN (group). So just for giggles, I put back the old rule I had for WG (group) ... voila! Now Netflix works. I don't think this is a real fix (@ab5g, I agree with you, this should go through the interface!). So I think this means that the interface rule is not quite right ... agreed?
So I checked the interface rule, and it looks right to me (I think) - meaning I think followed the recommendations, but I may have something broken. Pic below ... is the source for OW really right? Wondering about back to OW ... could that be the issue?
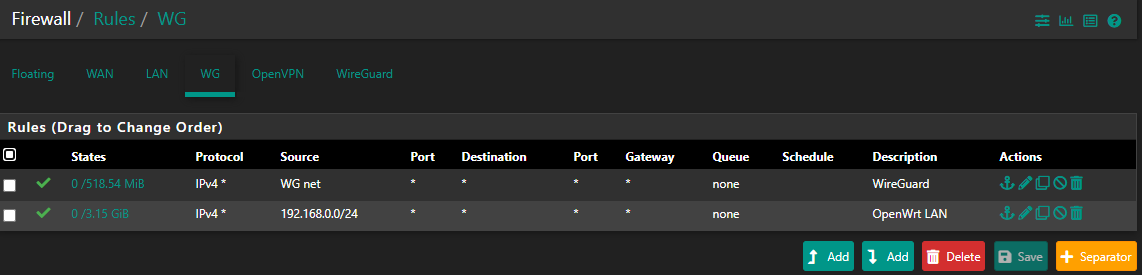
OK, really funny - but enabling the WG Group (for Netflix) breaks another web site ... LMAO! But let's get the WG Group rule out of there, that may take care of this also.
Thanks!!!
-
And a bit more debugging - pulling my hair out though! LOL. I turned off the group rule (pass-all), and yep ... Netflix blocked. So, I added an interface rule ... like above, but with source = all (for testing). Nope, still no go. So is this about return traffic? I admit, a bit confused.
Oh, and FYI - to capture it for others. I changed the rule back (i.e. re-enabled the group rule). Did not need to restart WG, and it all started working again (i.e. Netflix gets through).
Thanks!
PS, just noticed, poking around ... but WG_WGV4 is set to 192.168.253.2, one of the (other) clients. This doesn't seem right, but I also can't seem to change it?
-
I don't have any WG to play with as of yet.. But as soon as 2.5 drops I will be moving to it. And will be sure to fire up WG on one of vps to play with. Like I have openvpn access server setup now to play with when users have questions.
Wish I could be of more help.. Maybe your having problems with states? If traffic goes out way X and creates a state, even if you bring up another way to go out the wan, be it openvpn or wg, or just policy routing out another gateway.. That existing state can send traffic out way X, even when you have a new policy that should send it out Y.
-
@johnpoz said in Netflix Issues over WireGuard:
Like I have openvpn access server setup now to play with when users have questions.
Sounds great. And some of my notes above are to try to share findings with others. I know this is new, so whatever we can help each other with is all positive. To be honest, I'm really happy overall with how WG is working, just some fine tuning / details to work out.
@johnpoz said in Netflix Issues over WireGuard:
Wish I could be of more help..
No worries at all - your pointers are very helpful, even if they fall on "deaf ears" here some. Only because I'm still figuring this all out

@johnpoz said in Netflix Issues over WireGuard:
Maybe your having problems with states?
It is possible! Let me try to look deeper there. I'm also a bit confused about the WG gateway, wondering if that is part of it. I do notice that even wide open WG rules aren't getting "hit" (i.e. no states / traffic), so thinking this is a return issue? But I can't seem to set the WG IP, it's "locked" to default.
Thanks!
-
Hi,
Perhaps on to something - sharing some thoughts here, by all means comment if I'm out to lunch
 .
.-
I re-ordered the LAN rules, thinking the more selective one (192.168.0.0/24) needs to be above the general one, or traffic to that subnet won't get to the correct gateway. Agreed?
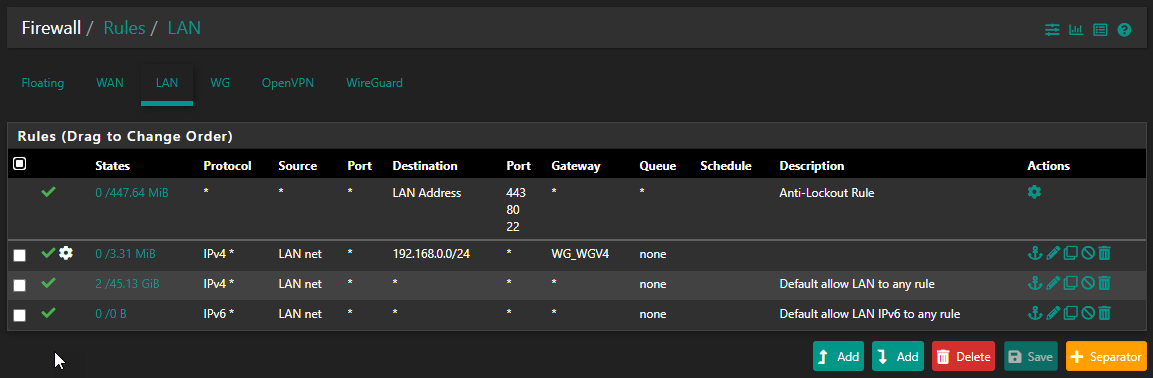
-
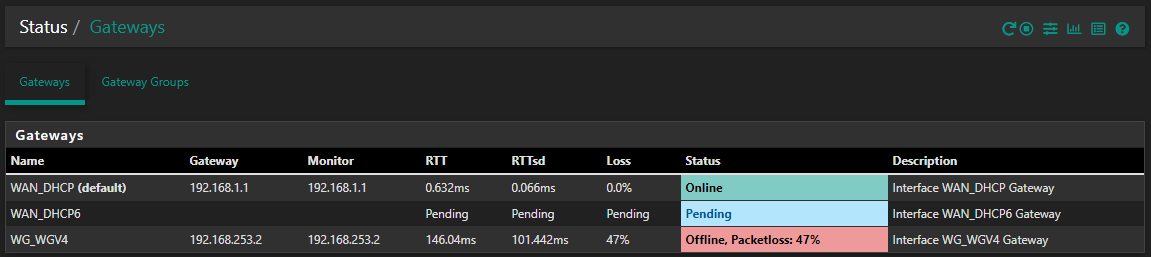
But, it seems that my WG gateway IP is not correct? As above, I can't change it, it shows "dynamic" ... but seems to be getting set to a different client address (i.e. my mobile phone!). Huh?
-
I may have stated incorrectly above about changing firewall rules, and not having to restart WG. It almost seems like there is a lag, which may be fooling me. Perhaps because current states don't get erased, and until they expire it seems like all is working?
Thanks!
-
-
I have no idea what you think this rule would do?
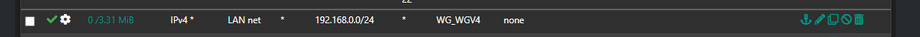
When would your clients ever being going to 192.168.0 IP.. netflix sure isn't on that network. Your clients don't try and go to your WG ip ever..
When a client wants to go to say 8.8.8.8, they send the traffic with that as a destination to the mac address of their gateway (pfsense).. Pfsense says oh you want to go to 8.8.8.8 let me look in my routing table were to send that.. either my default gateway, or something other gateway based upon a policy route..
That rule has no place ever.. And would only cause you grief trying to get to other vlans you have?? If you have them.. Also would cause problems just trying to talk to pfsense for say dns, etc.
-
@johnpoz said in Netflix Issues over WireGuard:
I have no idea what you think this rule would do?
LOL - NP! It was recommended that I add this one, to allow routing from the pfSense subnet, back to the OpenWrt subnet. And I realized it would never get hit as it is currently (below the pass-all rule, but with no gateway for the other subnet). Thoughts? I can see this needed to get between subnets, right? I do agree, this isn't the Netflix fix
 .
.That said, I'm still quite concerned about the (incorrect?) WG gateway IP. But it may just be me!
Thanks!
-
Your client has no clue about some openwrt network.. You have this
internet -- wrt -- 192.168.x/24 -- pfsense - 192.168.y/24 - client
When would the client need to talk to 192.168.x? And if it did - how would forcing traffic out your wg tunnel get you there?
Do you have stuff on this transit network between wrt and pfsense? If so that is asymmetrical problem for sure, especially if not natting at pfsense to this network.
I think maybe your misunderstanding something about policy routing and need to have rules that allow traffic above your policy route rule to get to other networks, but those would not be also policy routes, and they sure wouldn't go out some vpn connection.
There should be no reason for clients behind pfsense to have a care or need to get to some transit network between pfsense and your internet gateway.. If there is - your really doing it wrong... When you have to double nat, there should really be nothing on the network between the edge device and pfsense..
-
@johnpoz That (mostly) makes sense ... LOL! Not saying it's not right, I think it likely is - just my brain still trying to understand it, sorry!
I can disable that rule, NP at all. If I do ... the routing table gets updated "automatically" by WG, via the Allowed IP's - right? So then traffic does head back over the tunnel, correct?
Sorry for the dumb questions, just trying to understand how this all fits together (and play with the right "blocks" on the interface and group / tunnel, to get it all working).
Thanks for the pointers - very much appreciated!
-
What do you wan to do with your wg connection? Do you want to route all traffic out it, just some traffic?
Unless the upstream vpn provider knows about all your networks (which would for sure conflict with the other clients using the vpn service) You would need an outbound nat your networks to vpn network IP.
Just like you do in any other vpn connection. Just like you do on your normal wan connection. Pfsense nats your networks IPs to the IP of the connection.
If you setup wg to be your default route, then you wouldn't need to policy route, other than stuff you don't want to go down the vpn. If you don't have wg setup as your default route, then you would need to route traffic you want to go out that connection.. Your going to need an outbound nat in there somewhere..
Policy routing depends on what you want to do, and how your doing it. The protocols and methods used in wg doesn't really matter. When it comes to routing.
Not sure what guide you followed, or what service your using that provides wg as a method of connecting. But when it comes to routing and firewall rules - what you use for the tunnel.. What needs to be understood are you going to send all traffic down this tunnel or not?
My "guess" to your netflix issues or any other issues some other sites would be you messing with rules and having states, and then changing new connections to take a different route, etc.
You mention a phone? Not sure how that comes into play at all.. Why don't you draw up your network with this wrt, where your wifi comes in... And exactly your wanting to use wg.. I could see all kinds of issues if your wifi is of your wrt, and pfsense is downstream of that and your connecting to this wifi trying to connect to wg running on pfsense, and then send it down another wg connect to some vpn service to get to the internet?
-
@johnpoz said in Netflix Issues over WireGuard:
What do you wan to do with your wg connection? Do you want to route all traffic out it, just some traffic?
Thanks for taking the time to explain this, it does help! Let me try to clarify. FYI, this is a bit of a follow-on, to getting the basic setup working (first) ... captured here. But not expecting you to go through that, let me try to summarize!
Yes, I am trying to route all traffic over the WG connection. I know that WG relies on peer connections, but to make explaining easier, let me use the server and client terms. Hopefully why will become clear in a minute
 .
.I have a pfSense machine ("server") here beside me, and a remote OpenWrt (OW) "client" (child away at university - LOL!). So trying to route all the remote (client) traffic through my local pfSense firewall. I have WG up and running, and basically working pretty well - in fact, if I ssh in to the OW box itself, I can get to the internet, everything seems to work. Where I have been having issues is with the subnet (DHCP clients) hanging off of the OW router. Clear so far?
A bit more detail to help - the local subnet (behind pfSense) is 192.168.2.x (and the cable modem, WAN side of pfSense, is 192.168.1.x). The remote OW subnet is 192.168.0.x. For WG, pfSense is 192.168.253.1, OW is 192.168.253.3 (and another WG client, my mobile, is 192.168.253.2 ... odd that this is the WG GW address that pfSense shows - hence the comment above, but that may be a red herring).
Hopefully still clear. Now, I have assigned wg0 on pfSense to an interface (WG), so in the pfSense Rules I do see WG (interface), and WireGuard (application / group). If I pass all traffic on WireGuard, Netflix works just fine. But if I don't, and instead do it through WG (the interface) ... nope, issues then. Here are the rules I was recommended to add to pfSense (WG interface),
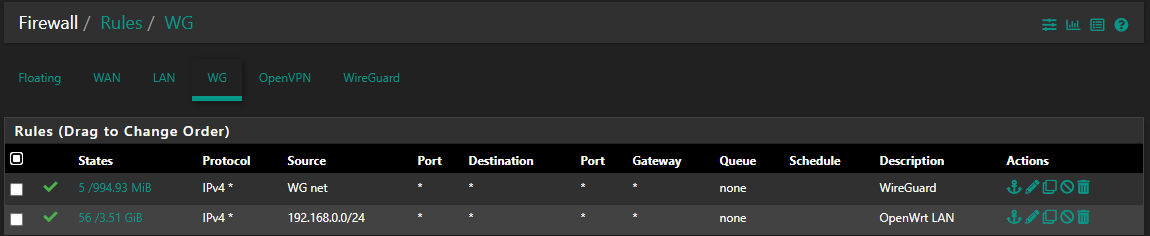
As you mention, I also have Outbound (Hybrid) NAT set up for the OW subnet, as it's not NAT'ing on the OW side. Here is that setup (and of course, on top of this I have the Automatic Rules) - BTW, I did ask, and I was told that the"Interface" here is supposed to be WAN, not WG (right?),
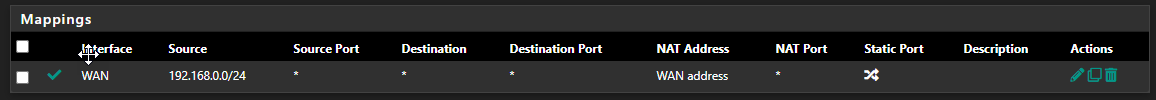
Still with me? Hopefully I'm explaining this OK. I agree with the recommendation that was mentioned in the other thread ... use the WG interface to ensure reply-to is enabled, but it seems to be part of my issue (as setting pass-all instead on WireGuard (group) allows Netflix to work).
Thoughts? Something here I have all messed up / misunderstood.
Thanks for the patience! And sorry for the long-winded summary
 .
. -
So you have a remote device using wrt running WG that you want to connect to pfsense, and get to stuff on your network, like a nas or plex server?
Not sure why you want to route traffic from this remote wrt box through your internet connection.. Why would you not just let them use their own internet, and only route through the wg vpn for access to your local stuff?
You want to route your internet through wg to this remote wrt box? Why?
Still at a loss to what your wanting to accomplish
you have
child - wrt --- internet (wg vpn) --- pfsense -- your network
Why would child not just use their internet, and pfsense use its internet. The wg is for you to talk to stuff on child network, and for child to talk to your network.
Why would you route netflix through wg or anything other than your 2 networks??
-
@johnpoz Two reasons actually
 ,
,- There have been a lot of security related issues with the university residence network - so I'd feel safer if all of her traffic comes back through here. Ya, it may just make me feel better ... LOL!
- The residence network does seem to have issues with a lot of things - almost any streaming video and audio is broken (even though they say it's fine, and the service is 100 Mb/s!). She can't even stream music to her Google Home Mini, and forget about Netflix (but I pay for 4 Netflix users ... arrgh!).
-
Not sure how you think streaming through your internet would make that faster? If they have a shared internet of 100mbps shared among how many students? Yeah its prob going to suck, routing through that internet to you isn't going to make it faster.. If anything slower..
The only reason to route their stuff through your internet would be circumvention.. She is behind a router, she is just as safe there as she is routing traffic through you.
-
@johnpoz Ya, I'm not sure it's speed - I tested, and she gets ~ 40 Mb/s back to here. Their DNS is really messed up, that I have seen / checked.
If this isn't going to work I guess I can go back to OpenVPN. That was working, it just requires a router reboot every couple of days (not sure why ... it's solid when running, just burps at times). And I admit, WG seemed like a challenge, so now it's more about proving I can get it working. Ya, I'm stubborn ... LMAO!
Thanks!