Adding VLAN based firewall rules.
-
Re: Setup problems with Vlans...
Hi,
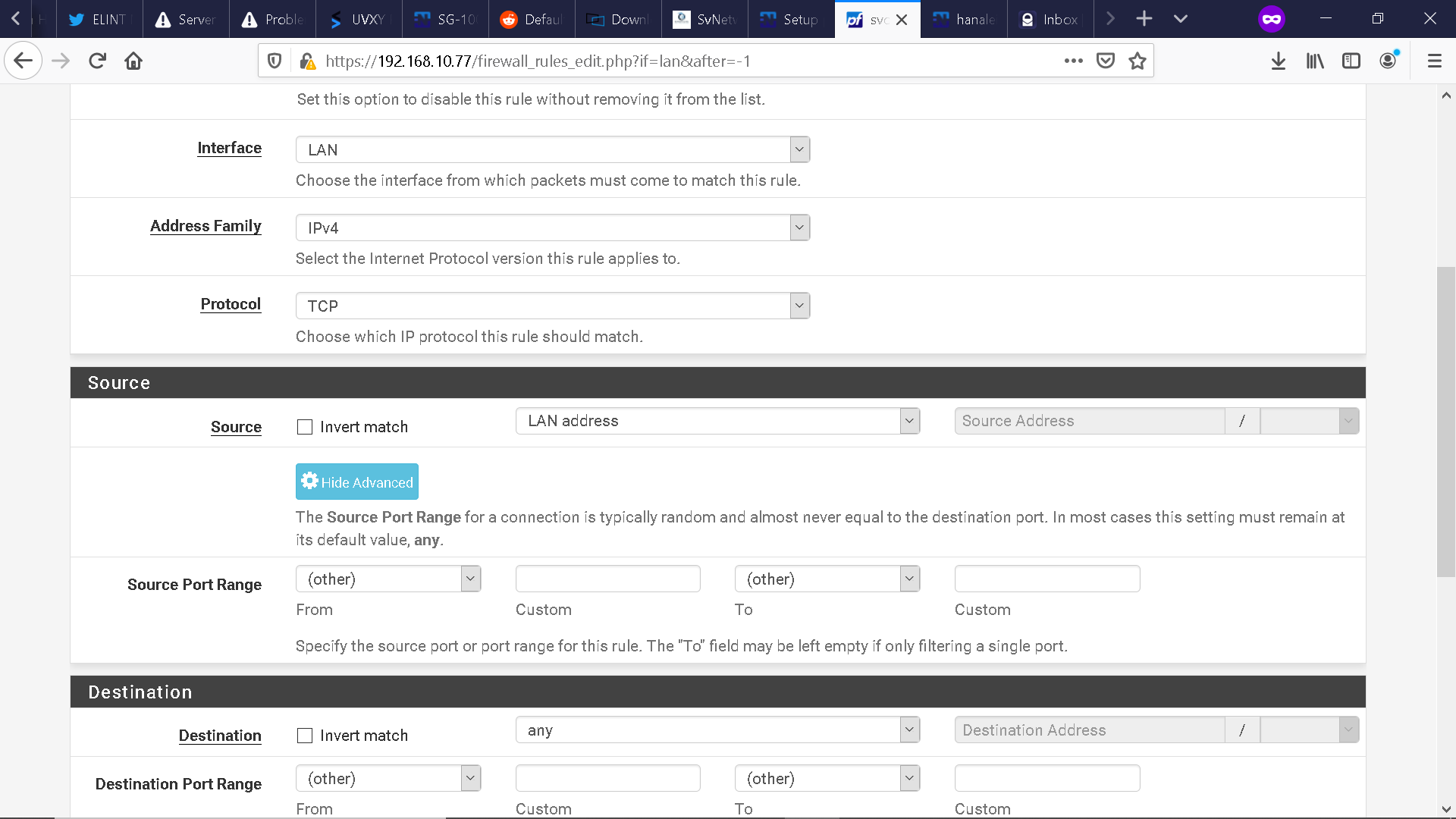
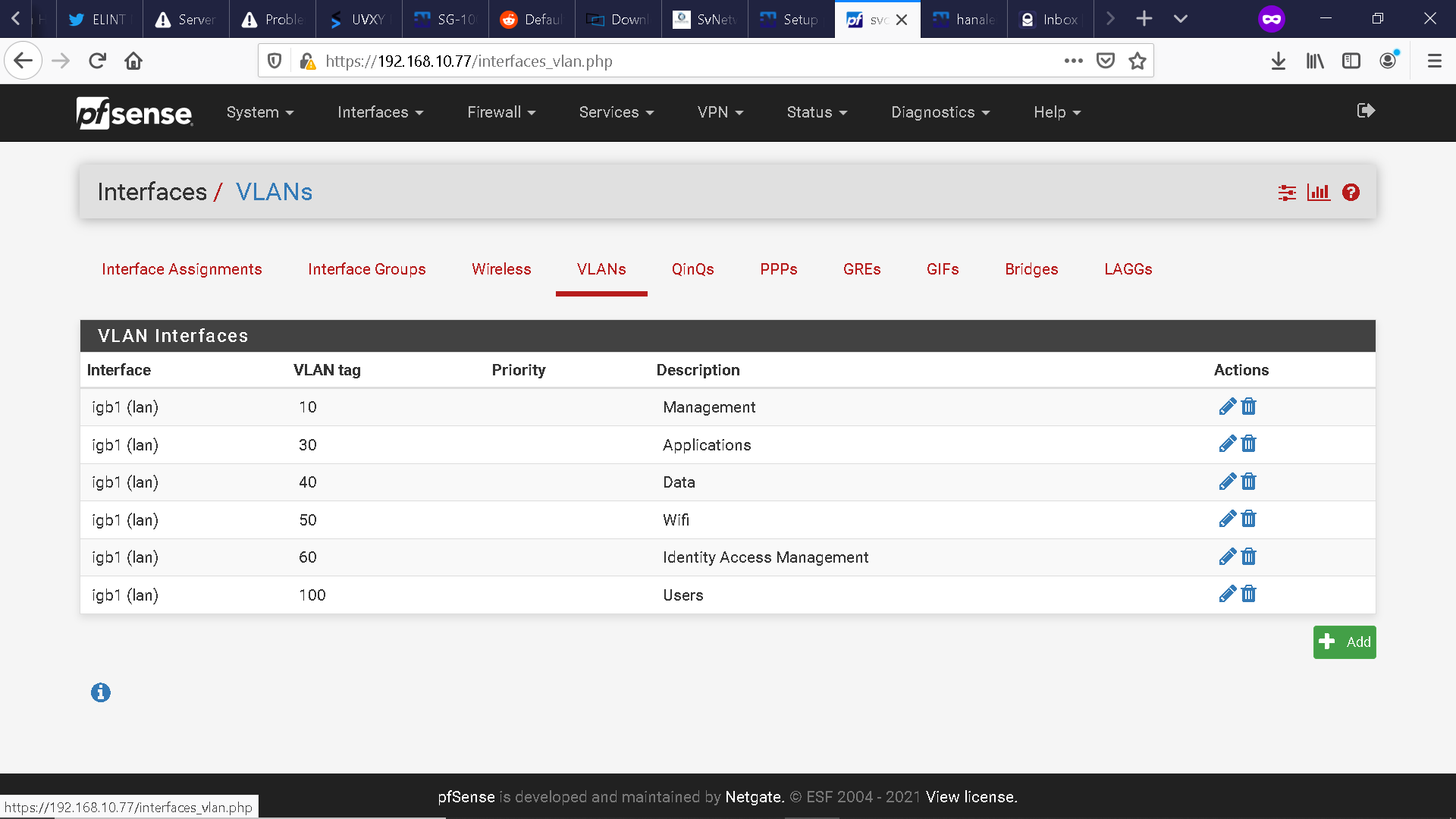
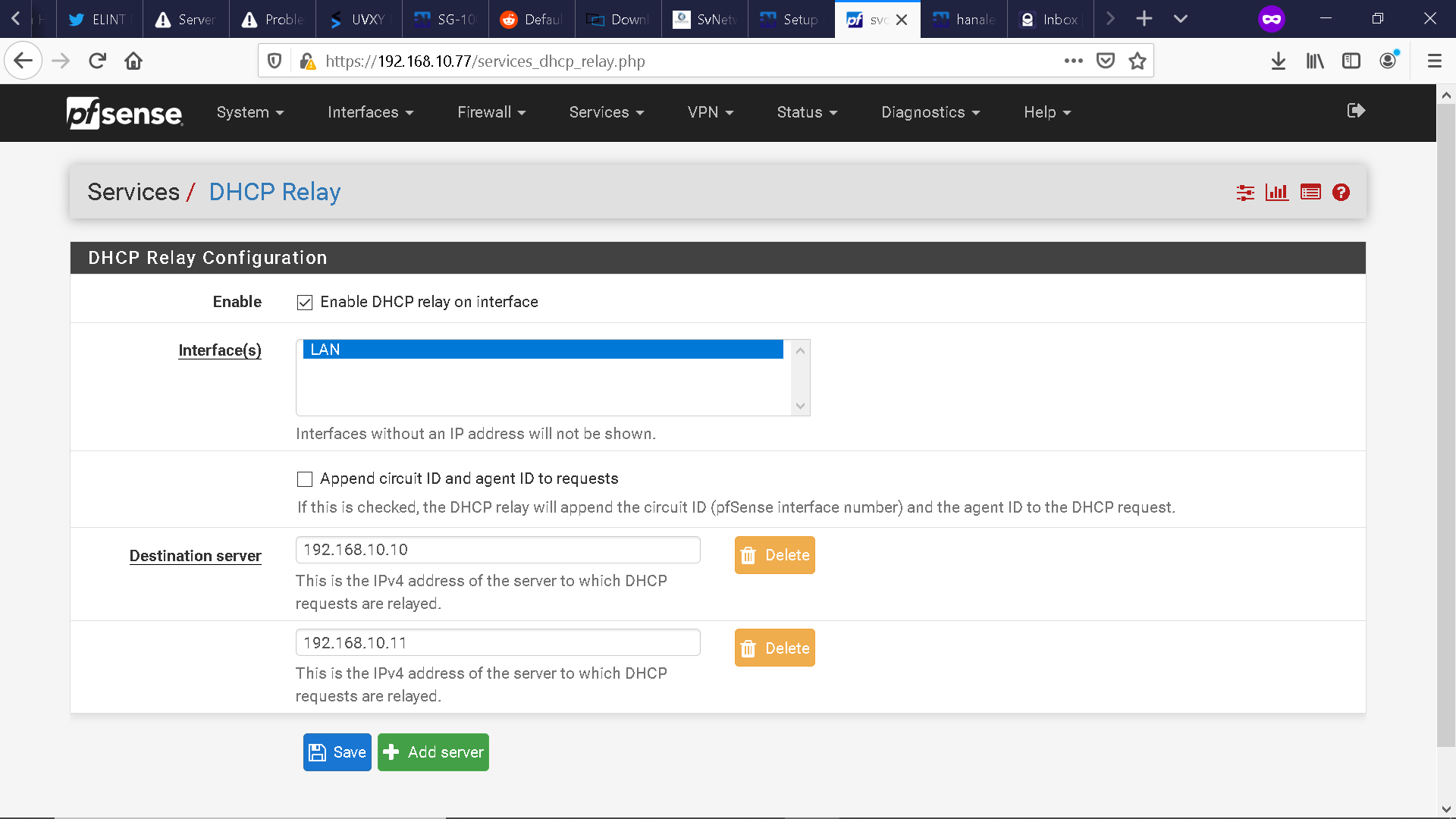
I purchased a SG-5100 not too long ago and I have one question so far: 1) How do I create VLAN based firewall rules through web configuration or console configuration on the LAN interface (in my case igb1)? I have included a snapshot of the Firewall screen, the Assignments - VLAN subsection screen, and the DHCP relay screen below.Just as an FYI, I am utilizing VLAN tagging via a Juniper EX3400 48 port POE switch.
I also have stood up two DHCP/DNS/AD domain controller servers on Windows Server 2019, one being a PDC (192.168.10.10) and one being a BDC (192.168.10.11).
I have one virtualized ESXi host that maintains the brunt of the infrastructure stack. I am tagging the respective VLANs to each VM in ESXi.
Many thanks in advance for you help!
-
There is no difference in creating rules for a VLAN compared with any other interface.
-
You are correct.
Once I created the VLANs in the console and assigned them to the igb1 LAN interface, things started jellying via the web configuration, whereby I could create subinterfaces for each VLAN and begin building rules to pass traffic between the VLANs.
At first the process was not completely intuitive until I toggled between the console and the web configuration to enable certain functionality.
One final question if that’s ok.
Do I need to create an additional firewall rule to allow dhcp requests to flow from one VLAN to another or is that traffic already passable since the DHCP relay is configured?
Many thanks again for your expeditious response!
-
You do not create a rule to allow DHCP to pass. You create a DHCP server for each interface. That's on the DHCP Server config page, where you will see the various interfaces listed across the top.
-
I am not using the native pfsense DHCP server. I am utilizing a centralized DHCP server stood up in a Windows Server 2019 virtualized environment.
Do you mean to say that I just need to enable the DHCP relay on each subinterface to pass the DHCP requests to the Windows DHCP server?
-
Yes, you would need a relay agent for each interface, just as you would for a DHCP server. DHCP uses broadcasts to the local network and doesn't go any further on it's own. That's where the relay agent comes in.
-
Hi. Another question if that’s ok.
So far I am able to get a DHCP lease for every VLAN subinterface defined with a relay, but I am not able to ping the gateway for any respective VLAN; e.g 192.168.10.1, nor am I able to ping 8.8.8.8 from a client connected to the Juniper EX3400 switch. The SG-5100 is connected to the very same EX3400 switch.
I am able to ping the VLAN gateways from within the SG-5100 (the statically assigned DHCP relay subinterfaces; e.g. 192.168.10.1, 192.168.30.1,192.168.40.1,etc...) using the Diagnostic->Ping tool.
I am also able to ping 8.8.8.8 from within the SG-5100.
I am also able to ping 8.8.8.8 and browse the internet when my client is connected directly to the LAN Interface on the SG-5100.
I do have firewall rules that allow any traffic from a respective VLAN net to the LAN net and WAN net.
Just as an FYI that I have mentioned before, all my traffic is tagged.
Ultimately my question is, why can’t my clients and VMs ping their respective VLAN gateways and ping the net?
Many thanks in advance again for your help!
-
@hanalei_boy said in Adding VLAN based firewall rules.:
but I am not able to ping the gateway for any respective VLAN
Try creating a rule to allow ping.
-
But isn’t “allow ping” encapsulated in a rule that says Allow any traffic to pass from VLAN xyz to destination ?
-
You'd think so, but it's not hard to give it a try to see what happens. Put it first, so that nothing else can affect it.