configure PfblokerNg to redirect traffic on the OpenVPN interface?
-
@hieroglyph redirect pfbloker and geoip traffic on openvpn interface
-
@antonio-briguglio Please show an illustration of what you want to do.
-
@hieroglyph hi I'm Sicilian and not American. I have a little trouble understanding you with the language.
I was clear in the previous post I need to know how to forward pfbloker traffic on the openvpn interface since when I connect with openvpn and try to check if a website such as facebook that I have blocked unfortunately with openvpn connection does not block it while on lan network is blocked.
I can't explain anything to you ....
thank you for your patience -
@antonio-briguglio No problem. Ok, I think I understand what you are asking now.
How to block traffic with pfblocker when remotely connected to your pfsense box using openvpn?
Go to Firewall > pfblockerNG > IP. Scroll down to "IP Interface/Rules Configurations". Select the LAN interface, select the openvpn interface, and save.
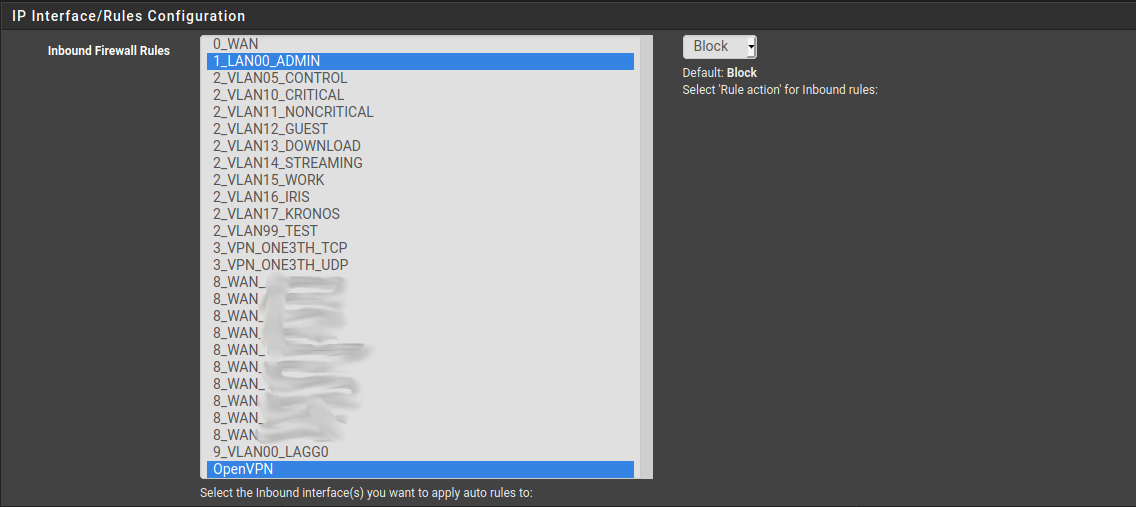
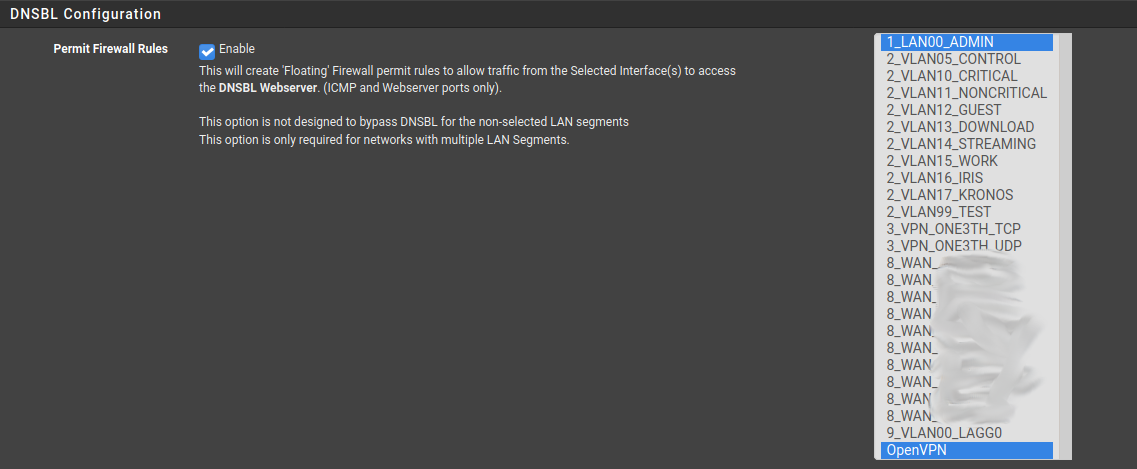
Go to Firewall > pfblockerNG > DNSBL. Scroll down to "DNSBL Configuration". Select the "Permit Firewall Rules" checkbox. Then select the LAN interface, select the openvpn interface, and save.
Go to Firewall > pfblockerNG > Update
Select reload.
Select all.
Select run.
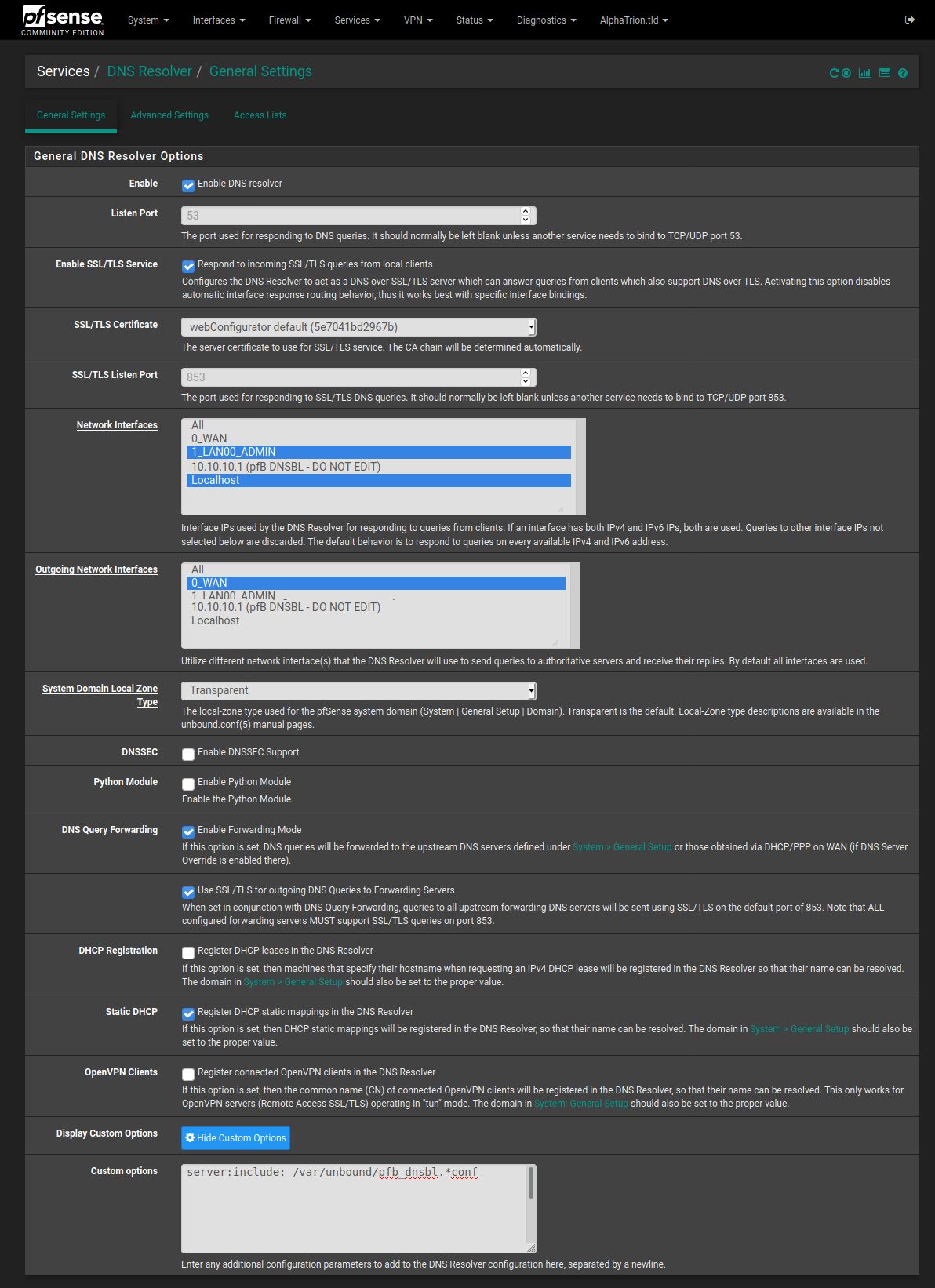
Wait for it to complete.Go to Services > DNS Resolver. Scroll down to "Network Interfaces". Select the LAN interface and the openvpn interface.
Scroll down to "Custom Options" and verify this is in the text box:server:include: /var/unbound/pfb_dnsbl.*conf
Select "save".Go to Firewall > Rules. Select "Floating". Make sure LAN and openvpn are shown as interfaces in the automatically created pfblocker rule.
-
This post is deleted! -
This post is deleted! -
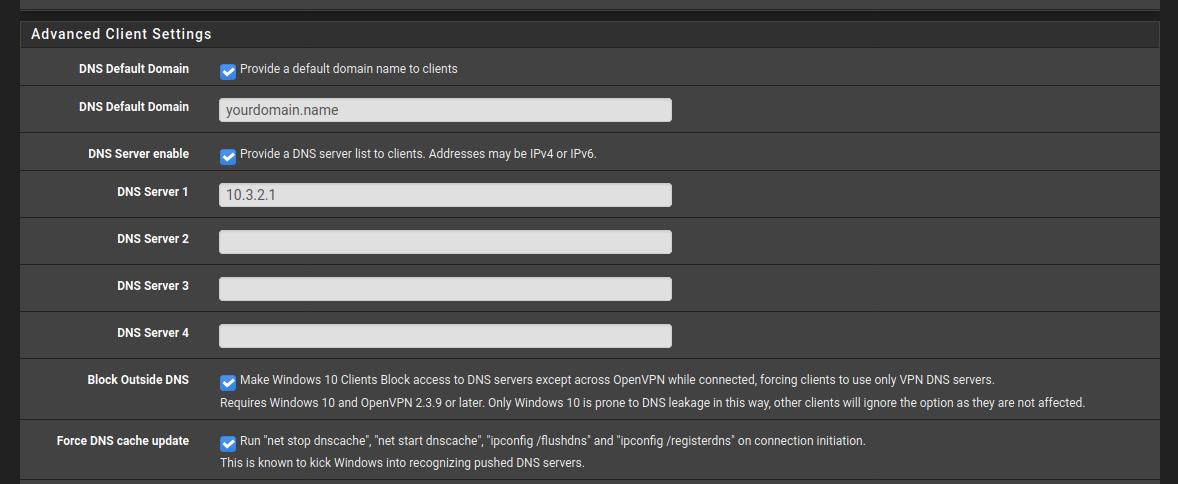
@antonio-briguglio Is your openvpn server setup to force clients to use it as their DNS server?
-
@hieroglyph yes
-
This post is deleted! -
This post is deleted! -
This post is deleted! -
@antonio-briguglio
Go to Firewall > pfblockerNG > IP
If pfblocker is setup the way the rest of pfsense is; "Inbound Firewall Rules" would apply to the LAN and openvpn interfaces. Not the WAN interface. Unless you have a special condition requiring WAN to be included as an inbound interface. Usually pfblocker rules are not needed on LAN because the default action is to block all traffic trying to enter thru the WAN. In this case, inbound rules should apply to the traffic coming into pfsense from from the LAN and openvpn interfaces. Treat the openvpn interface as just another LAN interface.Outbound firewall rules most likely do not need to be selected. But I must admit it has been an while since I have used the pfblocker auto-rules. I cannot remember if I used outbound firewall rules at all.
The DNS Resolver settings, the Network Interfaces should be LAN, openvpn, and localhost. The Outgoing Network Interface should be WAN.
-
@hieroglyph thank you :-)