Can I connect to switch UIs on tagged vlan interfaces from devices on non-vlan interfaces? Any workaround?
-
Hi,
First off, my sincere appreciation to the contributors on here. Self-proclaimed noob though i have 20 years of (simple) networking experience. Because of this forum (and others), and the contributions, I have created a great (vlan-aware) network. One nagging issue that I can't find through the googles.Ok, the BLUF (bottom line up front): I would like the ability to access my managed switch UI's that are tagged on a management VLAN from non-vlan interfaces without sacrificing the security aspect of VLANs. Be kind please, noob... The reality is I'm pursing this for the outcome, but ALL of this has been to learn, learn, learn (and I have a lot-thanks!)
More specifically: Should I be able to talk to devices on tagged vlan ports from simple LAN ports? If my understanding of vlans is correct, then the answer is 'no dummy' - then, next question: are there ways of routing "simple" LAN traffic to those devices that are on tagged interfaces?
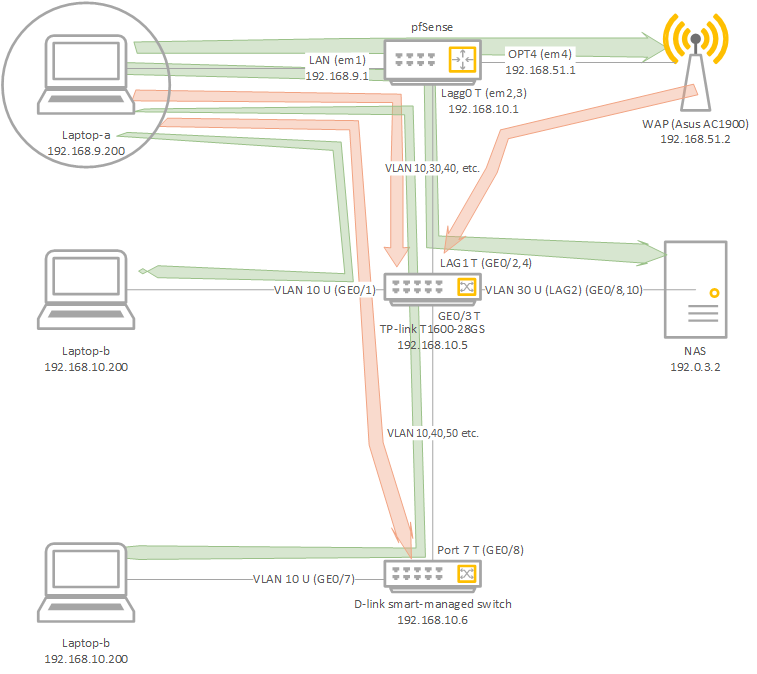
Background: Overly complicated (learning!) network, but after many lessons, it actually works like a charm. Basic idea is that I have everything on vlans except 2 ports on the pfsense box itself: em1 is my "backup" allowing me to access pfsense if I mess up something (yeah, a lesson learned), and em4 which goes to my non-vlan capable asus AC1900 wap. Overall, everything works great, vlans segment and route through the pfsense; that's why I kept the wifi off a vlan to avoid the routing overhead. the TP-link is a layer 2 managed with some layer 3 functionality, the d-link is a "smart" managed, but limited switch.
The management vlan is vlan10, and the ports between the TP-link and D-link are tagged with vlans, 10,20, 30 etc. I created a native vlan and blackhole vlans; the native is untagged between the two switches, and the black hole is used for any unused ports. An LACP Lagg0 connects the pfsense to the TP-link, and another to the NAS, but a single link connects the two switches.
So, when I plug into LAN (em0), or from the wap (em4), I'm not able to access the TP-link or dlink managed switch UI's. Though I can talk to end devices through them both. And I think this is due to (my) design. But I'd like to confirm this, and is there a "workaround" that doesn't cause me to open up my management vlan (vlan10)?
The part that alludes me is the fact that my LAN ports are able to talk to my NAS and any other untagged device (routing through the vlans on the switches), but the two devices that are tagged: the switch UI's, I cannot access - this is my assumption, but I don't know enough to troubleshoot properly.
I sincerely appreciate any assistance in learning or discovering a work around. I spent much of last year combing through forums and manuals, so not afraid to go hunt, and I probably have not provided nearly enough information, so please let me know what else I can supply (I may regrettably have to ask "how" or where the RTFM is...)
I apologize for the awful diagram, though I hope it helps show what I'm trying to do. Happy to provide more specifics.
THANK YOU!
-
@olgecko00 Trying to access 192.168.10.5 and 192.168.10.6 from the 192.168.9.x network will require a firewall rule permitting 192.168.9.x traffic to VLAN10. If you already have firewall rules permitting this you can run a packet capture in pfsense to see if 192.168.9.x packets are making it to the 192.168.10.x network. If there are no packets the firewall rule(s) allowing 192.168.9.x to access VLAN10 are not matching the packets as expected (i.e. the source, destination, ports, protocol, etc... is not right). If there is traffic and the switch is not responding it may be the switch is configured to only respond to traffic from a VLAN10 IP. In this case, create an outbound NAT rule to allow pfsense to translate packets from 192.168.9.1 to appear to come from 192.168.10.1 on the VLAN10 interface, which will "trick" the switch into thinking the packets originated from VLAN10.
If needed, check out these pfsense docs on outbout NAT.
Here and Here. -
@olgecko00 said in Can I connect to switch UIs on tagged vlan interfaces from devices on non-vlan interfaces? Any workaround?:
Ok, the BLUF (bottom line up front): I would like the ability to access my managed switch UI's that are tagged on a management VLAN from non-vlan interfaces without sacrificing the security aspect of VLANs. Be kind please, noob... The reality is I'm pursing this for the outcome, but ALL of this has been to learn, learn, learn (and I have a lot-thanks!)
If you're planning on passing through pfsense, from another interface, yes you can, but as described in another post you'll have to ensure the rules allow it. If you connect that unmanaged switch to an access port, configured for VLAN 10, then yes you can do that too and it will have nothing to do with pfsense, as you're not doing any routing.
-
Thank you both for your time!
- thank you for the suggestion on NAT, I need to do some reading on that, I thought that only applies for traffic between WAN and internet interfaces.
I just installed wireshark, but I definitely need to get smarter at reading the output. I know enough to be dangerous...but not smart LOL.
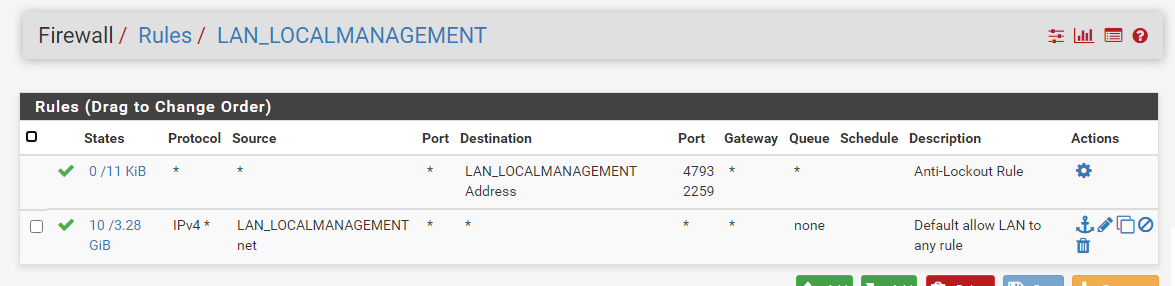
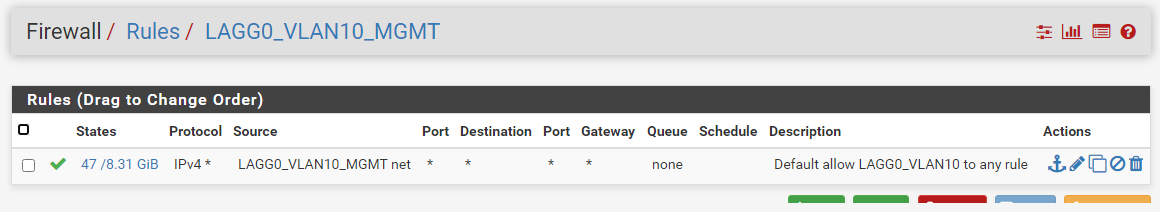
For both interfaces, firewall rules are basically empty shells with two exceptions - I've added a default any all to both, and currently the pfsense-set anti-lockout rule, which I'll tweak later.
When plugged into vlan10 (switch-1, port 1/0/1): no problems! I can access anything on the network, no limitations, including the switch interfaces. But with the two LAN interfaces (pfsense em1, OPT4), I can access anything except the two switch interfaces. And my suspicion is that the two switch UIs are seen as "tagged" on vlan10? Kinda thinking out loud, it's like if i'm on vlan10 on an untagged port, then the tag gets added to my frame and is correctly routed and switched to the device awaiting the tag on vlan10. But if I plug into the LAN interface, no tag is added, thus it would normally traverse the native vlan, but that is not setup between pfsense and switch-1. (due to what I've read, I only have them untagged on switch-to-switch ports).
Config of Switch 1: (port 1/0/1 that I'm connected to is PVID 10)
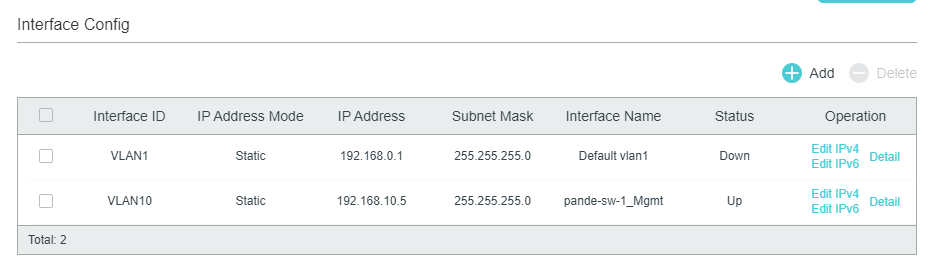
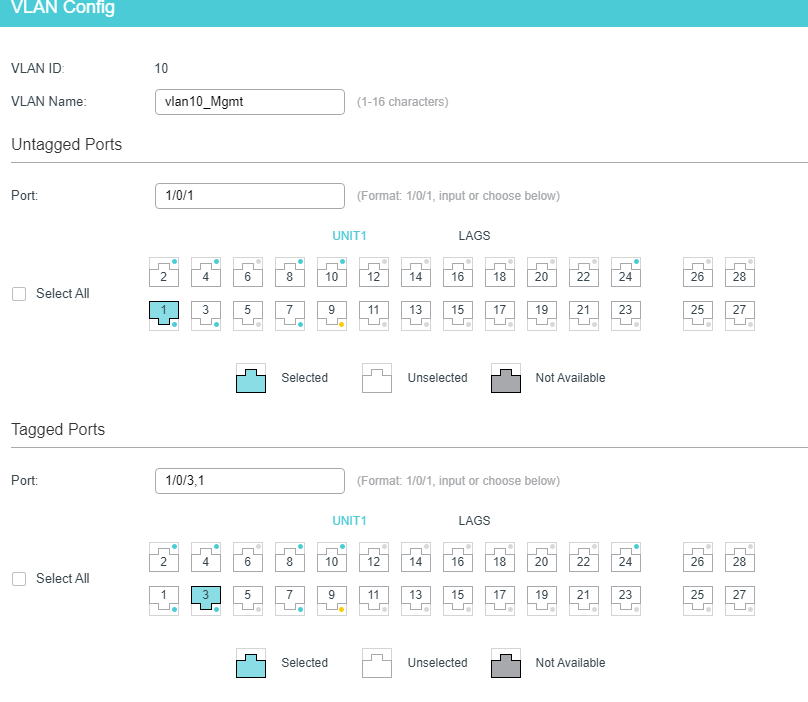
Switch 2 is effectively the same. The tagged port 1/0/3 happens to be the port connected to switch-2. Native vlan 254 is untagged on port 1/0/3 for both switches. LAG 1 is what connects switch 1 to pfsense box:
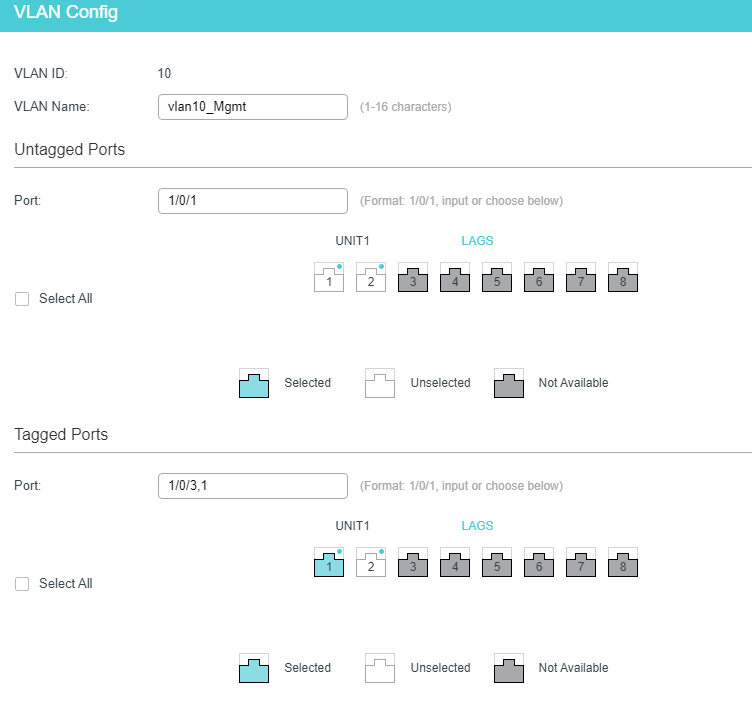
What perplexes me, is that though the two pfsense LAN interfaces cannot talk to the switch UI's, they can talk to endpoints running on any of the vlans (i.e. I'm able to ping a machine from pfsense LAN to 1/0/1 on switch 1).
i.e. I feel like I'm missing a nugget of knowledge to give the me the "ah-ha/duh" moment. My hypothesis is that the two switch interfaces are expecting tagged traffic, but don't get it from the LAN interfaces, which is fine, but it leads to my confusion, then what is allowing them to to connect to my endpoint devices on the vlans?Thank you both again, I'll take a few stabs and see what happens.
Thanks!
-
@hieroglyph , @JKnott ,
FIXED!
TL;DR: Could not understand why pfsense was not passing and/or routing untagged traffic to switch UI's via tagged interfaces, but no problems with any untagged<-vlan->untagged device traffic. solution: my ID10T mistake: uncheck "Enable Static ARP entries" in DHCP on the interfaces of the devices, or add the static APR entries necessary for all devices (hosts and switches...) to talk. Look for states in state table.
Dumb*** move on my part. Posted for all to read and groan/laugh at the noob...as the saying goes "KISS"...but, it's as much about learning as doing. And, I now have SSH for all my devices installed, putty/mobaXterm/wireshark installed on all my machines, and also WSL with ubuntu to help me out in the future :)
Ok, after i tried a ton of reading, pinging, capturing, triple checking/disabling rules and trying the outbound NAT, and that didn't work either, in the process I noticed something else recently changed: whereas before I could ping "just fine" from any of my vlans, well, my primary vlan stopped seeing the switches also... I like these types of failures!
So, resetting my assumptions, after more google-fu, I looked at the state tables (recommended in other posts), and realized there were no states in pfsense for switch-1. Well, if pfsense can't see it, pfsense won't route to it, but the other devices were present.... hmmm....as if the switch(es) weren't allowed....
I thought I'd try to add a static ARP for switch-1 - and... that's when I noticed that at some point in my former brilliancy, I happened to check the "Enable Static ARP entries" in DHCP on the VLAN10 interfaces. Now that's all fine and good as it had the machines I wanted to connect with, BUT no entries for switch-1 (or 2)! Added them to the VLAN10 interface since that is what they communicate to, and EVERYTHING is groovy again! Now I can use the firewall rules to fine tune access, and avoid NAT for now, as future challenge will be VPN's....I may be back...
Anyhoo, thank you again @hieroglyph and @JKnott for your time and help giving me direction!