Client cannot connect to OpenVPN from non-local network
-
@viragomann Thanks for replying. I'll add as much as I can, if you need anything specific, do let me know.
I used the Wizard to setup the VPN in this run but I have tried a lot of other methods from other tutorials.
Most things left as they were in the server setup. IPV4 UDP.
What I changed/added:
Tunnel Network: 10.0.0.0/24
Compression: Adaptive LZO
Enable NetbiosFirewall:
WAN Rule
Port: OpenVPN (1194), Protocol IPV4 UDPOpenVPN Rule
Destination: Protocol IPV4 UDPNAT Outbound Rules are Automatic but include the Tunnel Network.
Users and Certs were created by the Wizard and I am able to export and try them using my phone's cellular network to test.
-
@sna290130
Now, what's about the logs? Each, server and client writes log files which may provide hints to the problem.@sna290130 said in Client cannot connect to OpenVPN from non-local network:
OpenVPN Rule
Destination: Protocol IPV4 UDPThat's not needed. The UDP connection is coming in on WAN. The OpenVPN is the virtual interface (group) which the VPN clients are connected to. So here you have to allow the tunnel traffic from the client. The wizard adds an allow-any rule there.
@sna290130 said in Client cannot connect to OpenVPN from non-local network:
NAT Outbound Rules are Automatic but include the Tunnel Network.
Outbound NAT rules are only for outbound traffic, i.e. when you pass the VPN traffic from the client out to WAN. Don't know if this is your intention.
However, as you stated, the clients cannot connect. So that has nothing to do with the outbound NAT. -
Here is the client log:
Connecting to [192.168.0.11]:1194 (192.168.0.11) via UDPv4
EVENT: RESOLVE
EVENT: WAIT Server poll timeout, trying next remote entry...
EVENT: RECONNECTING
EVENT: RESOLVE
Contacting 192.168.0.11:1194 via UDP
UnixCommandAgent: transmitting bypass route to /var/run/agent_ovpnconnect.sockConnecting to [192.168.0.11]:1194 (192.168.0.11) via UDPv4
UDP send exception: send: Can't assign requested addressThere were no logs in System Logs > OpenVPN during the time of the connection.
-
@sna290130 said in Client cannot connect to OpenVPN from non-local network:
Contacting 192.168.0.11:1194 via UDP
The client tries to connect to a private IP. So I assume your "modem" is a router indeed and does NAT.
Do you have a static public IP or do you have a dynamic DNS name?
So edit the remote line in the client config file and put in into instead the private IP.In the client export utility you can put the public IP / name into the host box and save the settings.
So did you forward the OpenVPN traffic to pfSense?
-
@viragomann i've tried adding the public ip address to the file in the past and had no luck. Tried it again, I didn't know I had to add port forwarding rules for OpenVPN to the modem (Read that it's not necessary) but I tried it this go around and still no luck.
-
If your modem is a modem, then it can not do NAT. As NAT doesn't apply to a modem.
When you use a modem, your pfSense WAN IP is a non a RFC1918 IP.
Your client OpenVPN should use this IP.
If this IP isn't static (can change over time), you should use a DYNDNS solution, so you can have a host name point to your actual WAN IP.So,
What is your WAN IP ?
Where is your client OpenVPN situated ? Is it some phone using the OpenVPN client and the data carrier (3G/4G/etc) from your phone company ? (NOT the Wifi if your connection locally !!)Exemple :
My WAN OpenVPN firewall rule :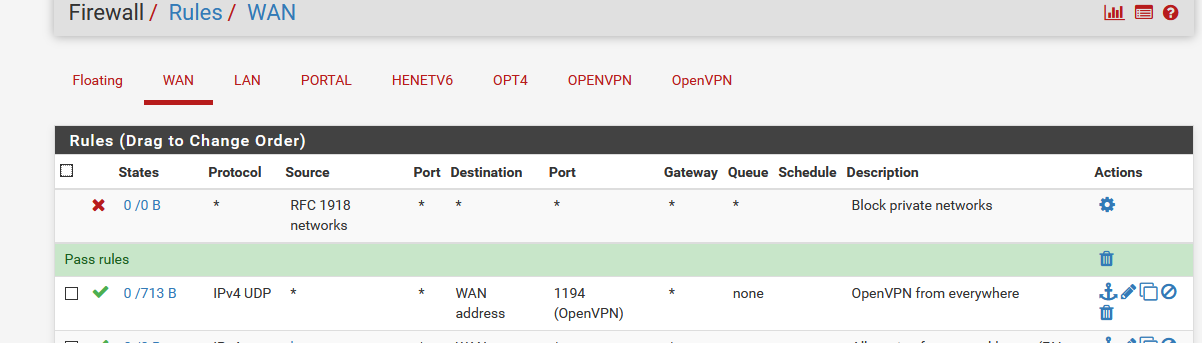
Initially, the (incoming) States and Bytes will be 0/0.
As soon as you connect to your WAN IP, the States will be a positive number, and the Bytes counter will .... count the bytes. This means your client - or some one else ;) is (trying to) connect.
If these two stay 0/0, this means that your OpenVPN client never makes it to your pfSense OpenVPN server. Most often, if not always, this is due to some up stream router/firewall.
Again : your local modem does not contain a firewall and doesn't have routing capabilities.Describe your network.
You can mention all RFC1918 IP's, as we all use the same.
Mention your WAN IP's - just mask the last byte. -
@gertjan Thanks for replying.
My network:
Internet
|
ISP Modem+Router (Just using to connect to PFsense) (LAN: 192.168.0.1)
|
PFsense (In Proxmox VM with it's own NIC) (WAN:192.168.0.x, LAN:192.168.50.1)
|
Wireless Router (192.168.50.x) -
@sna290130 said in Client cannot connect to OpenVPN from non-local network:
ISP Modem+Router
Put a NAT rule in it :
From any to 192.168.0.x, UDP, ports outside and inside 1194.
Done. -
This post is deleted! -
@gertjan Thanks, this worked. @viragomann thank you for being patient with me lol.
I tried different combinations of solutions that i found online that weren't working for some reason, including the ones that were posted here.
I tried this solutions initially tethered to my laptop and it didn't connect but directly on the phone it works. I will try again later again.
Edit: No LAN access. I searched that you need to add an outbound NAT rule for the LAN but it hasn't worked.
-
@sna290130 said in Client cannot connect to OpenVPN from non-local network:
Edit: No LAN access. I searched that you need to add an outbound NAT rule for the LAN but it hasn't worked.
Outbound ?
You ant to waccess your OpenVPN server, activated on your pfSense, from the outside, right ???You have a router in front of pfSense.
This router needs to contain an classic NAT roule.This NAT rule should take any UDP port 1194 on it's WAN to it's LAN port, using port 1194, and the WAN IP of pfSense, 192.168.0.x in this case.
There is no such thing as an "outbound" rule needed here. No need to search for it.
-
@gertjan Thanks for the explanation.
I had added that and coupled with the public IP in the config file, I was able to establish a remote connection but i am unable to access any internal addresses.
-
@sna290130 said in Client cannot connect to OpenVPN from non-local network:
but i am unable to access any internal addresses.
192.168.50.1 == pfSense works ?
Check with a 60 seconds setup : https://www.youtube.com/watch?v=jQHqPq7ftz4&t=310s&pbjreload=101
-
@gertjan Right. I cannot access Pfsense either. The VPN connects but there is no access to Pfsense or any other lan address (192.168.50.x).
-
@gertjan I checked the logs and did more research. It turned out to be a compression issue and I had to add push route... to the advanced settings. The config file was not changing the compression when it was no longer adaptive (Bug?) in the open vpn server config. So it kept on creating a file with adaptive compression. I commented out the compression line and it works now.
-
A AMartinelli referenced this topic on