OpenVPN client showing 100% packetloss following 2.5.0 upgrade
-
@rummonkey69 I don't have gateway monitoring enable aside "Do not create rules when gateway is down". I disable that as well and I'm getting same error Offline, Packetloss: 100%. I using two openvpn clients as well. I can't only point the issue to "Enable Data Encryption Negotiation" and "TLS keydir direction". On tutorial it show that uncheck Enable NCP which I guess replace with "Enable Data Ecnryption Negotiation".
-
I am having the same issue as well. I've been doing some research and tried a few different configurations on my VPN connection but no luck. Following this thread in hope that someone gets a lead.
-
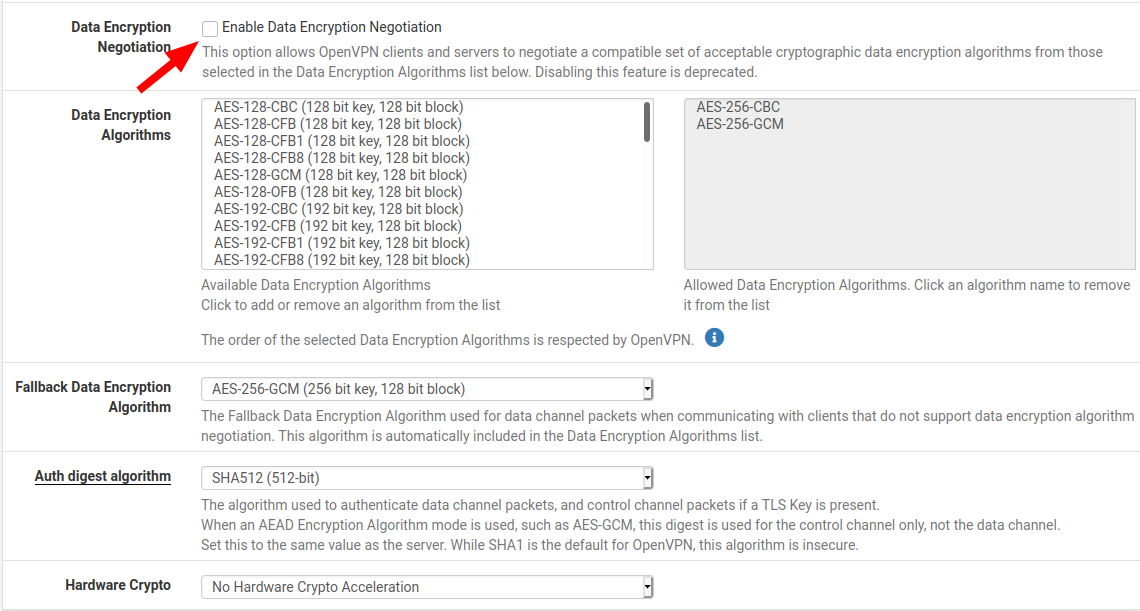
I played with the settings for a while and finally got it working by unchecking "Enable Data Encryption Negotiation". You might want to reboot after making this change.
-
@bjames88 Already tried that. so what confusing with the last sentence "Disabling this feature is deprecated." So unchecking does not do anything? So who is your vpn provider?
-
@bjames88 Thanks! This has solved my issue. I was pulling my hair out.
On top of that, Cloudflare had an issue in Chicago area tonight, which when navigating to www.nordvpn.com (and few others) caused 502 nginx bad gateway to be shown. Their app on android also didn't work for several minutes. -
@bjames88 thank you - this worked for me too
-
@nevar Deprecated means the feature will be removed in the feature but it is currently still available. It's not longer supported and will eventually be completely removed.
I use Nord as my VPN provider.
-
@bjames88 That's it. Thanks a lot! Everthing is working again. Worked right away, didn't even have to reboot.
-
I managed to get it work on Torguard somewhat. I need select AES-128-GCM instead of AES-256GCM for the Fallback Data Encryption Algorithm as well unchecked Enable Data Encryption Negotiation. But on Status > Gateways, it still showing Offline, 100% packet loss. Can you guy confirm if you still seeing that status ?
-
Relating to "Offline, Packetlost: 100%", Goto System > Routing, then edit the each vpn gateway you have and checked "Disable Gateway Monitoring" & "Disable Gateway Monitoring Action". Majority of VPN provider ignore ping which explain why you getting 100% Packetlost. This resolve my issue running multiple vpn clients. Since pfsense detects that gateway is offline since it didn't get ping response which causing some weird issue.
-
@nevar not true.
Reinstall clean of 2.5 and it's working as was before.
Doing upgrade and restore didn't fuck the issue.
-
@nevar thanks that worked for me
-
ok so doing that allowed the connection to work. However its now ignoring all my rules and routing everything thru the openvpn gateway. These rules have not changed in the last 2 years so something has changed with 2.5.0. I guess next step is to do a clean install and restore the config
-
ok, so a clean install did not work either. (restored config afterwards)
-
I have Torguard also and had the same issue.
System->Routing->Gateways->Edit-> Monitor IP - Set it to anything, I used 8.8.8.8
Now shows online in the Gateways. I believe it's an issue with ICMP over that gateway.
On an unrelated note, I had to dump OpenVPN because I couldn't get it to work with policy based routing. Either I had issues with the clients I wanted to connect through it or it took over as the main gateway for my LAN. I gave up and setup Wireguard as a client for now via Torguard. My policy based rules are working as they should.
-
@hypnosis4u2nv Here's my setting System > Routing > Gateways > Edit (Torguard)
Address Family: IPv4
Gateway: dynamic
Gateway Monitor: checked, Disable gateway monitoring
Gateway Action: checked, Disable gateway monitoring action
Force state: uncheckedHow do you setup wireguard as a client?
-
-
@nevar You don't need to disable monitoring, just use an IP to monitor and set it on the Monitor IP setting.
Go to the configurator page on Torguard, set it to Wireguard, choose your server location and plug in the private and public keys you generate in pfsense. It will pop out a configuration, just plug that data in Wireguard and into the peer.
Add a NAT rule for your WAN to LAN (or any other interface)
Add a firewall rule to allow any (everything) for the Wireguard interface.
Under LAN (or any other interface you set in NAT) allow any protocol, source set to whatever you want (I'm using aliases for certain devices), go to advanced tag the traffic (I use vpntraffic) and set the gateway to wireguard.
Create a floating rule for WAN block traffic, Any for all, go to advanced, set tagged to vpntraffic (or whatever you used in the above LAN rule. This is your killswitch, if the connection drops to the VPN, nothing can access the internet via WAN. Test Wireguard before you set the killswitch to rule out errors.
Enjoy Wireguard as a client.
-
@hypnosis4u2nv Did you post in the wrong thread? You're talking about WireGuard in an OpenVPN thread.
-
Nord has not posted their documentation for setting up NordVPN on pfSense 2.5.0.
https://support.nordvpn.com/Connectivity/Router/1626958942/pfSense-2-5-Setup-with-NordVPN.htm
I just went through this new howto doc and made a few changes to my current settings. Those were mostly in the crypto settings for the client config as far as I remember but you might want to go through everything. So far it looks good, I'm connecting and working though the VPN.