WireGuard VPN providers that support pfsense
-
-
@johnpoz I'm not too sure
I don't know if the VPN providers hide the keys inside the App.
When I spoke to NordVPN support for example, they informed me that they do not support connecting using pfsense routers using WireGuard protocols.
The NordVPN WireGuard service you would need to use the Nord Lynx service using the Windows app.
-
@dem That works out very expensive when you take the EGRESS and INGRESS data charges from the cloud provider into consideration
-
@n8rfe I use Amazon Lightsail and get 1 TB egress for $US 3.50 per month, but of course you might need more.
-
I think most VPN providers are going to say the same unless anyone here knows of a VPN provider that supports connectivity using pfSense and setting up the connection manually without using Apps?
Hence my post

This is direct from NordVPN support.
-
@dem said in WireGuard VPN providers that support pfsense:
Amazon Lightsail
The only problem with that way of connectivity is the EGRESS point at the cloud provider and the logs they will hold for the data exiting from your cloud account.
This is why VPN providers have their business interests registered in certain counties where law is not able to pull logs for customer data.
But if I'm wrong with this I stand corrected.
-
@n8rfe If you're going to use an external VPN, you have to trust somebody.
-
This is true but that is why it is important to select a VPN provider that does not log your connection activity and also has its business operations registered in a country that does not fall foul to law enforcement asking the VPN provider to hand over logs for its customers.
An example of a provider that does not hold customer logs and is registered in a country that cannot ask for customer logs is ExpressVPN.
-
PIA has a process to do it "manually", but it requires a series of api calls to register your public key and download a json blob that contains your connection details. Once you acquire the json blob then you use it to create your wg interface to establish the connection.
I've separated my PIA wg tunnels out to a linux vm, which pfsense uses as a gateway for policy routing traffic that needs to go out vpn. Then I wrote an app that manages and monitors the wg interfaces on that vm for me. It's basically a wrapper around
wg-quick.Now that I've upgraded to 2.5, I've started looking at if maybe I can remove the vm gateway and run it all on pfsense, but my initial thoughts are I won't bother. The manager app I wrote is never going to run on pfSense and my vm gateway gets the job done.
My app is based on the scripts provided by PIA here. I used those to figure out the api calls, etc. I needed in my app. I don't think it would be overly difficult to port those provided shell scripts to work on pfSense. The biggest challenges would be that those scripts assume and use
wg-quick, which isn't available on pfSense and how much work would be involved in taking the json blob from PIA and creating and configuring a wg interface within the pfSense environment (i.e. I doubt you can just start making calls towgto create a new interface on pfSense and the pfSense config/gui/etc just automatically noticing it). -
I don’t understand the appeal. I am reading it isn’t really geared towards privacy?
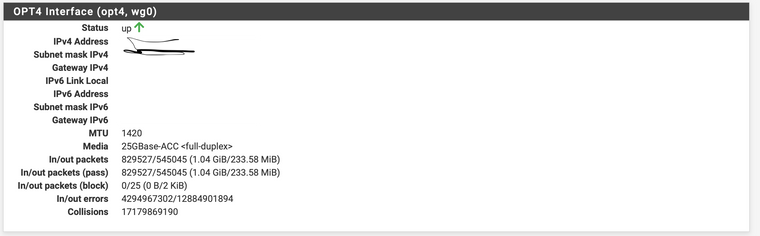
Of the 3 I tinker with one works. But I get thousands of collisions per kB transferred
No matter the server...
I originally posted only a few websites were working, that is entirely resolved now, but I refuse to let an unproven system run on my network
Just my opinion
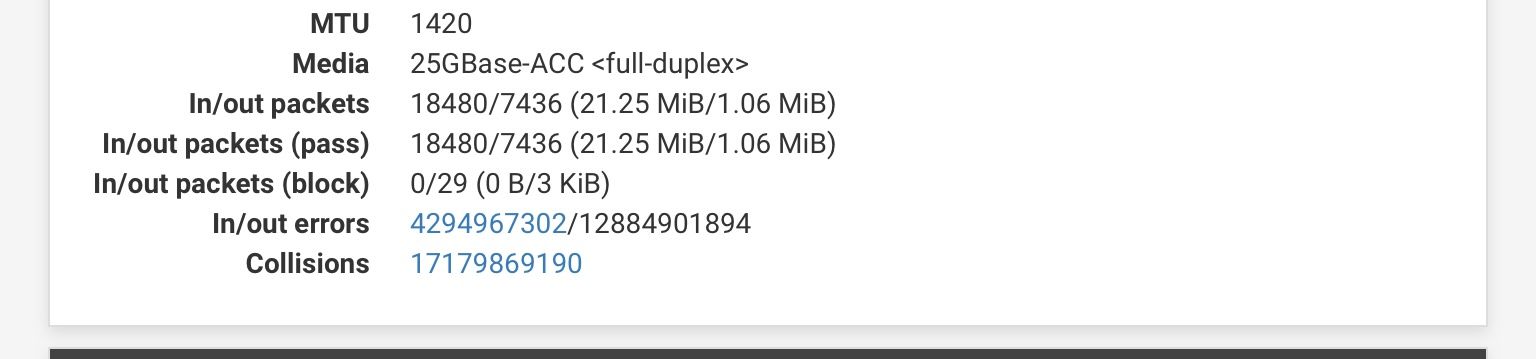
I am utilizing a sg 3100 -
@bcruze Definitely something wrong with your config. Should never have any collisions or errors really. Certainly not billions of them.
Wireguard itself definitely isn't about privacy. WG's purpose is security. A wg tunnel is secure, that's it.
As for the level of privacy using a commercial vpn, regardless of it using openvpn, wg or whatever, always be skeptical. I don't use commercial vpns for privacy or anonymity. If that's your expectation of these services, you're going to be disappointed. I use PIA 98% for getting around blackouts on my sports streaming services and 2% for downloading the odd "linux iso" here and there.
If you limit yourself to such benign activities, no one's going to bother you/care. If you think you can anonymize yourself using these services while doing sketchy stuff and find yourself on the radar of nation states, you're going to be disappointed when the three letter agencies track you down and show up at your door. :)
-
My purpose of using a VPN provider is not to do sketchy stuff. I like to limit what data i expose to the Wild West (logs etc) whilst keeping my connectivity secure.
-
My home ISP is AT&T and this is actual text from their Privacy Policy:
Here are detailed examples of types of information we collect from our Products or Services:
- Web browsing and app information includes things like the websites you visit or mobile apps you use, on or off our networks. It includes internet protocol addresses and URLs, pixels, cookies and similar technologies, and identifiers such as advertising IDs and device IDs. It can also include information about the time you spend on websites or apps, the links or advertisements you see, search terms you enter, items identified in your online shopping carts and other similar information.
One nation-state hack or disgruntled employee and all of the sudden everyone knows a lot about you.
So every device we browse from is on a personal AlgoVPN at all times using WireGuard, whether home or not.
-
@n8rfe Right, yeah, makes sense. I'd question what your expectations are of "keeping my connectivity secure", but otherwise yeah, vpns are good for nothing more than benign activities.
If you need to hide from nation states you need to do a lot more (and I mean a lot more) than just routing your internet traffic thru a commercial vpn.If you route absolutely everything thru a commercial vpn then you're basically hiding your activity from your ISP and pushing that trust down to your vpn provider. Is that more secure? I guess it depends who your ISP is. But eventually that traffic exits your vpn tunnel and hits the public Internet to reach its final destination.
-
@dem AT&T... damn! Ok, yeah, I'd probably route all my traffic thru a vpn, too. But the egress charges from cloud providers would kill me. I mean I ship 250GB of vm and other data backups from my home lab to the cloud every night. That doesn't even include the day to day traffic our house generates.
-
@slugger My only wired Internet option is DSL with 5.8 Mbps down and 0.41 Mbps up, so I don't have the problem of having to ship 250GB files around.

-
@dem Ouch, I feel for you.
-
@n8rfe Give Mullvad a try https://mullvad.net/en/servers/
Pretty easy to setup with pfsense and there is also a reddit thread https://www.reddit.com/r/PFSENSE/comments/l1uqkb/wireguard_works_with_mullvad/
-
Mullvad works 100%. I'm responding to you right now while pushing all my network traffic over a pipe through New York. It's 5 bucks a month and very privacy oriented.
-
@p1erre said in WireGuard VPN providers that support pfsense:
@n8rfe Give Mullvad a try https://mullvad.net/en/servers/
Pretty easy to setup with pfsense and there is also a reddit thread https://www.reddit.com/r/PFSENSE/comments/l1uqkb/wireguard_works_with_mullvad/
I am using a SG3100 W mullvad. can you please pass some traffic and see under interfaces of the bottom numbers ever change? ( specifically ran a 4k video to 1gb of traffic for the screen shot as you can see) see my first screen shot... the numbers are exactly the same... I wonder if this is a bug?