ExpressVPN - Geo-restricted website works when connected through their app over OpenVPN UDP but not through pfSense OpenVPN
-
Thanks for sharing your thoughts with us @Gertjan and indeed nothing new under the sun so-to-speak. But we are getting a little bit off topic here I think.
I still want to know what is different in pfSens compared to OpenWRT for OpenVPN client config and DNS leaks. Looking forward to the screenshots from @CrystalFire.
-
@CrystalFire said in ExpressVPN - Geo-restricted website works when connected through their app over OpenVPN UDP but not through pfSense OpenVPN:
by using ExpressVPN app, it just goes through fine - opens up and content plays too, however when I try to access it via pfSense OpenVPN - it just doesn't load completely.
Even if your are using the same
URL=> IP ( !) for ExpressVPN app and the OpenVPN client, nothing will guarantee you what the outgoing == your actual WAN IP - as seen by Netflix - is.One IP in their IP list can be listed, the other one not. It's purely random.
Maybe the App uses a privately known list with VPN server IP's, not known to the public - and the OpenVPN style of connections another list with IP per country.
Maybe the App uses another WAN style network ... etc.About the OpenVPN client : we / they all use the same open source OpenVPN, because why re invent the wheel as a good product already exist ?
Still, the App could be a mode made protocol.
At least, my iPhone ExpressVN is based on OpenVPN - the ExpressVN servers are based on a (modified by them to enforce accounting) OpenVPN.There is no such thing as
OpenVPN client 2.4.9 works and OpenVPN client 2.3.2 doesn't work.Your favourite VOD service can only see : your WAN IP and port. It can not see what is behind it.
Remember : when the VPN tunnel comes up, traffic starts to flow. For this VOD traffic, actually any type of traffic, the presence of the tunnel is not detectable for the destination address. [edit : the MTU might change]
IP packets, headers, payload, everything is the same. VPN tunnel ought to be transparent for the application (OS) on both sides. What changes on the client side is : the routing table changes. But this will not be visible to the destination side.
There are no bits or bytes or other info in the traffic (headers or payload) that says "this packet was handled by OpenVPN 2.4.9" - and the server is "OpenVPN 2.4.8".Take a look at https://serverfault.com/questions/480060/how-do-i-tell-if-all-traffic-is-going-though-the-vpn
pfSense uses : OpenVPN (server) :
[2.4.5-RELEASE][admin@pfsense.internal-wall.net]/root: openvpn --help OpenVPN 2.4.9 amd64-portbld-freebsd11.3 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on May 4 2020 .... -
@Gertjan said in ExpressVPN - Geo-restricted website works when connected through their app over OpenVPN UDP but not through pfSense OpenVPN:
[edit : the MTU might change]
https://medium.com/@ValdikSS/detecting-vpn-and-its-configuration-and-proxy-users-on-the-server-side-1bcc59742413
https://github.com/ValdikSS/p0f-mtu-script
http://witch.valdikss.org.ru/ -
@Gertjan said in ExpressVPN - Geo-restricted website works when connected through their app over OpenVPN UDP but not through pfSense OpenVPN:
At least, my iPhone ExpressVN is based on OpenVPN - the ExpressVN servers are based on a (modified by them to enforce accounting) OpenVPN.
This is exactly what I mean! The ExpressVPN app on the iphone is somehow always working with all VOD's. So the mtu detection (or VPN detection) as explained by @Pippin (great read btw) is somehow mitigated for if you use the dedicated VPN app. Off course there is always the IP-restriction but let's pretend that this is not the issue here.
I know that from 1st hand experience that the NordVPN app in iPhone is showing the exact same behaviour as the ExpressVPN app. Everything on Netflix, Disney+ or other VOD services cannot detect the VPN as long as you use the dedicated VPN app.
So how can we have this same experience from pfSense and the OpenVPN client configuration there? What combination of settings on pfSense can achieve the same level experience level as those dedicated VPN apps? Or at least come close...
Yes I understand that those VPN apps are maybe heavily modified versions of some VPN protocol and not opensource. But then again as @CrystalFire said earlier in this post, OpenWRT seems to be able to achieve that same level as the dedicated VPN apps.
-
@vjizzle Below screenshots are of pfSense configuration for ExpressVPN. Just getting you the relevant ones, let me know if you want screenshots for any other page. Hope you are able to match it against your configuration and fix your issue.
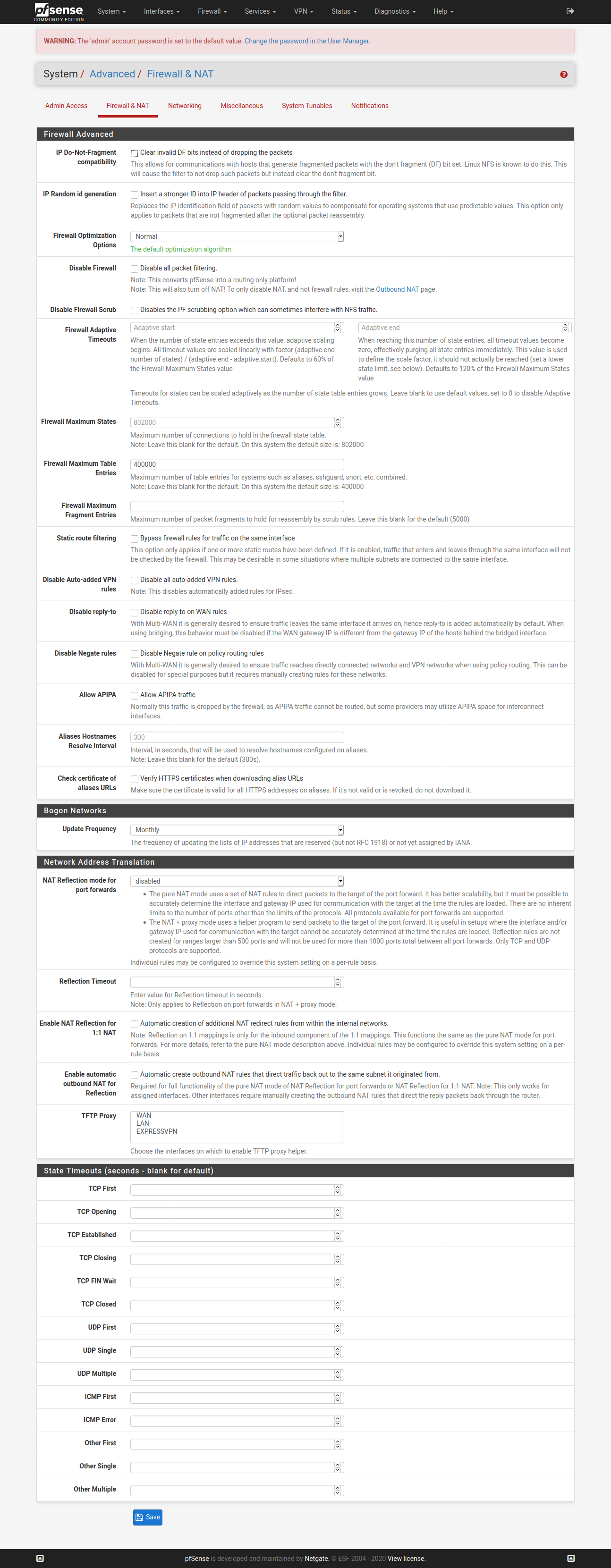
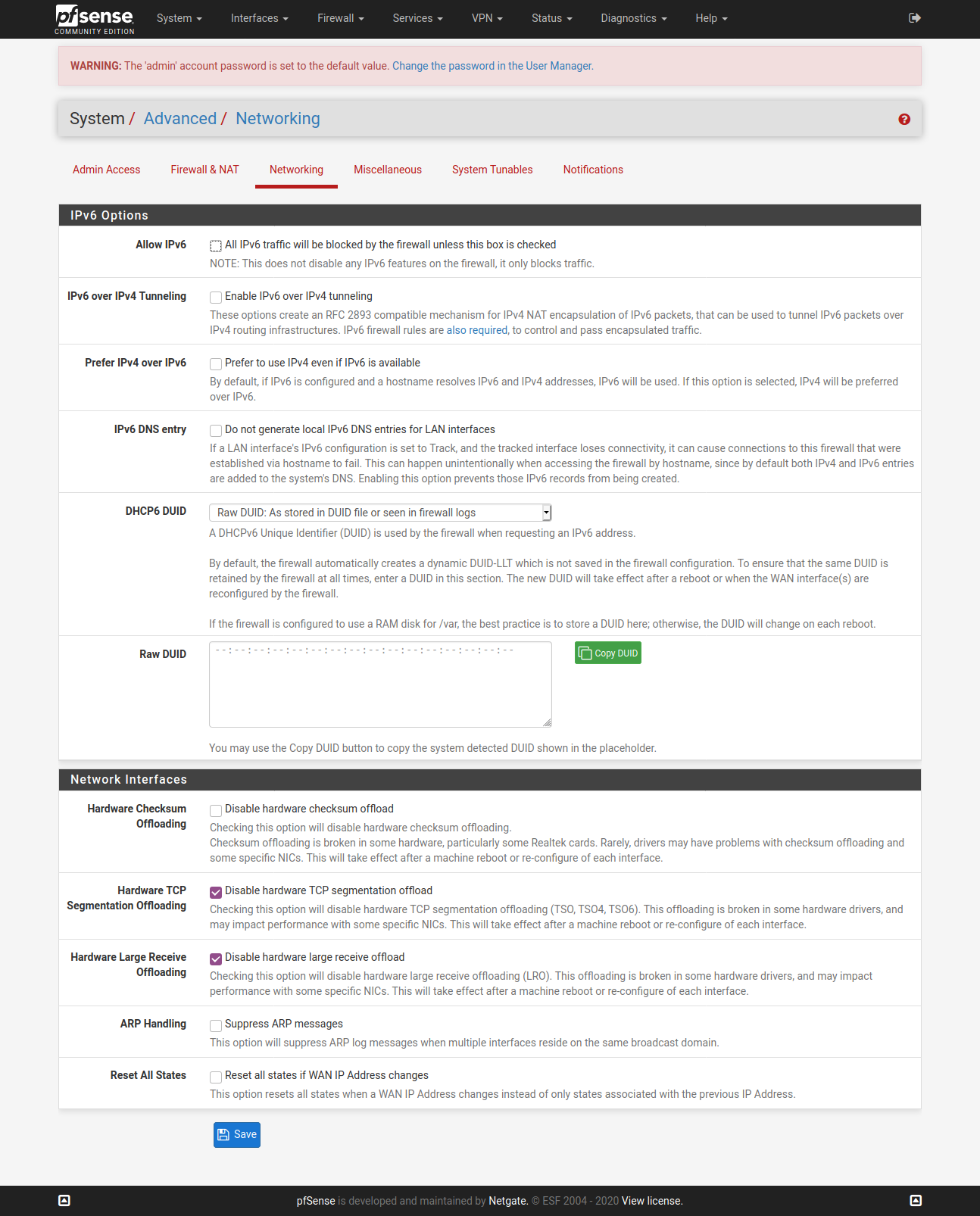
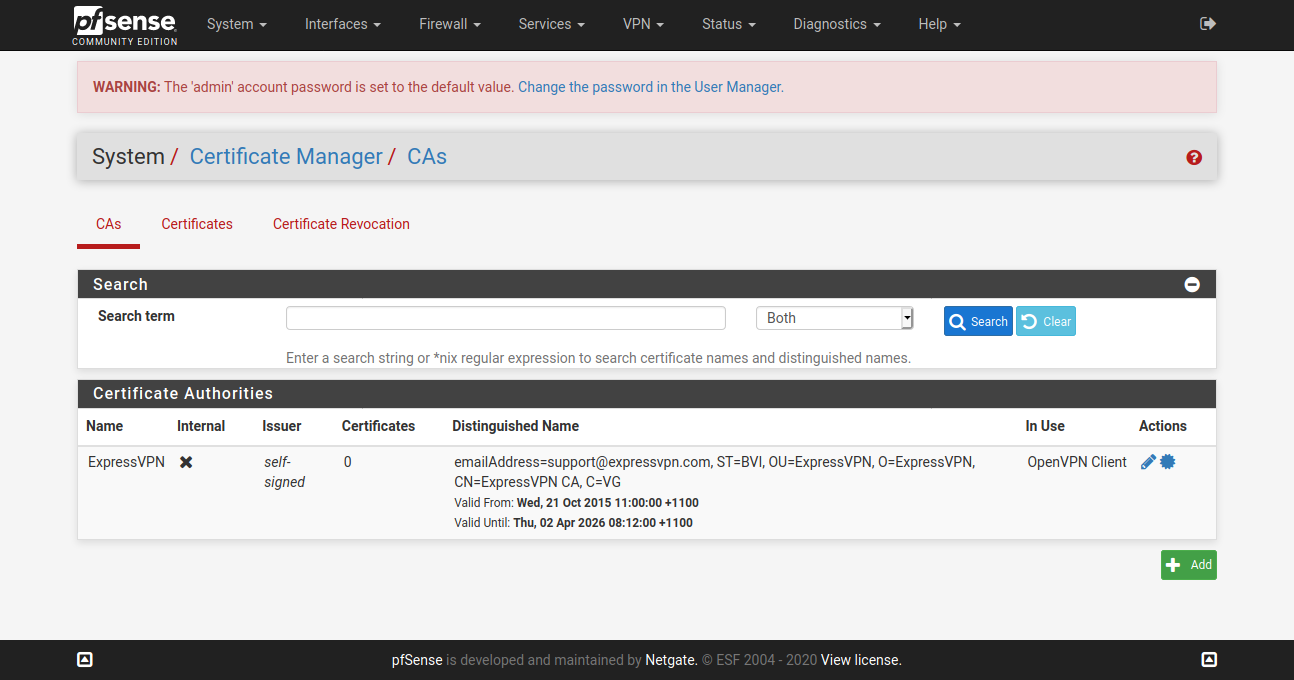
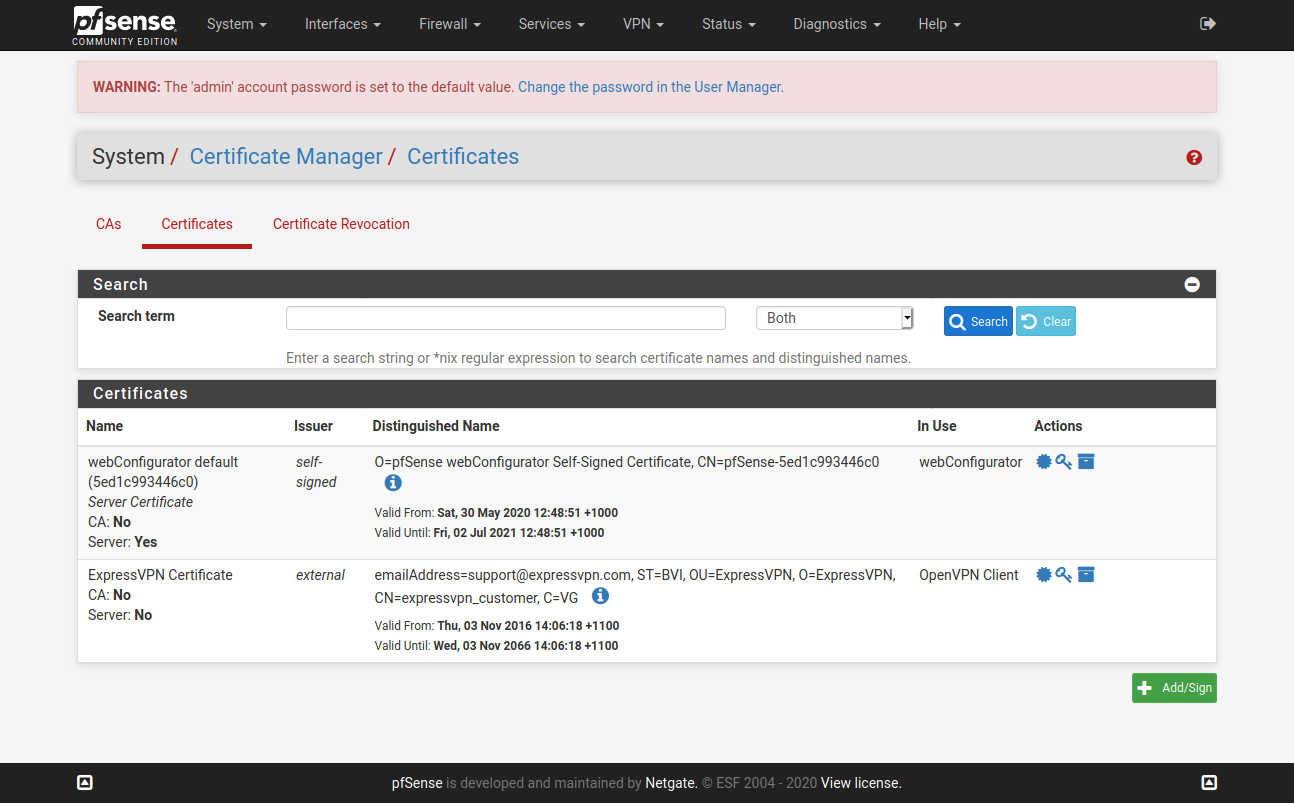
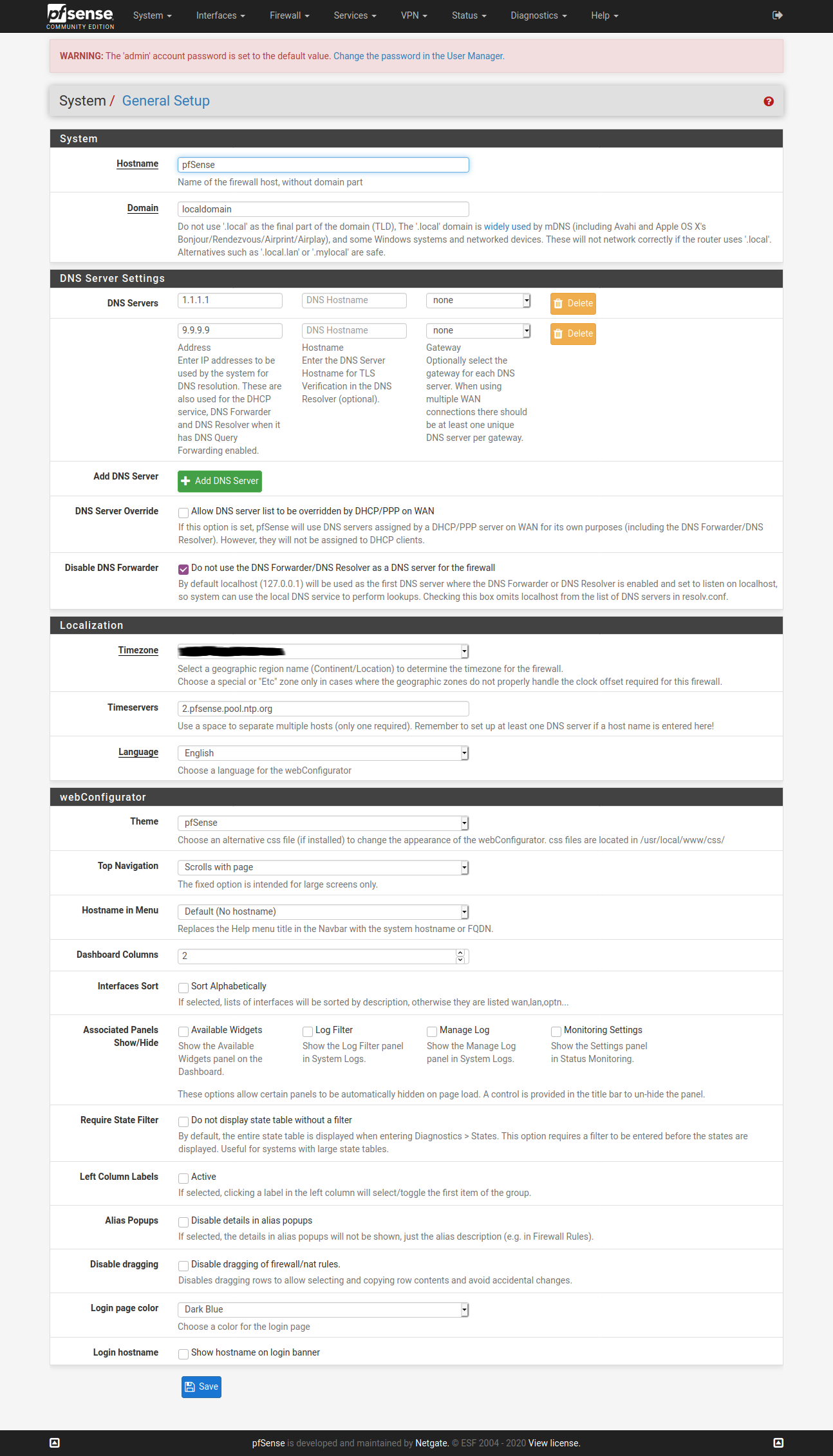
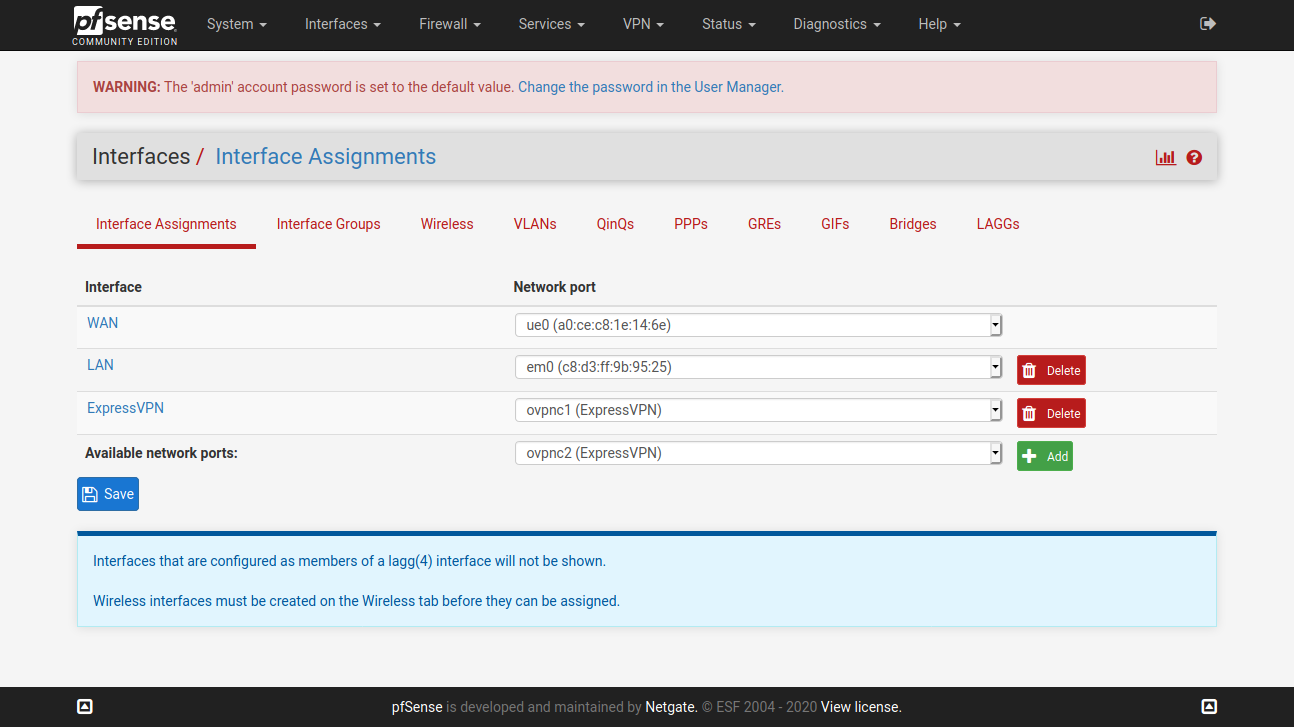
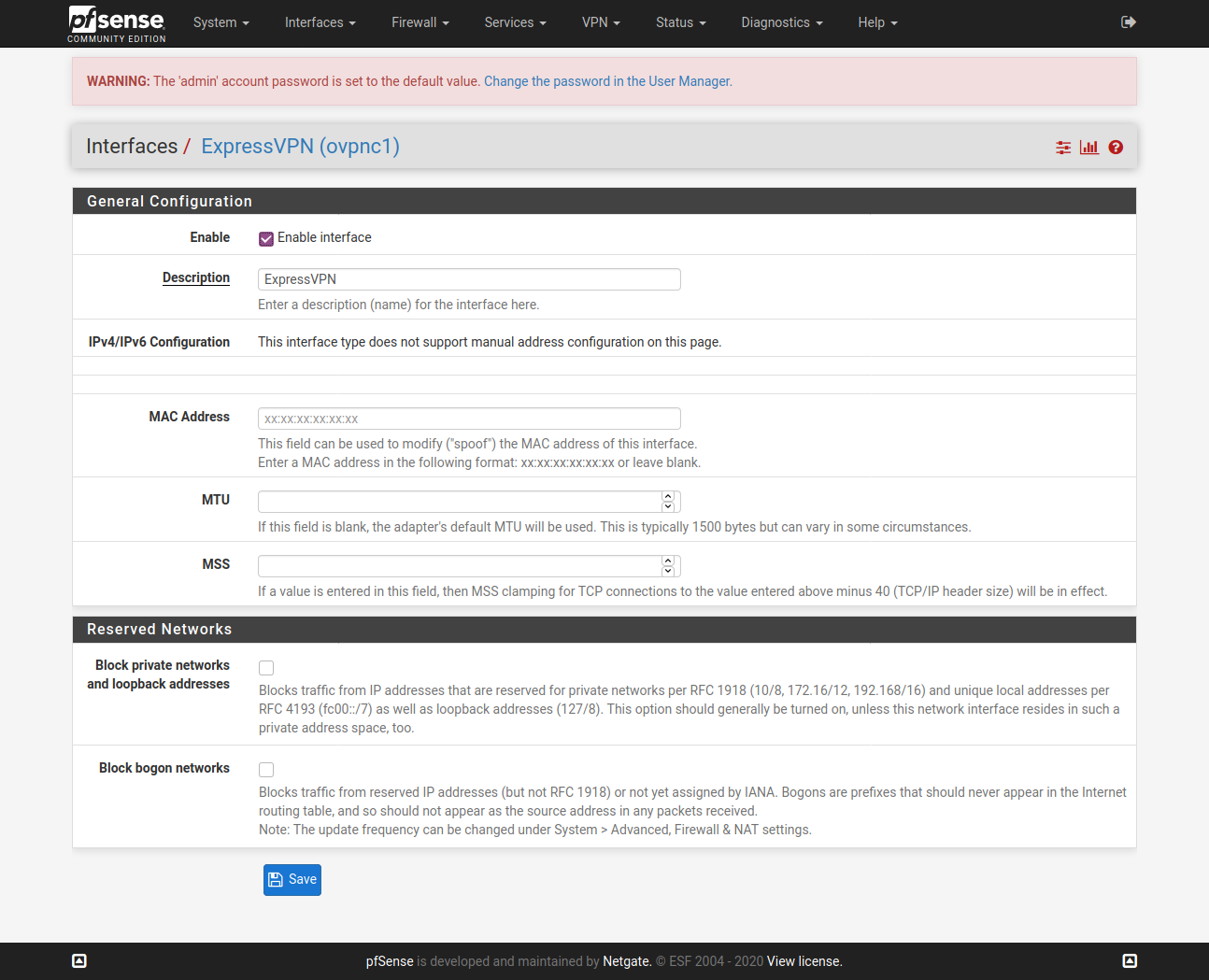
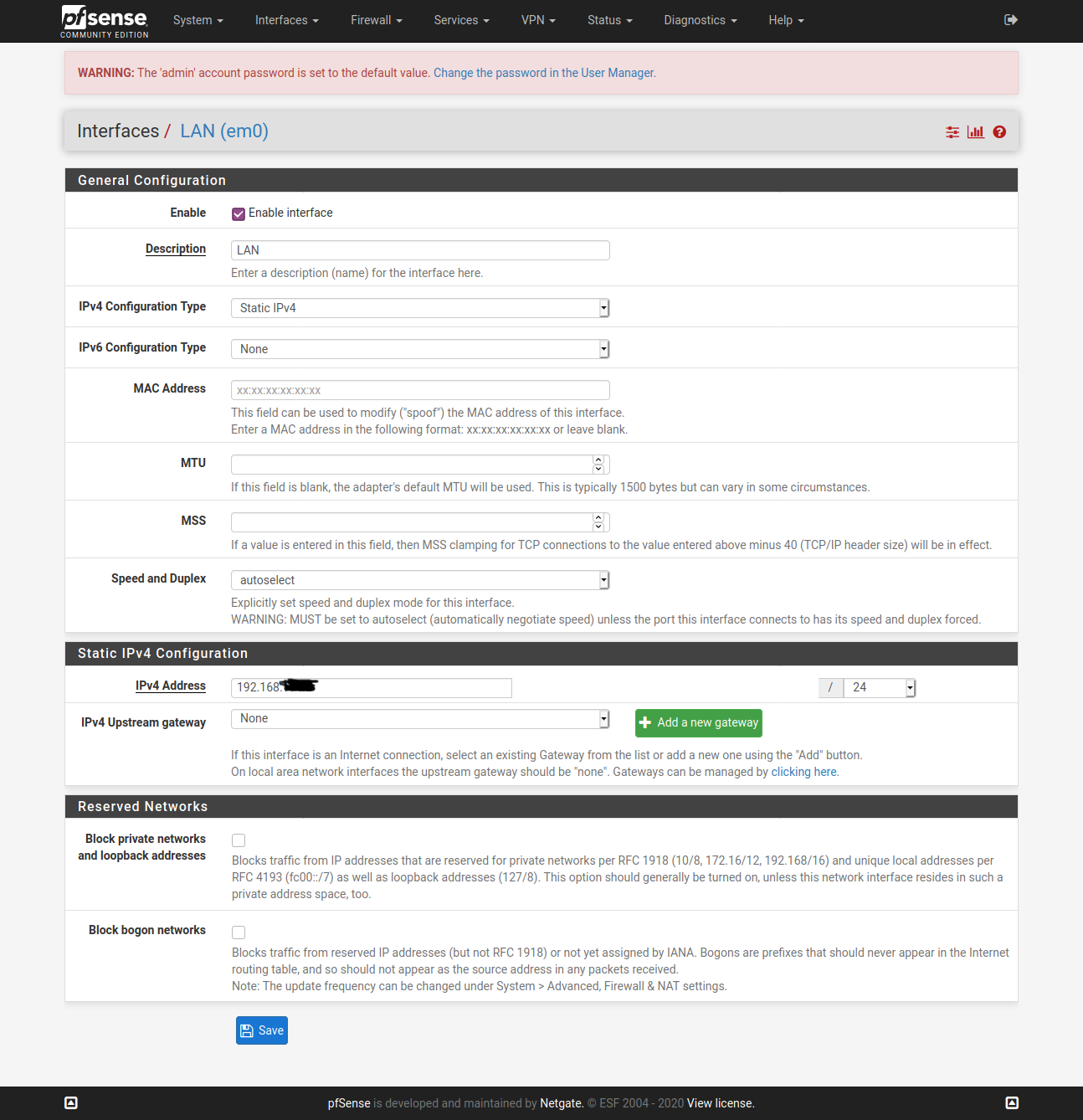
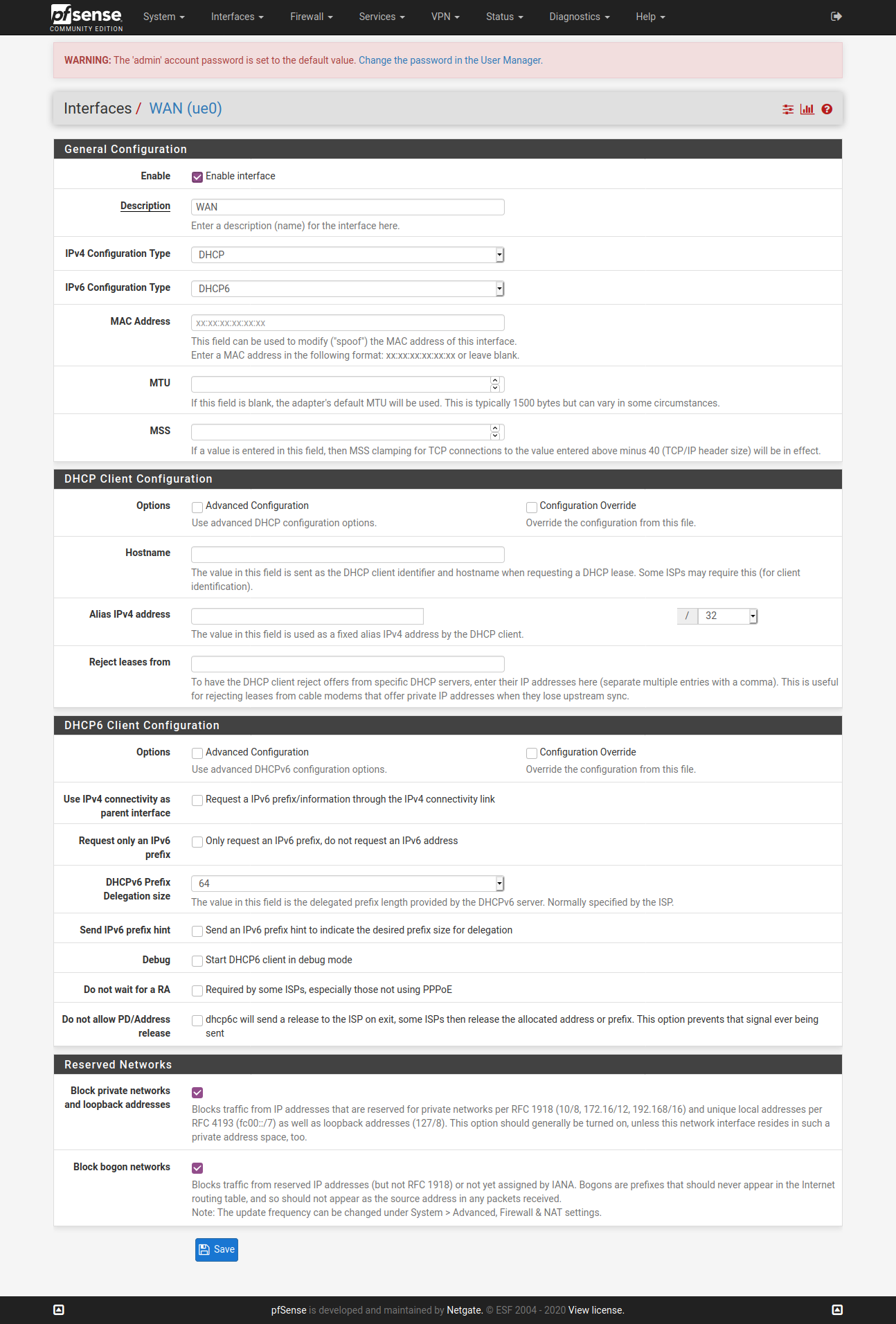
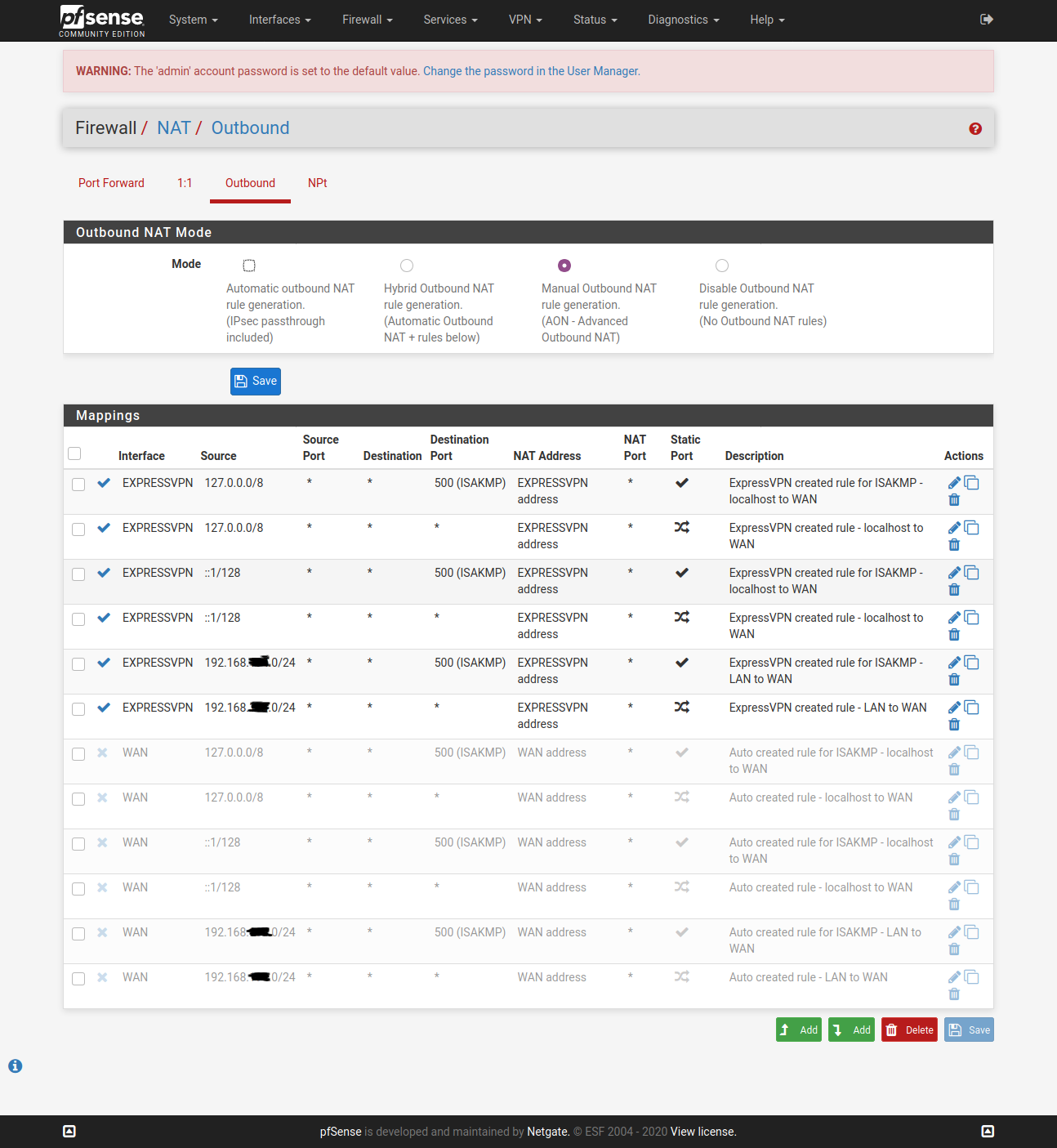
You don't need to have the X greyed WAN config.
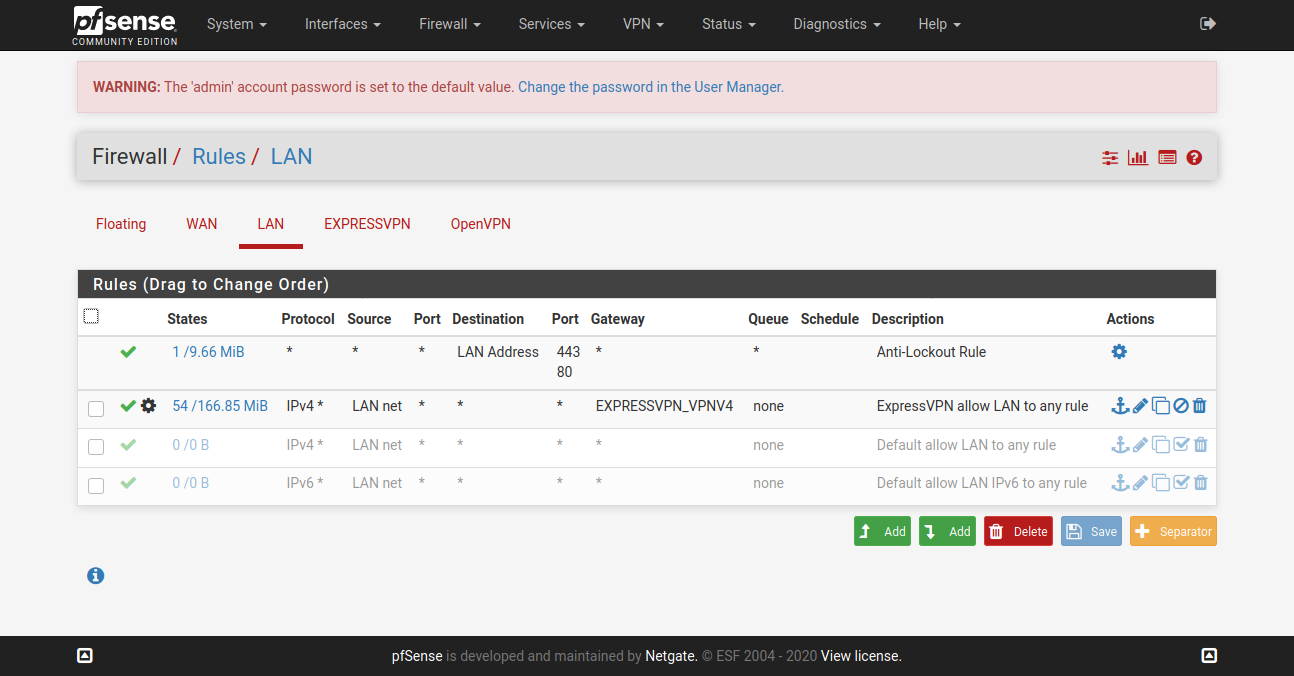
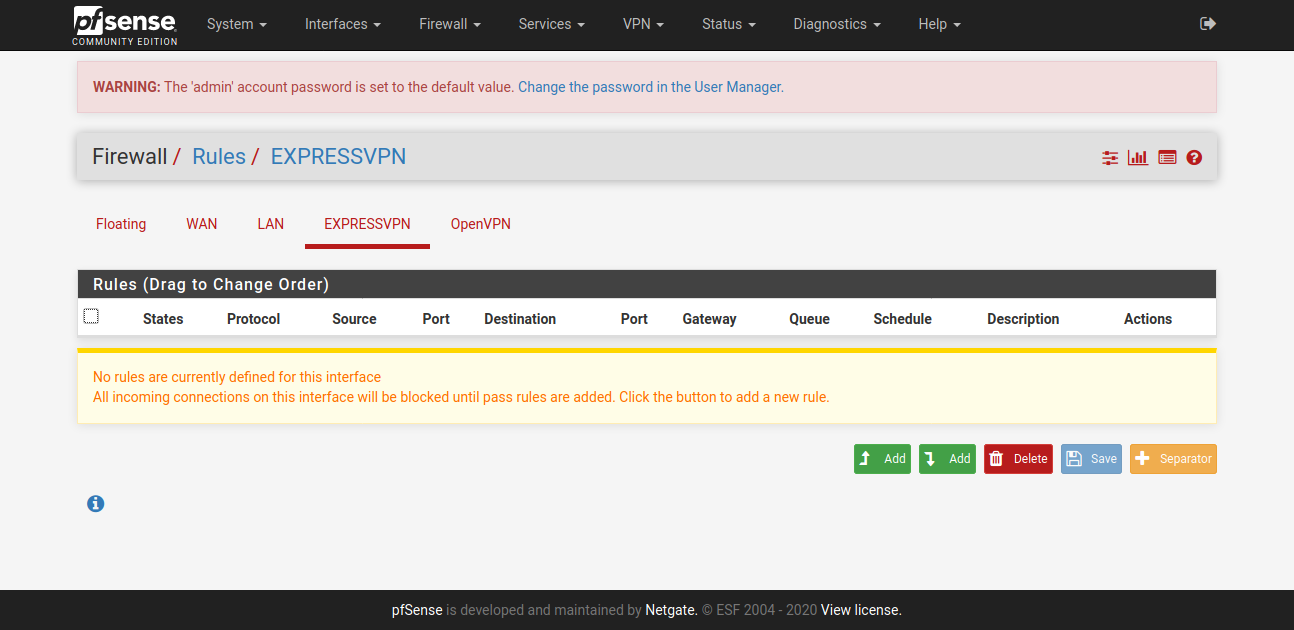
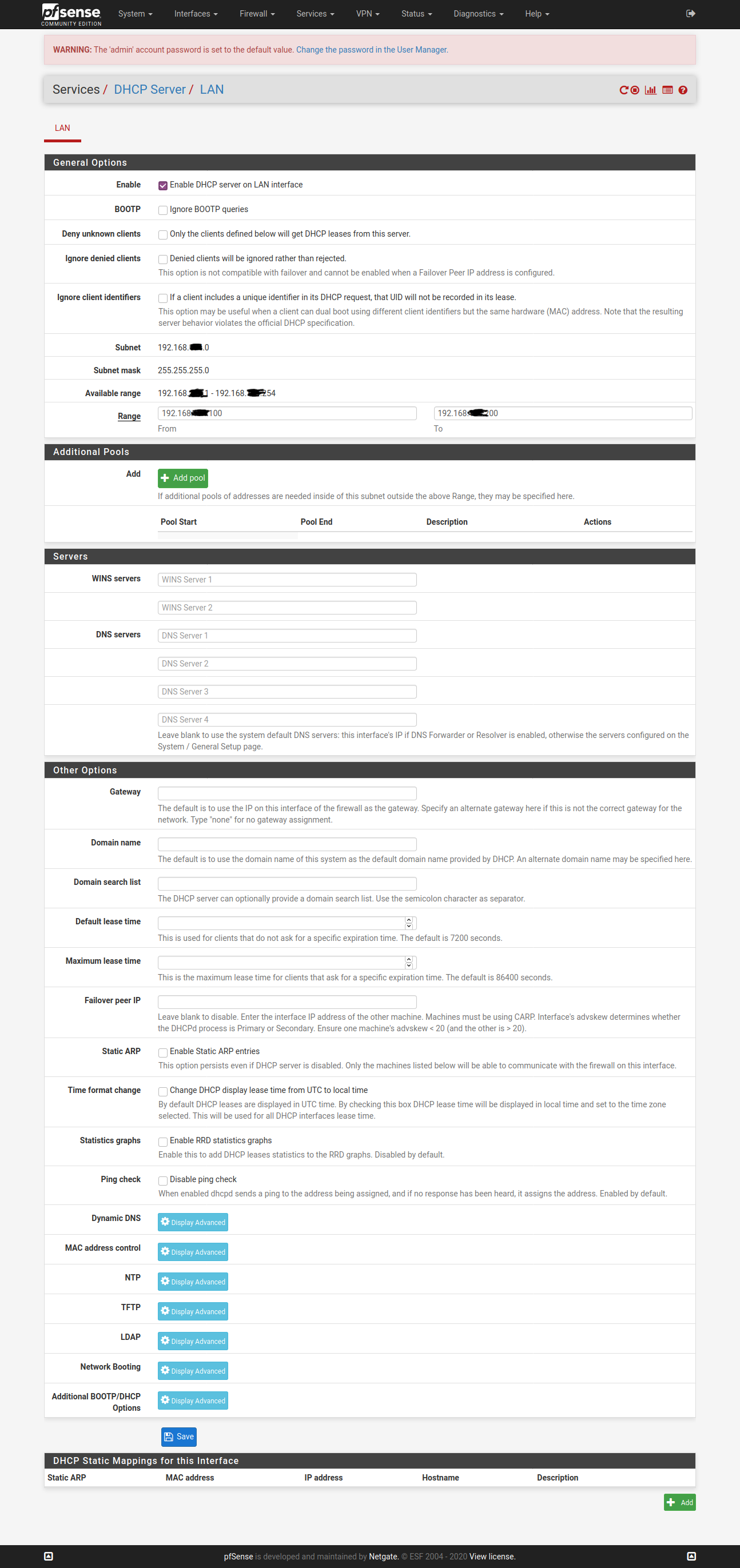
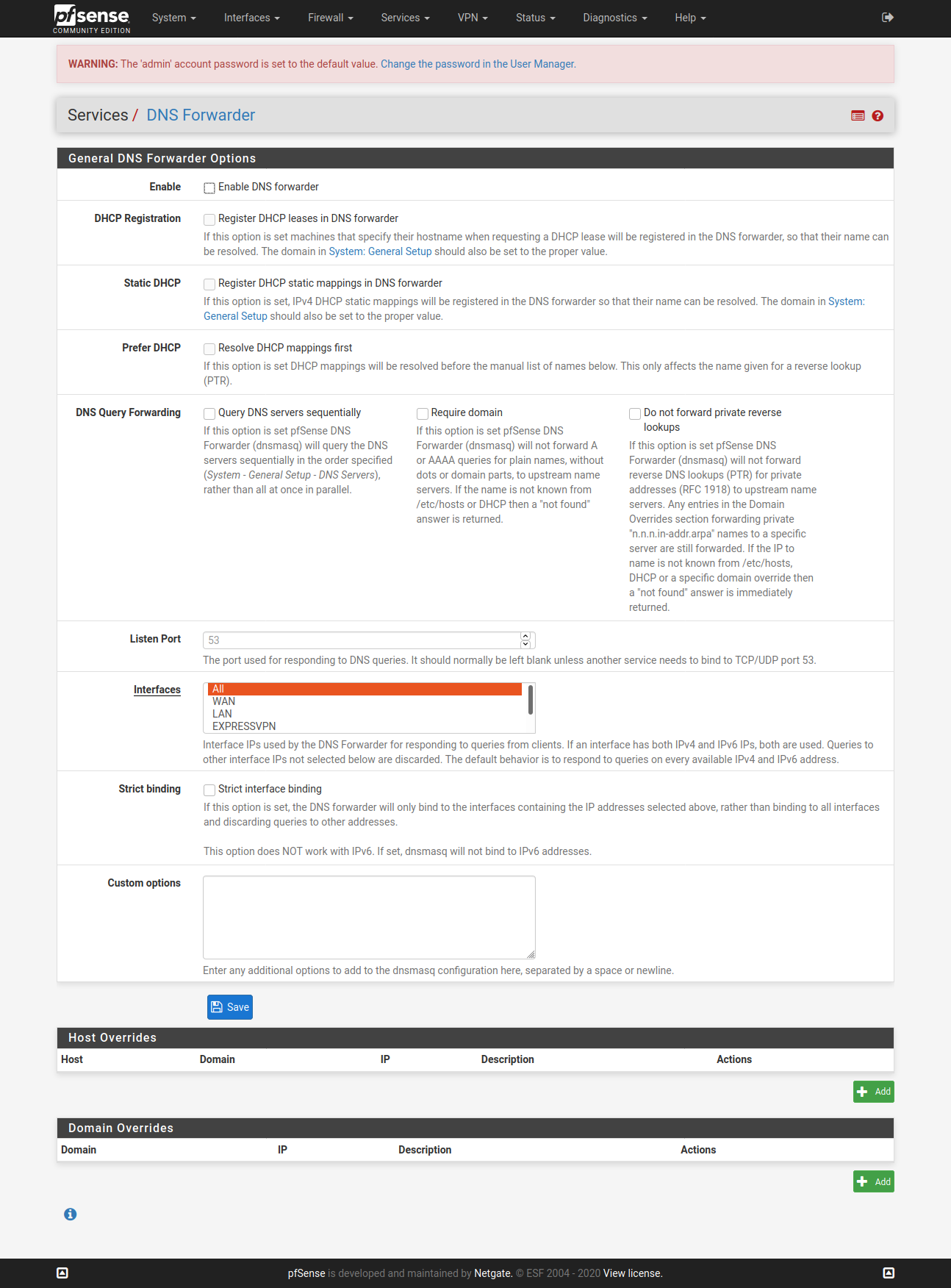
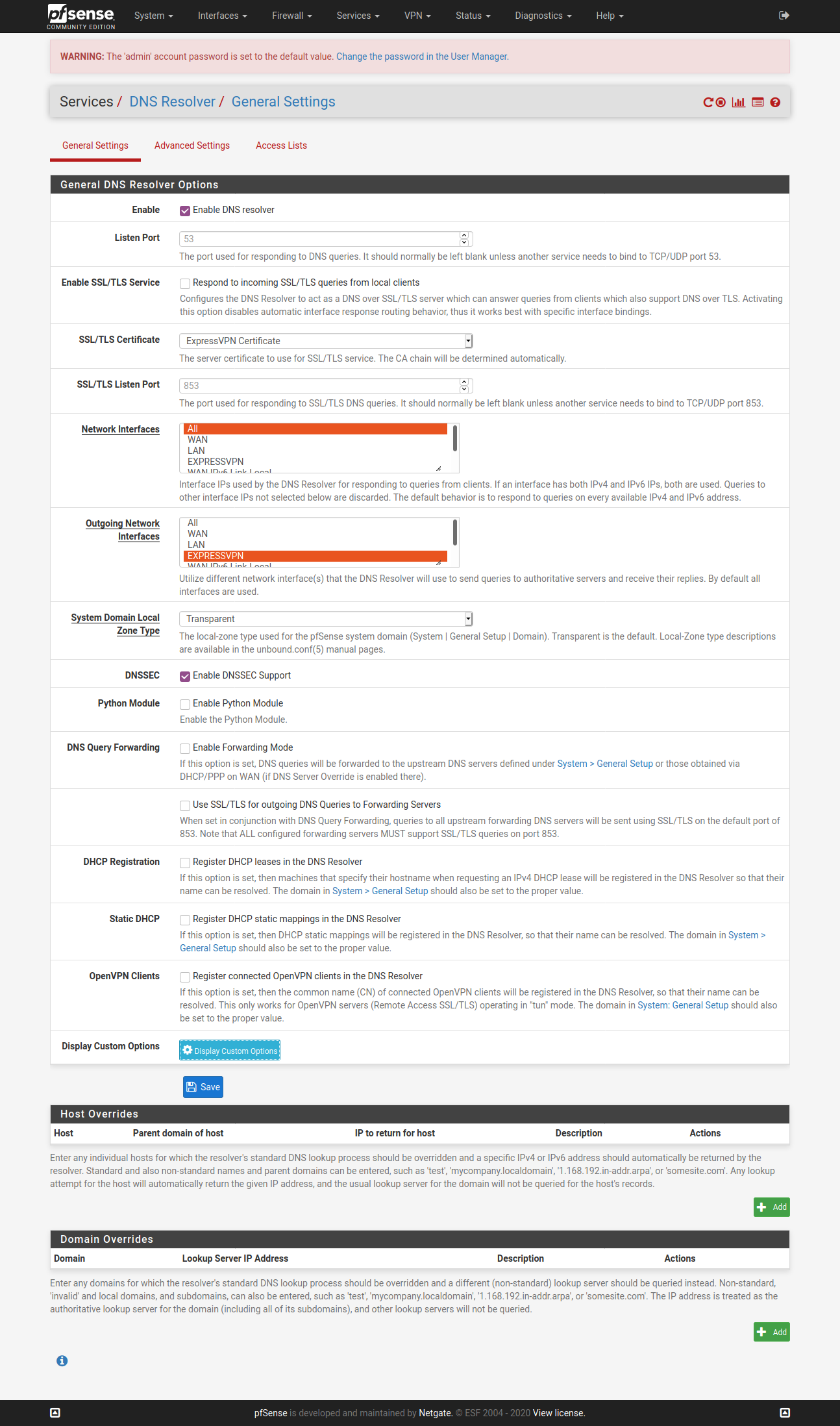
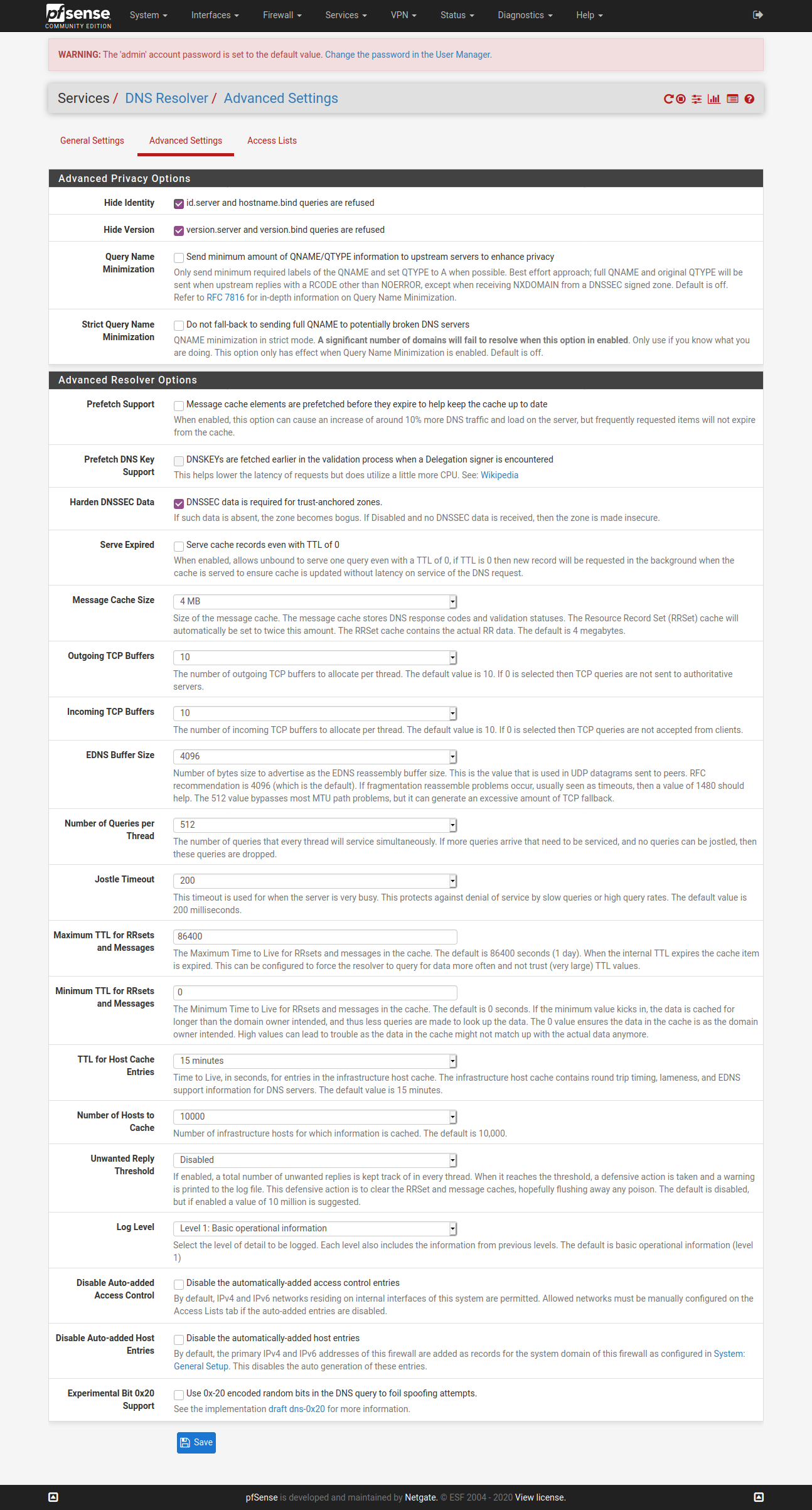
Configure only one OpenVPN Client here - ignore my greyed one in below screenshot.
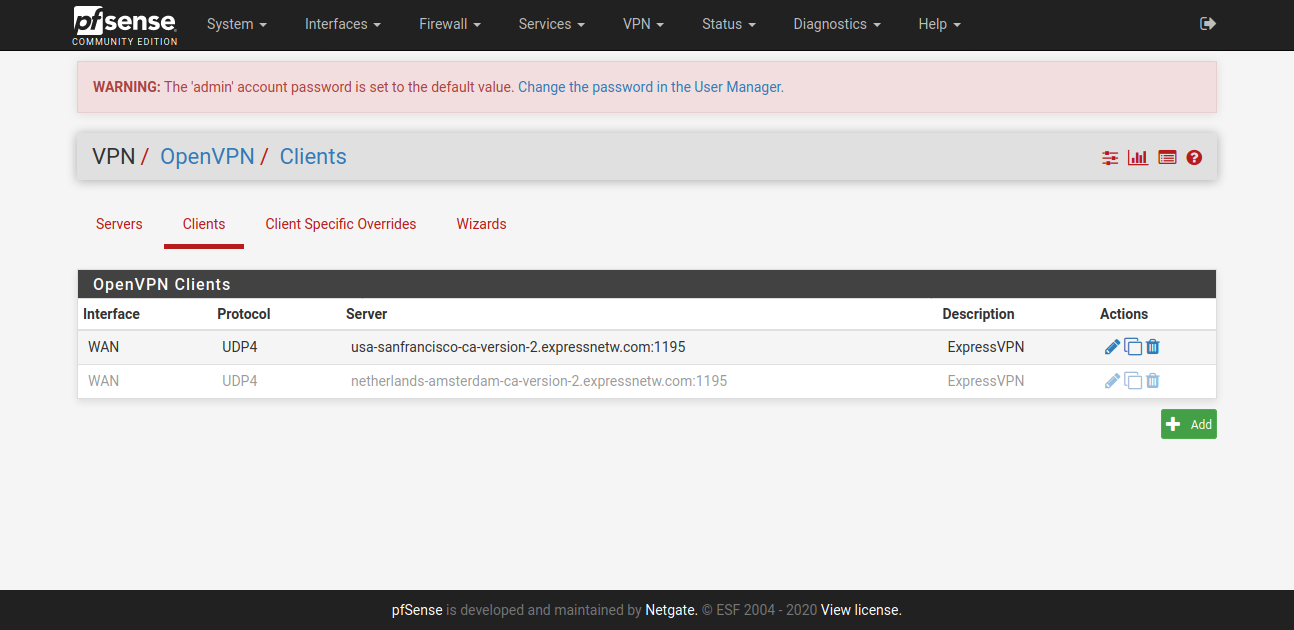
So, hopefully this is all you need to fix the configuration at your end and get ExpressVPN up & running for your purpose.
However, like I had mentioned earlier as well, use OpenWrt if you are trying to achieve ExpressVPN app kind of experience.
Cheers
-
Thanks for sharing your setting!
When I disable DNS Forwarding in the resolver (like you have) and select my VPN interfaces as outbound interface in DNS resolverI always have a DNS leak whenever I restart pfSense. dnsleaktest.com shows me DNS from my ISP. I have to restart unbound service manually after every reboot to make it use the VPN interface for resolving. This happens on every reboot / boot. And every time it can be fixed by manually restarting unbound. After that no dns leak until my pfSense restarts :(.
I have been playing with the outbound NAT rules but I can't seem to fix this. Does this sound familiar for anyone?
--edit typos
-
@vjizzle following this thread because of the same problems with expressvpn.
Even if it's not a technical fix you could use a ups so the pfsense box wont't go down
-
@vjizzle said in ExpressVPN - Geo-restricted website works when connected through their app over OpenVPN UDP but not through pfSense OpenVPN:
Thanks for sharing your setting!
When I disable DNS Forwarding in the resolver (like you have) and select my VPN interfaces as outbound interface in DNS resolverI always have a DNS leak whenever I restart pfSense. dnsleaktest.com shows me DNS from my ISP. I have to restart unbound service manually after every reboot to make it use the VPN interface for resolving. This happens on every reboot / boot. And every time it can be fixed by manually restarting unbound. After that no dns leak until my pfSense restarts :(.
I have been playing with the outbound NAT rules but I can't seem to fix this. Does this sound familiar for anyone?
--edit typos
This is why I have setup DNS servers in the General Setup tab in pfsense and then assigned the VPN interface as the gateway. Then I have Forwarding enabled in DNS Resolver with SSL/TLS. In this way on every (re)boot of pfSense I can make sure that there is not DNS leak with the DNS ip of my internet provider. Off course dnsleaktest.com us showing multiple cloudflare and quad9 dns servers, but I can live with that.
BTW I am running 3 VPN client connections to ExpressVPN and using a Routing group I am able to have a "fail-over" situation because I sometimes find that my ExpressVPN client disconnects. Those VPN interfaces are the only ones selected in DNS Resolver as outgoing interface. This setup has been tested with only 1 VPN client and shows the same behaviour.
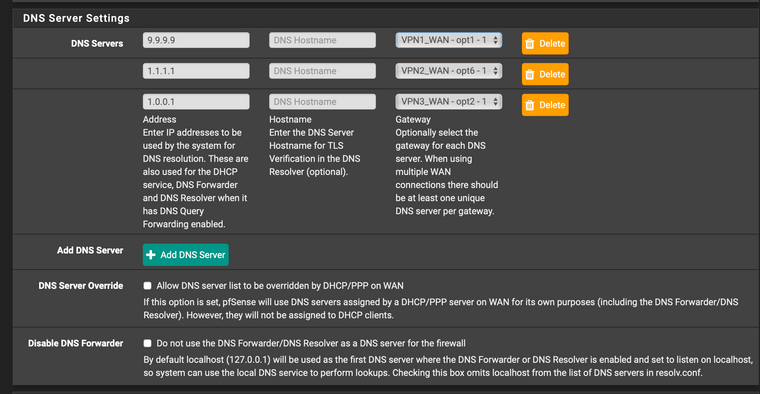
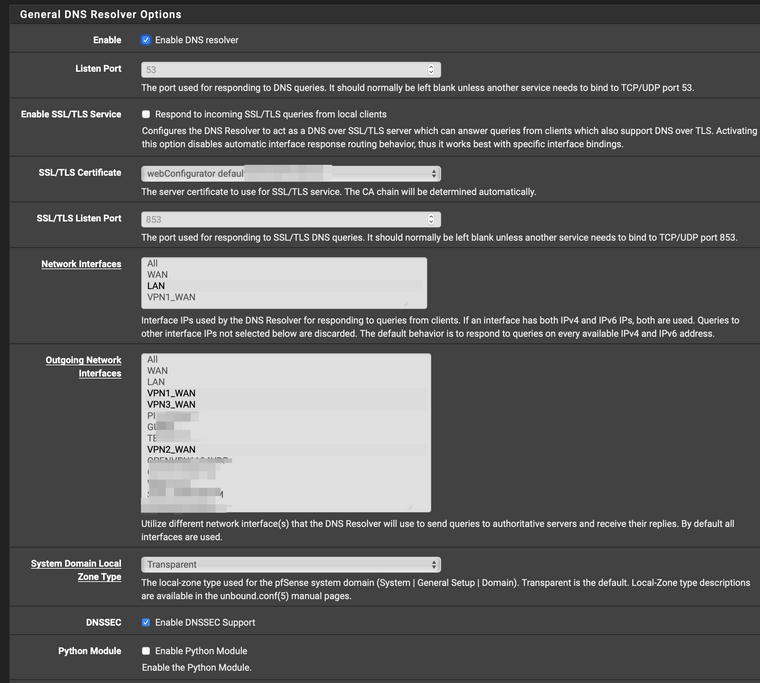
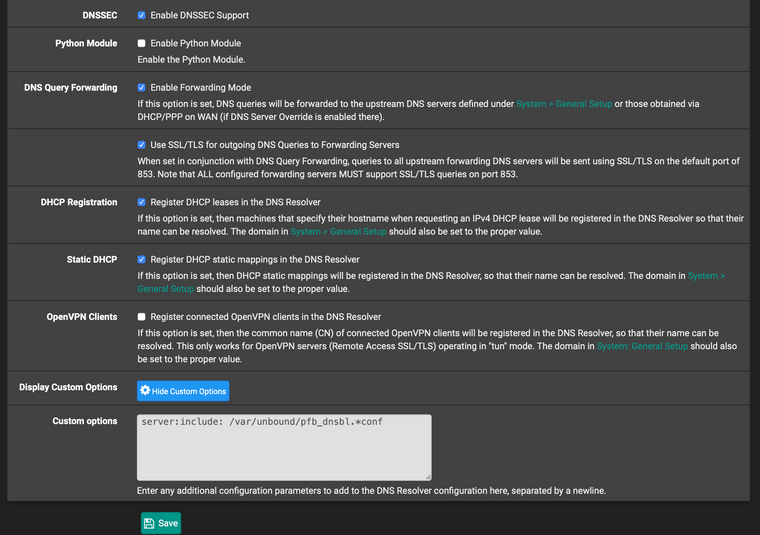
So with this configuration and by trying different ExpressVPN servers I found some of them working fine with Netflix. But I suppose just a matter of time that those servers are also backlisted :P.
The permanent solution here seems to be OpenWRT. For me that is a no go because pfSense is so much more user friendly. Plus I am using Suricata to protect internet exposed servers and with OpenWRT that is a p.i.t.a. to configure.
-
This post is deleted! -
First of all, I'm not a native English speaker so I apologize if I commit any mistake.
I was facing this issue recently with pfSense. In fact, I installed the new pfSense version and this was even worse because the ExpressVPN establishes well but no routing. Similar to what this post is about.
So I saw you guys mentioned that OpenWRT is the solution in this post. Nothing farther away from reality.
OpenWRT for x86_64 machines (which is my case) is a bad choice.
My deployment is:
ISP ——> vlan_10 ——> Vlan Capable 8 port Switch —> Old Laptop with one NIC running pfSense ——> Physical NIC for LAN ———> Same Switch I mentioned before ——> My Lan
OpenWRT didn't manage this deployment well. Constantly network issues, reinstalling image one and one more times, ethernet interfaces frozen so the local network couldn't reach appliance. The Installation is not user-friendly.
After 5 hours of fighting with OpenWRT, I was about to rollback to pfSense when I found which was, in my case the solution to Geo-Restriction. OpnSense
Yes. OpnSense is like the big brother of pfSense. Similar installation but with a better GUI. I followed the same wiki from ExpressVPN, no issue at all, everything connected at the first attempt.
The changes were with outbound NAT. If you choose Manual NAT, It deletes all rules created automatically so you have to create your own in my case the rules are:
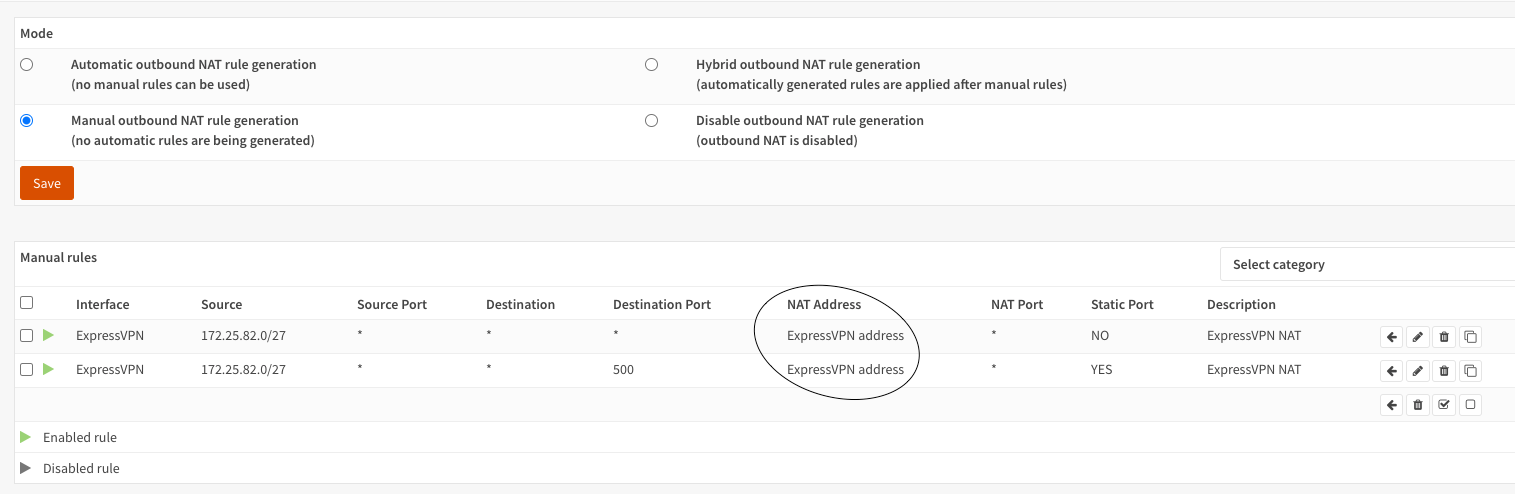
I think the trick is in the part I circled. In pfSense, if I am not mistaken, the Target Address is the WAN and not the ExpressVPN (I am not sure) Besides that the wiki suggests to clone the rules created by pfSense and change the interface to those. Here I just remove the automatic rules and create mine
The firewall rules are:
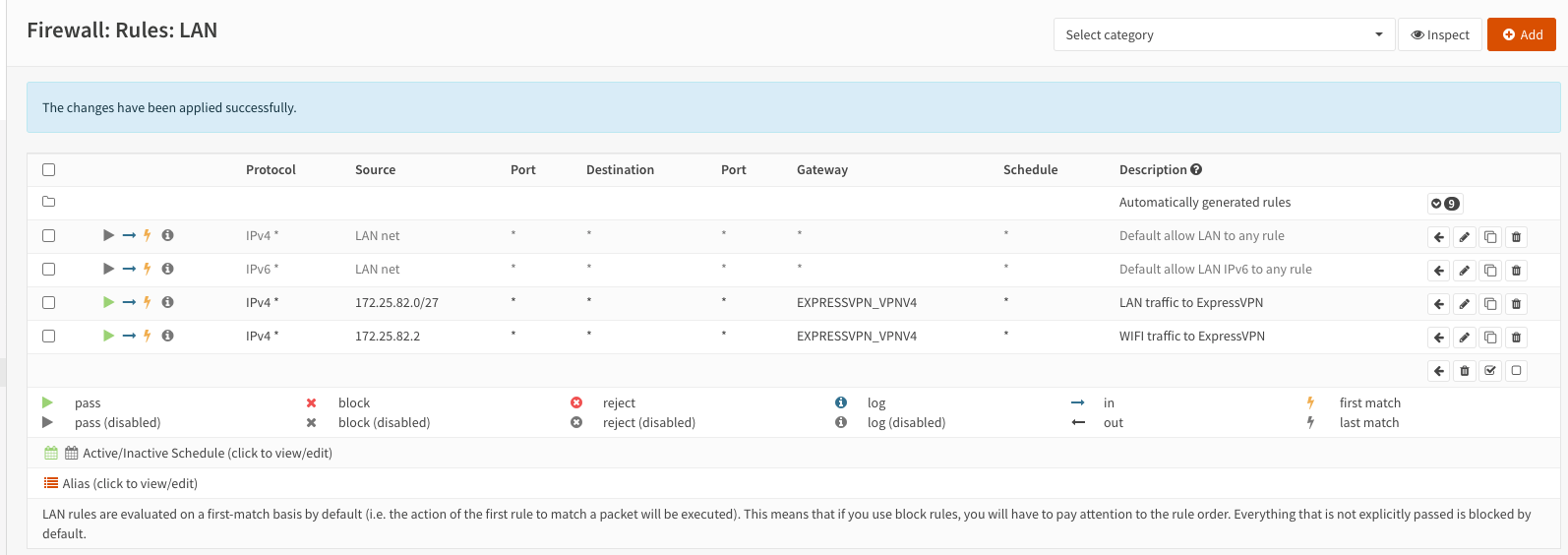
And finally, I enabled Unbound DNS and checked the box for DNS Query Forwarding.
Not Geo-restricted at least in Netflix, not Disney Plus. Not sure about other streaming services because I don’t use them. Worth trying.
-
@jairoav25
Hi,Thanks for sharing this. Can you tell me what dns servers you have unbound forwarding to? I will post my config later on. Thank you.
-
@jairoav25 said in ExpressVPN - Geo-restricted website works when connected through their app over OpenVPN UDP but not through pfSense OpenVPN:
OpnSense is like the big brother of pfSense
Um....... dispute!
-
Update for everyone:
Avoid using Google Chrome to test DNS leaks or Streaming services.
After messing with several configurations in the DNS part I ended up with this ones:
I tested ExpressVPN Dns gotten from using the app from the Phone and doing a DNS leak test but at the end, I set Cloudflare DNS
Under System — Settings — General:
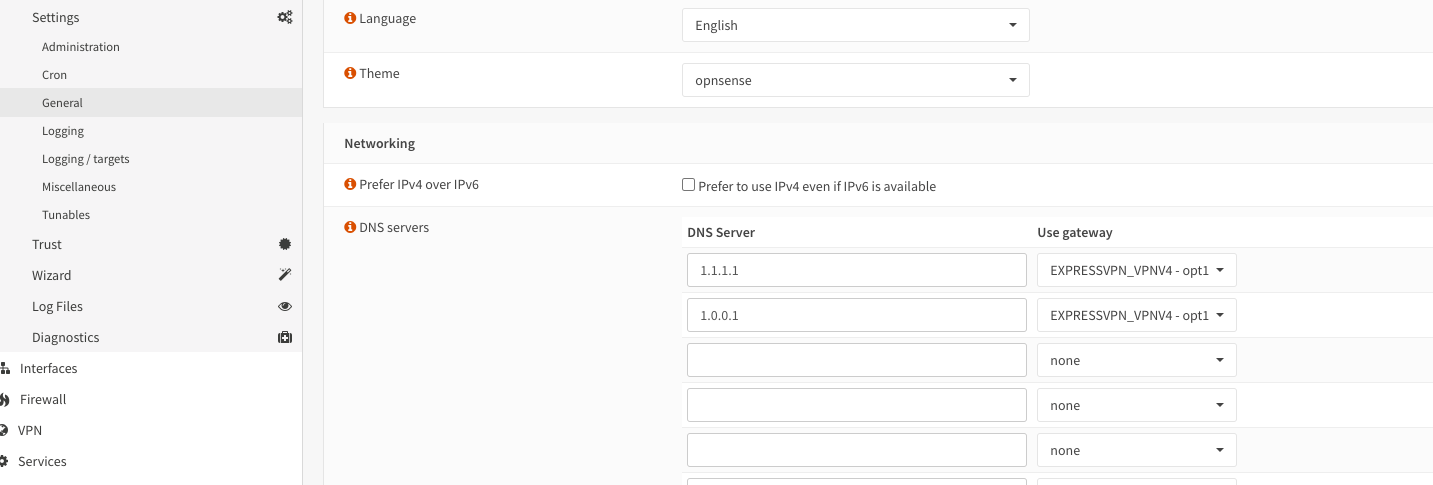
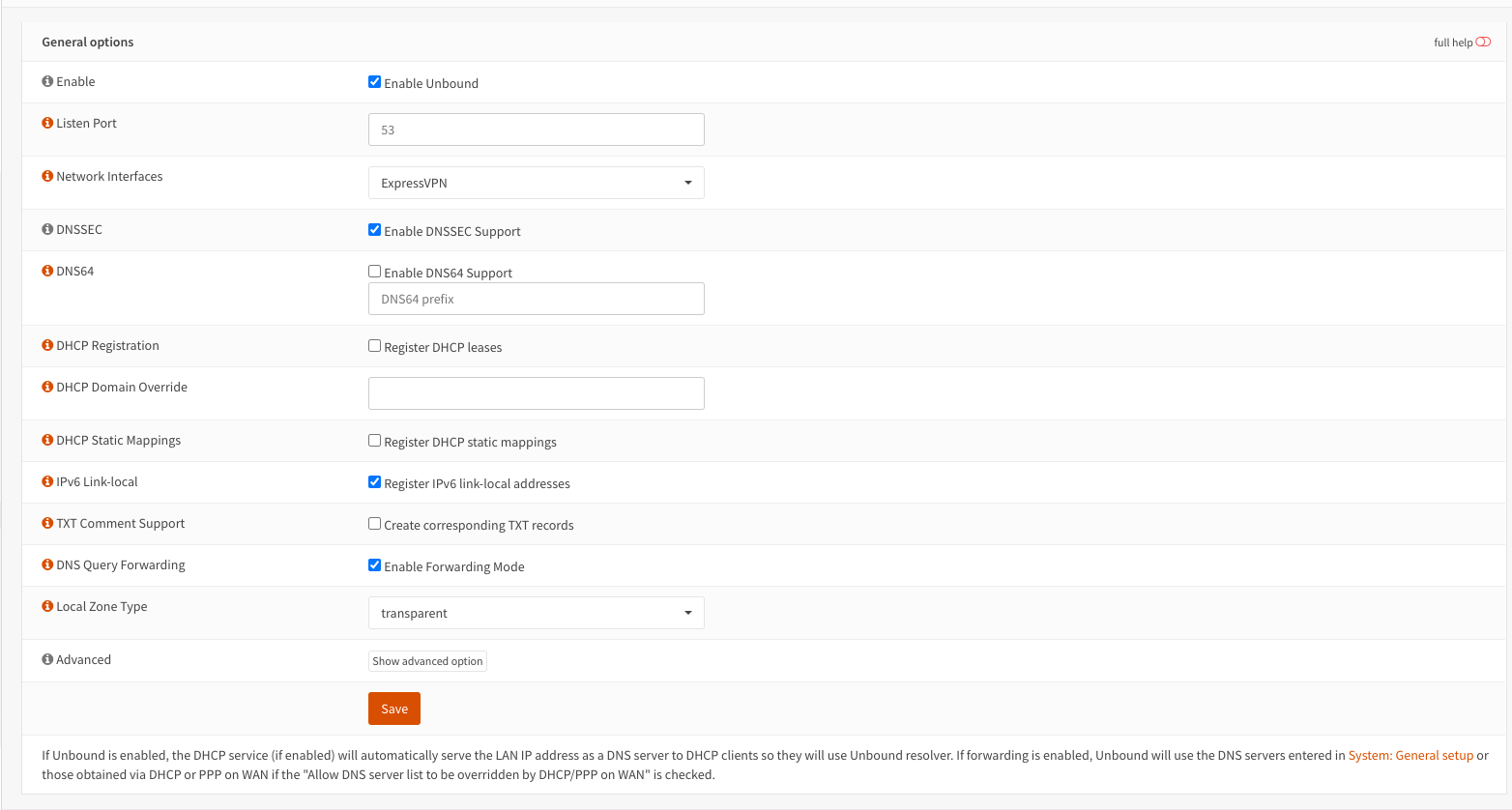
I activate DNSSEC, Forwarding, and Unbound as shown below,
Under Services — Unbound DNS — General:
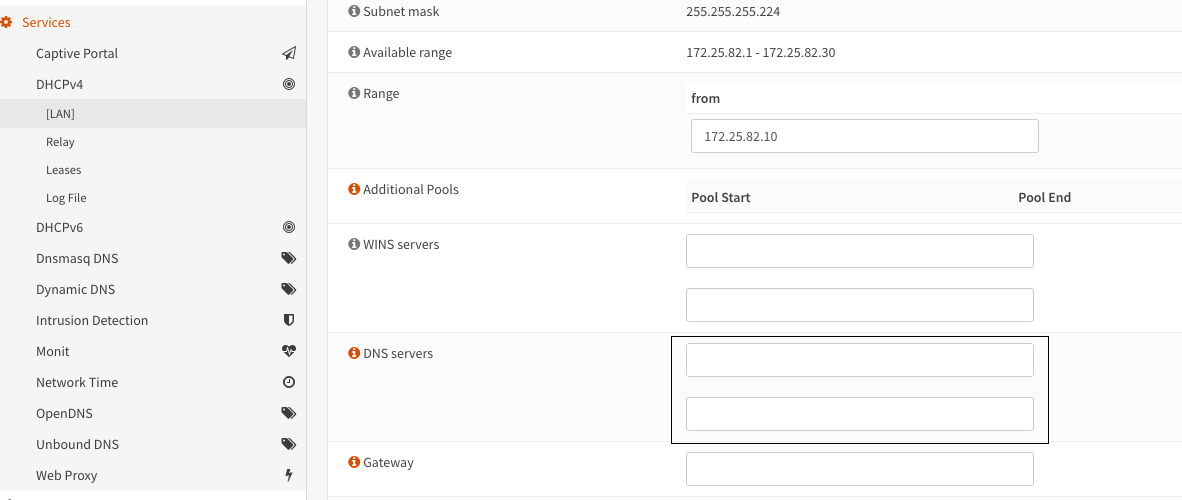
Under Services — DHCPv4 — LAN I left DNS servers blank
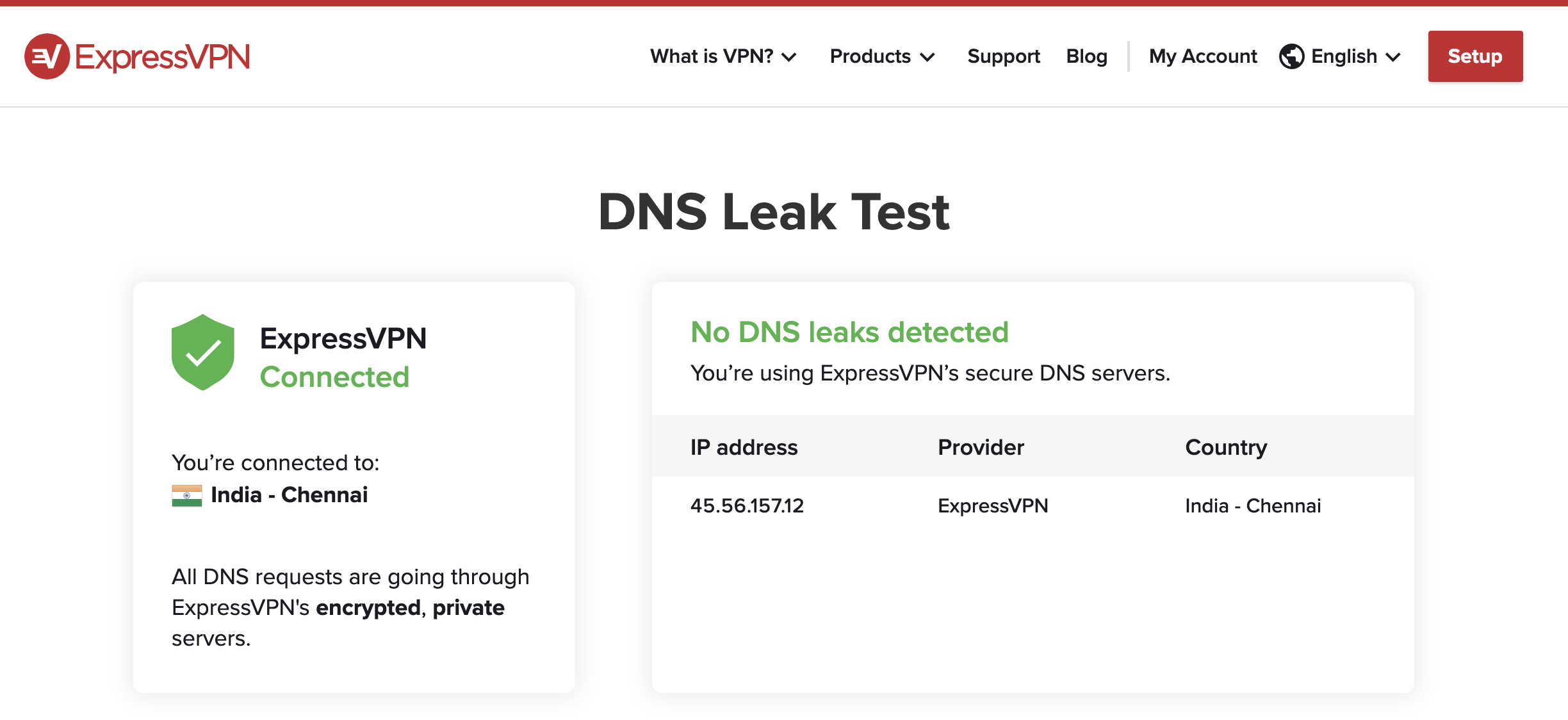
Finally, a Result that Disney, Amazon Prime, and Netflix and a DNS LEAK Test in ExpressVPN are working with Firefox:
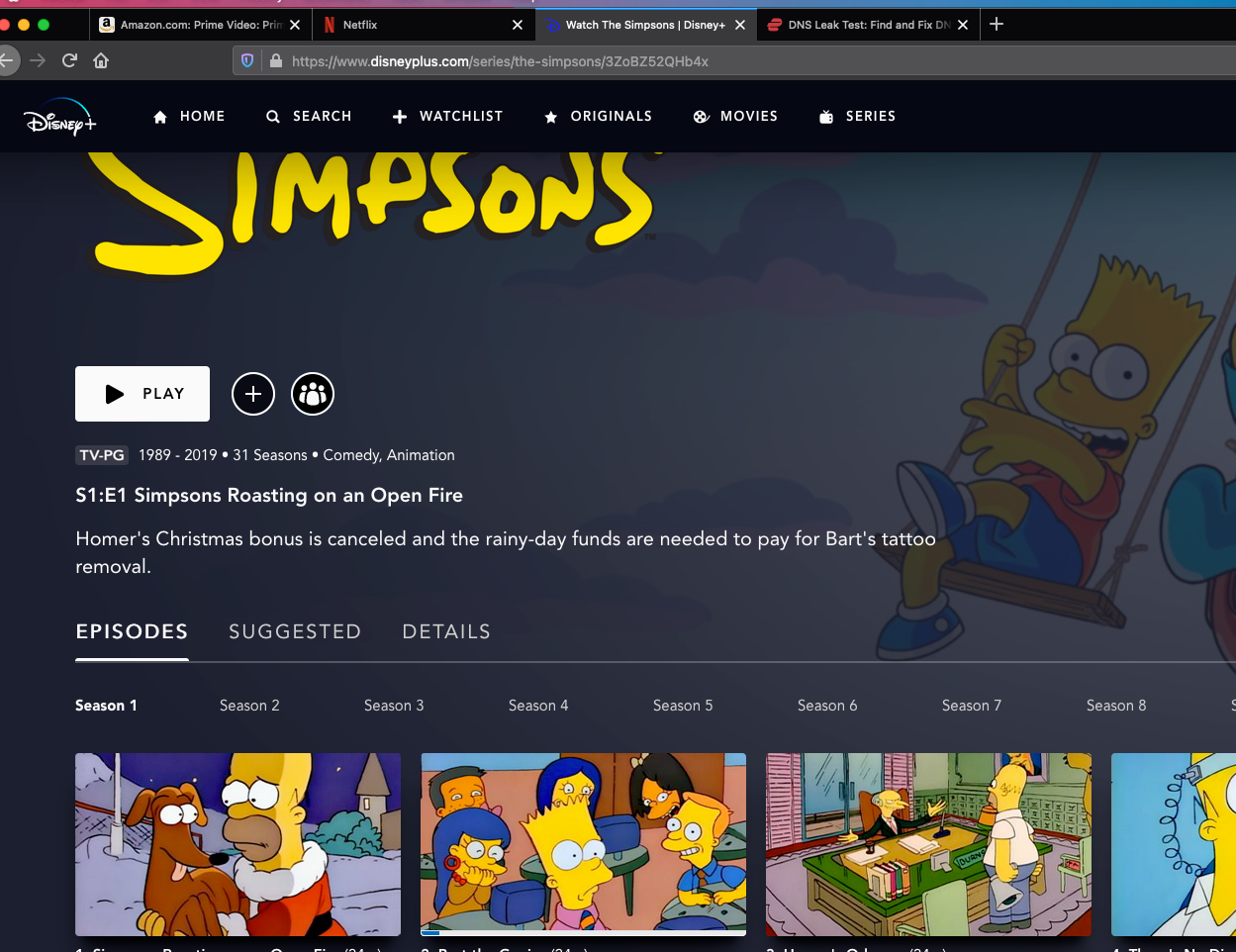
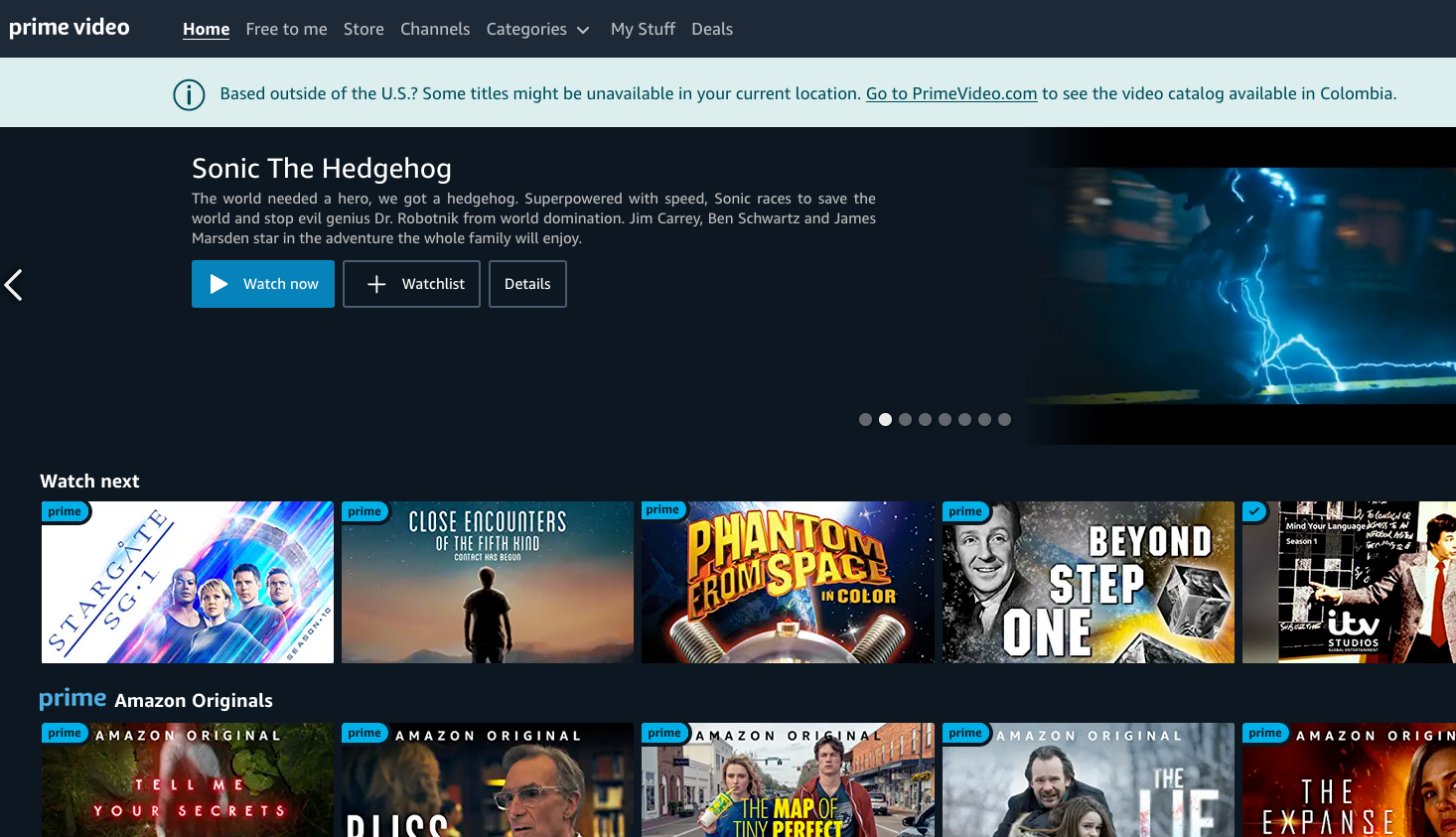
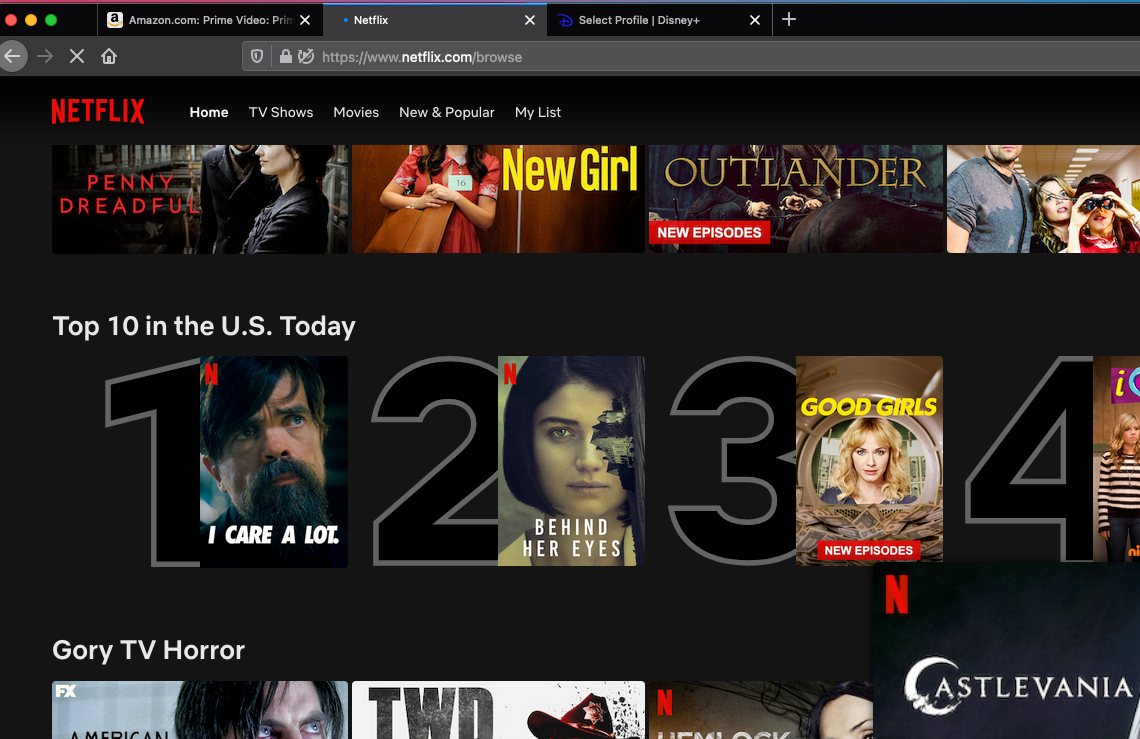
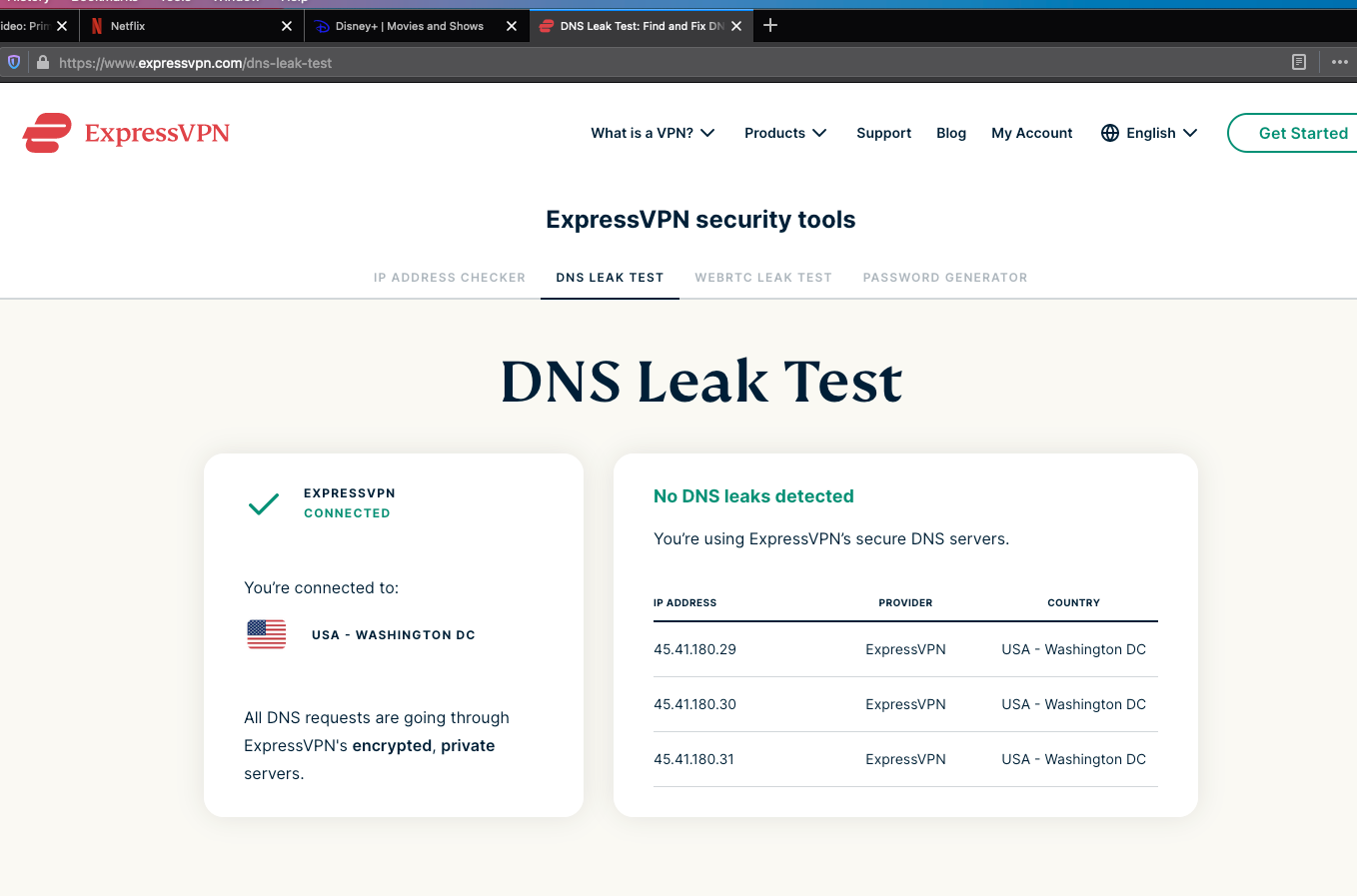
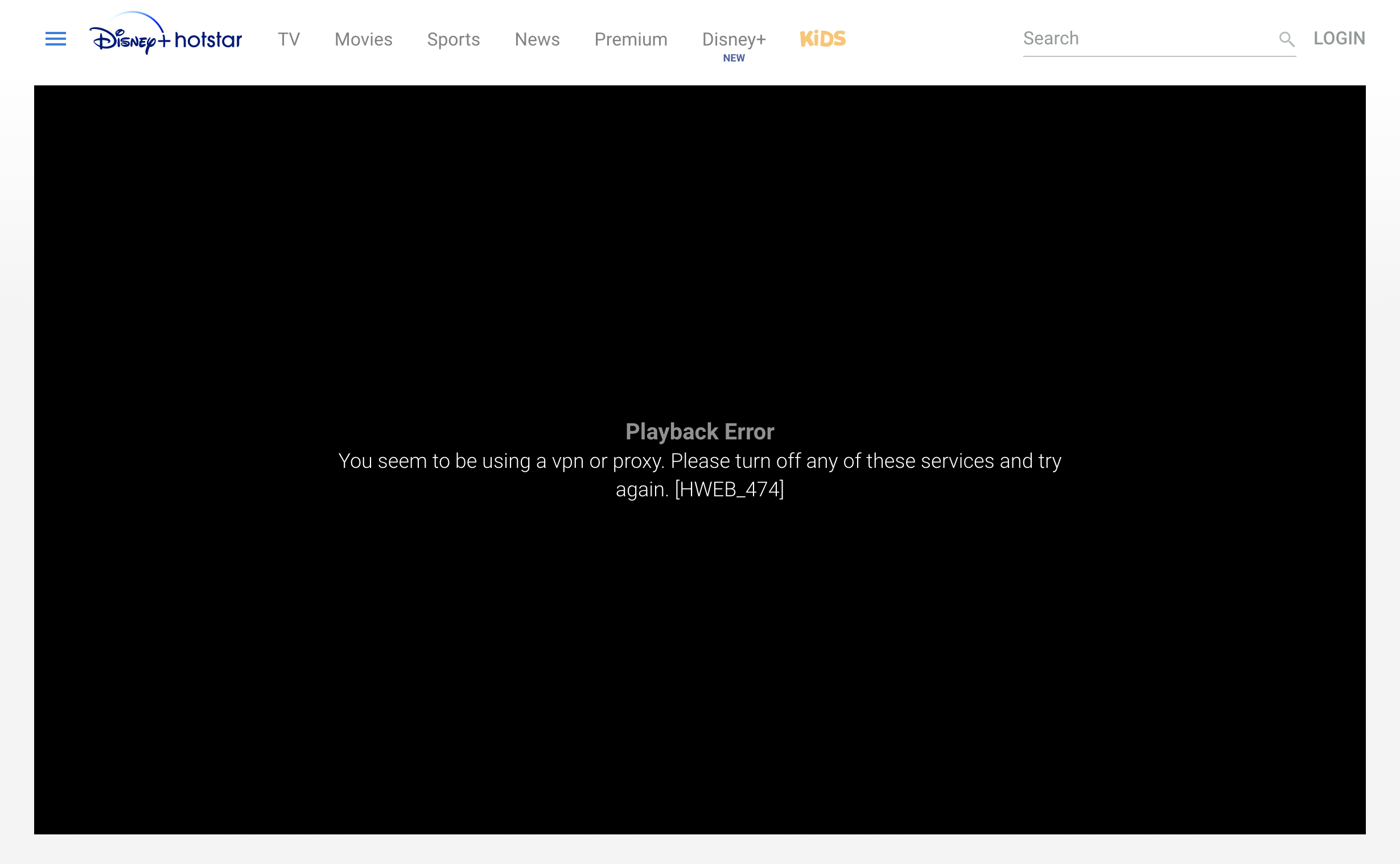
On Google Chrome, It is still showing DNS leak and Disney Plus doesn't load and Amazon Prime Video is showing VPN is being used. Weird:
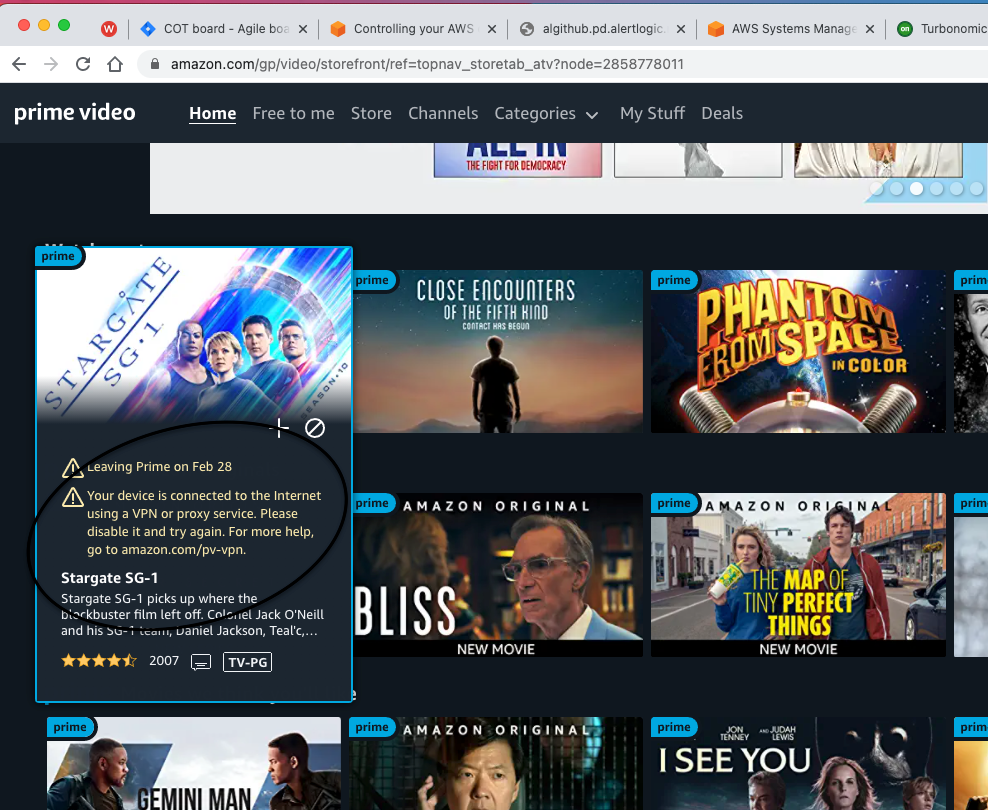
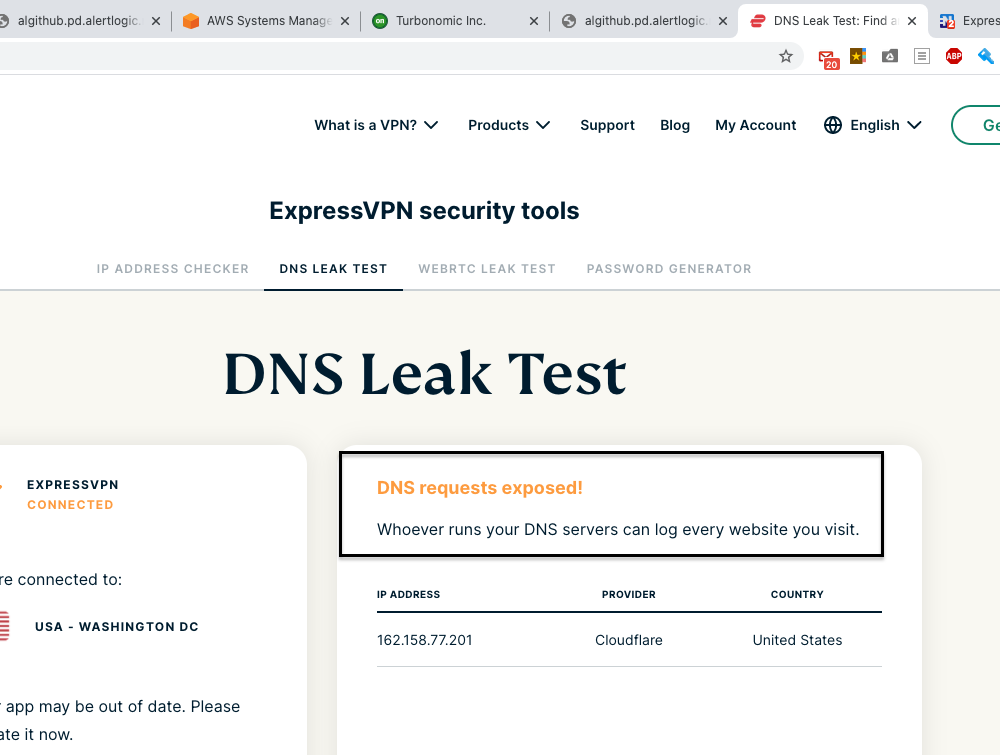
Let me know your thoughts on this.
EDIT:
If you want to test DNS leak from CLI:
https://github.com/macvk/dnsleaktest
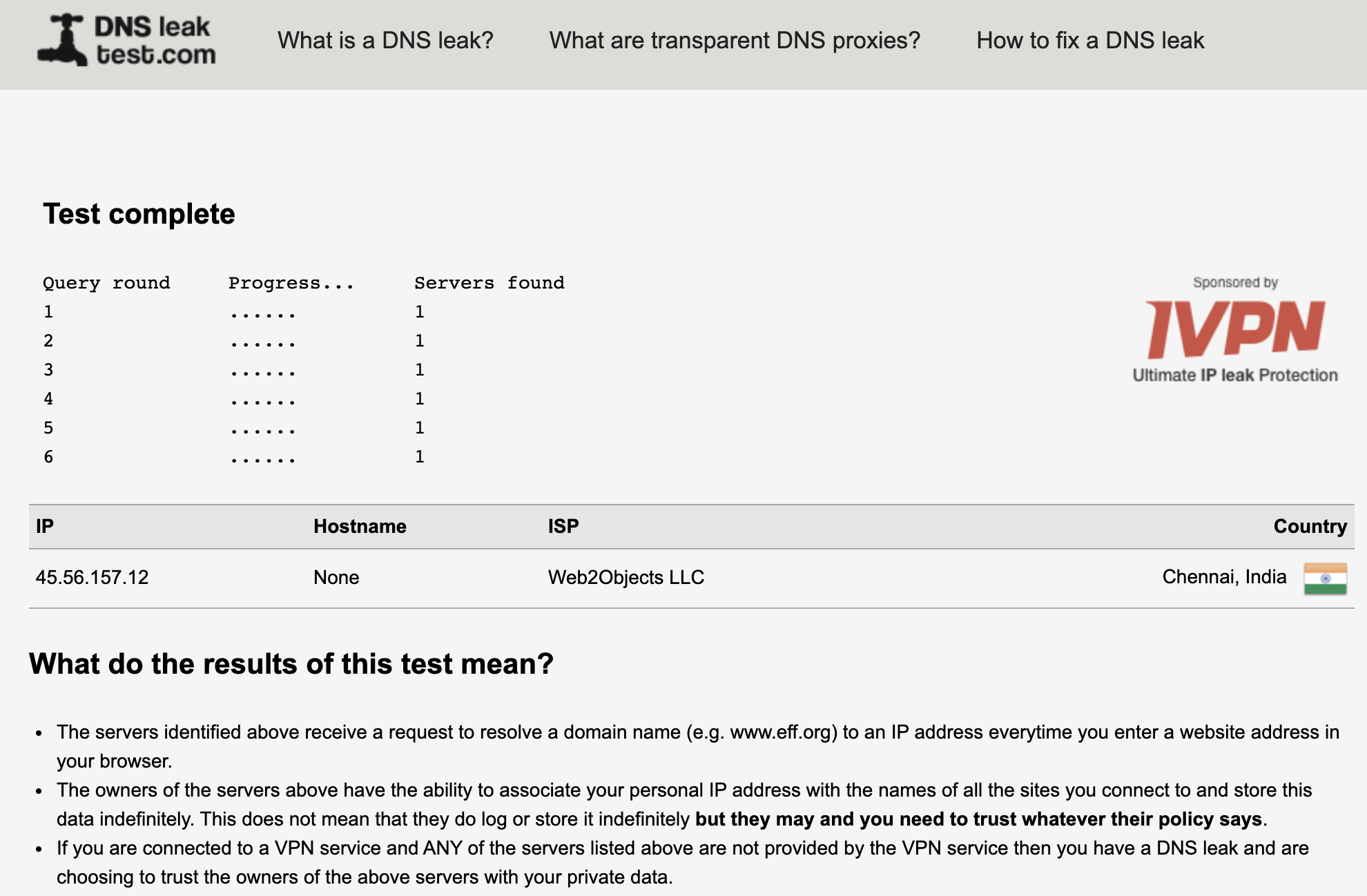
My results:
❯ ./dnsleaktest.sh Your IP: 45.41.180.30 [United States of America AS30633 Leaseweb-USA-WDC] You use 3 DNS servers: 45.41.180.29 [United States of America AS30633 Leaseweb-USA-WDC] 45.41.180.30 [United States of America AS30633 Leaseweb-USA-WDC] 45.41.180.31 [United States of America AS30633 Leaseweb-USA-WDC] Conclusion: DNS is not leaking. -
Hi JairoAV25,
Thank you for doing extensive research on this! I just tried to replicate your settings in pfSense and it did not work for Netflix. I believe the reason why it will not work is that the ExpressVPN app forces your iPhone, iPad or laptop (Mac and Windows) to use the DNS server assigned by ExpressVPN. On my pfSense I use pfBlockerNG and if I leave the DNS field on the DHCPv4 server empty, pfSense will forward all the DNS requests for my LAN clients trough the ExpressVPN tunnel (which will be redirected to ExpressVPN DNS server) bypassing my pfBlockerNG. BUT I think that is what will make ExpressVPN on pfSense work just like the app on a device :).
I do need pfBlockerNG function so bypassing local DNS on pfSense is not an option. From experience I know that there are other VPN providers which claim (and in fact do!) work with pfSense and Netflix. But all of them specify their own DNS server which you have to enter in pfSense. If only we could get this from ExpressVPN :(
-
@vjizzle
I C.Have you tried to contact ExpressVPN to get the DNS from them? When I was troubleshooting and digging into many posts, I read some people saying that ExpressVPN gave them DNS to set.
Not sure if was this before and now they are suggesting Google or CLoudfare DNS. It worth a try.
-
@jairoav25
Yes in the past I tried to get DNS from them. Their advice was also to use Google or Cloudflare because officially they don't support pfSense. In since have moved away from ExpressVPN. There are beter options out there. Thank you for trying and sharing your experience!