pfSense Community Edition (CE) 2.5.0 and pfSense Plus 21.02 now available!
-
@mkryger said in pfSense Community Edition (CE) 2.5.0 and pfSense Plus 21.02 now available!:
disappeared from my SG-3100.
Can you possibly provide a linkhttps://forum.netgate.com/topic/160959/21-02-sudden-lockup/
-
@mkryger said in pfSense Community Edition (CE) 2.5.0 and pfSense Plus 21.02 now available!:
@bmeeks
Thank you for the info, as i was also a bit confused why it disappeared from my SG-3100.
Can you possibly provide a link for the source of this information, so we will be able to follow the progress and get to know about what the bug was about?
I find it weird the team didn't inform about this in the original post or made it clear elsewhere in this thread.@teamits beat me to it, but here is a copy of his link as a clickable one: https://forum.netgate.com/topic/160959/21-02-sudden-lockup/.
-
@teamits
https://twitter.com/NetgateUSA/status/1362791245546946561
-
@weldong - I wish that I had been as smart as you and not "upgraded" as soon as I saw the alert. My system is a SG-4860 and after a couple of days working on it I think I've got it working reliably again.
The main problem that I see with the update process is that you are just told that an update is read to be installed but without any information of details. -
@mkryger said in pfSense Community Edition (CE) 2.5.0 and pfSense Plus 21.02 now available!:
@bmeeks
Thank you for the info, as i was also a bit confused why it disappeared from my SG-3100.
Can you possibly provide a link for the source of this information, so we will be able to follow the progress and get to know about what the bug was about?
I find it weird the team didn't inform about this in the original post or made it clear elsewhere in this thread.I'm not a Reddit user, but I understand something was also posted there by the team (and perhaps on Twitter, but not sure about that one). I'm just not an active social media guys, so I don't follow all those sites.
The main bug causing the lockups appears to have been a sort of estoteric thing where the llvm compiler for ARM hardware was reordering some memory reads and writes for optimization, but that reordering, in one particular case, resulted in a thread locking deadlock situation. If this link opens for you, here is the bug fix: https://github.com/pfsense/FreeBSD-src/commit/4b914061a48bb289ede4d3a7362ed6adf9378c0f. This is also being backported into FreeBSD-12, I believe.
-
Still no GUI for ZFS?
-
and how about ZFS email notification, is it available on Pfsense 2.5.0
-
Upgraded SG-5100 to 21.02.
IPsec seems to have issue. Tunnels connect but some are duplicated and shown as disconnected at bottom of Status->IPsec page but instead create a different IPsec ID with a larger con# eg. con400000 vs typical lower number like con1000. These large connections have same information and show connection except there is blank where name should be. If I identify one what it should be and disconnect, reconnecting the "correct" one, or sending IP traffic across a tunnel still creates these incorrect IDs. This also slows down the interface when loading status. Some tunnels are fine and do not have this behaviour. I deleted the tunnels and recreated and same problem.
Anyone else ever see this?
Here is example (which IP address blocked out) that shows disconnected an a con400000 that actually connects...
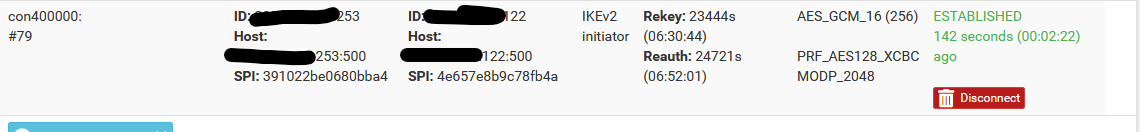
-
Seems there is a problem with updating snort GPLv2 suricata rules.
Anyone else seen this problem?
Starting rules update... Time: 2021-02-25 07:03:23 Downloading Emerging Threats Open rules md5 file... Checking Emerging Threats Open rules md5 file... Emerging Threats Open rules are up to date. Downloading Snort GPLv2 Community Rules md5 file... Snort GPLv2 Community Rules md5 download failed. %#ff26000)[Server returned error code 404. Server error message was: 404 Not Found] Snort GPLv2 Community Rules will not be updated. The Rules update has finished. Time: 2021-02-25 07:03:23 -
@elvisimprsntr said in pfSense Community Edition (CE) 2.5.0 and pfSense Plus 21.02 now available!:
Seems there is a problem with updating snort GPLv2 suricata rules.
Anyone else seen this problem?
Starting rules update... Time: 2021-02-25 07:03:23 Downloading Emerging Threats Open rules md5 file... Checking Emerging Threats Open rules md5 file... Emerging Threats Open rules are up to date. Downloading Snort GPLv2 Community Rules md5 file... Snort GPLv2 Community Rules md5 download failed. %#ff26000)[Server returned error code 404. Server error message was: 404 Not Found] Snort GPLv2 Community Rules will not be updated. The Rules update has finished. Time: 2021-02-25 07:03:23Are you running Suricata and using the Snort GPLv2 Community Rules?
What is the version of your Suricata package?
And what hardware and pfSense type? Is is CE or pfSense+ (on Netgate hardware)?
This line in your update log is very puzzling:
%#ff26000)[Server returned error code 404.It's the "%#ff26000)" part that is weird. Almost like some kind of memory corruption occurred.
-
I tried to color code the error message in red when I posted the log output, unfortunately I cannot edit my OP.
I am running Suricata 6.0.0_8
Hardware is a https://protectli.com/product/fw4a/
Running pfsense CE
-
@elvisimprsntr said in pfSense Community Edition (CE) 2.5.0 and pfSense Plus 21.02 now available!:
I tried to color code the error message in red when I posted the log output, unfortunately I cannot edit my OP.
I am running Suricata 6.0.0_8
Hardware is a https://protectli.com/product/fw4a/
Running pfsense CE
Oh, okay ...
 . That one had me wondering for a minute.
. That one had me wondering for a minute.I don't know of any other problems reported like that recently. I will fire up my test VM and check it out to be sure. Many times this is caused by one of the following:
-
a temporary issue with posting of the actual file (and copying it to all the servers in the CDN network). This would be on the Snort end and will heal itself once the file is replicated around.
-
a problem accessing the specific Amazon Web Services IP space where the rules file lives. Even though the URL says it's a snort.org site, it actually redirects you to AWS infrastructure. In the past, folks using pfBlockerNG with various IP feeds have sometimes encountered feeds that block some of the IP space of AWS.
-
a problem with Squid or Squidguard blocking the download if those packages are installed.
Wait a bit and then retry the rules update manually by going to the UPDATES tab and clicking the button. If it still does not succeed and fails with the same error, then I would first check for anything blocking stuff on your end.
I will post back with the results of my test shortly.
-
-
Thanks.
I disabled pfBLockNG and DNSBL and attempted manual suricata update.
Unfortunately, I get the same error message -
@elvisimprsntr said in pfSense Community Edition (CE) 2.5.0 and pfSense Plus 21.02 now available!:
Thanks.
I disabled pfBLockNG and DNSBL and attempted manual suricata update.
Unfortunately, I get the same error messageI've duplicated the error in my VM, and the answer is not good. It's not a problem with the Suricata package. Instead, it appears the Snort team has changed the Community Rules to work with only with Snort3 now. The old URL (filename, actually) no longer works, and the new community rules file is named "snort3-community-rules.tar.gz".
-
Thanks for the detective work!
I guess there is not workaround other than wait for a package update
-
@elvisimprsntr said in pfSense Community Edition (CE) 2.5.0 and pfSense Plus 21.02 now available!:
Thanks for the detective work!
I guess there is not workaround other than wait for a package update
Well, first I need to check and test if those rules will even work in Snort 2.x. If they have rewritten the rules to use any Snort3-specific syntax, then they won't work in Snort 2.x binaries anymore.
-
I have 2 minor issues.
1 - igb driver looks like it had a replacement, different sysctl's etc. I noticed its unstable when checksums are off, fixed by turning on (was off from som etesting I did a while ago and forgot to turn back on).
2 - For some reason the LAN rule page is slow to load, slow after save, apply also, WAN and other rule pages are fine.Everything else at first glance seems ok.
-
Just for kicks, I enable use snort custom URL on the on the suricata global settings tab and pasted the v3 community rules URL and performed a manual update.
https://www.snort.org/downloads/community/snort3-community-rules.tar.gz
The update worked. I can't tell is the rules are actually working.
-
@elvisimprsntr said in pfSense Community Edition (CE) 2.5.0 and pfSense Plus 21.02 now available!:
Just for kicks, I enable use snort custom URL on the on the suricata global settings tab and pasted the v3 community rules URL and performed a manual update.
https://www.snort.org/downloads/community/snort3-community-rules.tar.gz
The update worked. I can't tell is the rules are actually working.
I believe all (or nearly all) of the Community Rules are default disabled out-of-the-box by the creator (Talos). So they are actually not loading. Open up and look at the file and you will see the comment character ("#") in front of each rule. That means it is not processed by the Snort or Suricata engine.
To really test compatibility, you would need to remove the comment and enable each rule. I'm researching now to see if these new rules are backwards compatible.
Let's take the discussion out of this thread and instead post any further replies and updates to a new thread that has opened in the IDS/IPS sub-forum. This is not an issue with the new pfSense releases. It is an externally-caused problem.
-
@elvisimprsntr
I don’t think snort3 rules will work with Suricata. Please extract from my pfSense settings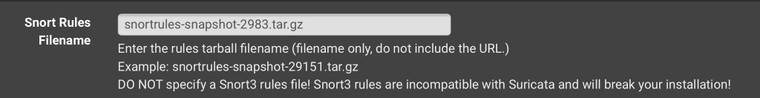
Hope it helps