OpenVPN fails with 2.50
-
I was looking in that area too and the keys match. Here's my configs:
(Sorry, I couldn't screen capture the entire page)Client
General Information
DisabledDisable this client
Set this option to disable this client without removing it from the list.
Server mode
Peer to Peer ( SSL/TLS )
Protocol
UDP on IPv4 only
Device mode
tun - Layer 3 Tunnel Mode
"tun" mode carries IPv4 and IPv6 (OSI layer 3) and is the most common and compatible mode across all platforms.
"tap" mode is capable of carrying 802.3 (OSI Layer 2.)
Interface
WAN
The interface used by the firewall to originate this OpenVPN client connection
Local port
Set this option to bind to a specific port. Leave this blank or enter 0 for a random dynamic port.
Server host or address
vpn.jknott.net
The IP address or hostname of the OpenVPN server.
Server port
1194
The port used by the server to receive client connections.
Proxy host or address
The address for an HTTP Proxy this client can use to connect to a remote server.
TCP must be used for the client and server protocol.
Proxy port
Proxy Authentication
none
The type of authentication used by the proxy server.
Description
A description may be entered here for administrative reference (not parsed).
User Authentication Settings
Username
Leave empty when no user name is needed
Password
Leave empty when no password is needed
Authentication RetryDo not retry connection when authentication fails
When enabled, the OpenVPN process will exit if it receives an authentication failure message. The default behavior is to retry.
Cryptographic Settings
TLS ConfigurationUse a TLS Key
A TLS key enhances security of an OpenVPN connection by requiring both parties to have a common key before a peer can perform a TLS handshake. This layer of HMAC authentication allows control channel packets without the proper key to be dropped, protecting the peers from attack or unauthorized connections.The TLS Key does not have any effect on tunnel data.
TLS Key2048 bit OpenVPN static key
-----BEGIN OpenVPN Static key V1-----
d737a4e2b3bb487f1cc60e55f140135a
96e0c969b9fead9f4d449a829c71a5d5
b8d470d001147ae074e0330952325735
0306e7635b4d58a8433e4ecd36845aee
cd49a96ced0b2a6b1e5fce3e151e18bf
810bf767310ca0888476f20a3b32fc94
0d4a99ca83bf7978ad9b9b5f3bd48a99
e796c0968a137403d45e753cc359a330
fb8808e081d8a5ba6b1065dab8165cb6
3b73405c96351a131b67f15fda0e803e
4743fe1055d4d8763ebe954216999de3
30a10b6b36eaa108f0d0f7d36585561d
bf70103495cc2e08a41afcec37f9971c
4234a060f31d1cafb8c07db013aa15e6
22d996a03652db7241348adc56f16035
1a2eaef7c99b006a582042d29afb8f09
-----END OpenVPN Static key V1-----Paste the TLS key here.
This key is used to sign control channel packets with an HMAC signature for authentication when establishing the tunnel.
TLS Key Usage Mode
TLS Authentication
In Authentication mode the TLS key is used only as HMAC authentication for the control channel, protecting the peers from unauthorized connections.
Encryption and Authentication mode also encrypts control channel communication, providing more privacy and traffic control channel obfuscation.
TLS keydir direction
Use default direction
The TLS Key Direction must be set to complementary values on the client and server. For example, if the server is set to 0, the client must be set to 1. Both may be set to omit the direction, in which case the TLS Key will be used bidirectionally.
Peer Certificate Authority
jknott.net
Peer Certificate Revocation listNo Certificate Revocation Lists defined. One may be created here: System > Cert. Manager > Certificate Revocation
Client Certificate
VPN to home network (Server: Yes, CA: jknott.net, In Use)
Data Encryption NegotiationEnable Data Encryption Negotiation
This option allows OpenVPN clients and servers to negotiate a compatible set of acceptable cryptographic data encryption algorithms from those selected in the Data Encryption Algorithms list below. Disabling this feature is deprecated.
Data Encryption AlgorithmsAES-128-CBC (128 bit key, 128 bit block)AES-128-CFB (128 bit key, 128 bit block)AES-128-CFB1 (128 bit key, 128 bit block)AES-128-CFB8 (128 bit key, 128 bit block)AES-128-GCM (128 bit key, 128 bit block)AES-128-OFB (128 bit key, 128 bit block)AES-192-CBC (192 bit key, 128 bit block)AES-192-CFB (192 bit key, 128 bit block)AES-192-CFB1 (192 bit key, 128 bit block)AES-192-CFB8 (192 bit key, 128 bit block)AES-192-GCM (192 bit key, 128 bit block)AES-192-OFB (192 bit key, 128 bit block)AES-256-CBC (256 bit key, 128 bit block)AES-256-CFB (256 bit key, 128 bit block)AES-256-CFB1 (256 bit key, 128 bit block)AES-256-CFB8 (256 bit key, 128 bit block)AES-256-GCM (256 bit key, 128 bit block)AES-256-OFB (256 bit key, 128 bit block)ARIA-128-CBC (128 bit key, 128 bit block)ARIA-128-CFB (128 bit key, 128 bit block)ARIA-128-CFB1 (128 bit key, 128 bit block)ARIA-128-CFB8 (128 bit key, 128 bit block)ARIA-128-OFB (128 bit key, 128 bit block)ARIA-192-CBC (192 bit key, 128 bit block)ARIA-192-CFB (192 bit key, 128 bit block)ARIA-192-CFB1 (192 bit key, 128 bit block)ARIA-192-CFB8 (192 bit key, 128 bit block)ARIA-192-OFB (192 bit key, 128 bit block)ARIA-256-CBC (256 bit key, 128 bit block)ARIA-256-CFB (256 bit key, 128 bit block)ARIA-256-CFB1 (256 bit key, 128 bit block)ARIA-256-CFB8 (256 bit key, 128 bit block)ARIA-256-OFB (256 bit key, 128 bit block)BF-CBC (128 bit key by default, 64 bit block)BF-CFB (128 bit key by default, 64 bit block)BF-OFB (128 bit key by default, 64 bit block)CAMELLIA-128-CBC (128 bit key, 128 bit block)CAMELLIA-128-CFB (128 bit key, 128 bit block)CAMELLIA-128-CFB1 (128 bit key, 128 bit block)CAMELLIA-128-CFB8 (128 bit key, 128 bit block)CAMELLIA-128-OFB (128 bit key, 128 bit block)CAMELLIA-192-CBC (192 bit key, 128 bit block)CAMELLIA-192-CFB (192 bit key, 128 bit block)CAMELLIA-192-CFB1 (192 bit key, 128 bit block)CAMELLIA-192-CFB8 (192 bit key, 128 bit block)CAMELLIA-192-OFB (192 bit key, 128 bit block)CAMELLIA-256-CBC (256 bit key, 128 bit block)CAMELLIA-256-CFB (256 bit key, 128 bit block)CAMELLIA-256-CFB1 (256 bit key, 128 bit block)CAMELLIA-256-CFB8 (256 bit key, 128 bit block)CAMELLIA-256-OFB (256 bit key, 128 bit block)CAST5-CBC (128 bit key by default, 64 bit block)CAST5-CFB (128 bit key by default, 64 bit block)CAST5-OFB (128 bit key by default, 64 bit block)CHACHA20-POLY1305 (256 bit key, stream cipher)DES-CBC (64 bit key, 64 bit block)DES-CFB (64 bit key, 64 bit block)DES-CFB1 (64 bit key, 64 bit block)DES-CFB8 (64 bit key, 64 bit block)DES-EDE-CBC (128 bit key, 64 bit block)DES-EDE-CFB (128 bit key, 64 bit block)DES-EDE-OFB (128 bit key, 64 bit block)DES-EDE3-CBC (192 bit key, 64 bit block)DES-EDE3-CFB (192 bit key, 64 bit block)DES-EDE3-CFB1 (192 bit key, 64 bit block)DES-EDE3-CFB8 (192 bit key, 64 bit block)DES-EDE3-OFB (192 bit key, 64 bit block)DES-OFB (64 bit key, 64 bit block)DESX-CBC (192 bit key, 64 bit block)IDEA-CBC (128 bit key, 64 bit block)IDEA-CFB (128 bit key, 64 bit block)IDEA-OFB (128 bit key, 64 bit block)RC2-40-CBC (40 bit key by default, 64 bit block)RC2-64-CBC (64 bit key by default, 64 bit block)RC2-CBC (128 bit key by default, 64 bit block)RC2-CFB (128 bit key by default, 64 bit block)RC2-OFB (128 bit key by default, 64 bit block)RC5-CBC (128 bit key by default, 64 bit block)RC5-CFB (128 bit key by default, 64 bit block)RC5-OFB (128 bit key by default, 64 bit block)SEED-CBC (128 bit key, 128 bit block)SEED-CFB (128 bit key, 128 bit block)SEED-OFB (128 bit key, 128 bit block)SM4-CBC (128 bit key, 128 bit block)SM4-CFB (128 bit key, 128 bit block)SM4-OFB (128 bit key, 128 bit block)None (No Encryption)
Available Data Encryption Algorithms
Click to add or remove an algorithm from the list
AES-256-GCMAES-128-GCMCHACHA20-POLY1305
Allowed Data Encryption Algorithms. Click an algorithm name to remove it from the list
The order of the selected Data Encryption Algorithms is respected by OpenVPN.
Fallback Data Encryption Algorithm
AES-256-CBC (256 bit key, 128 bit block)
The Fallback Data Encryption Algorithm used for data channel packets when communicating with clients that do not support data encryption algorithm negotiation. This algorithm is automatically included in the Data Encryption Algorithms list.
Auth digest algorithm
SHA256 (256-bit)
The algorithm used to authenticate data channel packets, and control channel packets if a TLS Key is present.
When an AEAD Encryption Algorithm mode is used, such as AES-GCM, this digest is used for the control channel only, not the data channel.
Set this to the same value as the server. While SHA1 is the default for OpenVPN, this algorithm is insecure.
Hardware Crypto
No Hardware Crypto Acceleration
Tunnel Settings
IPv4 Tunnel Network
This is the IPv4 virtual network used for private communications between this client and the server expressed using CIDR notation (e.g. 10.0.8.0/24). The second usable address in the network will be assigned to the client virtual interface. Leave blank if the server is capable of providing addresses to clients.
IPv6 Tunnel Network
This is the IPv6 virtual network used for private communications between this client and the server expressed using CIDR notation (e.g. fe80::/64). When set static using this field, the ::2 address in the network will be assigned to the client virtual interface. Leave blank if the server is capable of providing addresses to clients.
IPv4 Remote network(s)
IPv4 networks that will be routed through the tunnel, so that a site-to-site VPN can be established without manually changing the routing tables. Expressed as a comma-separated list of one or more CIDR ranges. If this is a site-to-site VPN, enter the remote LAN/s here. May be left blank for non site-to-site VPN.
IPv6 Remote network(s)
These are the IPv6 networks that will be routed through the tunnel, so that a site-to-site VPN can be established without manually changing the routing tables. Expressed as a comma-separated list of one or more IP/PREFIX. If this is a site-to-site VPN, enter the remote LAN/s here. May be left blank for non site-to-site VPN.
Limit outgoing bandwidth
Between 100 and 100,000,000 bytes/sec
Maximum outgoing bandwidth for this tunnel. Leave empty for no limit. The input value has to be something between 100 bytes/sec and 100 Mbytes/sec (entered as bytes per second). Not compatible with UDP Fast I/O.
Allow Compression
Refuse any non-stub compression (Most secure)
Allow compression to be used with this VPN instance.
Compression can potentially increase throughput but may allow an attacker to extract secrets if they can control compressed plaintext traversing the VPN (e.g. HTTP). Before enabling compression, consult information about the VORACLE, CRIME, TIME, and BREACH attacks against TLS to decide if the use case for this specific VPN is vulnerable to attack.Asymmetric compression allows an easier transition when connecting with older peers.
Topology
Subnet -- One IP address per client in a common subnet
Specifies the method used to configure a virtual adapter IP address.
Type-of-ServiceSet the TOS IP header value of tunnel packets to match the encapsulated packet value.
Don't pull routesBars the server from adding routes to the client's routing table
This option still allows the server to set the TCP/IP properties of the client's TUN/TAP interface.
Don't add/remove routesDon't add or remove routes automatically
Do not execute operating system commands to install routes. Instead, pass routes to --route-up script using environmental variables.
Ping settings
Inactive
0
Causes OpenVPN to exit after n seconds of inactivity on the TUN/TAP device.
The time length of inactivity is measured since the last incoming or outgoing tunnel packet.
0 disables this feature.
Ping method
keepalive -- Use keepalive helper to define ping configuration
keepalive helper uses interval and timeout parameters to define ping and ping-restart values as follows:
ping = interval
ping-restart = timeout
Interval
10
Timeout
60
Advanced Configuration
Custom options
Enter any additional options to add to the OpenVPN client configuration here, separated by semicolon.
UDP Fast I/OUse fast I/O operations with UDP writes to tun/tap. Experimental.
Optimizes the packet write event loop, improving CPU efficiency by 5% to 10%. Not compatible with all platforms, and not compatible with OpenVPN bandwidth limiting.
Exit Notify
Disabled
Send an explicit exit notification to connected servers/peers when restarting or shutting down, so they may immediately disconnect rather than waiting for a timeout. This value controls how many times this instance will attempt to send the exit notification.
Send/Receive Buffer
Default
Configure a Send and Receive Buffer size for OpenVPN. The default buffer size can be too small in many cases, depending on hardware and network uplink speeds. Finding the best buffer size can take some experimentation. To test the best value for a site, start at 512KiB and test higher and lower values.
Gateway creation Both IPv4 only IPv6 only
If you assign a virtual interface to this OpenVPN client, this setting controls which gateway types will be created. The default setting is 'both'.
Verbosity level
default
Each level shows all info from the previous levels. Level 3 is recommended for a good summary of what's happening without being swamped by output.None: Only fatal errors
Default through 4: Normal usage range
5: Output R and W characters to the console for each packet read and write. Uppercase is used for TCP/UDP packets and lowercase is used for TUN/TAP packets.
6-11: Debug info rangeServer
General Information
DisabledDisable this server
Set this option to disable this server without removing it from the list.
Server mode
Remote Access ( SSL/TLS )
Protocol
UDP on IPv4 only
Device mode
tun - Layer 3 Tunnel Mode
"tun" mode carries IPv4 and IPv6 (OSI layer 3) and is the most common and compatible mode across all platforms.
"tap" mode is capable of carrying 802.3 (OSI Layer 2.)
Interface
WAN
The interface or Virtual IP address where OpenVPN will receive client connections.
Local port
1194
The port used by OpenVPN to receive client connections.
Description
Remote access
A description may be entered here for administrative reference (not parsed).
Cryptographic Settings
TLS ConfigurationUse a TLS Key
A TLS key enhances security of an OpenVPN connection by requiring both parties to have a common key before a peer can perform a TLS handshake. This layer of HMAC authentication allows control channel packets without the proper key to be dropped, protecting the peers from attack or unauthorized connections.The TLS Key does not have any effect on tunnel data.
TLS Key2048 bit OpenVPN static key
-----BEGIN OpenVPN Static key V1-----
d737a4e2b3bb487f1cc60e55f140135a
96e0c969b9fead9f4d449a829c71a5d5
b8d470d001147ae074e0330952325735
0306e7635b4d58a8433e4ecd36845aee
cd49a96ced0b2a6b1e5fce3e151e18bf
810bf767310ca0888476f20a3b32fc94
0d4a99ca83bf7978ad9b9b5f3bd48a99
e796c0968a137403d45e753cc359a330
fb8808e081d8a5ba6b1065dab8165cb6
3b73405c96351a131b67f15fda0e803e
4743fe1055d4d8763ebe954216999de3
30a10b6b36eaa108f0d0f7d36585561d
bf70103495cc2e08a41afcec37f9971c
4234a060f31d1cafb8c07db013aa15e6
22d996a03652db7241348adc56f16035
1a2eaef7c99b006a582042d29afb8f09
-----END OpenVPN Static key V1-----Paste the TLS key here.
This key is used to sign control channel packets with an HMAC signature for authentication when establishing the tunnel.
TLS Key Usage Mode
TLS Authentication
In Authentication mode the TLS key is used only as HMAC authentication for the control channel, protecting the peers from unauthorized connections.
Encryption and Authentication mode also encrypts control channel communication, providing more privacy and traffic control channel obfuscation.
TLS keydir direction
Use default direction
The TLS Key Direction must be set to complementary values on the client and server. For example, if the server is set to 0, the client must be set to 1. Both may be set to omit the direction, in which case the TLS Key will be used bidirectionally.
Peer Certificate Authority
jknott.net
Peer Certificate Revocation listNo Certificate Revocation Lists defined. One may be created here: System > Cert. Manager
OCSP CheckCheck client certificates with OCSP
Server certificate
VPN to home network (Server: Yes, CA: jknott.net, In Use)
DH Parameter Length
2048 bit
Diffie-Hellman (DH) parameter set used for key exchange.
ECDH Curve
Use Default
The Elliptic Curve to use for key exchange.
The curve from the server certificate is used by default when the server uses an ECDSA certificate. Otherwise, secp384r1 is used as a fallback.
Data Encryption NegotiationEnable Data Encryption Negotiation
This option allows OpenVPN clients and servers to negotiate a compatible set of acceptable cryptographic data encryption algorithms from those selected in the Data Encryption Algorithms list below. Disabling this feature is deprecated.
Data Encryption AlgorithmsAES-128-CBC (128 bit key, 128 bit block)AES-128-CFB (128 bit key, 128 bit block)AES-128-CFB1 (128 bit key, 128 bit block)AES-128-CFB8 (128 bit key, 128 bit block)AES-128-GCM (128 bit key, 128 bit block)AES-128-OFB (128 bit key, 128 bit block)AES-192-CBC (192 bit key, 128 bit block)AES-192-CFB (192 bit key, 128 bit block)AES-192-CFB1 (192 bit key, 128 bit block)AES-192-CFB8 (192 bit key, 128 bit block)AES-192-GCM (192 bit key, 128 bit block)AES-192-OFB (192 bit key, 128 bit block)AES-256-CBC (256 bit key, 128 bit block)AES-256-CFB (256 bit key, 128 bit block)AES-256-CFB1 (256 bit key, 128 bit block)AES-256-CFB8 (256 bit key, 128 bit block)AES-256-GCM (256 bit key, 128 bit block)AES-256-OFB (256 bit key, 128 bit block)ARIA-128-CBC (128 bit key, 128 bit block)ARIA-128-CFB (128 bit key, 128 bit block)ARIA-128-CFB1 (128 bit key, 128 bit block)ARIA-128-CFB8 (128 bit key, 128 bit block)ARIA-128-OFB (128 bit key, 128 bit block)ARIA-192-CBC (192 bit key, 128 bit block)ARIA-192-CFB (192 bit key, 128 bit block)ARIA-192-CFB1 (192 bit key, 128 bit block)ARIA-192-CFB8 (192 bit key, 128 bit block)ARIA-192-OFB (192 bit key, 128 bit block)ARIA-256-CBC (256 bit key, 128 bit block)ARIA-256-CFB (256 bit key, 128 bit block)ARIA-256-CFB1 (256 bit key, 128 bit block)ARIA-256-CFB8 (256 bit key, 128 bit block)ARIA-256-OFB (256 bit key, 128 bit block)BF-CBC (128 bit key by default, 64 bit block)BF-CFB (128 bit key by default, 64 bit block)BF-OFB (128 bit key by default, 64 bit block)CAMELLIA-128-CBC (128 bit key, 128 bit block)CAMELLIA-128-CFB (128 bit key, 128 bit block)CAMELLIA-128-CFB1 (128 bit key, 128 bit block)CAMELLIA-128-CFB8 (128 bit key, 128 bit block)CAMELLIA-128-OFB (128 bit key, 128 bit block)CAMELLIA-192-CBC (192 bit key, 128 bit block)CAMELLIA-192-CFB (192 bit key, 128 bit block)CAMELLIA-192-CFB1 (192 bit key, 128 bit block)CAMELLIA-192-CFB8 (192 bit key, 128 bit block)CAMELLIA-192-OFB (192 bit key, 128 bit block)CAMELLIA-256-CBC (256 bit key, 128 bit block)CAMELLIA-256-CFB (256 bit key, 128 bit block)CAMELLIA-256-CFB1 (256 bit key, 128 bit block)CAMELLIA-256-CFB8 (256 bit key, 128 bit block)CAMELLIA-256-OFB (256 bit key, 128 bit block)CAST5-CBC (128 bit key by default, 64 bit block)CAST5-CFB (128 bit key by default, 64 bit block)CAST5-OFB (128 bit key by default, 64 bit block)CHACHA20-POLY1305 (256 bit key, stream cipher)DES-CBC (64 bit key, 64 bit block)DES-CFB (64 bit key, 64 bit block)DES-CFB1 (64 bit key, 64 bit block)DES-CFB8 (64 bit key, 64 bit block)DES-EDE-CBC (128 bit key, 64 bit block)DES-EDE-CFB (128 bit key, 64 bit block)DES-EDE-OFB (128 bit key, 64 bit block)DES-EDE3-CBC (192 bit key, 64 bit block)DES-EDE3-CFB (192 bit key, 64 bit block)DES-EDE3-CFB1 (192 bit key, 64 bit block)DES-EDE3-CFB8 (192 bit key, 64 bit block)DES-EDE3-OFB (192 bit key, 64 bit block)DES-OFB (64 bit key, 64 bit block)DESX-CBC (192 bit key, 64 bit block)IDEA-CBC (128 bit key, 64 bit block)IDEA-CFB (128 bit key, 64 bit block)IDEA-OFB (128 bit key, 64 bit block)RC2-40-CBC (40 bit key by default, 64 bit block)RC2-64-CBC (64 bit key by default, 64 bit block)RC2-CBC (128 bit key by default, 64 bit block)RC2-CFB (128 bit key by default, 64 bit block)RC2-OFB (128 bit key by default, 64 bit block)RC5-CBC (128 bit key by default, 64 bit block)RC5-CFB (128 bit key by default, 64 bit block)RC5-OFB (128 bit key by default, 64 bit block)SEED-CBC (128 bit key, 128 bit block)SEED-CFB (128 bit key, 128 bit block)SEED-OFB (128 bit key, 128 bit block)SM4-CBC (128 bit key, 128 bit block)SM4-CFB (128 bit key, 128 bit block)SM4-OFB (128 bit key, 128 bit block)None (No Encryption)
Available Data Encryption Algorithms
Click to add or remove an algorithm from the list
AES-256-GCMAES-128-GCMCHACHA20-POLY1305
Allowed Data Encryption Algorithms. Click an algorithm name to remove it from the list
The order of the selected Data Encryption Algorithms is respected by OpenVPN.
Fallback Data Encryption Algorithm
AES-256-CBC (256 bit key, 128 bit block)
The Fallback Data Encryption Algorithm used for data channel packets when communicating with clients that do not support data encryption algorithm negotiation. This algorithm is automatically included in the Data Encryption Algorithms list.
Auth digest algorithm
SHA256 (256-bit)
The algorithm used to authenticate data channel packets, and control channel packets if a TLS Key is present.
When an AEAD Encryption Algorithm mode is used, such as AES-GCM, this digest is used for the control channel only, not the data channel.
The server and all clients must have the same setting. While SHA1 is the default for OpenVPN, this algorithm is insecure.
Hardware Crypto
No Hardware Crypto Acceleration
Certificate Depth
One (Client+Server)
When a certificate-based client logs in, do not accept certificates below this depth. Useful for denying certificates made with intermediate CAs generated from the same CA as the server.
Tunnel Settings
IPv4 Tunnel Network
172.16.255.0/24
This is the IPv4 virtual network used for private communications between this server and client hosts expressed using CIDR notation (e.g. 10.0.8.0/24). The first usable address in the network will be assigned to the server virtual interface. The remaining usable addresses will be assigned to connecting clients.
IPv6 Tunnel Network
2607:fea8:4c82:5900::/64
This is the IPv6 virtual network used for private communications between this server and client hosts expressed using CIDR notation (e.g. fe80::/64). The ::1 address in the network will be assigned to the server virtual interface. The remaining addresses will be assigned to connecting clients.
Redirect IPv4 GatewayForce all client-generated IPv4 traffic through the tunnel.
Redirect IPv6 GatewayForce all client-generated IPv6 traffic through the tunnel.
Concurrent connections
6
Specify the maximum number of clients allowed to concurrently connect to this server.
Allow Compression
Refuse any non-stub compression (Most secure)
Allow compression to be used with this VPN instance.
Compression can potentially increase throughput but may allow an attacker to extract secrets if they can control compressed plaintext traversing the VPN (e.g. HTTP). Before enabling compression, consult information about the VORACLE, CRIME, TIME, and BREACH attacks against TLS to decide if the use case for this specific VPN is vulnerable to attack.Asymmetric compression allows an easier transition when connecting with older peers.
Type-of-ServiceSet the TOS IP header value of tunnel packets to match the encapsulated packet value.
Inter-client communicationAllow communication between clients connected to this server
Duplicate ConnectionAllow multiple concurrent connections from the same user
When set, the same user may connect multiple times. When unset, a new connection from a user will disconnect the previous session.Users are identified by their username or certificate properties, depending on the VPN configuration. This practice is discouraged security reasons, but may be necessary in some environments.
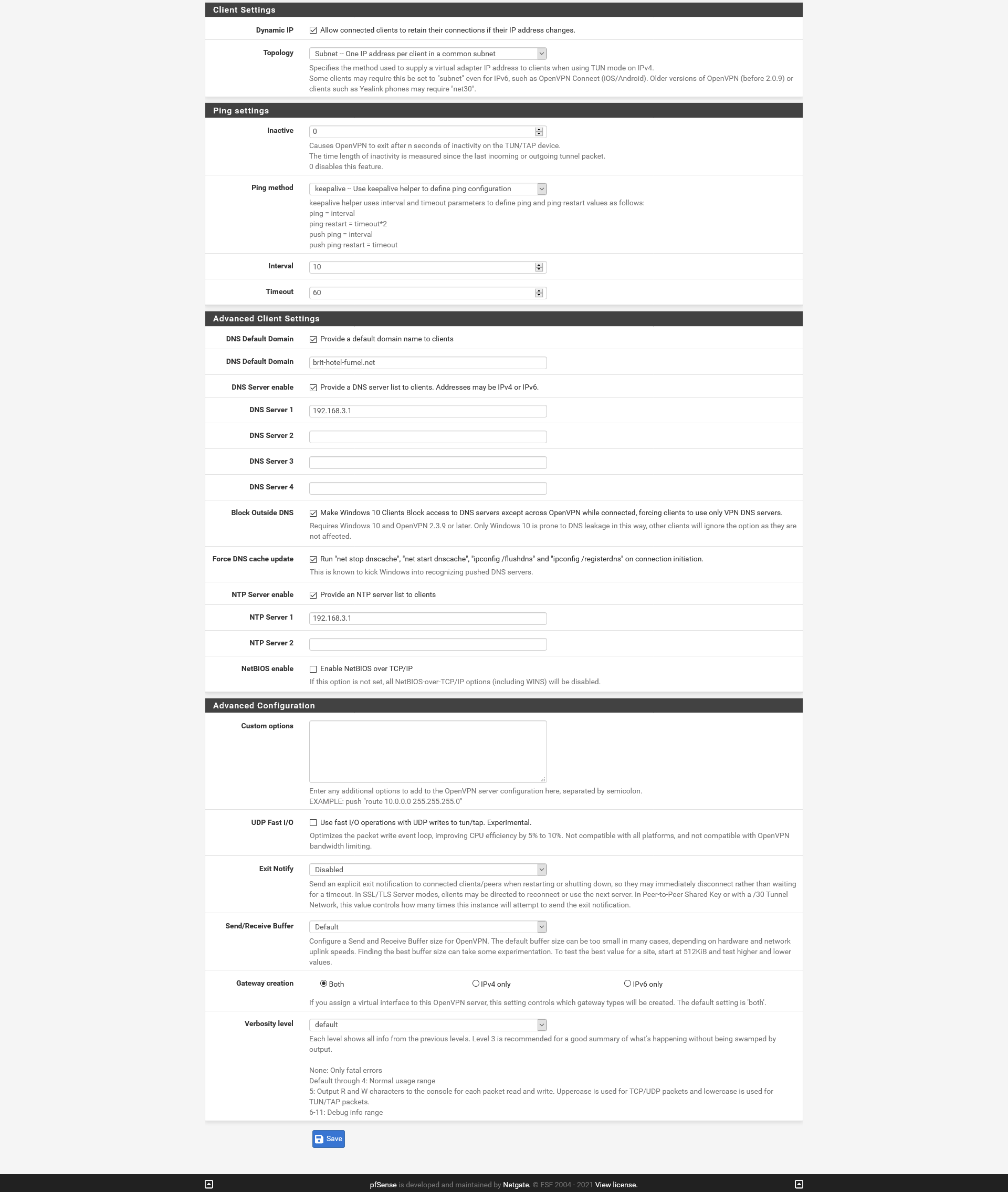
Client Settings
Dynamic IPAllow connected clients to retain their connections if their IP address changes.
Topology
Subnet -- One IP address per client in a common subnet
Specifies the method used to supply a virtual adapter IP address to clients when using TUN mode on IPv4.
Some clients may require this be set to "subnet" even for IPv6, such as OpenVPN Connect (iOS/Android). Older versions of OpenVPN (before 2.0.9) or clients such as Yealink phones may require "net30".
Ping settings
Inactive
0
Causes OpenVPN to exit after n seconds of inactivity on the TUN/TAP device.
The time length of inactivity is measured since the last incoming or outgoing tunnel packet.
0 disables this feature.
Ping method
keepalive -- Use keepalive helper to define ping configuration
keepalive helper uses interval and timeout parameters to define ping and ping-restart values as follows:
ping = interval
ping-restart = timeout*2
push ping = interval
push ping-restart = timeout
Interval
10
Timeout
60
Advanced Client Settings
DNS Default DomainProvide a default domain name to clients
DNS Server enableProvide a DNS server list to clients. Addresses may be IPv4 or IPv6.
Block Outside DNSMake Windows 10 Clients Block access to DNS servers except across OpenVPN while connected, forcing clients to use only VPN DNS servers.
Requires Windows 10 and OpenVPN 2.3.9 or later. Only Windows 10 is prone to DNS leakage in this way, other clients will ignore the option as they are not affected.
Force DNS cache updateRun "net stop dnscache", "net start dnscache", "ipconfig /flushdns" and "ipconfig /registerdns" on connection initiation.
This is known to kick Windows into recognizing pushed DNS servers.
NTP Server enableProvide an NTP server list to clients
NetBIOS enableEnable NetBIOS over TCP/IP
If this option is not set, all NetBIOS-over-TCP/IP options (including WINS) will be disabled.
Advanced Configuration
Custom options
push "route 0.0.0.0 0.0.0.0";push "route-ipv6 ::/0"
Enter any additional options to add to the OpenVPN server configuration here, separated by semicolon.
EXAMPLE: push "route 10.0.0.0 255.255.255.0"
UDP Fast I/OUse fast I/O operations with UDP writes to tun/tap. Experimental.
Optimizes the packet write event loop, improving CPU efficiency by 5% to 10%. Not compatible with all platforms, and not compatible with OpenVPN bandwidth limiting.
Exit Notify
Disabled
Send an explicit exit notification to connected clients/peers when restarting or shutting down, so they may immediately disconnect rather than waiting for a timeout. In SSL/TLS Server modes, clients may be directed to reconnect or use the next server. In Peer-to-Peer Shared Key or with a /30 Tunnel Network, this value controls how many times this instance will attempt to send the exit notification.
Send/Receive Buffer
Default
Configure a Send and Receive Buffer size for OpenVPN. The default buffer size can be too small in many cases, depending on hardware and network uplink speeds. Finding the best buffer size can take some experimentation. To test the best value for a site, start at 512KiB and test higher and lower values.
Gateway creation Both IPv4 only IPv6 only
If you assign a virtual interface to this OpenVPN server, this setting controls which gateway types will be created. The default setting is 'both'.
Verbosity level
default
Each level shows all info from the previous levels. Level 3 is recommended for a good summary of what's happening without being swamped by output.None: Only fatal errors
Default through 4: Normal usage range
5: Output R and W characters to the console for each packet read and write. Uppercase is used for TCP/UDP packets and lowercase is used for TUN/TAP packets.
6-11: Debug info rangeThe keys have been modified, so they won't connect to my network.
-
@jknott, it's an authhentification errors. Try to change your VPN client password.
-
No, I'm not connecting from the same network. I get 2 IPv4 addresses from my ISP. My firewall is on one and my notebook computer on the other.
I used colour coded Ethernet cables. The white ones connect directly to my modem. One goes to my firewall and the other to my notebook. I also have blue for connecting to my LAN and yellow for my test LAN. It helps to keep things straight when testing.

-
I'm using TLS, not user authentication, so no password used.
-
Same problem
-
I just tried again and once again I can connect over the local LAN, but not from outside my firewall. I have the same firewall rule for it since 2017.
-
In VPN>OpenVPN>Servers>Edit change Protocol to "UDP on IPv4 only".
-
That's all I have ever used.
-
Here are the relevant parts of the server and client logs:
Server:
Feb 25 10:04:24 firewall openvpn[88273]: 99.245.217.240:32854 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Feb 25 10:04:24 firewall openvpn[88273]: 99.245.217.240:32854 TLS Error: TLS handshake failed
Feb 25 10:04:34 firewall openvpn[38758]: WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info.
Feb 25 10:04:34 firewall openvpn[38758]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Feb 25 10:04:34 firewall openvpn[38758]: TCP/UDP: Preserving recently used remote address: [AF_INET]172.16.0.1:1194
Feb 25 10:04:34 firewall openvpn[38758]: UDPv4 link local: (not bound)
Feb 25 10:04:34 firewall openvpn[38758]: UDPv4 link remote: [AF_INET]172.16.0.1:1194Client - OpenSUSE 15.2 network manager
2021-02-25T10:04:23.967189-05:00 E520 NetworkManager[1467]: <warn>
[1614265463.9636]
vpn-connection[0x5649aad226e0,58407612-4bce-4c1b-9421-3dcc15e7f6e7,"firewall-UDP4-1194-E520-config",0]:
VPN connection: connect timeout exceeded.
2021-02-25T10:04:23.971490-05:00 E520 nm-openvpn-serv[5314]: Connect
timer expired, disconnecting.
2021-02-25T10:04:23.974072-05:00 E520 nm-openvpn[5317]: SIGTERM[hard,]
received, process exiting
2021-02-25T10:04:23.974457-05:00 E520 NetworkManager[1467]: <warn>
[1614265463.9729]
vpn-connection[0x5649aad226e0,58407612-4bce-4c1b-9421-3dcc15e7f6e7,"firewall-UDP4-1194-E520-config",0]:
VPN plugin: failed: connect-failed (1)
2021-02-25T10:04:23.974809-05:00 E520 NetworkManager[1467]: <info>
[1614265463.9730]
vpn-connection[0x5649aad226e0,58407612-4bce-4c1b-9421-3dcc15e7f6e7,"firewall-UDP4-1194-E520-config",0]:
VPN plugin: state changed: stopping (5)
2021-02-25T10:04:23.975133-05:00 E520 NetworkManager[1467]: <info>
[1614265463.9730]
vpn-connection[0x5649aad226e0,58407612-4bce-4c1b-9421-3dcc15e7f6e7,"firewall-UDP4-1194-E520-config",0]:
VPN plugin: state changed: stopped (6)As I mentioned earlier, it will connect when the client is on the LAN side of pfsense, but not WAN side. The client is OpenVPN 2.5.1, but I had similar results with 2.4.3.
-
@jknott
If you can connect on LAN, I would think the server config is fine?
Wondering now what did you set in the gui, did you change interface from WAN to LAN for that test or is it set to Any (and thus it listens on all if's)?
I've upgraded 5d ago to 2.5.0, and have 2 openvpn instances running without issues, where one serves a "Peer to Peer" for a pfSense still running 2.4.x. also with only certs and no user auth. No change has been done on that one, it reconnected after upgrade so at least we (I) know it can work...Did you try rebooting?

-
@bennyc said in OpenVPN fails with 2.50:
If you can connect on LAN, I would think the server config is fine?
My thought too.
Wondering now what did you set in the gui, did you change interface from WAN to LAN for that test or is it set to Any (and thus it listens on all if's)?
It's set to WAN, but I have tried any. No difference
Did you try rebooting?
Several times.
-
@jknott
Just curious, but has your only test been off the same CPE? I've seen strange behavior between clients on the same ISP (Cough... Comcast)
Maybe verify from somewhere external. -
I have 2 IPv4 addresses from my ISP. With my notebook plugged into the same modem as my firewall, I get a different address. So, it would appear as though it was another customer with my ISP. BTW, I have used this setup for years, for testing. However, I just tried tethering with my cell phone and that seems to work. I wonder what's different with 2.5.0, as this using my 2nd IPv4 address worked with the pfsense 2.4.5, as I have done many times. My firewall rule for OpenVPN hasn't changed since Sept. 19, 2017 and the source is any. Also, why is it allowing a connection from the LAN?
-
- Make sure your default gateway is set to your WAN gateway on System > Routing
- Try setting the OpenVPN server Protocol value to "UDP IPv4 and IPv6 on all interfaces (multihome)"
-
I have only used IPv4 for the UDP packets, as I run into DNS issues, due to the IPv4 host name being an alias and IPv6 being an actual address. Regardless, this worked reliably until I updated to pfsense 2.5.0. I can ping pfsense from my notebook and both the OpenVPN logs and Packet Capture show the connection is being attempted. The gateway is correct as it has been since I started using pfsense 5 years ago. Connecting the VPN in this manner most recently worked the day before I updated to 2.5.0, when I was testing for an issue with the Windows client. I normally use the VPN with Linux.
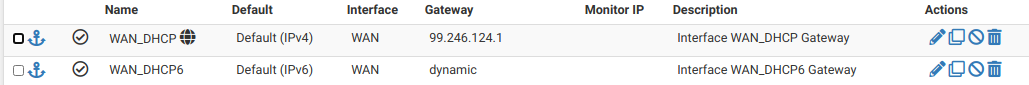
-
Wow, detail are not missing here ....
This is what I have :
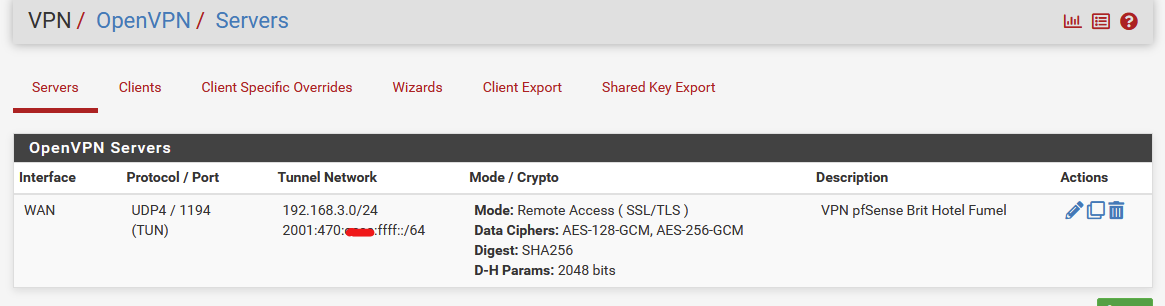
The settings :
.....
Ok, cut in half :
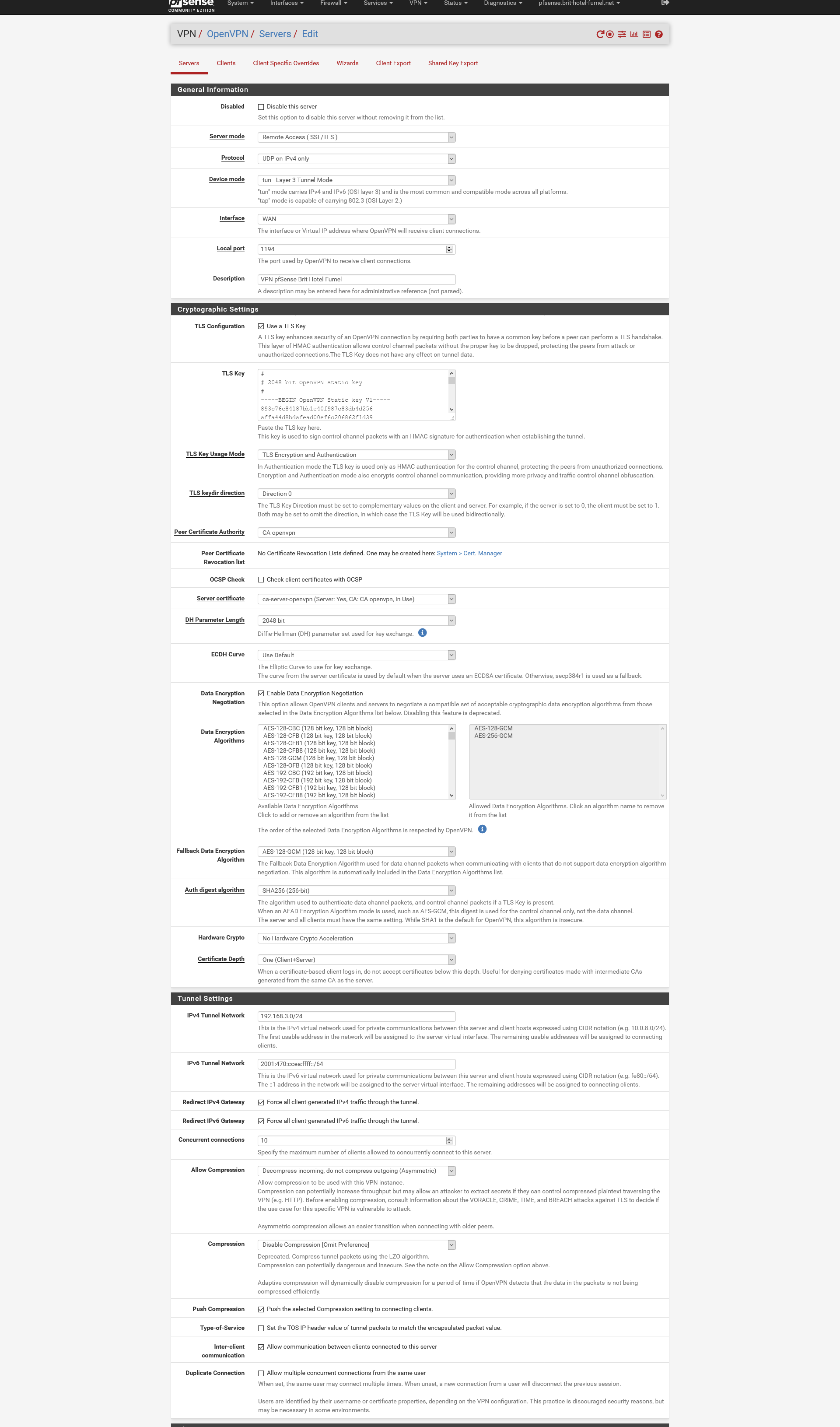
When exporting :
Note : I do accept the new "2.5.0 OpenVPN stuff".
When I export, I only use one of these button :
Result : using the iPhone OpenVPN Connect App (the official one ?!) it connects using IPv4 - IP ok - also received an IPv6 (correct address) but IPv6 is out.
I can live with that.@home, I use the OpenVPN connect version 2.4.9 or 2.4.10 (have to check - it from last year) NOT the latest 2.5.1 from yesterday or so (and yes, shame or Netgate for not pushing that one out the minute it came out of the oven, I'm with you here
 )
)It connects with any (or just one) warnings just fine !
IPv4 and IPv6 are up !My OpenVPN servers bind to my WAN = 192.168.10.3 - I have an upstream ISP router with its NAT rule stuff for VPN on port 1194-UDP.
"Works for yers" .Now this seems strange. I presumed that I needed to upgrade at least my Windows 10 home OpenVPN connect App, but no ... it was working and kept on working.
Btw : my routes :
I never use my VPN client facilities (I do have a xxxxVPN to play with) - they are just there so I can fool around with it so I can maybe once understand some one wants to tunnel my already TLS encrypted traffic.
I'm using he.net for my IPv6 because, well, you know why.edit : Maybe I should raise my cyphering. Dono.
The VPN is just for me so I can 'do things at work' while not being at work. -
The VPN is working, just not when I use my 2nd IPv4 address. As I mentioned above, it does work when my notebook is tethered to my phone. My ISP provides 2 IPv4 addresses, which are not in the same /23 subnet and I normally use the 2nd address for testing. Testing this way has worked for years, until I updated to pfsense 2.5.0. I'd rather not have to tether to my phone for testing, but it appears I may have to.
What changed in pfsense or OpenVPN to cause this?
-
@jimp said in OpenVPN fails with 2.50:
"UDP IPv4 and IPv6 on all interfaces (multihome)"
Set that and try it again -- doesn't matter why you have the settings you have now or if it worked before.
-
It still fails when I use my second IPv4 address.
-
I just tried with ssh and the same thing happens. If I use my 2nd IPv4 address, Packet Capture shows the attempt, but no connection. I can connect with ssh if I tether to my phone. This shows the problem is with FreeBSD and not OpenVPN.
Here's what ifconfig shows:
inet 99.246.125.121 netmask 0xfffffe00 broadcast 255.255.255.255This shows the appropriate /23 subnet mask. My 2nd address (99.245.223.190) is also a /23, but in a different subnet.
On the other hand, ping works in both directions. What is it that's causing this issue with OpenVPN & ssh?