Can't get port forwarding to work
-
I have successfully configure a WG interface on pfSense using this guide https://docs.netgate.com/pfsense/en/latest/recipes/wireguard-client.html I have set host 192.168.100.9 only to use created WG_MULLVAD interface and the host can access the Internet through that interface without issues.
Now I wanted to be able to access port on the host through VPN provider. I have configured port forwarding on Mullvad's website, and forwarding to firewall seems to be working as I can see following:
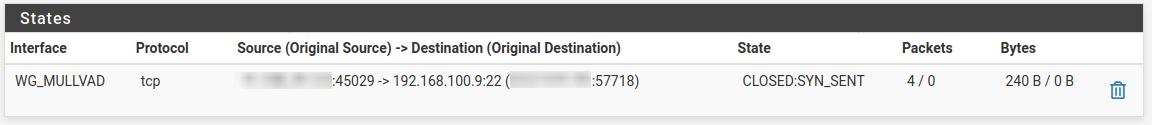
I have also configured port forwarding, so host's port would be accessible through WG_MULLVAD interface:
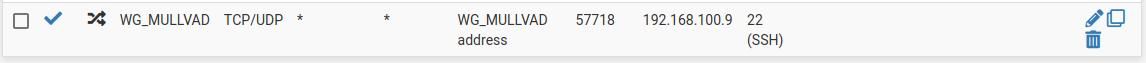
I think I'm missing some kind of inbound rule to allow traffic from WG interface to the host. Not sure how to configure it. Could somebody help me? -
@apstndp What's your outbound NAT look like for the 192.168.100.9 host?
-
@vbman213 Here are my rules for outbound NAT
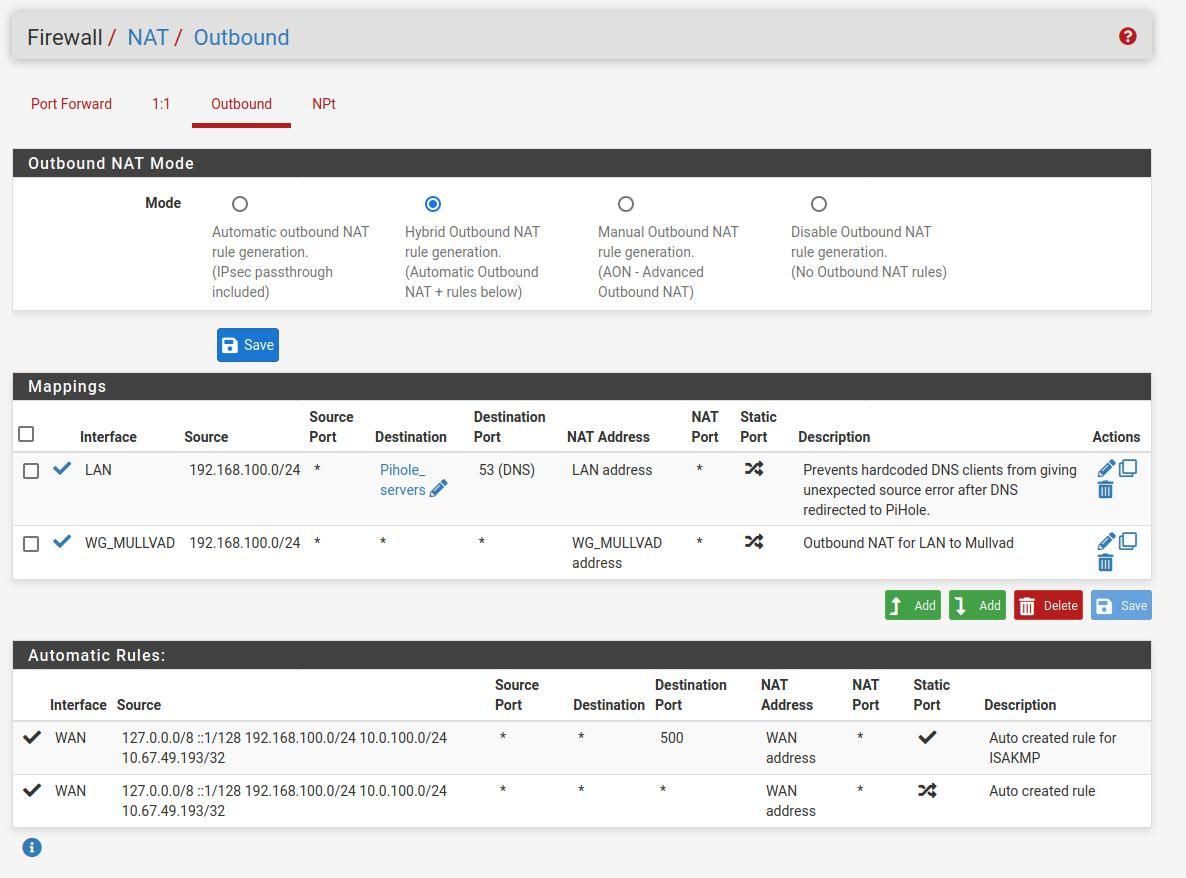
-
Also, in WG_MULLVAD interface settings "Block private networks and loopback addresses" and "Block bogon networks" are not selected.
-
Make sure your firewall rules are on the WG_MULLVAD interface tab and not the general WireGuard tab. If rules on the WireGuard tab match, then it won't have
reply-toand the reply traffic won't route back out that specific WireGuard interface. -
Ok, so I got it to work. Not sure that where the problem was exactly. Was it in misconfiguration or in my human element...
In general WireGuard tab I had rule from this guide https://docs.netgate.com/pfsense/en/latest/recipes/wireguard-ra.html. I removed all the configurations from that guide and left only configurations from this guide https://docs.netgate.com/pfsense/en/latest/recipes/wireguard-client.html. Here I noticed that netcatting the port gave connection timeout and trying to access the port using actual client worked...
So after coming to conclusion that port forward works, I started adding the remote access using already mentioned guide https://docs.netgate.com/pfsense/en/latest/recipes/wireguard-ra.html with one exception: before adding rules to general WireGuard tab as said in the guide, I created an own interface for this, and added the "Pass VPN traffic from WireGuard peers" rule under the tab with the new wg interface. So, I have no rules under general Wireguard tab now.
Now both use cases are working well. Thanks to everybody who helped and hopefully this post will help somebody with a similar issue.
PS. port forwarding ssh port was just a port forward test, as I thought ssh would be an easy service to test that port forwarding works. Going to use another service for actual port forwarding use case and use ssh over remote access.