Cisco AVPair ACL from RADIUS to OpenVPN on 2.5.0
-
Hello, guys! Please help me to understand what I'm doing wrong.
I have tested Cisco AVPair ACL pushed from radius server to pfsense per user session - everything works as expected on 2.4.5-p1 with limitation that TCP/UDP ports are not parsed to PF filter - expected behavior because in version 2.4.5-p1 there are no options to parse source and destination operators in openvpn.attributes.php file located in /etc/inc
Then I have found this article https://redmine.pfsense.org/issues/9206 where feature enhancement for parsing TCP/UDP ports described. This new parser is available for development version 2.5.0. I have found it as well on Github repo https://github.com/pfsense/pfsense/blob/master/src/etc/inc/openvpn.attributes.php
So when I tested this new file openvpn.attributes.php on version 2.5.0 (and 2.4.5 by coping this file to desired folder) it seems this parser doesn't insert required rules in pf table, and there are no temporary files for user, that should be created with parsed rules.
I use such test rules as Radius attributes (rules sanitized):
cisco-avpair = "ip:inacl#1=permit udp 10.0.0.0 0.0.0.255 host 10.0.0.1 eq 53",
cisco-avpair += "ip:inacl#2=deny ip any 10.0.0.0 0.0.0.255",
cisco-avpair += "ip:inacl#3=permit tcp 10.0.0.0 0.0.0.255 host 10.2.0.5 eq 3389",
cisco-avpair += "ip:inacl#4=deny ip any 0.0.0.0 255.255.255.255"The output on version 2.4.5p1 (with old php file) (as you can see there no ports inserted as expected)
[2.4.5-RELEASE][admin@pf.localhost]/: pfctl -a openvpn/testuser1 -s rules
pass in log quick on openvpn inet proto udp from 10.0.0.0/24 to 10.0.0.1 keep state
block drop in log quick on openvpn inet from any to 10.0.0.0/24
pass in log quick on openvpn inet proto tcp from 10.0.0.0/24 to 10.2.0.5 flags S/SA keep state
block drop in log quick on openvpn inet allThe output on version 2.5.0 (as you can see no rules was inserted)
[2.5.0-DEVELOPMENT][admin@pf.localhost]/: pfctl -a openvpn/testuser1 -s rules
pfctl: DIOCGETRULES: Invalid argumentI can't find any error logs for this (maybe I was looking in the wrong place) . Please help find an answer why this new openvpn.attributes.php on version 2.5.0 is not insert rules to pf.
Thanks!
-
Use the following syntax to check the rules:
# pfctl -a openvpn/{OPENVPNSERVERINTERFACE}_{USERNAME}_{REMOTEPORT} -srFor example:
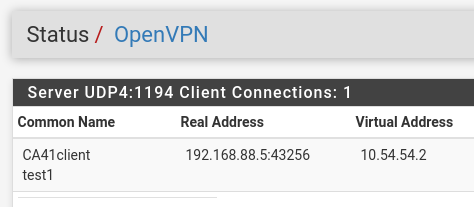
test1 - username
43256 - remote port from the Status / OpenVPN page:
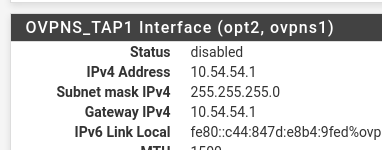
ovpns1 - interface name from the Status / Interfaces page (or from the
ifconfigoutput):
Let's try:
# pfctl -a openvpn/ovpns1_test1_43256 -sr pass in quick on ovpns1 inet proto udp from 3.3.3.3 to 7.7.7.7 port < 566 no state pass in quick on ovpns1 inet proto udp from 3.3.3.3 to 7.7.7.7 port != 899 no state