iPhone via WG tunnel - help validate my setup
-
Hello all
I'd like to share my setup connecting iPhone WG app via WG tunnel and clarify some questions. Hope it will be useful to other users.In general all is working fine:)
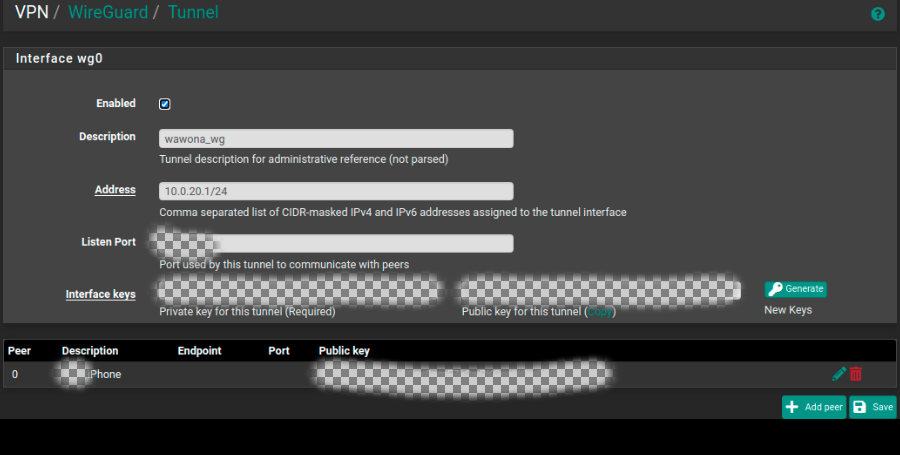
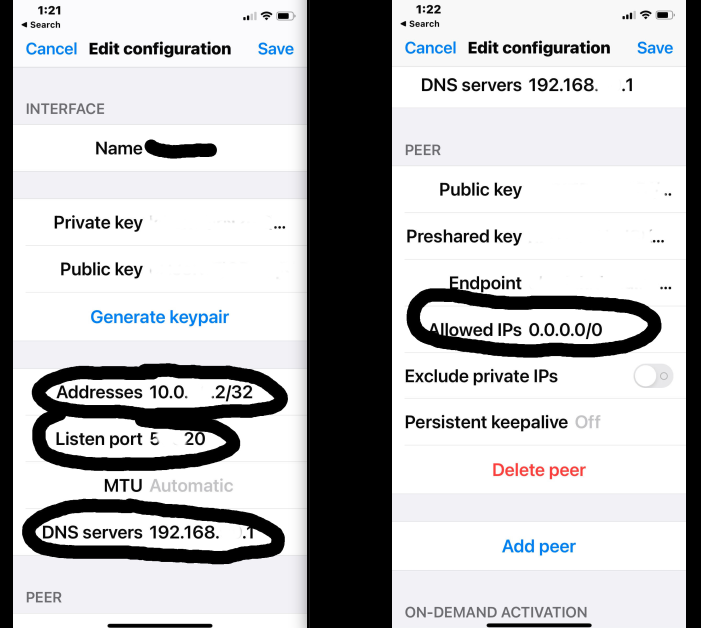
Is the Address field used correctly above?
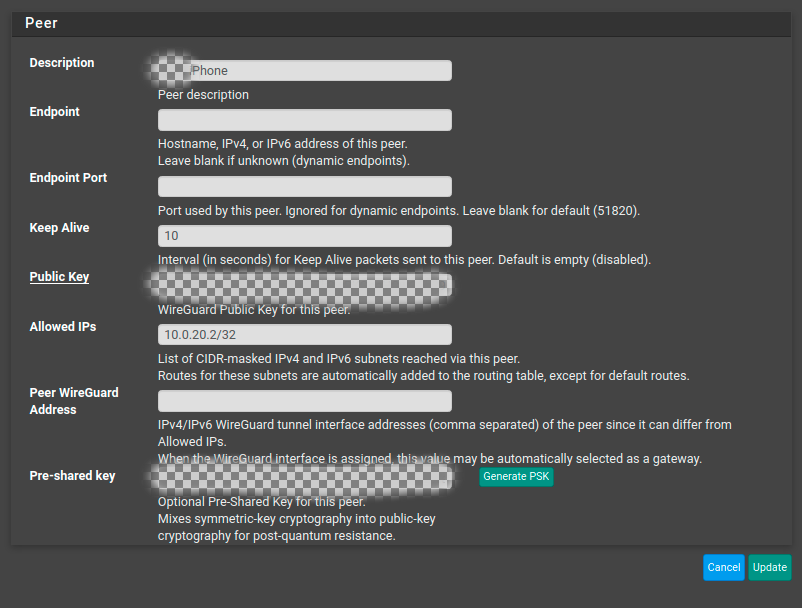
Allowed IPs above, what are other examples to this ?
Firewall rules
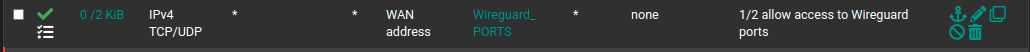
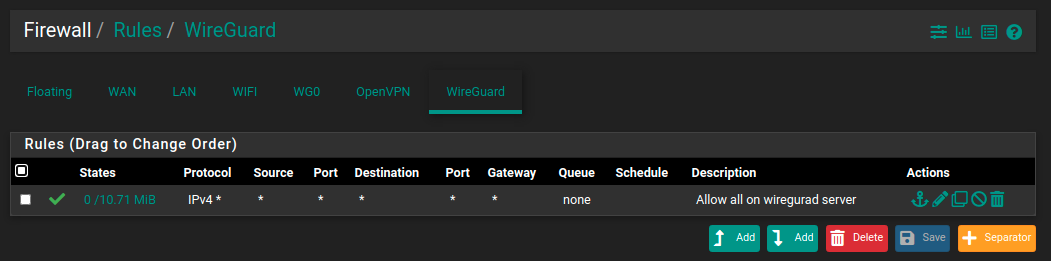
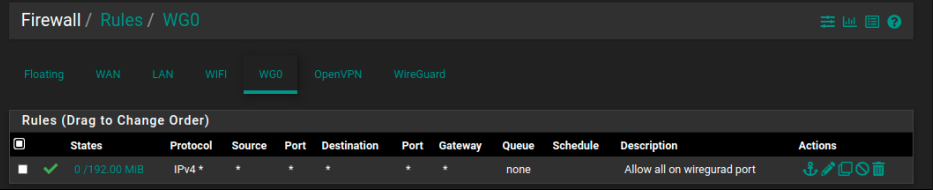
FW rules, what's the difference between WG0 and Wireguard tabs rules?
oniPhone
Please comment and critique.
Thx -
And the graph never shows any activity!?
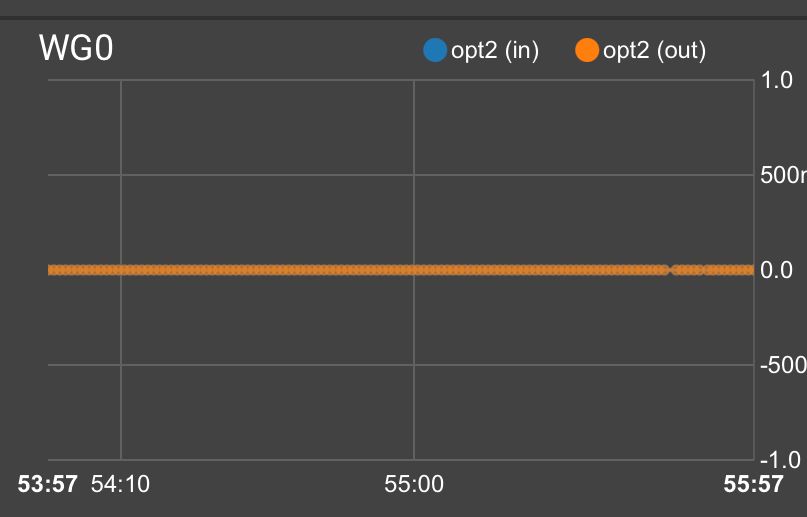
-
@chudak The lack of traffic on the graph is expected at the moment. See here: https://forum.netgate.com/topic/161060/v2-5-0-wireguard-traffic-graphs-flatline-on-zero
-
@chudak said in iPhone via WG tunnel - help validate my setup:
FW rules, what's the difference between WG0 and Wireguard tabs rules?
From the Netgate Docs:
*"Rules on the WireGuard group tab are considered first and can match traffic on any WireGuard interfaces whether or not they are assigned.
Assigned WireGuard interfaces get their own individual rule tabs and will only match traffic on that specific tunnel interface. Rules on assigned WireGuard interface tabs also get reply-to which ensures that traffic entering a specific assigned WireGuard interface exits back out the same interface. Without that, return traffic will follow the default gateway."*
Source is here: https://docs.netgate.com/pfsense/en/latest/vpn/wireguard/rules.html
-
Thx for the reply !
It's useful...Do you have any comments of actual settings ?
I think Listen Port on iPhone is not needed.
What do you use for Allowed IPs and IP Address in the peer ?
-
@chudak said in iPhone via WG tunnel - help validate my setup:
Do you have any comments of actual settings ?
Let me preface this post by saying I'm not an expert with Wireguard. I've just been playing with is since the upgrade to 2.5 a week ago. So the comments that follow are my understanding up to this point and what I think I've learned so far, and what I've done that is working up to this point .... so beware!

Regarding the IP Address in the Interface wg0 picture:
Is the Address field used correctly above?
I believe it is. I also used xxx.xxx.xxx.1/24 per the recommendations here: https://docs.netgate.com/pfsense/en/latest/recipes/wireguard-ra.html
In the second picture in your post for the Peer settings the same article as above says the following:
-
Regarding Allowed IP's:
Allowed IPs:
The tunnel IP address for this peer, from the list determined above, with a /32 CIDR mask. For example, the first peer will be 10.6.210.2/32, the second will be 10.6.210.3/32, and so on. -
Regarding Peer WireGuard Address:
Peer WireGuard Address
The IP address assigned to the client again. This field can differ from Allowed IPs in many cases, but in this type of configuration it is generally the same, as remote access clients do not usually have additional networks routed to them. Use the same subnet mask as the Tunnel address, rather than /32.
In your case I would enter 10.0.20.2/24
I think Listen Port on iPhone is not needed.
What do you use for Allowed IPs and IP Address in the peer ?
I don't use iPhone, but used the native Wireguard Android app. I left the Listening Port empty for the phone's Interface.
For the IP Address I used xxx.xxx.xxx.xxx/24. It works but I'm not sure if it should be /32 like you have it. Allowed IPs I used 0.0.0.0/0 which allow anything including out to the internet. But you could use different IPs to lock it down. For example your LAN network address if you only wanted to be able to access resources on the internal network.
-
-
@dma_pf said in iPhone via WG tunnel - help validate my setup:
rather
Cool, I am no expert myself, just trying to learn :)
Did you anything special for FW rules ?
-
@chudak said in iPhone via WG tunnel - help validate my setup:
Did you anything special for FW rules ?
I did 2 things with my firewall rules. The first was to policy route all my traffic out to the internet out through a Gateway Group that I have set up to an off site VPN provider.
The second was to lock down DNS queries to use unbound by redirecting all DNS request on ports 53 & 853 back to unbound.
-
@dma_pf said in iPhone via WG tunnel - help validate my setup:
@chudak said in iPhone via WG tunnel - help validate my setup:
Did you anything special for FW rules ?
I did 2 things with my firewall rules. The first was to policy route all my traffic out to the internet out through a Gateway Group that I have set up to an off site VPN provider.
The second was to lock down DNS queries to use unbound by redirecting all DNS request on ports 53 & 853 back to unbound.
Same as me :)
See this https://www.youtube.com/watch?v=mXG0RShQbaw
So called split tunnel makes more sense now !
I removed any rules from the Wireguard rules tab.
-
@chudak said in iPhone via WG tunnel - help validate my setup:
I removed any rules from the Wireguard rules tab.
I didn't mention that in my post, but my configuration is the same.
Thanks for the link. Watched it once but will watch it again and study it. The split tunnel thing is still a bit fuzzy in my head still. My next step is trying to lock down what access different Peers are going to need to internal resources. The link should help a lot in figuring that out.

-
When I set Allowed IPs and Peer WireGuard Address as suggested in the video to 10.0.0.6/32 I get 100% loss on WG0_XX Gateway seeing in the dashboard. Have you tried this ?
-
@chudak said in iPhone via WG tunnel - help validate my setup:
When I set Allowed IPs and Peer WireGuard Address as suggested in the video to 10.0.0.6/32 I get 100% loss on WG0_XX Gateway seeing in the dashboard. Have you tried this ?
I'm seeing the same result. In my case I have been testing this with my android phone. It's the only peer I have set up at the moment. It's using the native Wireguard app. The only time I'm seeing the 100% packet loss on the dashboard is after I get home, shut off wireguard and turn and connect it to my WiFi which is connected to pfSense.
I haven't really looked into why it's showing the loss. But I just looked at the System/Gateways log and saw that there were entries showing the packet logs on the tunnel interface. I just noticed that the gateway in pfsense had the Gateway Monitor enabled. I just shut it off to see what happens. I'll let you know.