WG - Full tunnel problematic
-
@80scyborgninja Well the nice thing is this now seems like one of two things:
- The traffic coming in on wg0 is being blocked/dropped by pfsense
- The routing of that traffic coming in wg0 is setup to send it somewhere other than WAN
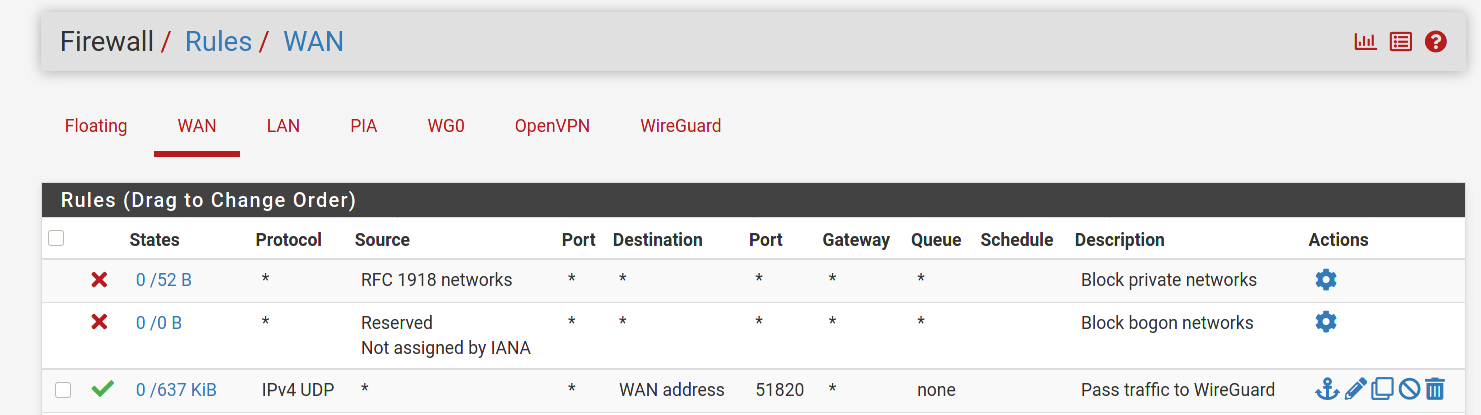
That's about all there is at this stage since nothing is going out WAN. So check your firewall rules for wg0 and if that's not it then it's a routing issue.
-
Check floating rules as well. Something is preventing those packets from going back out the wan interface. It's either firewall rules blocking it or misconfigured (policy) routing.
-
@slugger said in WG - Full tunnel problematic:
@80scyborgninja Well the nice thing is this now seems like one of two things:
- The traffic coming in on wg0 is being blocked/dropped by pfsense
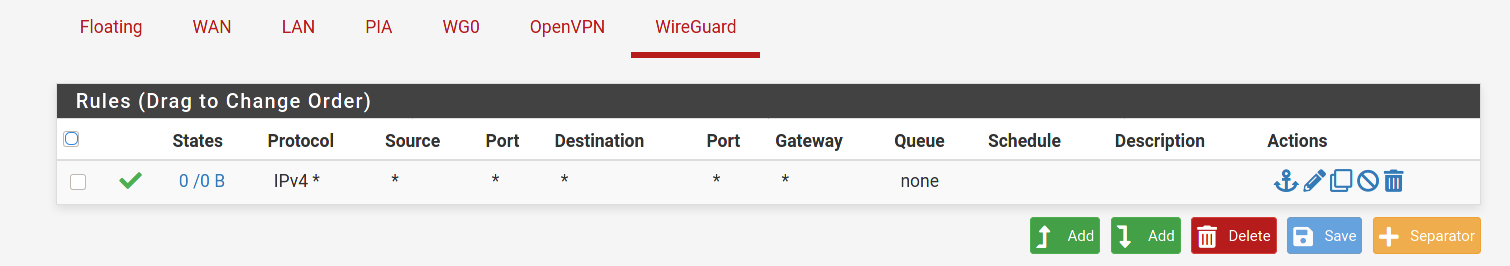
This is a guess on my part. But doesn't the any/any rule that is currently on the WireGuard tab need to be moved to the Wg0 tab? Per the docs:
Assigned WireGuard interfaces get their own individual rule tabs and will only match traffic on that specific tunnel interface. Rules on assigned WireGuard interface tabs also get reply-to which ensures that traffic entering a specific assigned WireGuard interface exits back out the same interface. Without that, return traffic will follow the default gateway.
Is it possible that the lack of a reply-to tag is messing up the routing?
-
@dma_pf Good call. I didn't notice that the any/any was on the WireGuard tab. Yeah, that's probably it. I just instinctively create interfaces for all my openvpn and wg tunnels and never use the generic tabs for rules.
-
-
@80scyborgninja said in WG - Full tunnel problematic:
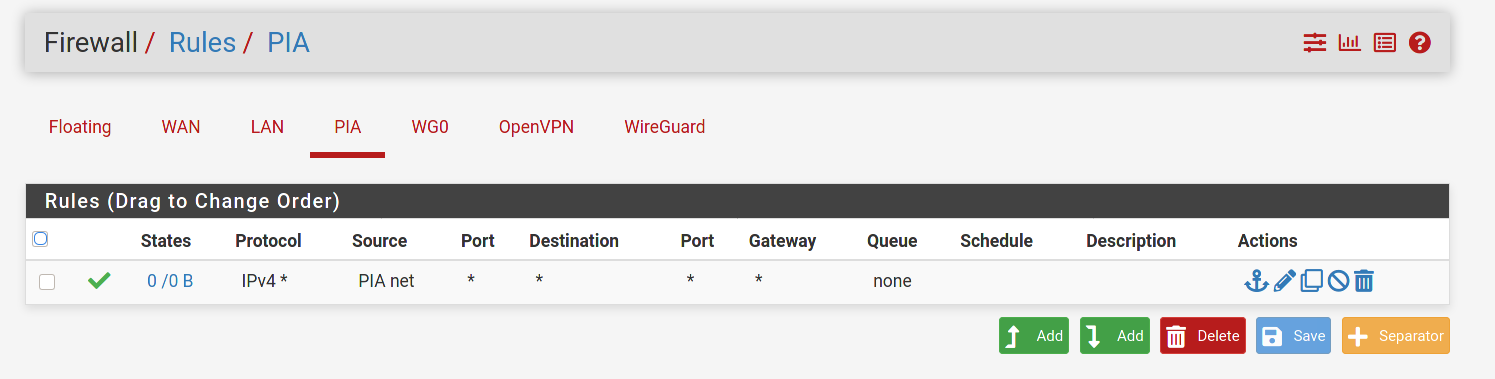
I've checked all of the rules and made adjustments as described earlier and I'm still seeing the same issue unfortunately. Could it be my OVPN PIA interface messing things up? Thanks
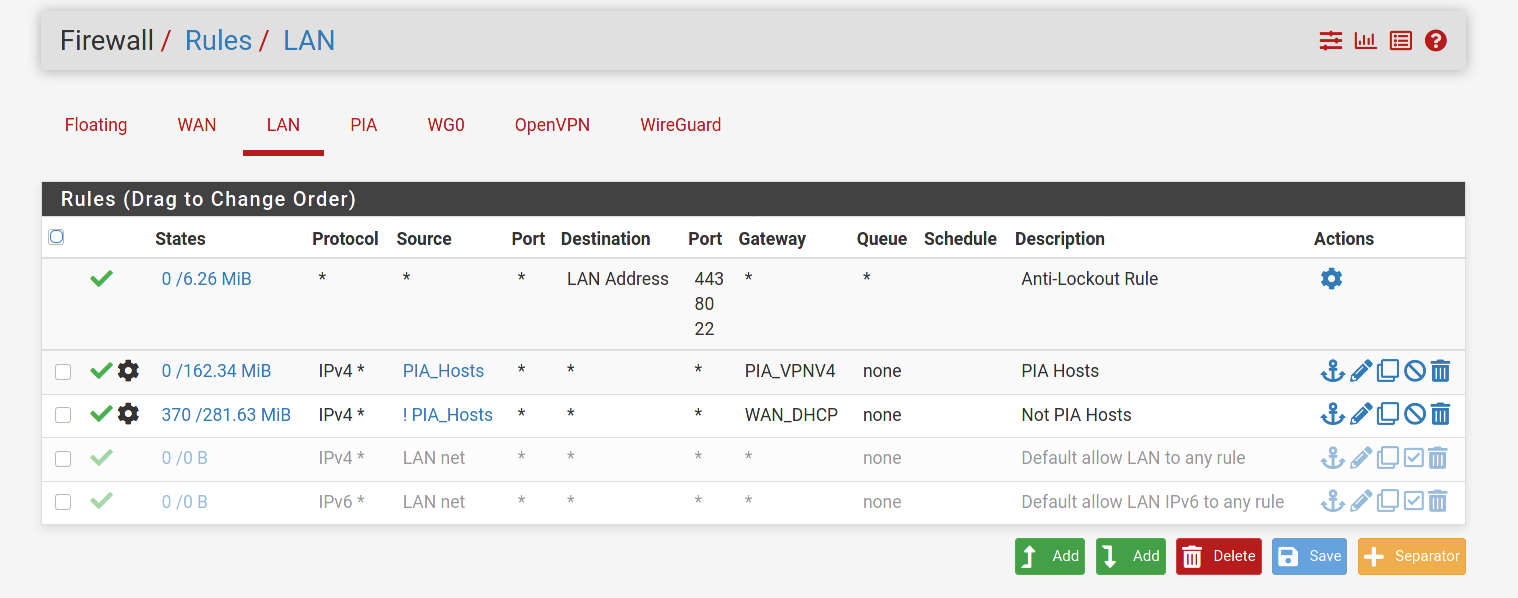
First thing I see is you do not need the PIA rule. What that rule is saying is to allow any traffic coming across from PIA into pfsense. There should never be any traffic coming across from PIA that was not initiated by your networks. All traffic initiated from your networks would automatically be allowed back in through the PIA interface because it is stateful. You would never want to allow any uninitiated traffic across the tunnel.
I'd try changing the source on the WG0 firewall rule to any for now. Enable logging and see what happens to the traffic in the firewall logs. Which interface (PIA or WAN) are you ultimately trying to route the traffic out to the internet on? What interface do you have set as the default Gateway in System/Routing?
-
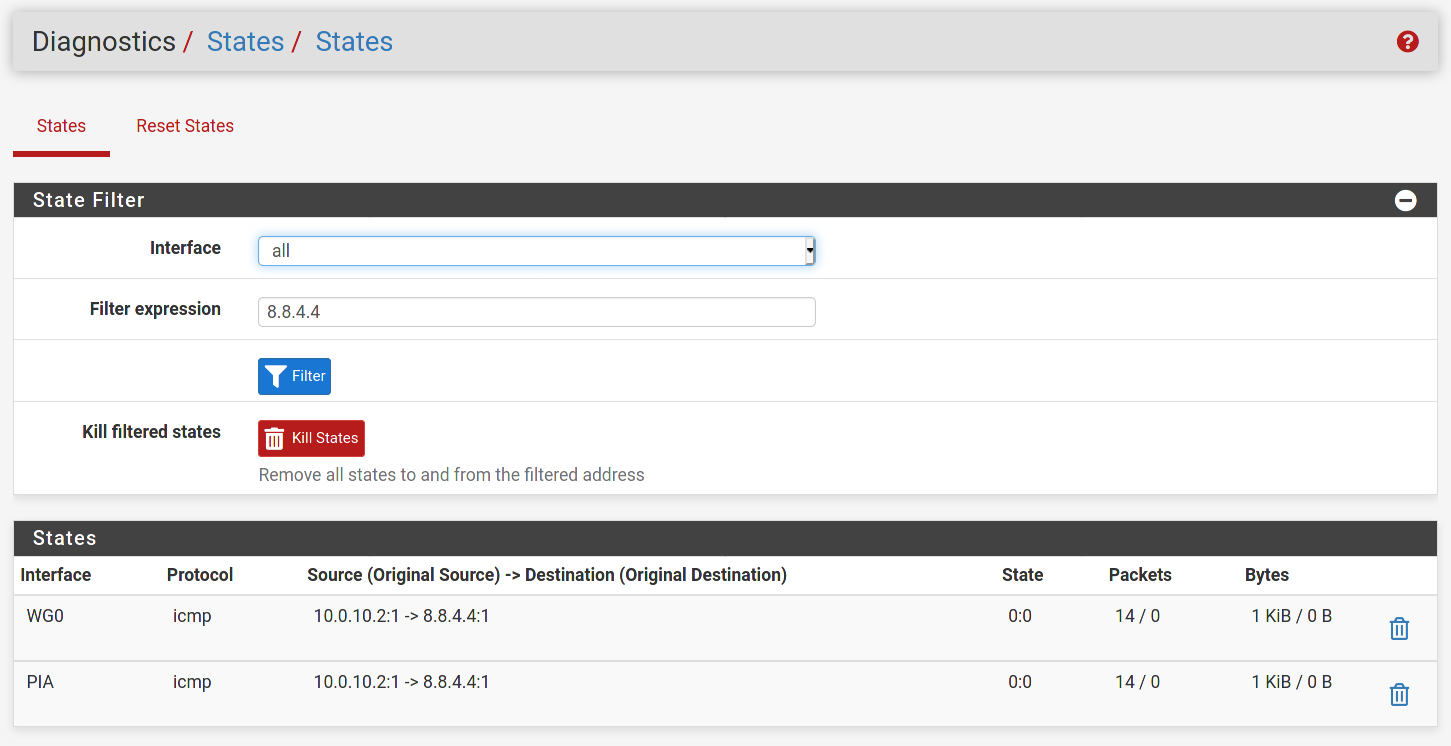
@dma_pf I removed the PIA rule as you had recommended. I also changed the source to any on the WG0 rule and enabled logging. When I ping from the WG client to
8.8.4.4I see nothing in the system firewall logs for destination8.8.4.4. I am still unable to ping from the client to internet hosts.I am trying to route traffic from my wireguard client out the WG interface to the internet using full tunnel on the client. Currently I can only hit the LAN network from my WG client.The default gateway is set to my WAN DHCP gateway. Thanks!
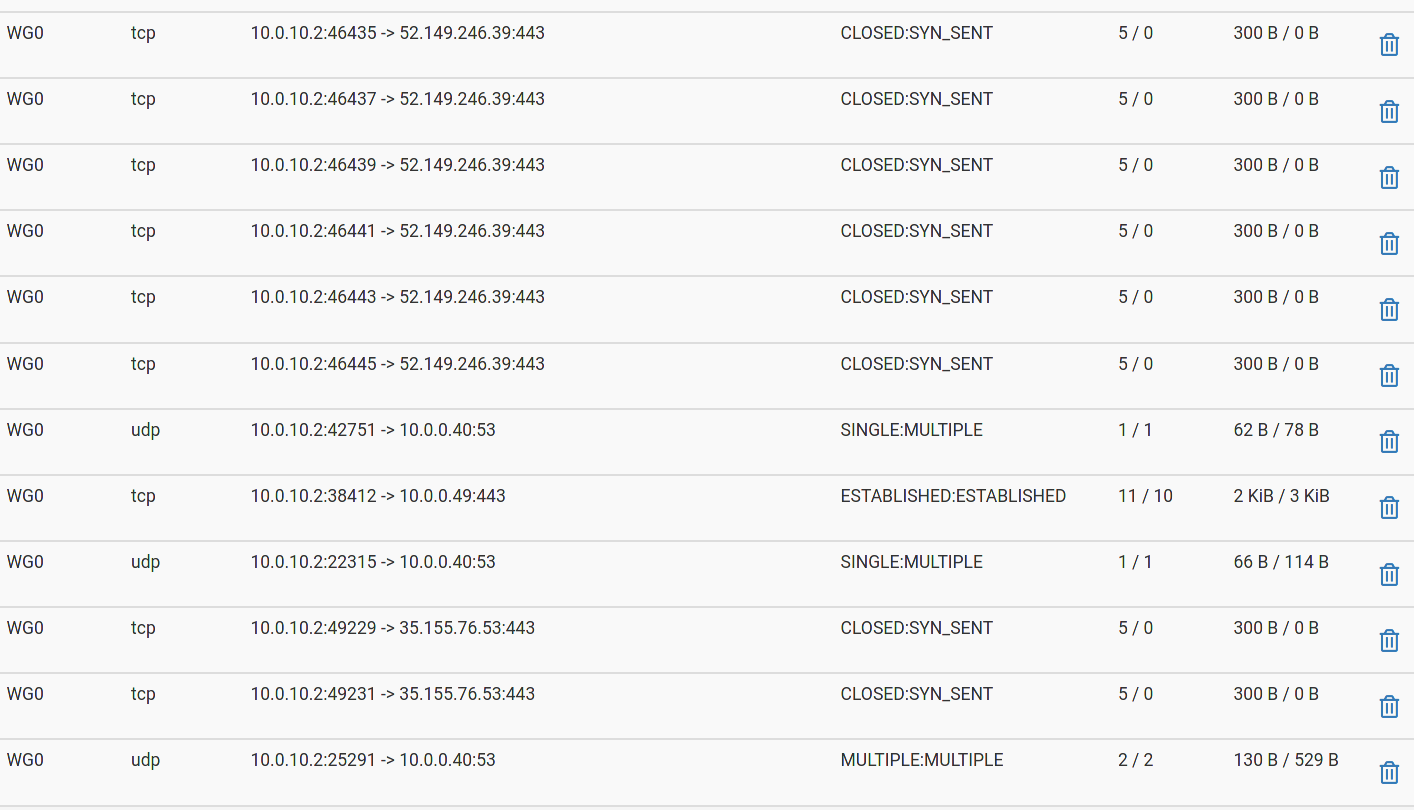
Adding a screenshot of the states as firewall logging doesn't generate for the WG0 interface.
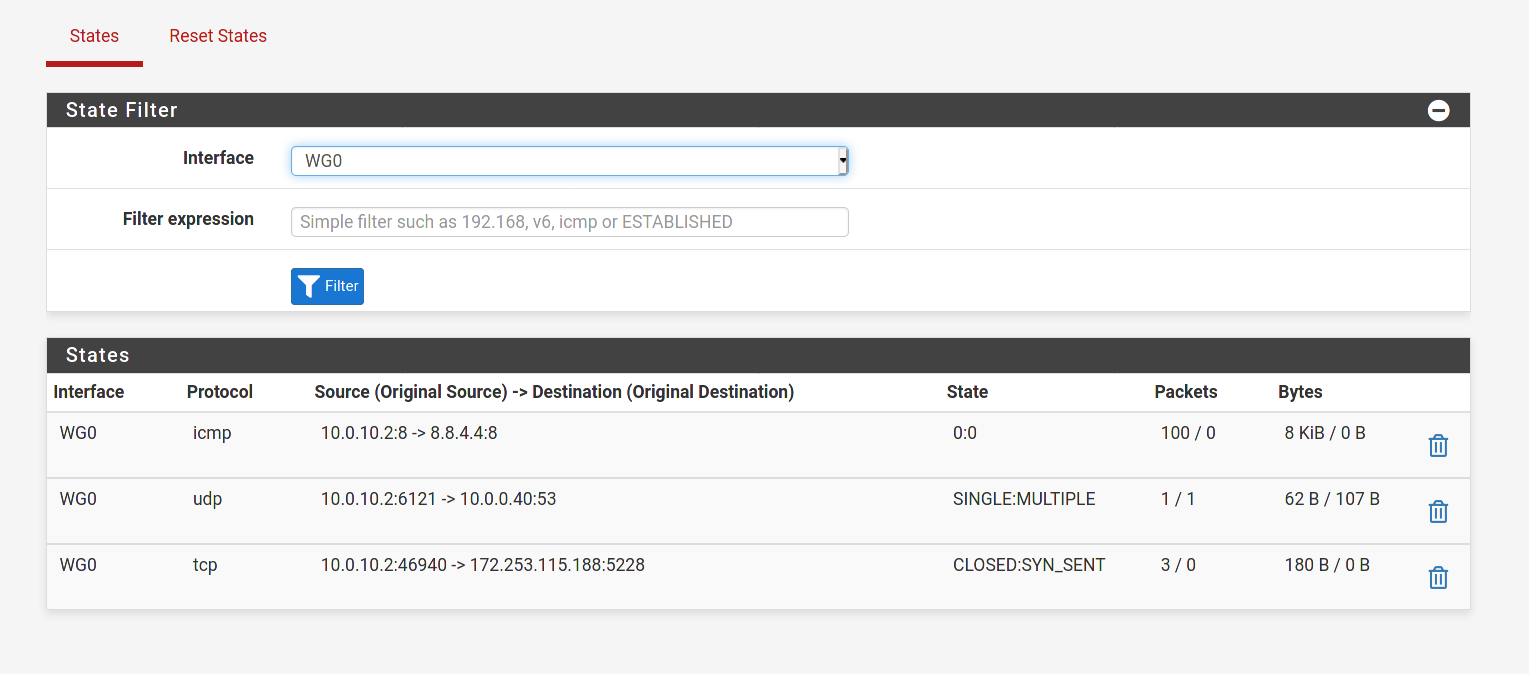
-
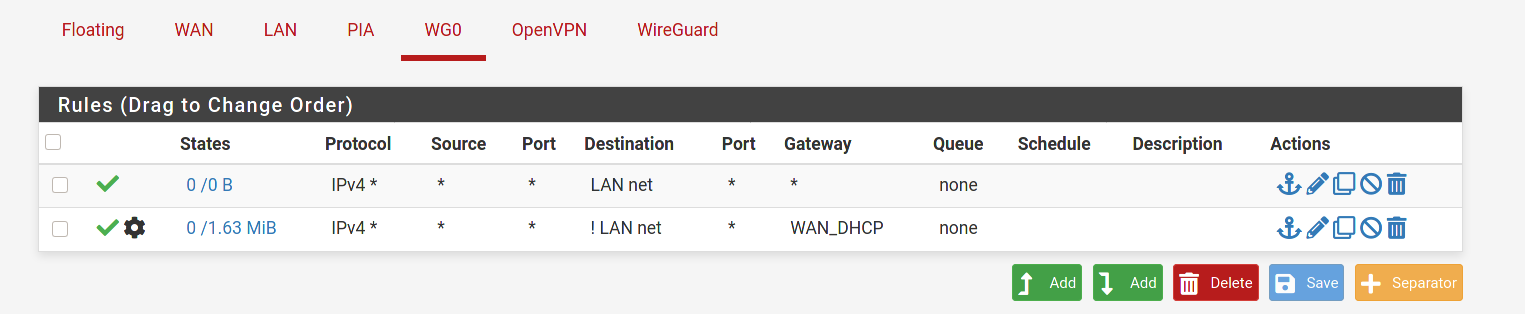
@80scyborgninja I'm seeing a couple of things that are different in your settings than mine.
-
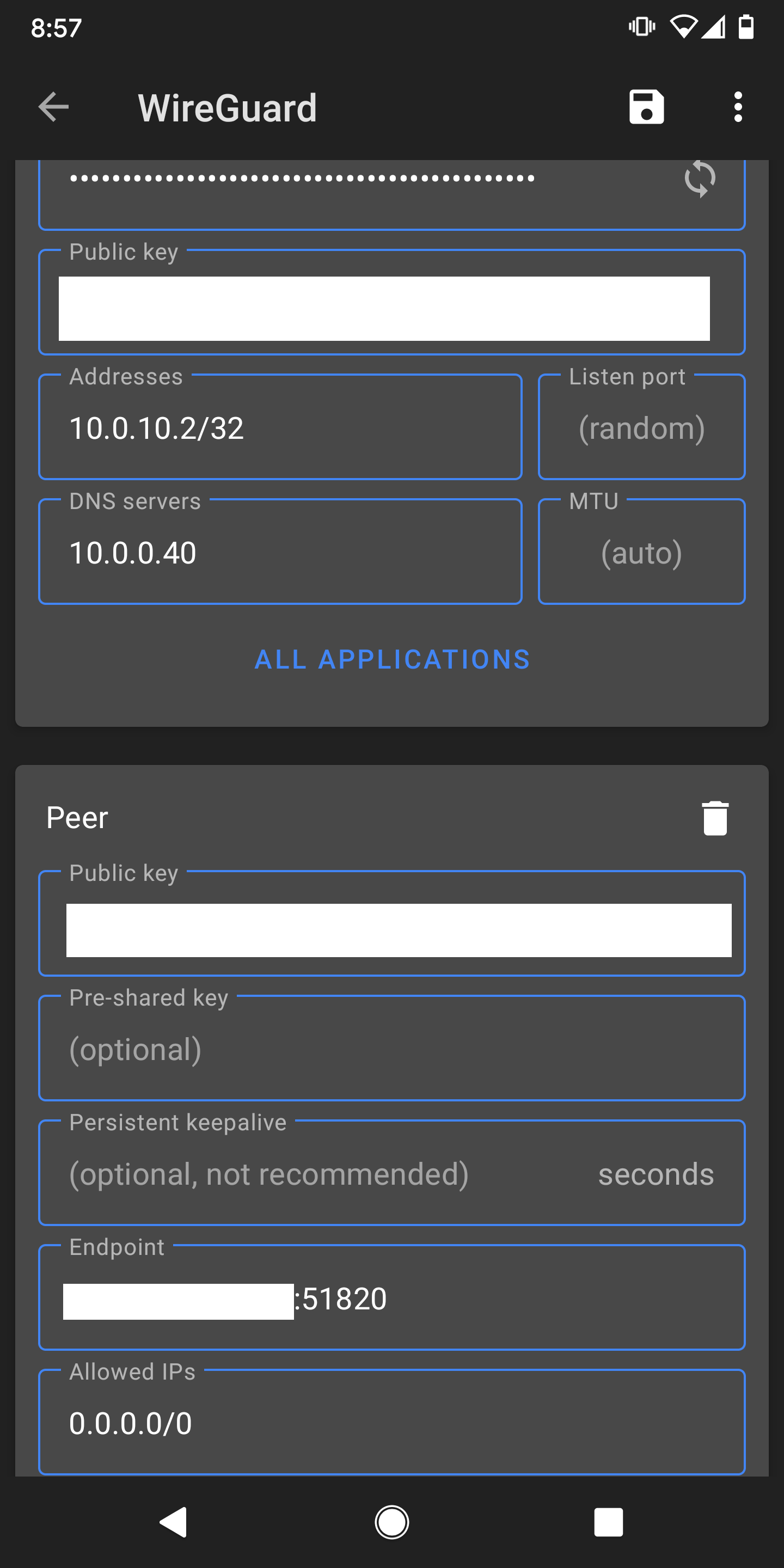
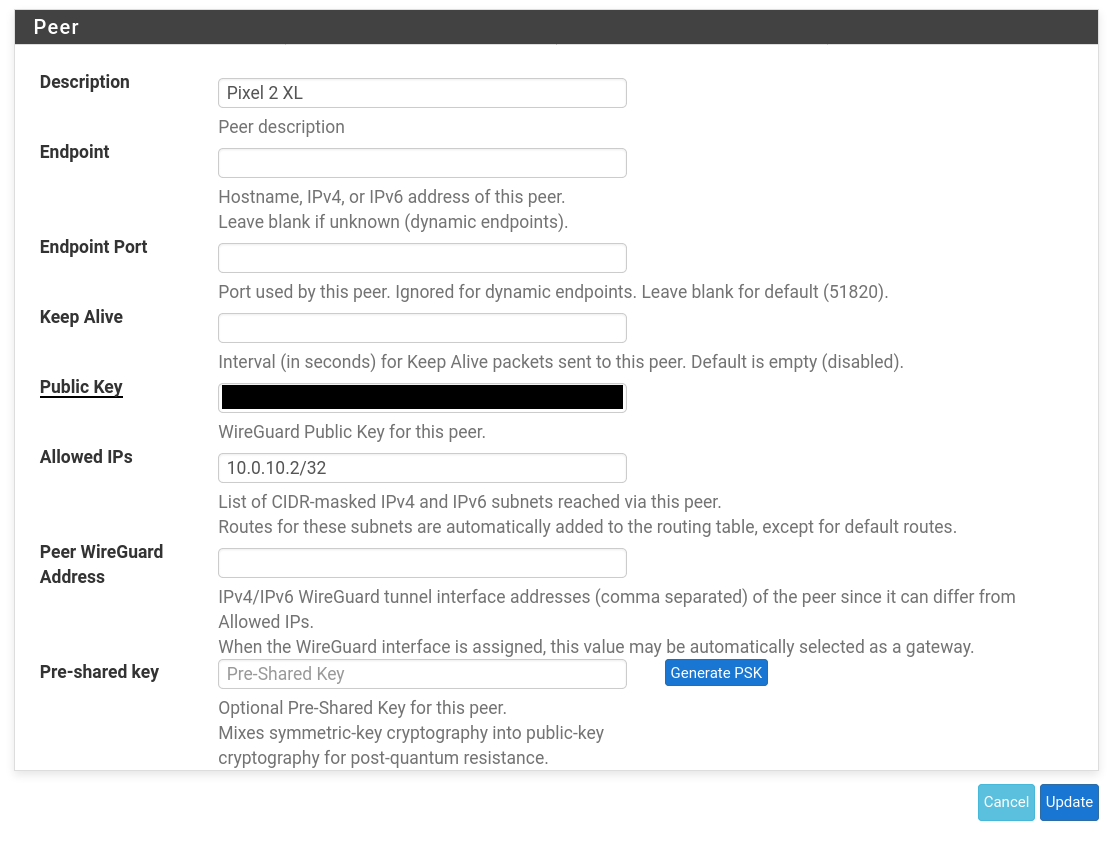
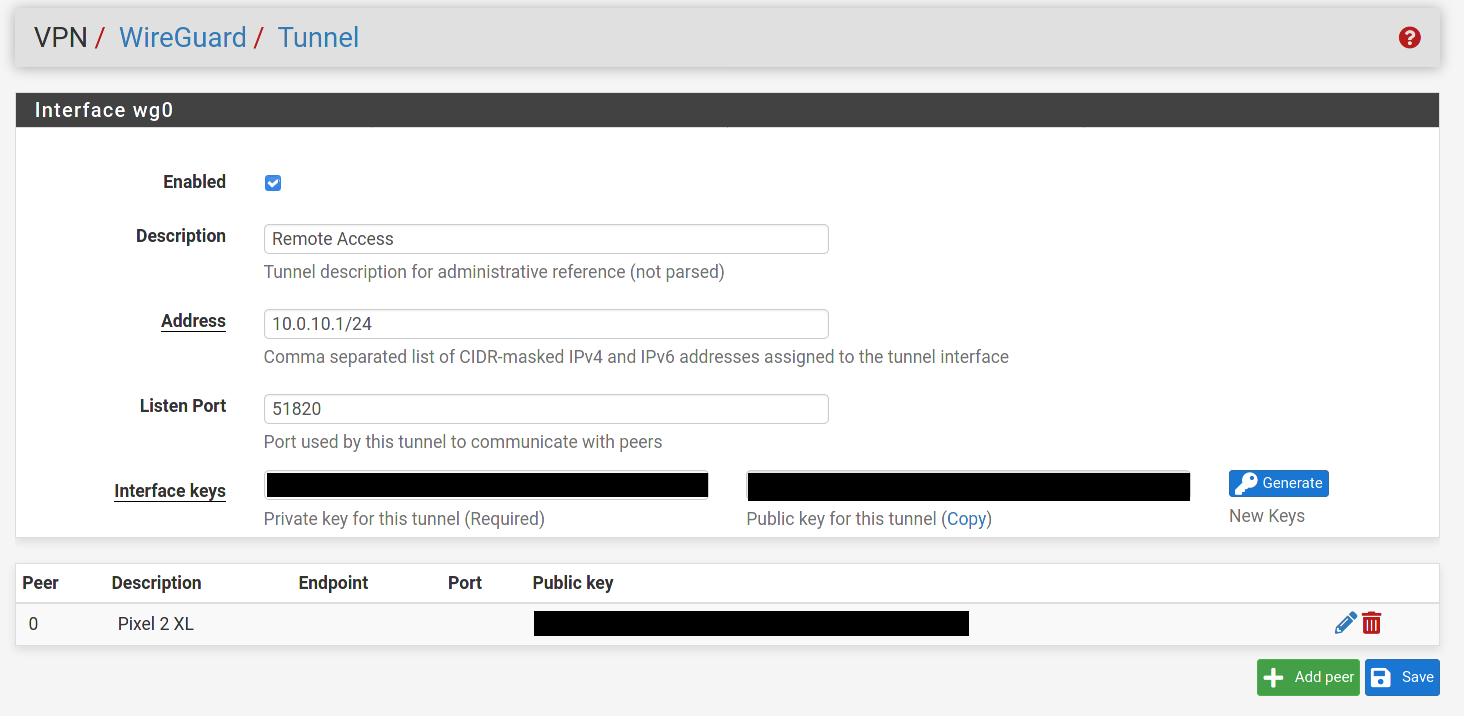
In the Peer settings for your Wg0 tunnel the "Peer Wireguard Address" is blank. I populated it with my tunnel network with the /24 mask as described here. So in your case I would try 10.0.10.2/24.
-
In the Interface settings in the phone's app I have 2 things that are different than you. The Address field is populated with a mask of /24, yours is set to/32. And I set my MTU value to match the MSS value set for the Wg0 interface in pfsense. I think @Slugger had you set it for 1420. I would make sure they match.
-
-
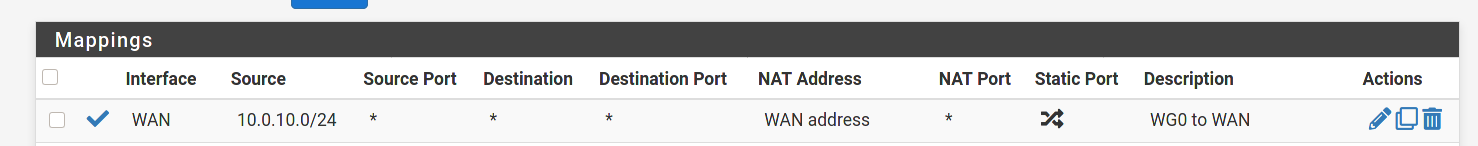
@80scyborgninja One other difference. In the Wg0 firewall rule I have a gateway defined instead of any. In my particular case it's my VPN provider. I'd suggest trying to set it to your WAN for now, as using PIA is going to require an additional NAT rule.
-
@dma_pf Ok I made all of the changes you suggested, but still the same problem. Are you able to ping out your WG interface using pfsense Diagnostics to
8.8.4.4? I can't do that and feel that others would probably be able to with a working setup. Thanks -
@80scyborgninja said in WG - Full tunnel problematic:
@dma_pf Ok I made all of the changes you suggested, but still the same problem. Are you able to ping out your WG interface using pfsense Diagnostics to
8.8.4.4? I can't do that and feel that others would probably be able to with a working setup. ThanksYes, i just tried it and it works perfectly.
-
@dma_pf damn ok I'll try and trouble shoot that a bit. Real weird. Thanks
-
@dma_pf Hmm oddly, my WG gateway IP is the IP of my WG peer and I can't seem to change it as it is set to dynamic. Not sure if that is expected, but would explain all of my issues I think. Thanks

-
@80scyborgninja said in WG - Full tunnel problematic:
@dma_pf Hmm oddly, my WG gateway IP is the IP of my WG peer and I can't seem to change it as it is set to dynamic. Not sure if that is expected, but would explain all of my issues I think. Thanks

Mine looks the same way.
Not sure why it would show the Peer address instead of 10.0.9.1. Nonetheless, it's working for me.
-
-
@80scyborgninja I'm glad you stumbled on a solution that worked!
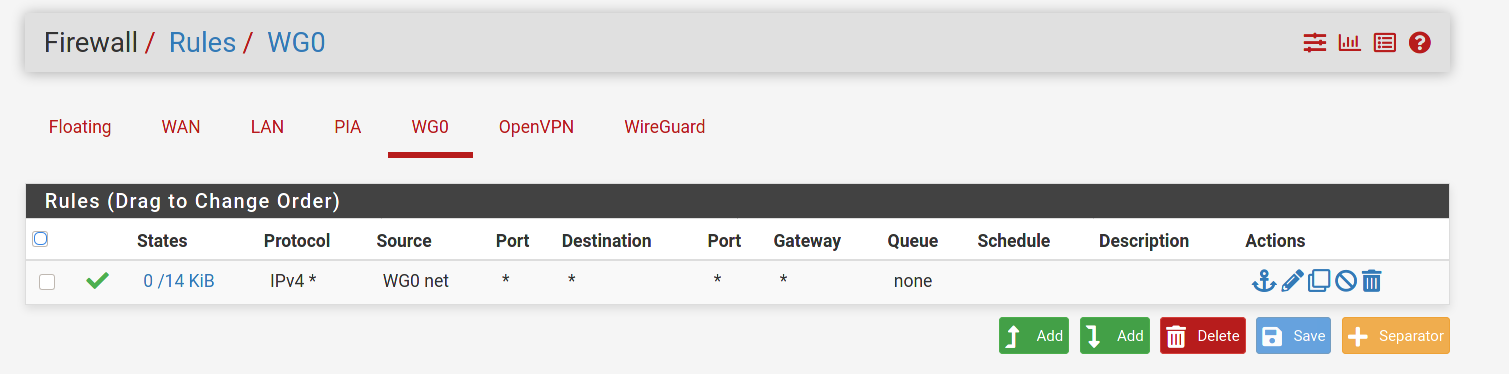
I thought that we had tried setting a rule on Wg0 like this before:
Protocol: IPv4*, Source, Source Port, Destination, Destination Port: *
If we did I'm surprised it did not work. Did you make any other changes? Did you reboot pfsense recently and had not done that before?
-
@dma_pf Yep, I did try that rule and cleared states after, also rebooted after each rule for testing. Oddly the only way I could get anything to work was with rules I have screenshoted above. Definitely very strange.
-
@80scyborgninja said in WG - Full tunnel problematic:
Definitely very strange.
Definitely a mystery here
 , but I am glad you got it working. And thanks for the feedback.
, but I am glad you got it working. And thanks for the feedback.