Phone not accessing the internet after rule to avoid the router VPN
-
@dma_pf The phone can connect to the VPN all the ways except when that rule is active. It can connect to the VPN through the celular network, it can connecct to the VPN through the WIFI (without the rule active) which I am guessing it is double VPN'ing (have not traceroute'd it). The only time the phone can not connect is when the rule is active (and I know it gets triggered because I have added the rule to the log and I see it in the logs).
This is the screenshot of the rules of the LAN (there are no more rules after what you see in the screenshot):

LAN is a bridge than bridges ELAN (Ethernet LAN) and WLAN (Wifi LAN), the other I think are obvious, but I will answer and try anything. Thanks for your time.
-
@dicmo try inverting these 2 rules
then on this rule
Change the Source to the IP Address of the phone and change the destination to Any. Let me know if that works.Also, what is in the alias Local_Networks?
-
Local_Networks is 10.10.10.0/24 (ips of the LAN) and 192.168.1.0/24 (these are the ips of the ISP router and the NIC that connects the pfSense to the ISP router). The real important addresses are 10.10.10.0/24.
Not sure how making those changes would help. Can you explain?
EDIT:
I think it will help if I describe the network a bit.
Internet --- ISP Router (192.168.1.1) ----- (192.168.1.102) pfSense router (10.10.10.1) ---- LAN network with phone @10.10.10.200 .
Hope that helps. Anything else please ask.
-
@dicmo said in Phone not accessing the internet after rule to avoid the router VPN:
Not sure how making those changes would help. Can you explain?
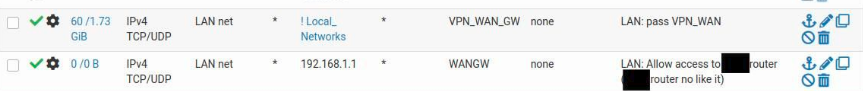
Sure. If you look at this rule

It's saying that any Traffic on the LAN interface that is coming from a LAN Address (10.10.10.0/24) and is headed to any address other than 192.168.1.0/24 or 10.10.10.0/24 should be allowed into the firewall and routed out the VPN. This would also include the phone (10.10.10.200) as it is part of the LAN (10.10.10.0/24). So when your phone hits that rule it will always policy route out to the VPN gateway if the destination is anything other than a 10.10.10.0/24 or 192.168.1.0/24 address.
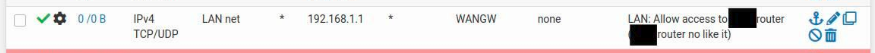
Note that on this rule (below) there are 0 States Open and 0 Traffic hitting the rule (0/0 B) That clearly shows that nothing is hitting the rule.
Using the same logic as we did on the previous rule, the rule above is saying that any Traffic on the LAN interface that is coming form a LAN Address (10.10.10.0/24) and is headed only to 192.168.1.1 should be allowed into the firewall and routed out the WAN. Your phone would therefore never get to the internet (including to the VPN endpoint) using this rule as any internet address (Destination) would be something other than 192.168.1.1. In pfSense rules are evaluated from the top down. Once a rule applies that's it, nothing below will be evaluated. So, by inverting the rules, and only having the phone's IP address as the Source in this rule, and Any as the Destination, only your phone will go out the WAN and nothing else. Then the other rule will policy route everything else out the VPN.
@dicmo said in Phone not accessing the internet after rule to avoid the router VPN:
192.168.1.0/24 (these are the ips of the ISP router and the NIC that connects the pfSense to the ISP router)
I'm curious, why does the ISP router assign a 192.168.1.0/24 address? Can't it be put in bridge mode so the WAN address of pfSense is the IP assigned by your ISP?
-
@dma_pf said in Phone not accessing the internet after rule to avoid the router VPN:
I'm curious, why does the ISP router assign a 192.168.1.0/24 address? Can't it be put in bridge mode so the WAN address of pfSense is the IP assigned by your ISP?
I have to put the ISP router in bridge mode, I just have not gotten around to. I am still setting up the whole system. But you are right, it should be.
As for the rules, I think you misread. The rule that is supposed to send the traffic from the phone to the WAN instead of the VPN_WAN is disabled in the screenshot I posted and it is before the rule that sends all the internet traffic to the VPN_WAN. If you check, the disabled rule says source PhoneStaticIP, destination !Local_Networks and the description says LAN: Phone avoid double VPN. I have it disabled because otherwise the phone can not access the Internet when connected to the wifi. But if I activated, it gets triggered when the phone tries to connect to the internet.
The last rule before the default reject rules, the one you are asking me to put on top, only redirects the traffic from LAN to the ISP router (destination 192.168.1.1, probably should make it an alias) through the WAN so a LAN can access the ISP router, although my ISP router does not like it and refuses the connection, my guess is because it does not come from the same local address as the ISP router.
-
@dicmo said in Phone not accessing the internet after rule to avoid the router VPN:
As for the rules, I think you misread
On brother! I did miss that disabled rule. Sorry about that. Nonetheless, that disable rule should accomplish what I outlined above. I'm wondering if this could be a NAT issue, especially since pfsense is sending packets out the WAN with RFC1918. Mind posting your NAT rules?
-
@dma_pf said in Phone not accessing the internet after rule to avoid the router VPN:
@dicmo said in Phone not accessing the internet after rule to avoid the router VPN:
I'm wondering if this could be a NAT issue, especially since pfsense is sending packets out the WAN with RFC1918. Mind posting your NAT rules?
Actually yeah, the rule to access the ISP router should work too as the NAT should be changing the address and the ISP router should be seeing the 192.168.1.102 address. I assume it was the ISP router rejecting it, but it seems that both rules that have the WAN as gateway are getting triggered but they do not get a response back or something else, the connection through there just does not work. So it is probable the router rule and the phone rule both suffer from the same problem.
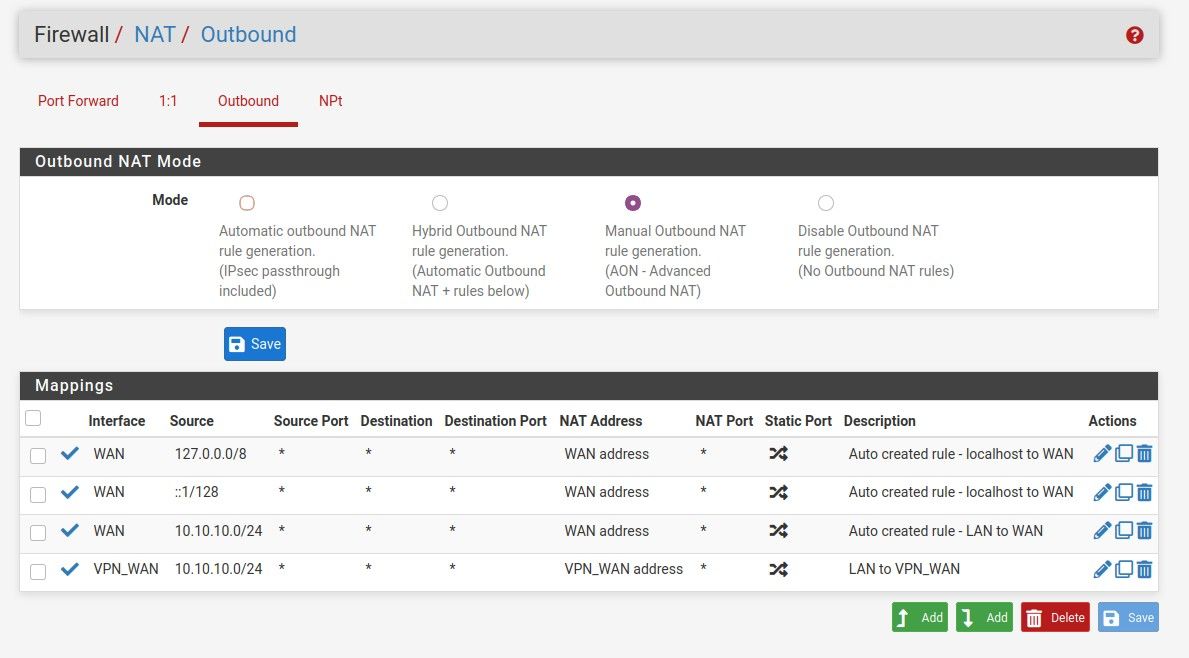
This is the NAT:
-
@dicmo I really think this is a Double NAT issue. pfSense is NATing traffic that is then being NATed again by the router. Somewhere in that process the routing is getting lost. Unfortunately, I have no experience working on that issue so my help is limited here.
I think the easiest thing to do is set the router to bridge mode....probably just the flick a switch. This will put all of the routing on pfsense which is certain to be more robust than on a commercial router. At that point your NAT rules should work.
If that's not an option you might want to check the pfSense docs here. There's also a pfSense Hangout that might be useful here. Then of course there's always searching around these forums and google for "Double NAT".
I'm sorry I can't shed more light on fixing the issue but please let me know how you resolve it. I'm really curious to know what fixes the issue.
-
@dma_pf hey, thanks for taking the time to look into this. At least, it gives me confidence that my rules make some sense. Since I am new to pfSense I was not so sure.
I will set the IPS Router in bridge mode in the next days, as I am busy right now trying to fix a couple other issues in the new system, as setting it in bridge mode was in the TODO list anyways. When I do I will report back. Hopefully it solves the issue, but what makes me not very hopeful is that accessing the ISP router was not working either and that is only one NAT. We will see. Again, thanks for your time.
-
@dicmo said in Phone not accessing the internet after rule to avoid the router VPN:
Hopefully it solves the issue, but what makes me not very hopeful is that accessing the ISP router was not working either and that is only one NAT.
Double NAT to the web is a different issue than the router issue. Here's how to access the router correctly:
https://docs.netgate.com/pfsense/en/latest/recipes/modem-access.html
-
@dma_pf ok, so I am ready to set access to the router and set the router in bridge mode, but I have some doubts that I was hoping you could resolve before I do.
First, I have read the instructions of the last link you have posted, but the issue is that I do not have a PPPOE interface. The interface talking with the ISP router is defined as a normal WAN. So I can not create another interface to do the NAT to the ISP router like the link says.
Also, I am wondering if I need to set up a PPPOE interfacce to put the router in bridge mode. I have been reading quite a bit on the internet and I can not fully undestand how the bridge mode works. For what I understand the ISP modem will keep having the 192.168.1.1 address (some people say there is a need to change it, others do not), and the pfsense interface facing the ISP router has to be listening for the DHCP server of the ISP (not from the ISP router in my house, from the ISP server) to assign an internet IP just like it would assign to the ISP router when not in bridge mode. Set up this way, the ISP router will just pass all the traffic with the internet IP's from the ISP server to the pfSense router, and only will react when he sees a packet for 192.168.1.1.
Can you please correct the misunderstandings that I might have and clarify the process? Thank you.
-
@dicmo said in Phone not accessing the internet after rule to avoid the router VPN:
The interface talking with the ISP router is defined as a normal WAN. So I can not create another interface to do the NAT to the ISP router like the link says.
Sorry about that. You'll have to create a vLAN first, then assign that vLAN to the same interface as the WAN. Then you can set the NAT Rules. Like this:
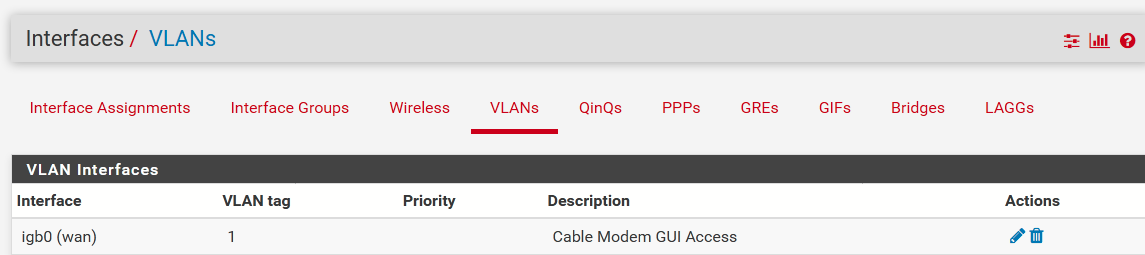

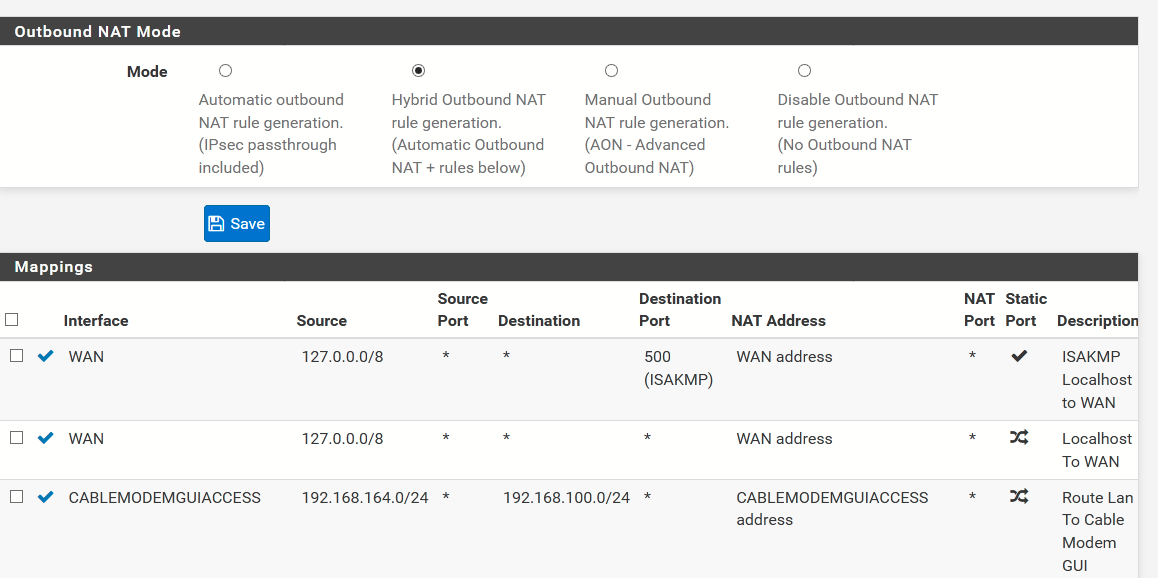
That should let you access the router's GUI.
@dicmo said in Phone not accessing the internet after rule to avoid the router VPN:
For what I understand the ISP modem will keep having the 192.168.1.1 address (some people say there is a need to change it, others do not), and the pfsense interface facing the ISP router has to be listening for the DHCP server of the ISP (not from the ISP router in my house, from the ISP server) to assign an internet IP just like it would assign to the ISP router when not in bridge mode. Set up this way, the ISP router will just pass all the traffic with the internet IP's from the ISP server to the pfSense router, and only will react when he sees a packet for
The way the router is working now is like this:
ISP -> assigns WAN IP Address To Router - > Router uses DCHP to assign IP addresses to clients - Pfsense (acting as a client to the router) receives an IP (not the WAN IP) from the router 's DHCP server and binds it to the WAN Interface. Pfsense then uses it's DHCP to assign a different IP addresses to it's clients.
In bridge mode the router works like this:
ISP -> assigns WAN IP Address To Router - > Router passes along the WAN IP Address to pfsense who then binds it to the WAN Interface. Pfsense then uses it's DHCP to assign a different IP address to it's clients.
As you can see above, in bridge mode the router is passive. It's just letting the ISP forward the WAN IP address to pfsense which then does all of the DHCP assignments and routing for the internal works. The internal networks then get routed out the pfsense WAN to the the router which passively (No NAT) sends it out to the ISP.
Depending on the protocol used by the ISP, routers can connect to the ISP in different ways. In bridge mode you will have to match that protocol in the WAN interface settings in pfsense by selecting the correct "IPv4 Configuration Type":

-
@dma_pf Ok, great. Thanks again.
One thing that is confusing me is, in bridge mode, if the ISP Router does not have its own IP, how can you access its web configuration page?
-
@dicmo said in Phone not accessing the internet after rule to avoid the router VPN:
One thing that is confusing me is, in bridge mode, if the ISP Router does not have its own IP, how can you access its web configuration page?
The router should have a default IP Address for the GUI from the manufacturer. If the ISP provides the router you should be able to find that info on the ISP's website. If not try googling for it. If it's not provided by the ISP google the make and model of the router.
If you want to take a wild stab at it try 192.168.1.1 ... it's handing out 192.168.1.0/24 addresses so it most likely in that network (192.168.1.1 to 192.168.1.254)
-
@dma_pf No, that is not the question. I can access the ISP router webconfigurator at 192.168.1.1 right now (if I am on its network obviously) and if I remember correctly the configuration allows to select the ISP router IP.
My doubt comes from this: when you put the router in bridge mode, you explain that the ISP gives an Internet IP to the ISP router and the router then passes that IP to the pfSense router. So the WAN interface of the pfSense has that IP. In that situation, which IP will I be able to use to access the webconfigurator of the ISP router?
-
@dicmo said in Phone not accessing the internet after rule to avoid the router VPN:
My doubt comes from this: when you put the router in bridge mode, you explain that the ISP gives an Internet IP to the ISP router and the router then passes that IP to the pfSense router. So the WAN interface of the pfSense has that IP. In that situation, which IP will I be able to use to access the webconfigurator of the ISP router?
As I mentioned in my previous post, you'll access the router's GUI by the default IP address of the router provided by the manufacturer. Now, that assumes that the router is in it's default state. If you've changed that IP network yourself and have selected to use the 192.168.1.0/24 network (and it is not the default network) then I'm not quite sure. At that point it would be a matter of whether or not the router will revert back to the default GUI IP address, or if the one you have selected (192.168.1.1) will "stick", when you select bridge mode.
In either case, you'll need to go through the steps I posted above to add another interface to have access to the GUI. The only difference being which network you'll be using for the static IP address in the Interface's settings in pfsense. (see bottom of picture)

The static IPv4 IP address has to be in the same network as the GUI network, but not the same IP address as the GUI. So for example, if the GUI is 192.168.1.1, the static needs to be between 192.168.1.2 to 168.168.1.254 (your pick!). -
Is this standard on cablemodems to use VLAN 1 for their management interface when in bridge mode?
On my Telus modem, I can set bridge mode on port 1 and the remaining three LAN ports are normal. I just connect one of those to my managed switch on an untagged port separate VLAN to access.
Previous Shaw modems I had when I enabled Bridge mode I think I had to access the default subnet somehow during bootup, reset the modem using pin, or contact Shaw to take it out.
-
@dma_pf Now that the problem with the connection going down is solved, I have come back to this. I have managed to put the ISProuter in bridge mode and now the pfSense router is connecting to the ISP directly.
It is expected, but I feel the connection is more snapy, there is less lag between asking for a webpage and it opening. Not having a second NAT from a underpower router will do that I guess.
Also, you were completely right and now the phone is connecting fine, the firewall rule to have the static IP of my phone routed through the WAN instead of the VPN_WAN is working. It was indeed the double NAT that was giving trouble as you suggested.
Now that the ISP Router firewall is down I am getting a lot of activity blocked by the pfSense firewall in the WAN interface, but that was to be expected too. Most of it from China from what I have sampled, also to be expected.
In case there is another "noobie" that it is reading, what I had to do after I had set up the ISPRouter in bridge mode is in pfSense go to Status->Interfaces, then in WAN release the DHCP lease (this is the one that I had with the ISPRouter, usually address 192.168.X.X) and then adquire the lease again (now with the ISP directly, the IP is completely different, not 192.X.X.X). This worked, but pfSense was confused about the routing, it was giving me error 65, which websearching told me it was lack of routing. So I went to System -> Routing, I changed the "Default gateway IPv4" from Automatic to WAN_DHCP, Save and Apply. Apparently that made pfSense get a sense of the routing again and everything was working fine. I switched it back to automatic, save and apply, and everything was working well still. So apparently pfSense needed a trigger to reshape the routing or something.
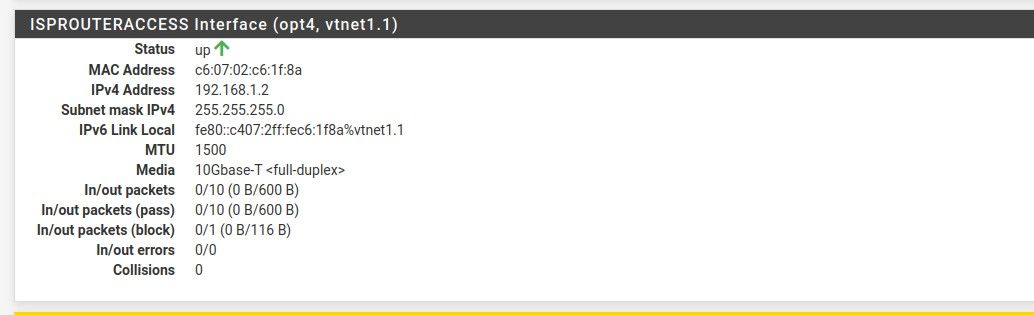
Now, the only issue is that I can still not access the ISPRouter from behind the pfSense Router. It is not the biggest deal, since I do not need to touch it anymore and I can access it by connecting a ethernet cable to it directly from the laptop, but I would like to have access from the pfSense LAN network. I think I followed @dma_pf advice but still not connecting. Here is the relevant configuration (feel free to ask for anything):
I created the VLAN interface and gave it a static address in the range of the ISPRouter address:

Then I created the rule in the NAT:

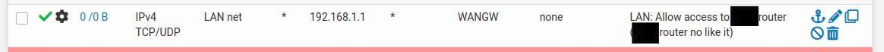
The problem with this is that the firewall was blocking access to 192.168.1.1 (as it should by the rules I had), so I created a new rule to allow access (the last rule before the default reject rules):

With all of this the connection is still not going through. It times out. For the record, the IP of the ISP Router is included in the Local_Network alias, so the two previous rules that deny it do not affect it. More evidence to this is that when the last pass rule was not present, the traffic to the ISPRouterHost was being catch by the Default reject rule, so the other rules were not being triggered (as expected). Plus, I added the rule to the logs and it is getting triggered when trying to access the ISPRouter IP.
Do I need to create a gateway and set it up in the firewall rule or with the NAT rule should be enough? I have not been able to find anything relevant in the logs, what can I do to debug and see what is happening?
-
@dicmo said in Phone not accessing the internet after rule to avoid the router VPN:
Do I need to create a gateway and set it up in the firewall rule or with the NAT rule should be enough? I have not been able to find anything relevant in the logs, what can I do to debug and see what is happening?
You don't have to set up a new gateway. But you do need to let the new ISPROUTERACCESS interface route out of pfsense to get to the router. Move this rule to the ISPROUTERACCESS tab in Firewall/Rules and change "LAN net" to "ANY" :
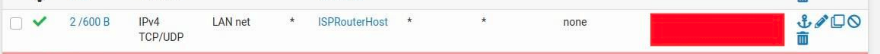
-
@dma_pf Still not working. This is what I did.
I moved the rule to ISPROUTERACCESS in the firewall and set destination to Any. The rule is logged. The problem here is that the origin is LAN and the Default reject rule of the LAN gets triggered, blocking the request from my LAN computer to the ISPRouter IP. The firewall rule at ISPROUTERACCESS never gets triggered.
I tried to duplicate the rule and have it both in LAN and ISPROUTERACCESS and still does not work. Only the rule in LAN gets triggered and the connection times out.
Maybe I misunderstood what you were suggesting.