Where does Snort store captured packets?
-
I'm attempting to track down the source of a DNS query for a .to domain. In Snort, under Interfaces|Lan Settings there a check box (in the Alerts section) to enable packet captures. I turned that on, then examined the entire disk looking for a pcap file or anything that might resemble a packet capture. Suggestions on where to look or what to look for?
-
@rloeb Do you run pfBlocker ?
If you do you may find it’s pfBlocker itself doing lookups of hosts hitting your WAN interface.
Have a look in /var/log/snort/interface for u2 files, you’ll need to use u2boat to convert them to pcap files or if you just want to view them use u2spewfoo.
-
@nogbadthebad Thanks. No U2 files found. There are directories in /var/log/snort for three interfaces. Permission is denied when I attempt to access with WINSCP, but the contents listed from a GUI command prompt appear to be alerts and an app-stats.log.
-
@rloeb There should be something there, unless you've cleared the alerts.
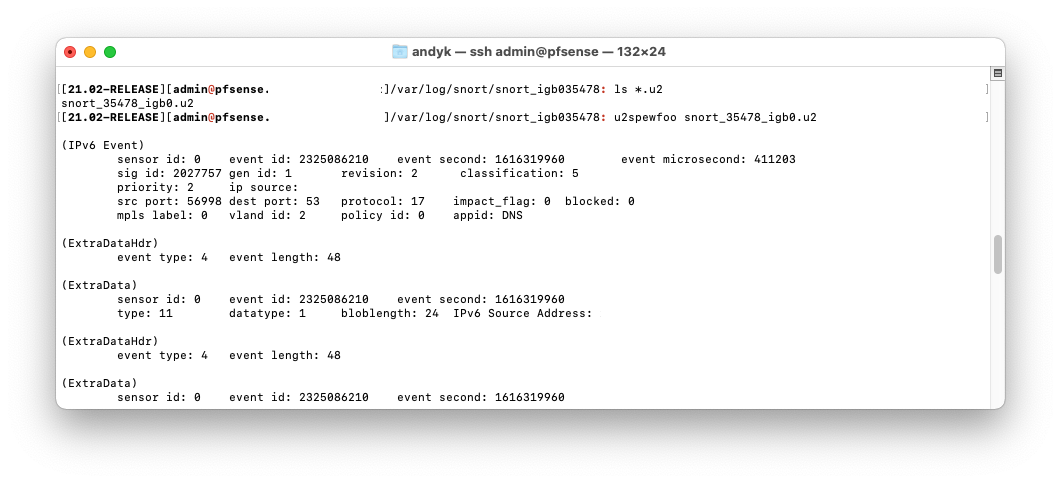
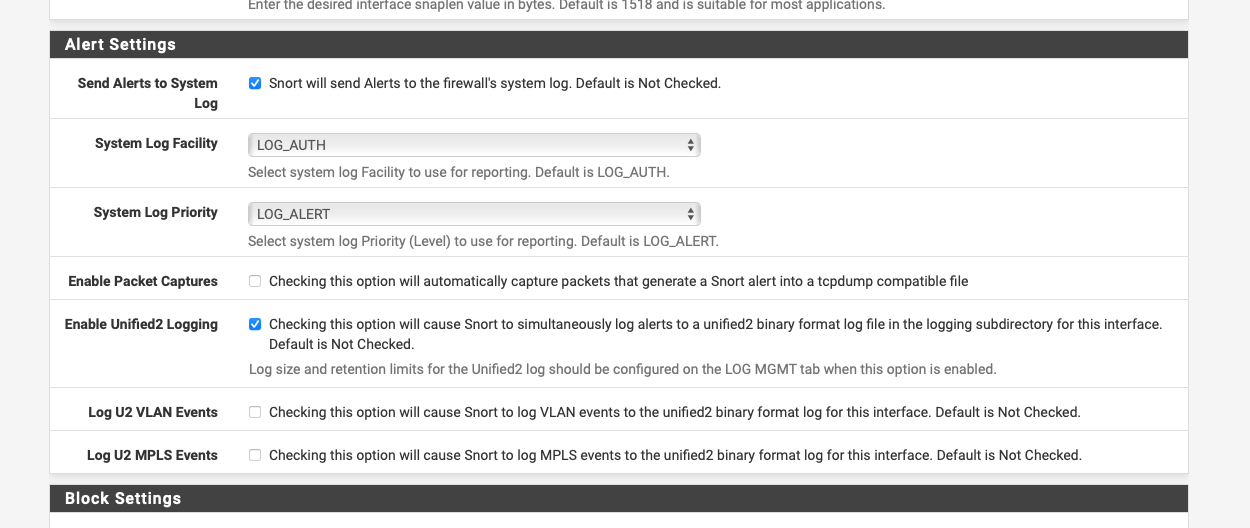
You may need to enable u2 logging.
-
@nogbadthebad Thank you for all the help! I finally got what I needed, although I'm not sure what to do with it. I was concerned about Snort alerts for DNS lookup for .to top level domains, because we seem to get rather a lot of them. .to domains have plenty of legitimate uses, but one of our important clients is convinced that most .to domains are in use for malware purposes, which may or may not be accurate. Having now had the opportunity to examine numerous .to DNS requests, I'm concerned because blocking them seems to also be blocking some important access. (The first one I looked at was yelp.to.)