New to VLAN's
-
Hello All,
I would like to start using VLAN's. I'm not sure if it's posssible with my setup. Whether or not I need them, I would still like to use them just for learning.
Are there any reasons/caveats that you can see that would be an issue?
I have PfSense setup on an old PC, I have one 4 port NIC, each port is a different subnet: 192.168.1.x, 192.168.2.x, 192.168.3.x, etc
Would I just turn them into VLAN's?
As usual, any advice is appreciated!
-
You can "turn them into VLANs" if you want to, it's pretty easy. You don't have to, but you can. You say you want to learn, so...
Here's a good video on pfsense and VLANs by Lawrence Systems:
How To Setup VLANS With pfsense & UniFI
Depending on how big and how complex your network is, you might want to add a small managed switch where you can also do VLAN tagging/passing.
Small managed switch - Netgear Prosafe GS105E
You use something like this, for example, if you wanted to use a single WIFI access point to serve multiple SSID networks - guest and LAN, or guest and trusted, etc.
-
The only significant difference between a VLAN frame and an ordinary frame is the 4 byte VLAN tag. Once you have a VLAN enabled on an interface using it is no different than any other interface. VLANs are used to carry multiple subnets over a single network and logically appears as a separate network. You can use them for multiple SSIDs to an access point, VoIP and computer sharing the same LAN port, etc.
You have to select a VLAN ID and use it at every point the VLAN passes through or connects to. For example, when I set up my guest WiFi, I used VLAN 3 and enabled it on both the AP and pfsense. I also had to configure my switch to pass VLAN 3 through the AP and pfsense ports. You can also use a managed switch to separate the networks into individual ones. Some devices can deal with VLANs directly, others can't.
If you put those multiple interface onto a VLAN, you'd need something, such as a managed switch to separate them again.
-
So I have created a VLAN, which is 192.168.20.1, assigned it to opt1, which is 192.168.2.1
I have setup DHCP on it, and created an allow-all firewall rule on it.
So far, I don't see any difference from what I did.
Doesn't this mean that my IP address should changed to something in the 192.168.20.1 range?
Shouldn't the 192.168.2.1 become 192.168.20.1 now?
Not sure what to expect here. Any suggestions?
-
No, the addresses won't change. They'll be whatever you configure.
-
Well, I did all of the above, but I don't see anything that confirms I did it correctly.
So I assigned VLAN 20 to em0, how can I see or confirm that it's working?
My pc is the only thing plugged into the parent interface (em0) 192.168.2.x
I assumed that my PC would take on the IP of the new VLAN, which is 192.168.20.x
I see no traffic in the logs from the VLAN range.
How can I tell I did this right?
-
In order for that PC to use a VLAN, the interface has to be configured for it. This you can do in both Linux and Windows. But, if you already have a native LAN connection, a VLAN won't do much. As mentioned, VLANs are typically used to allow multiple SSIDs on an access point or share a network connection between a computer and VoIP phone. If you just want to see if the VLAN is working, you can use Wireshark on a computer or Packet Capture on pfsense. You can also use a managed switch (avoid TP-Link) to separate the VLAN and see if it works. You'd have one port on the switch used as a trunk port, which allows multiple VLANs and pick another port to be configured on VLAN 20. Then connect a computer to that port and see if it works.
-
When you say: "the interface has to be configured for it", do you mean the NIC of the PC? I went into the properties of the NIC, and there was: "Packet priority and VLAN - Enabled"
I just want to turn the LAN and OPT interfaces on the 4 port NIC on the Pfsense box into VLAN's:
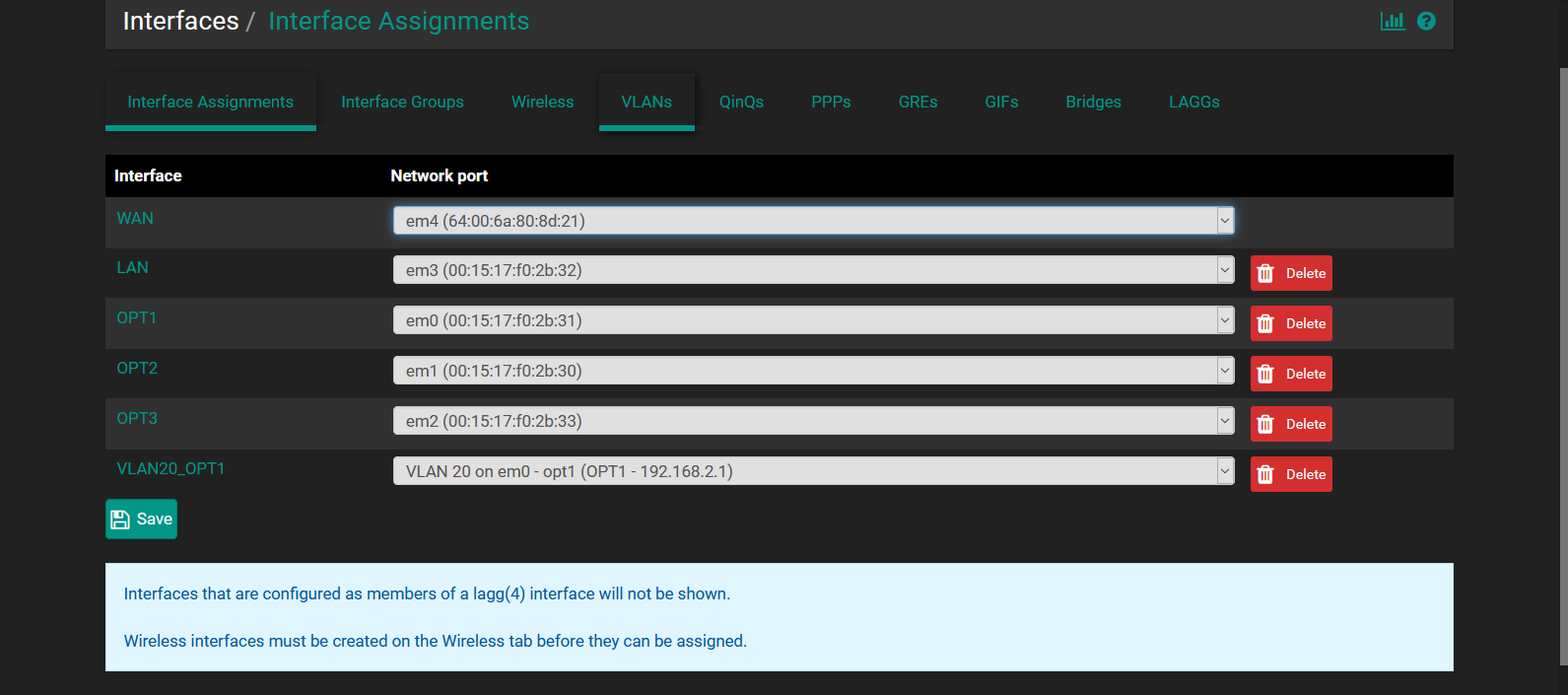
The PC is plugged directly into em0 (OPT1), and that's what I tried to turn into a VLAN.
-
What do you mean by PC? I was referring to a computer connected to your network, not the one pfsense is running on. However, as you mentioned, you have already done that in pfsense. Now with that VLAN 20 configured, you need something else to make use of it. Here I have the 2nd SSID on my access point. While you could also configure a computer to access a VLAN, it wouldn't accomplish much, as you can already do everything over the native LAN.
I'm not sure what you're trying to do here. I know you said you want to start using VLANs, but you don't just use them without some need. In my case, it's a 2nd SSID. In offices, it's to share a single switch port between a computer and VoIP phone. You need some goal here, to do something useful with VLANs. If you want to experiment, you could get a cheap managed switch and configure one port as the trunk port that can carry all the VLANs you've configured and then place individual ports on the VLANs you've created. Regardless, think of VLANs as separate networks that just happen to share the same hardware. What could you do with those separate networks?
-
Yes, I mean a computer connected to the network.
Instead of getting a cheap managed switch, couldn't I treat the 4 port nic as the switch?
Not sure if there would have to be a trunk port in that case.As for a goal, I already have separation across machines using different subnets, I wanted to turn them into VLAN's
That is all I can think of for now, just as a way to start learning VLAN's.
-
If you have 4 NICs, there's likely not much use with using VLANs. If you want to learn about VLANs, you have to actually set them up and have something at the other end of the wire that can handle them. A managed switch will do that. You can create multiple subnets and put them on individual VLANs. Then use the managed switch to sort them out, so that when you plug a computer into the different ports, it will be on the different subnets. Depending on your WiFi situation, you might get a proper AP and use a VLAN to provide a guest WiFi.
One other thing you can do with a managed switch is create a data tap, so you can monitor a connection with Wireshark. This is very handy when learning about networks.
Again, small managed switches are cheap. Just avoid TP-Link.