Securing VLANs
-
I am fairly new to computer networks.
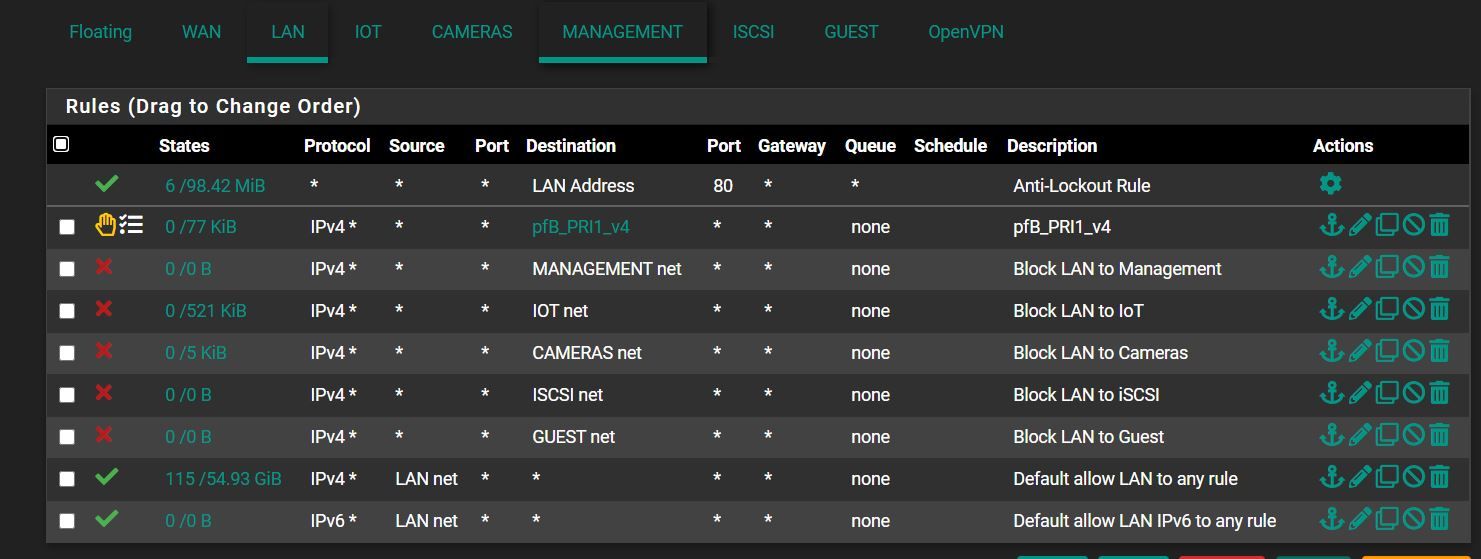
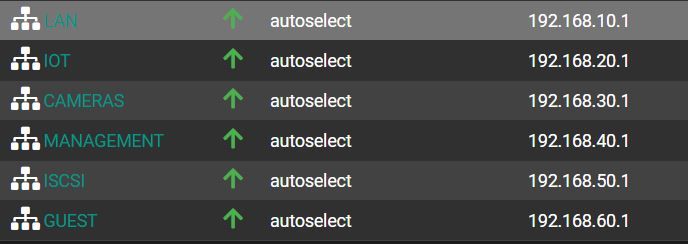
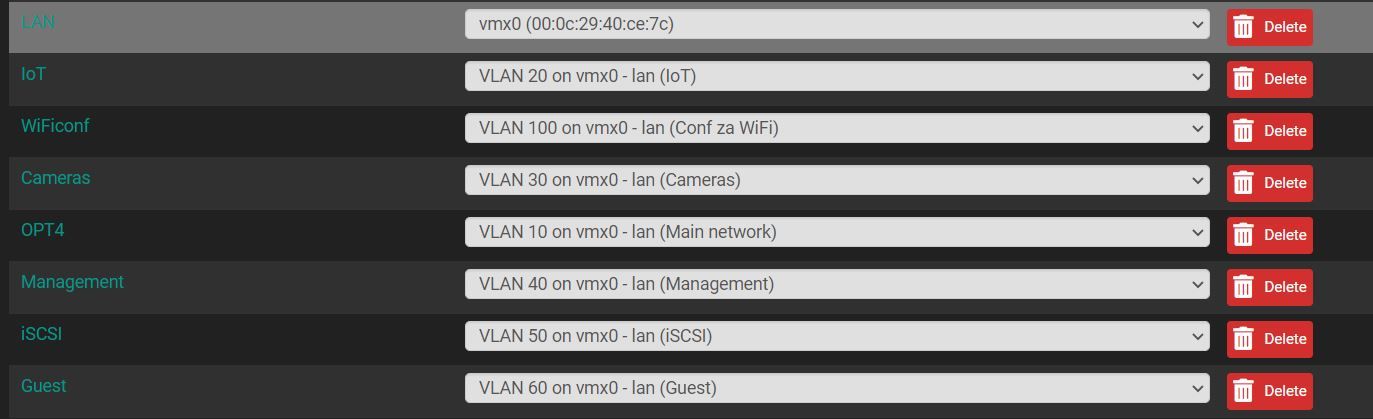
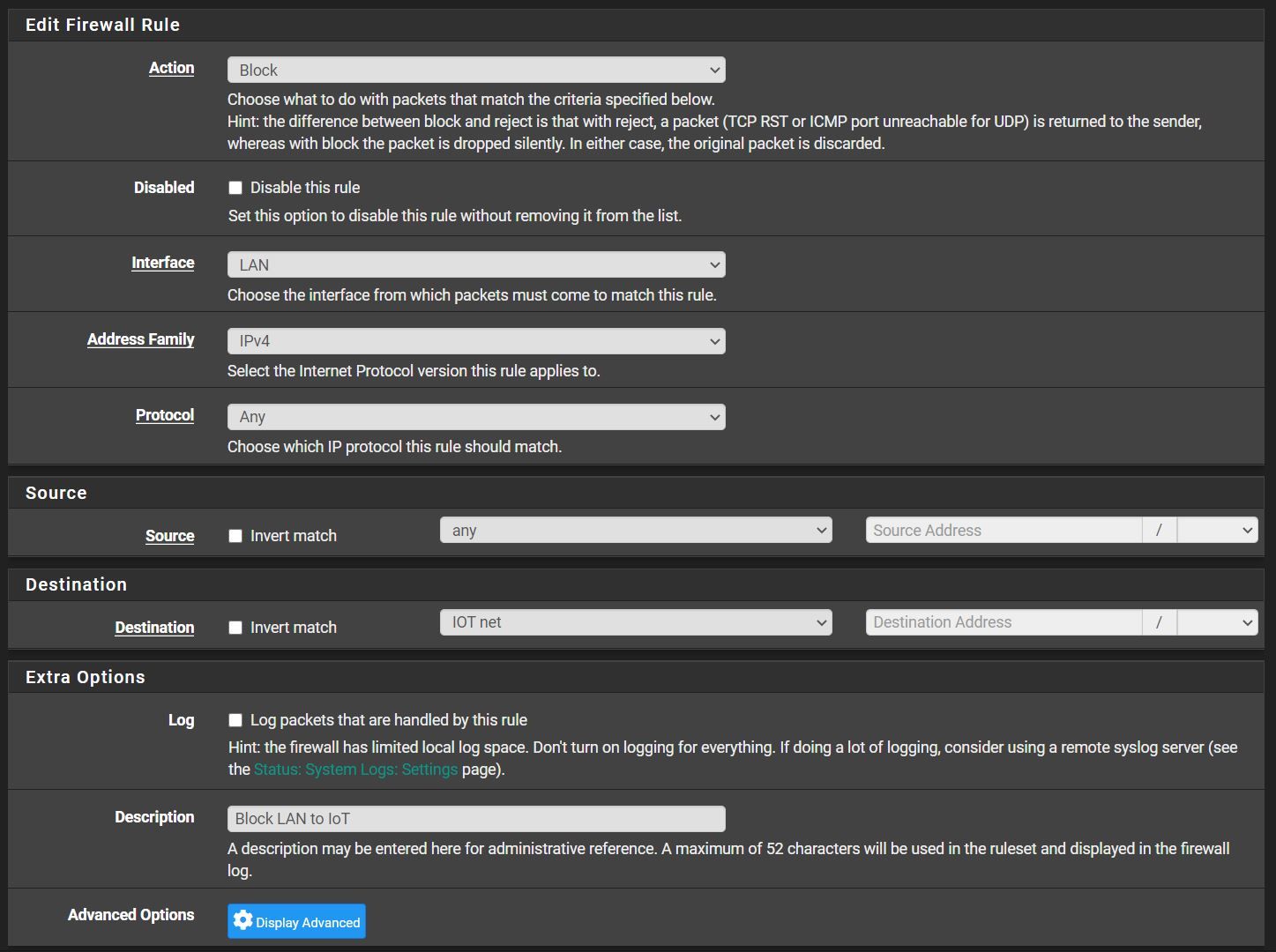
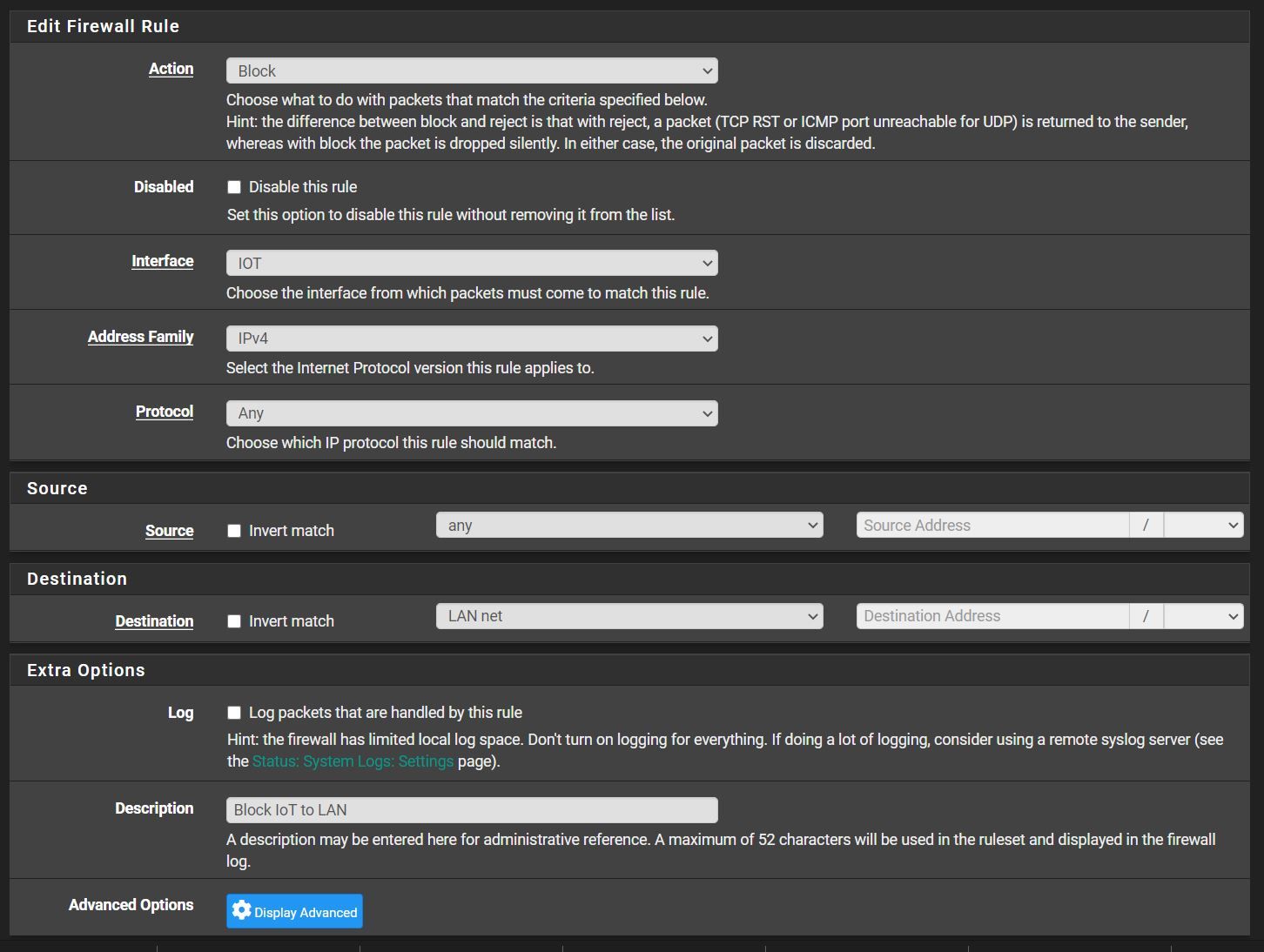
On PfSense (and the switch), I set up a few VLANs to segment my home network.
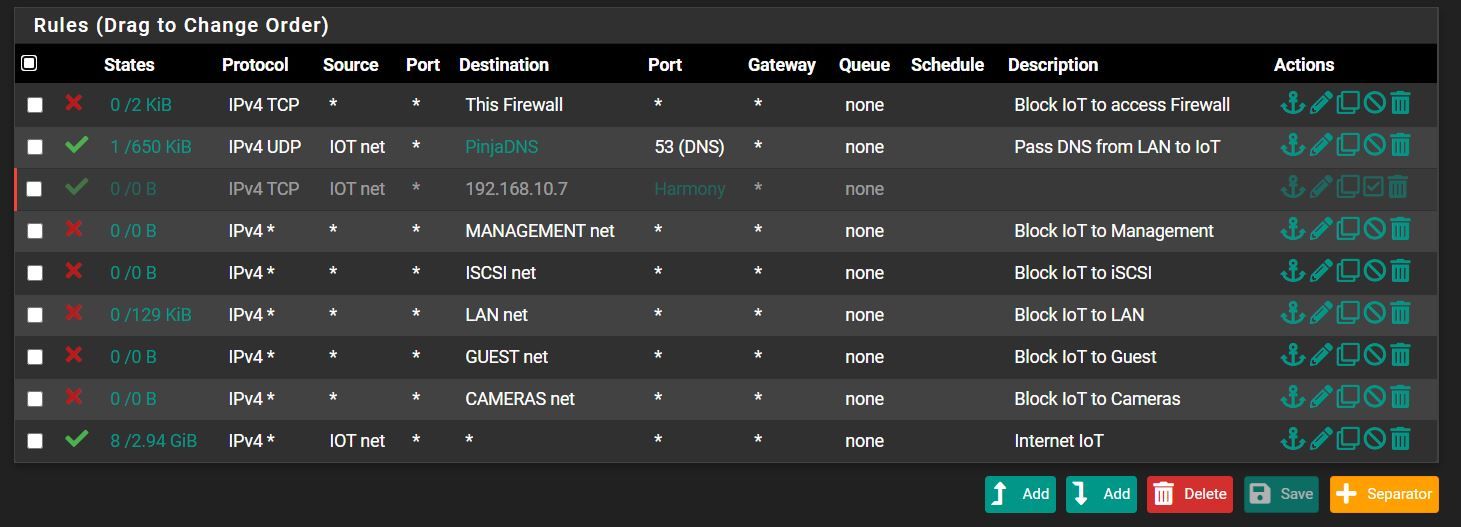
In FW, I set the rules so that the networks do not see each other.
Basically the thing works: from other VLANs ping doesn't work, I can't access shares, printers, etc.
The problem, though, is that I've obviously set something wrong:
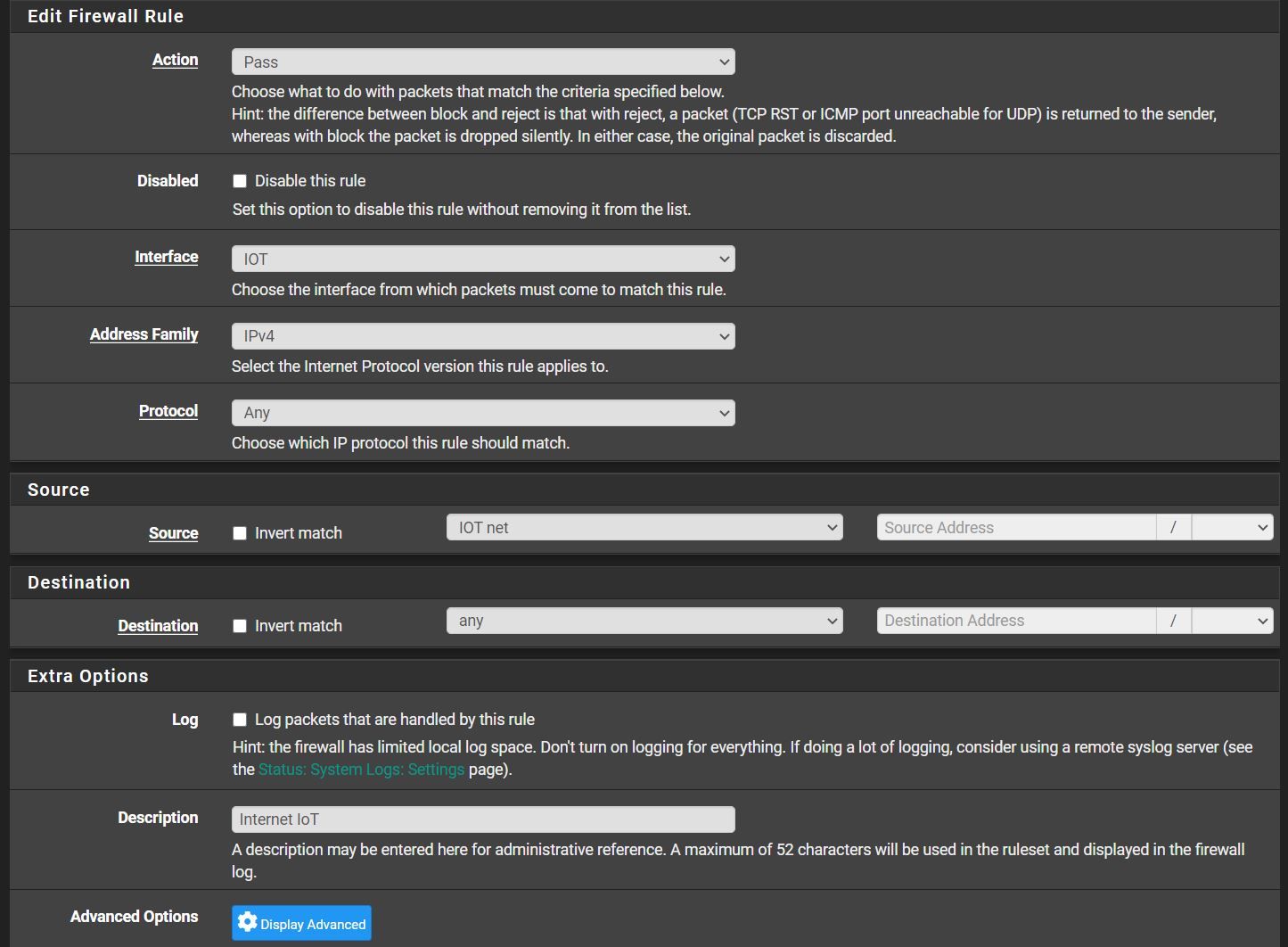
In an IoT VLAN, I have a Logitech Harmony hub that can still communicate with my phone, which is in another VLAN.
By my logic, a phone in VLAN LAN and logitech harmony in VLAN 20 (IoT) should not communicate.
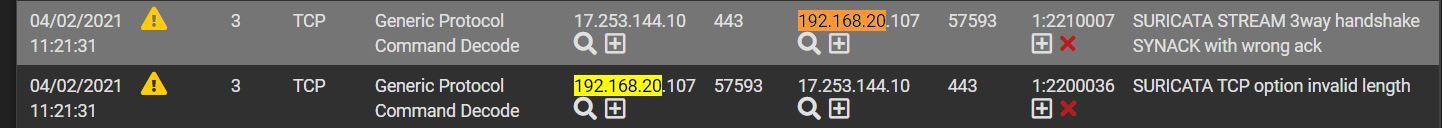
I also watch alerts in Surikata, on LAN network (192.168.10.0) a device from the IoT VLAN (192.168.20.0) appears under the alerts.
I am attaching some Screenshots.
Please advice :)
-
Just so you know, Suricata does not respect VLANs. It will run on the parent physical interface and see ALL traffic passing over the interface. That includes any defined VLANs on that interface.
So while you can appear to "select" just a specific VLAN interface to put Suricata on, the practical result (since it always runs on the physical interface) is that Suricata (and Snort, too, when used) sees all the traffic for all the VLANs defined on the interface.
-
Your rules look "ok", so it maybe was just an old state, kill states or reboot firewall for immediate effects.
Or they use the internet for communication. -
thanks for the explanation about Suricata.
You were right, if I turn off DNS on VLAN20 (IoT), the communication between harmony and the phone no longer works, so they communicate over the Internet and not the LAN.
Thanks!