SG-2100 DMZ for home cloud
-
@sean-0 The link I posted walks one through setting up the LAN switch ports as VLANs so they behave as discrete interfaces. Then the web server plugs into that port and it's on its own network. Am I misunderstanding the goal?
-
@SteveITS The parent interface would be the WAN for the vlan, correct? The webserver should be isolated, removing the port numbers that are not connected to the webserver. This way the server can connect to a dns. I am not experienced with pfsense, so this would be my guess.
-
No, if the web server is in the WAN network there is no need for configuration in the router since it would be outside the router.
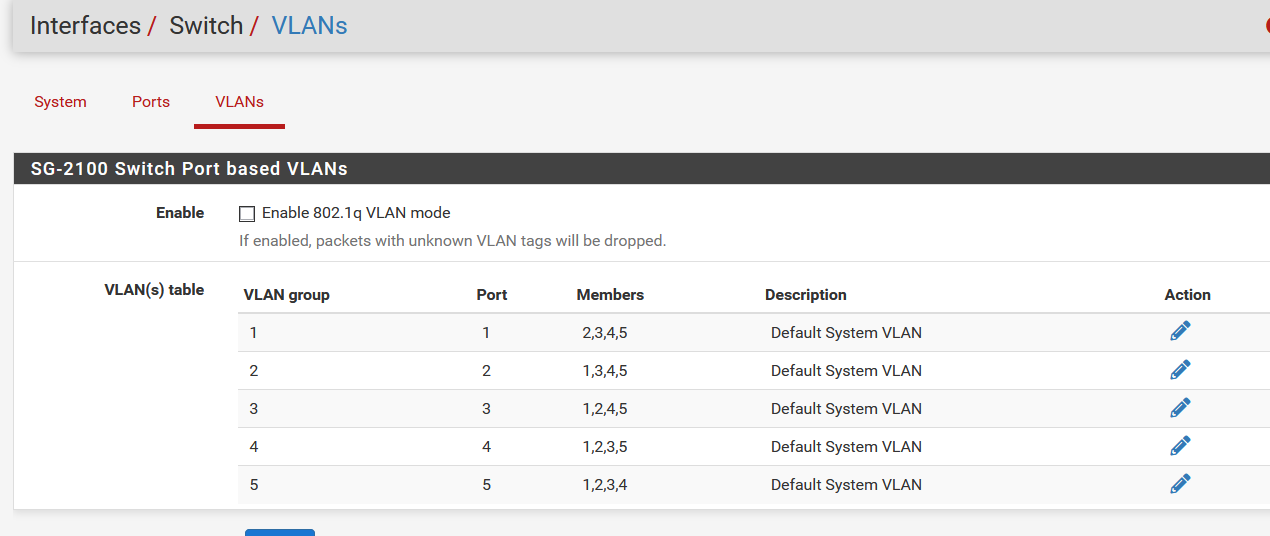
Typically one would set up let's say LAN port 4 on the router to be its own interface (in this case via a VLAN since they are not independent hardware ports) and then the web server plugs into port 4. It has its own network, WANIP:443 can be NATted to webserver:443, and it is isolated from the PCs on LAN. So one would end up with something like:
WAN: public IP
LAN: 10.0.0.0/24
OPT1 using VLAN: 192.168.1.0/24The web server could then be 192.168.1.2, its gateway the router at 192.168.1.1. NAT redirection is set up from WAN:443 to 192.168.1.2:443. PCs on LAN browse to it at 192.168.1.2, or NAT reflection using the WAN IP.
-
@steveits said in SG-2100 DMZ for home cloud:
Typically one would set up let's say LAN port 4 on the router to be its own interface (in this case via a VLAN since they are not independent hardware ports) and then the web server plugs into port 4. It has its own network, WANIP:443 can be NATted to webserver:443, and it is isolated from the PCs on LAN. So one would end up with something like:
WAN: public IP
LAN: 10.0.0.0/24
OPT1 using VLAN: 192.168.1.0/24The web server could then be 192.168.1.2, its gateway the router at 192.168.1.1. NAT redirection is set up from WAN:443 to 192.168.1.2:443. PCs on LAN browse to it at 192.168.1.2, or NAT reflection using the WAN IP.
How do I specify the vlan switch port? What type of NAT rule is that?
Port Forward | 1:1 | Outbound (where wan is) | NPt
The vlan isn't listed as an interface, and because it is dchp, I'm not sure how the server is specified in that connection.
Thanks for the help. I'm much farther because of it.
-
1:1 NAT is for mapping a specific (not the primary) WAN IP to an internal IP.
If you just have one public IP then set up a regular NAT for destination WAN IP, port 443 redirected to your server's private IP port 443.
-
@steveits Is a port forward considered a regular NAT?
-
@steveits said in SG-2100 DMZ for home cloud:
. It has its own network, WANIP:443 can be NATted to webserver:443, and it is isolated from the PCs on LAN. So one would end up with something like:WAN: public IP
LAN: 10.0.0.0/24
OPT1 using VLAN: 192.168.1.0/24The web server could then be 192.168.1.2, its gateway the router at 192.168.1.1. NAT redirection is set up from WAN:443 to 192.168.1.2:443. PCs on LAN browse to it at 192.168.1.2, or NAT reflection using the WAN IP.
Wouldn't 192.168.1.2 be under the lan network when we are creating a seperate vlan switch connected to the wan? I put in 192.168.100.1 to get is to work, but that's not the ip address of the server so I am figuring it out as I go.
-
@SteveITS Ok so I did something. When I type in the opt IP it takes me to the firewall dchp, this can't be right.
-
@sean-0 said in SG-2100 DMZ for home cloud:
Wouldn't 192.168.1.2 be under the lan network
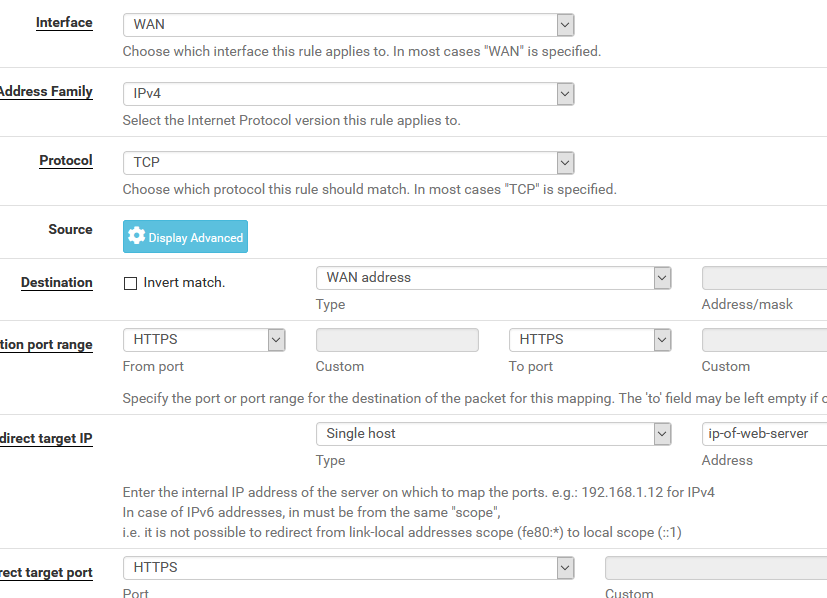
Don't know, you have to tell us. :) What is the IP of the web server? You should end up with something like this on the NAT port forward:
@sean-0 said in SG-2100 DMZ for home cloud:
it takes me to the firewall dchp
Not sure what that means...pfSense's web page? That would be if you're browsing to an IP on the pfSense.
-
@steveits I am creating a subnet in the process. I stumbling through the ip routing/network setup. 192.168.1.1 is the pfsense router/firewall ip. So at somepoint a static ip has to transcribe to the vlan ip. I am considering using haproxy, I believe this would add security and I wouldn't have to change the dchp server setup
-
@steveits How would I determine the webserver IP, it is currently a dchp server... do i need to convert to static or can I reverse proxy?
-
For NAT to work it directs to a specific IP so the web server either needs a static IP or a DHCP reservation. If it's DHCP it will work until the web server happens to get a different IP for some reason.
As far as determining the IP what is the OS of the web server? (run "ipconfig" for Windows or "ip a l" or whatever) If it's getting DHCP from pfSense it would be shown in the DHCP status page.
-
This post is deleted! -
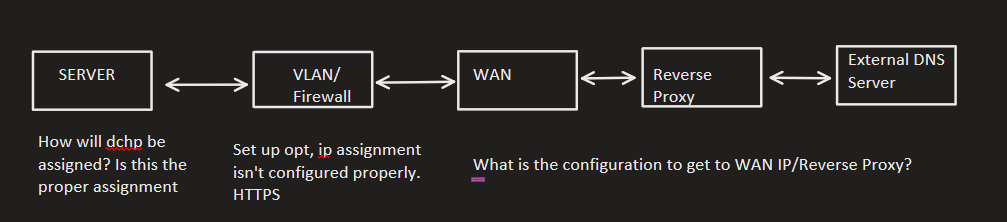
@steveits Its ubuntu live server running apache, but the ip seems off. It doesn't match the ip I entered following the vlan guide. Reverse proxy will solve any dchp potential issues, once configured correctly. My set up matches your picture. I need to accomplish:
-
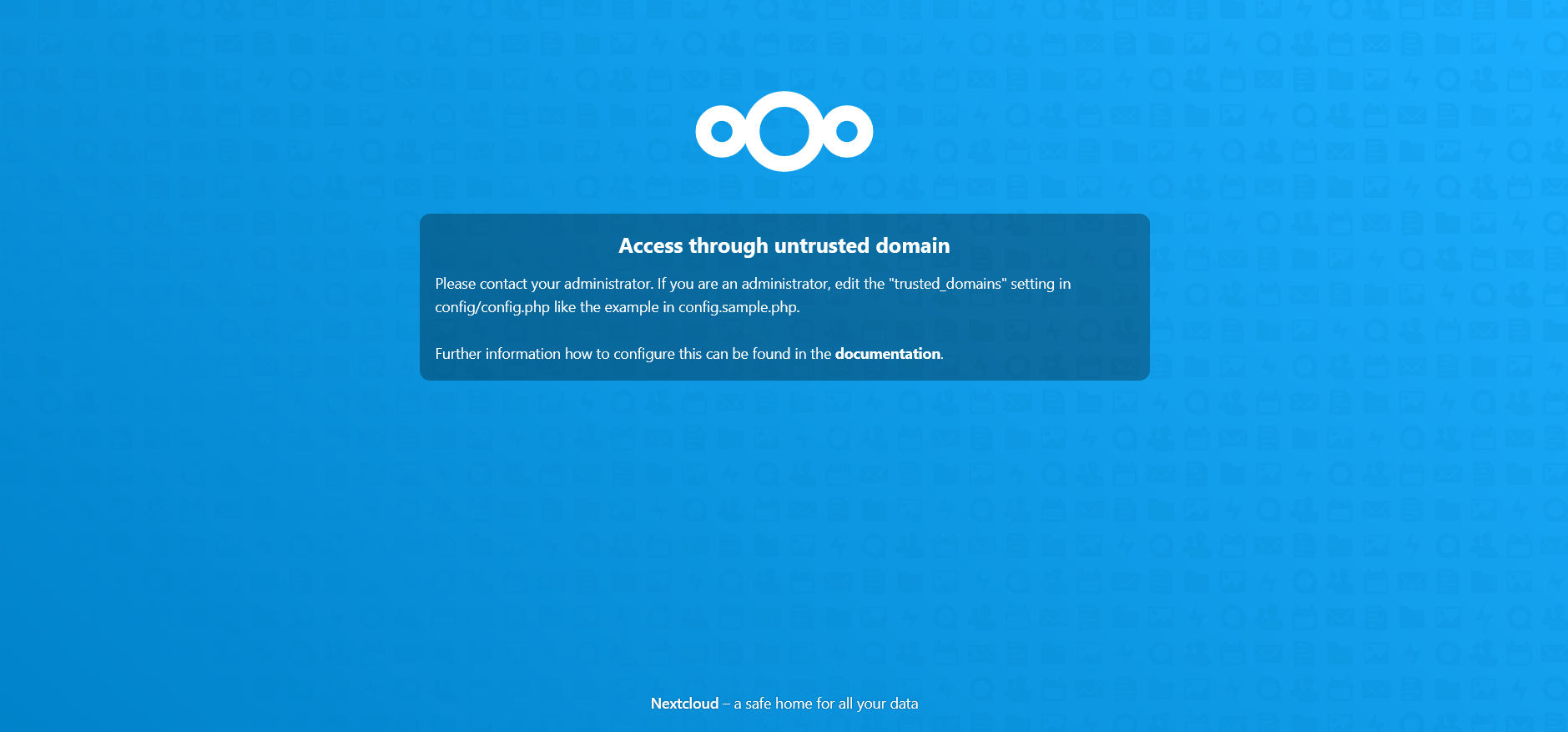
The server is showing, I can't seem to figure out how to set the trusted domain properly, I have entered as many as I can find. -
The end of the doc I posted above mentions "You should also enable DHCP if necessary, by going to Services > DHCP Server > OPT1 (for the example above)." If you didn't do that you'll need to set a static IP on the web sever.
re: untrusted domain, is that what shows in your browser when you connect to the web server? If you're using HTTPS you'll either need a certificate matching the hostname you're using to connect to it, or you'll need to ignore the certificate warning. That's not a pfSense issue.
-
@steveits I got it working on lan. Now I'll have to figure out wan so I can Isolate the server via vlan switch
-
@SteveITS After isolating the vlan on the switch, I had to configure a static IP, and now must configure for the WAN access. Would you know anything about this?