Block IoT to access Internet
-
As I mentioned in previous topic, I am new to computer networks. But learning :)
At home I have been using the Apple HomeKit. Since my Air-condition does not support HomeKit I use a HomeBridge server that allows me to operate the air conditioner with HomeKit. That works OK.
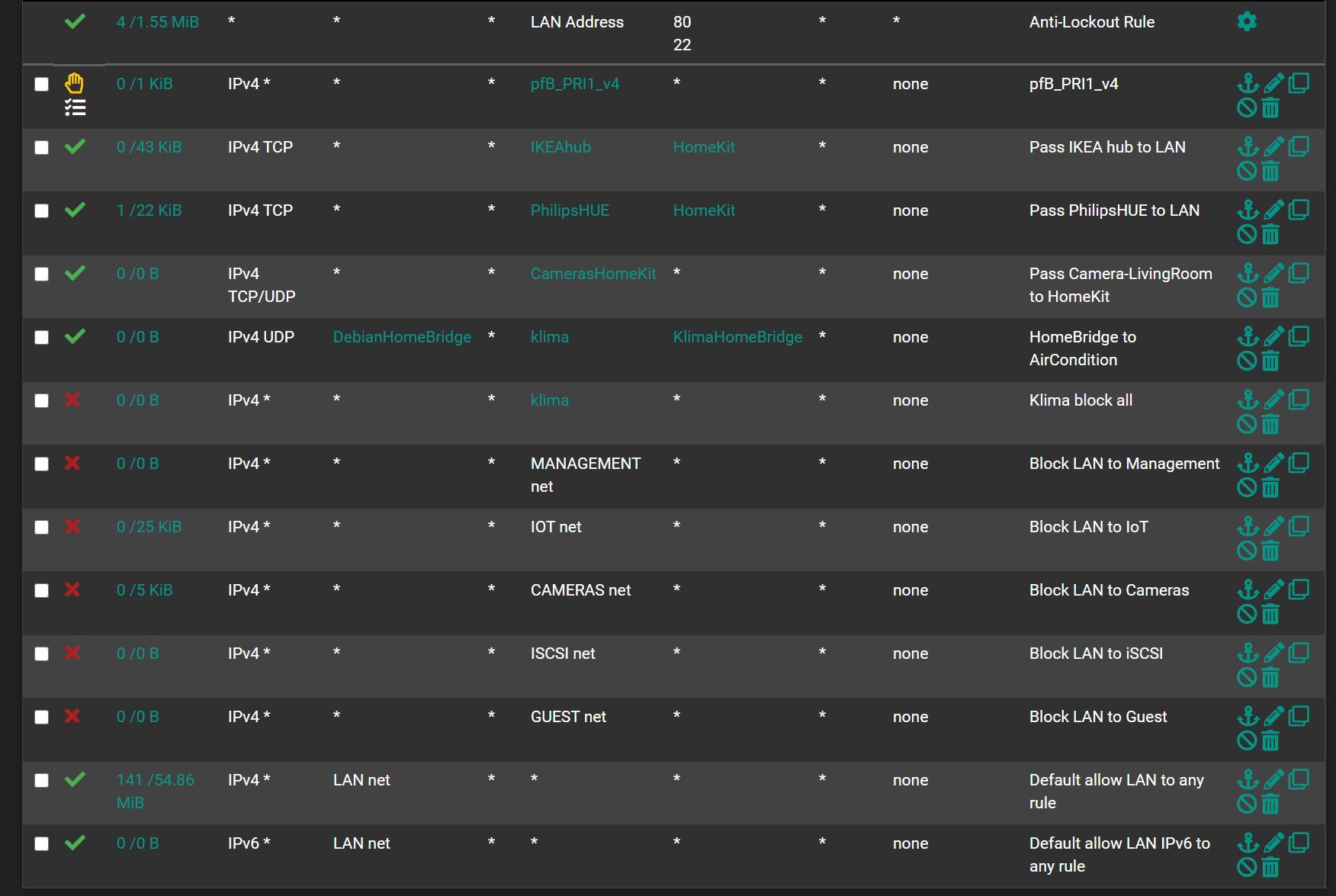
I made two rules in FW, which by my logic should allow communication between the Air-condition and the HomeBridge server. The second rule, however, should block air-condition access to the Internet.
Why do I see connections to external servers when watching Packets Capture?
I don’t want the air conditioner to communicate with the internet, I just want communication between the HomeBridge server that is on my LAN and the air-condition that is in different VLAN than HomeBridge server.
I am attaching some screenshots.
What am I doing wrong?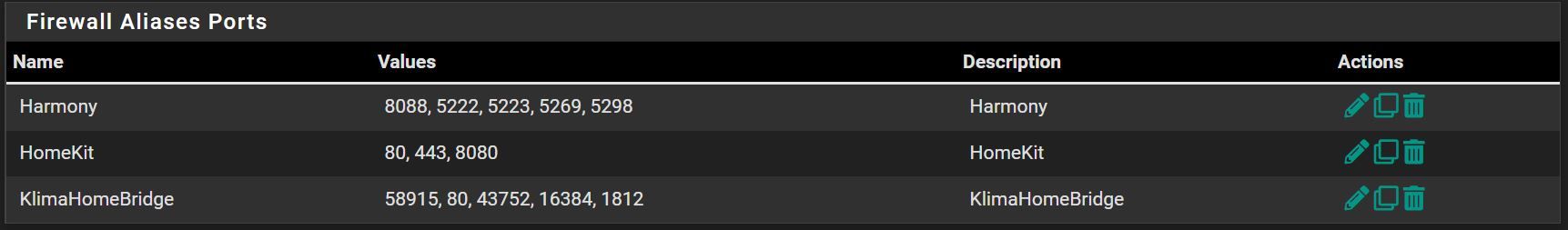

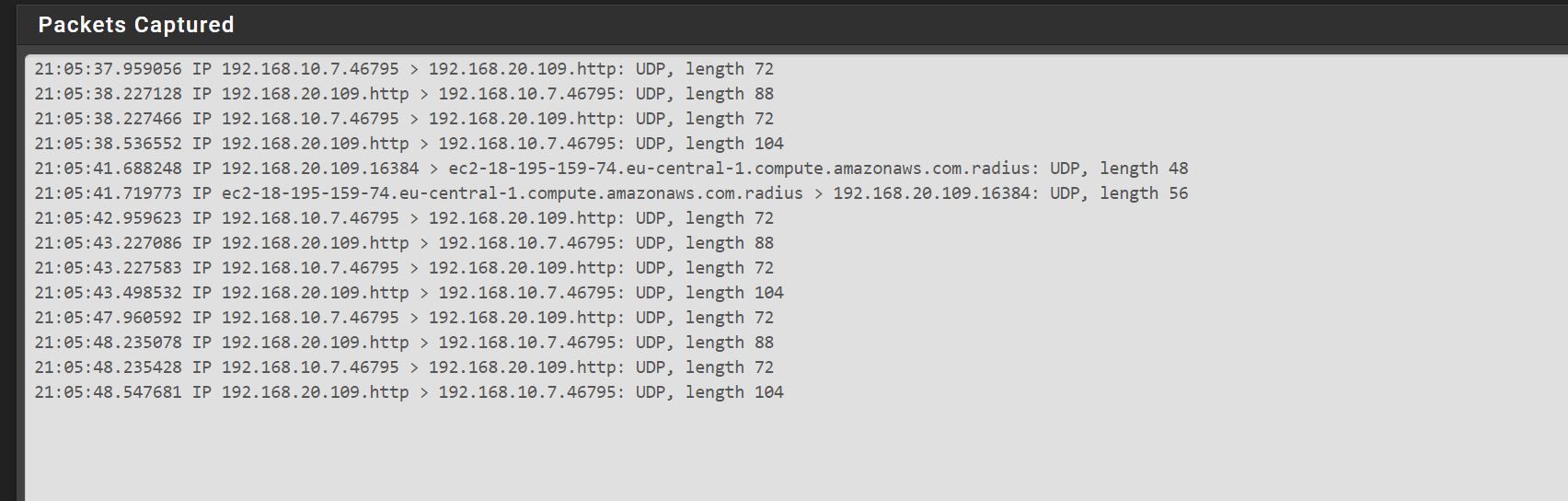
-
Why not just put them on their own network? Failing that, you could create some filters to block 'em.
-
AirCondition is on VLAN20
Server is in VLAN1 -
What specific interface(s) are those rules on? It hard to tell really.. Are those just all your lan rules? I see the antilock out on the top picture.. So that is lan..
But are those other rules also on lan, or some other interface?
You have a rule there at the end that say iot net any - so yeah it can talk to the internet..
-
yes I have IoT net rule. But also have rule "Klima block all" which is above "Internet IoT"
If I am correct rule "klima block all" wins in this situation? Not sure:)
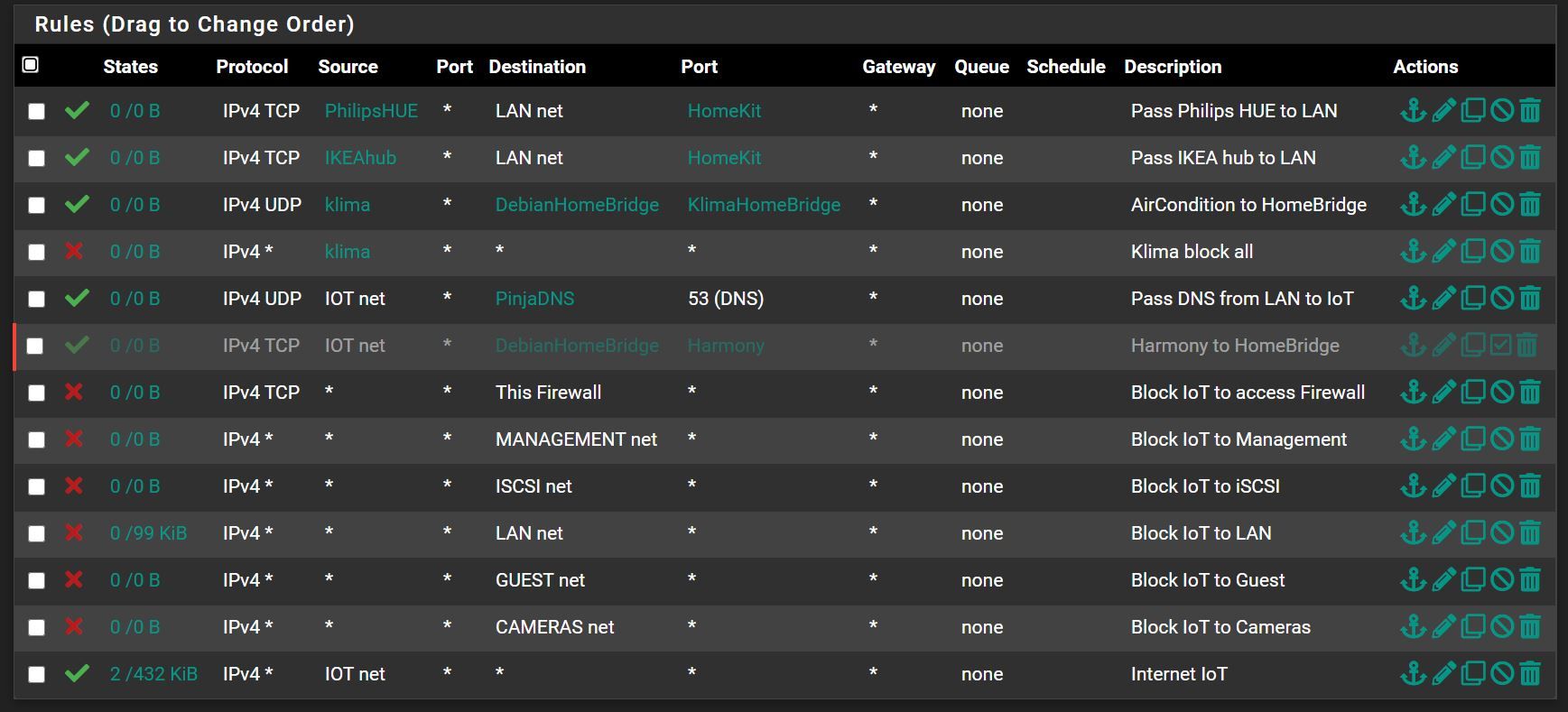
Two more screenshots, with interfaces names included:
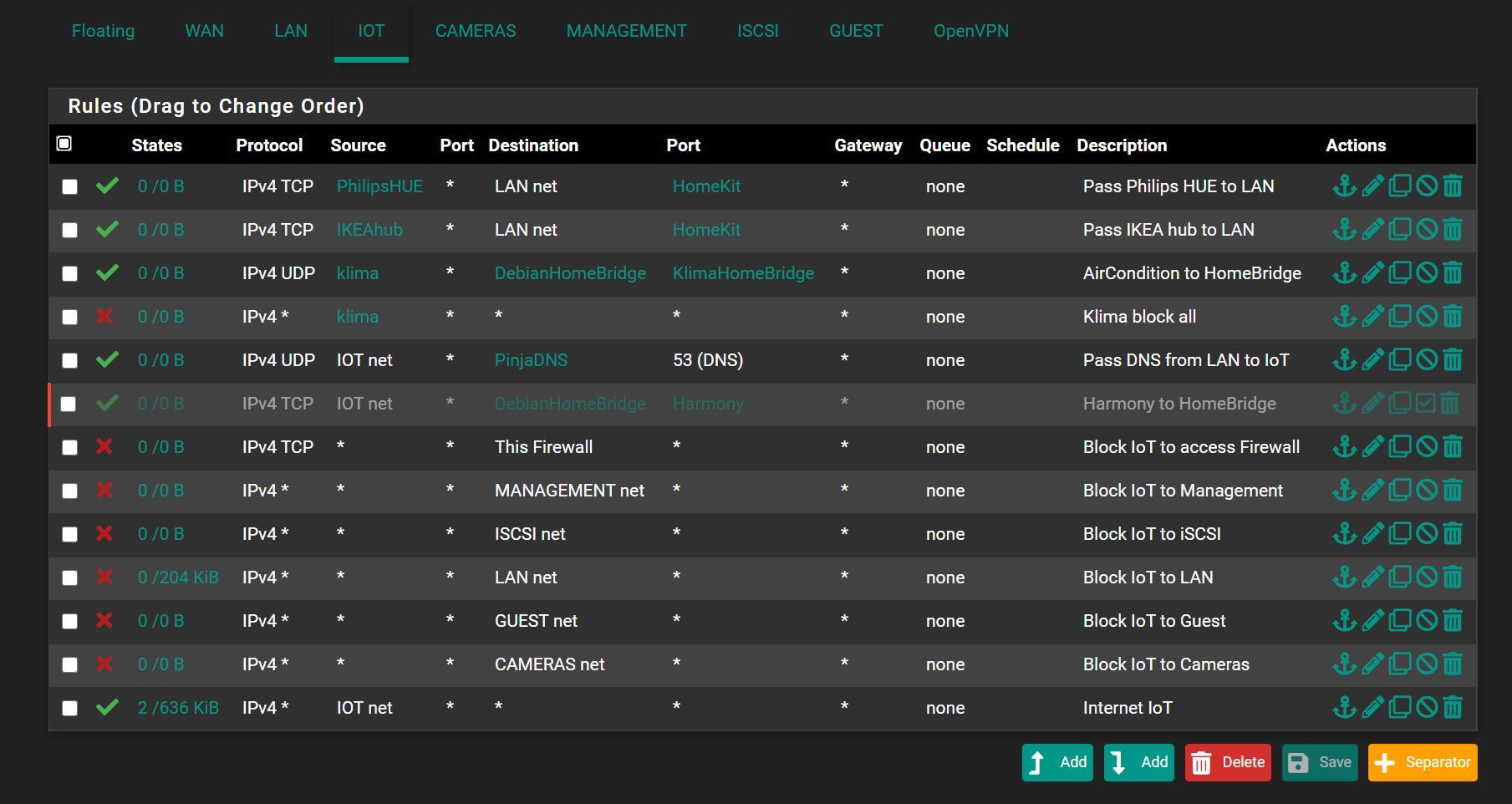
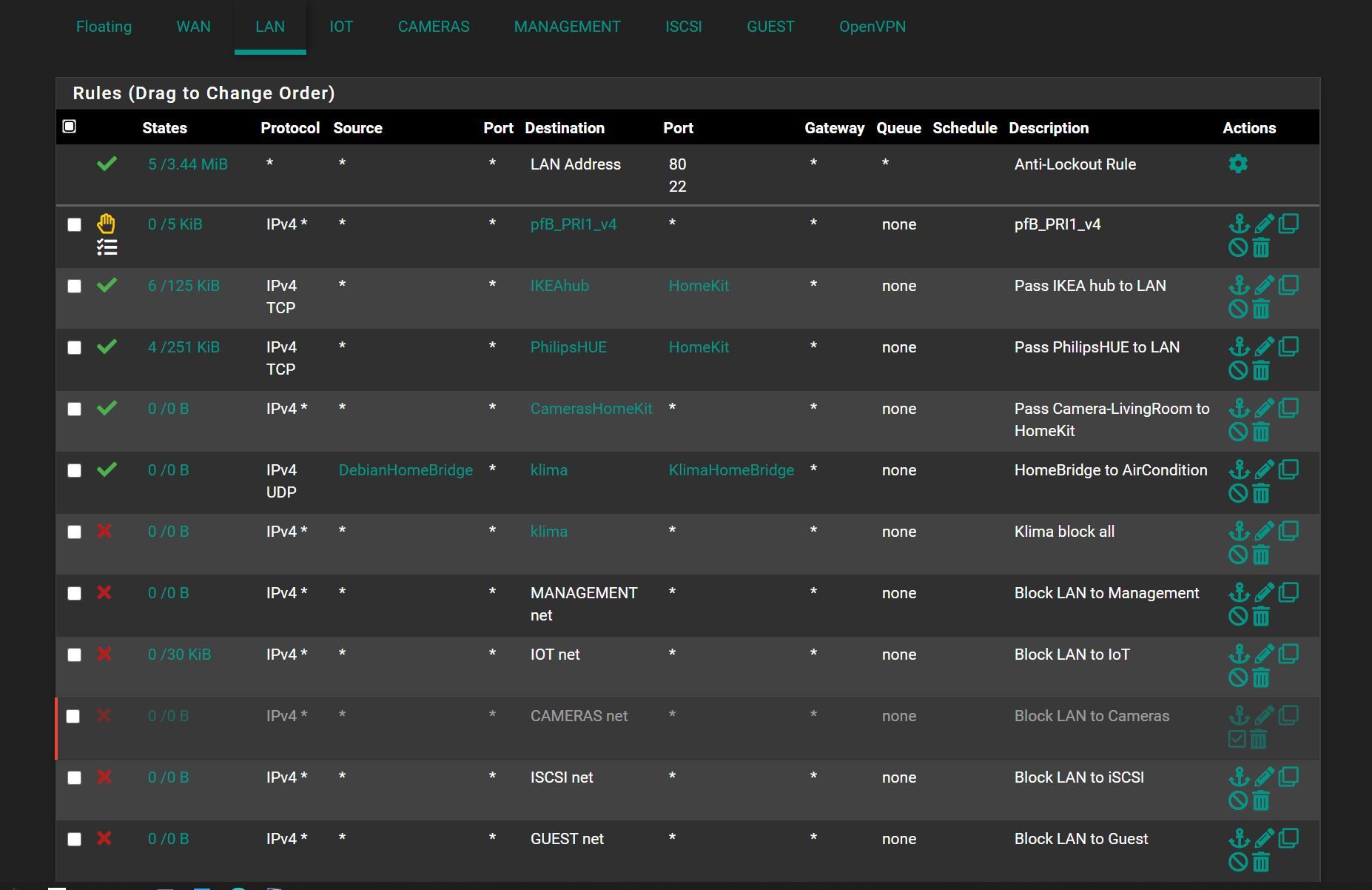
-
well yes rules are evaluated top down, first rule to trigger wins. No other other rules are evaluated.
So you need to validate that the source IP of this klima alias does in fact contain the source IP of what your wanting to block.
And second you need to make sure there are no active states for this IP. If there is an active state already - rules that block said access would not come into play until this state either times out or is removed.
Quick way would be to look in your states for this source IP - and kill any states that you no longer want, ie say something to the internet IP.
3rd thing - make sure you have no rules say in floating that would allow the access, since floating is evaluated before interface rules.
-
Hi,
thanks for explanation.
source IP "klima" is OK.
I do not have anyfloating rules.
I did kill all states. And it seams that this work. Now there is no more connections to internet.
Now I am trying to figure out why is still trying to communicate to my DNS (192.168.10.3)? DNS is not responding, thats OK.
09:46:47.787722 IP 192.168.20.109.1086 > 192.168.10.3.domain: UDP, length 43
09:46:48.786857 IP 192.168.20.109.1087 > 192.168.10.3.domain: UDP, length 41
09:46:48.832515 IP 192.168.20.109.1087 > 192.168.10.3.domain: UDP, length 41
09:46:49.784541 IP 192.168.20.109.1087 > 192.168.10.3.domain: UDP, length 41
09:46:50.788731 IP 192.168.20.109.1087 > 192.168.10.3.domain: UDP, length 41 -
@charlie48 said in Block IoT to access Internet:
Now I am trying to figure out why is still trying to communicate to my DNS (192.168.10.3)? DNS is not responding, thats OK.
09:46:47.787722 IP 192.168.20.109.1086 > 192.168.10.3.domain: UDP, length 43
09:46:48.786857 IP 192.168.20.109.1087 > 192.168.10.3.domain: UDP, length 41
09:46:48.832515 IP 192.168.20.109.1087 > 192.168.10.3.domain: UDP, length 41
09:46:49.784541 IP 192.168.20.109.1087 > 192.168.10.3.domain: UDP, length 41
09:46:50.788731 IP 192.168.20.109.1087 > 192.168.10.3.domain: UDP, length 41That would prob be your IOT device that is configured for that ip.
Either via DHCP or a static assignment (that says 192.168.10.3 is your DNS server)If those are "Smart IOT devices" it might even remember that last ip it has used as a succesfull DNS server.
/Bingo
-
Thanks for explanation.
Main thing is, that Air-condition is now blocked to "call home". I really do not see reason to do that.
I am now sniffing traffic of my other IoT devices and I am really not happy. Lots of traffic.
Philips Hue hub constantly connect to multiple WAN IPs. Need to find solution how to make it work with apple home kit without Internet connection.
I did try it wit Avahi packet, but at the moment not seems that it work for me.
-
Most iot devices - say smart lightbulbs really need to be able to talk to the mothership to work correctly. This how for example your able to turn your lights on while your outside your network.
Since you tell the mothership - hey turn lights on, and light is talking to mothership to know - hey I should turn on.
Is this the most secure setup - prob not ;) But it does allow for your typical user without a clue to how to port forward, etc. to be able to control their devices without having to do anything but connect to an account with their app on their phone and be able to control said device from pretty much anywhere.
To get your devices to work without doing this will prob take some tinkering.. And your device(s) maybe not even support such control - and only work with stuff coming from the mothership connection.
You might just have to embrace the suck if you want to use cheap iot devices. And let them phone home. Just isolate them to their own vlan, and keep them from talking to the rest of your network.. And just keep an eye on what they are talking to on the internet.
The serious drawback to these devices, other than the obvious security concerns - is if the mothership goes away or offline, you can not control your devices.. Other than the physical flipping of the switch.. Even when your local network might be running just fine.
edit: I can live with the mothership connection to be honest, but what blows my mind is the serious amount of noise they put on the network.. They are broadcast storm monkeys - did they really think this through as the number of devices ramp up on the network.. Which is just a limit wifi 2.4 network..
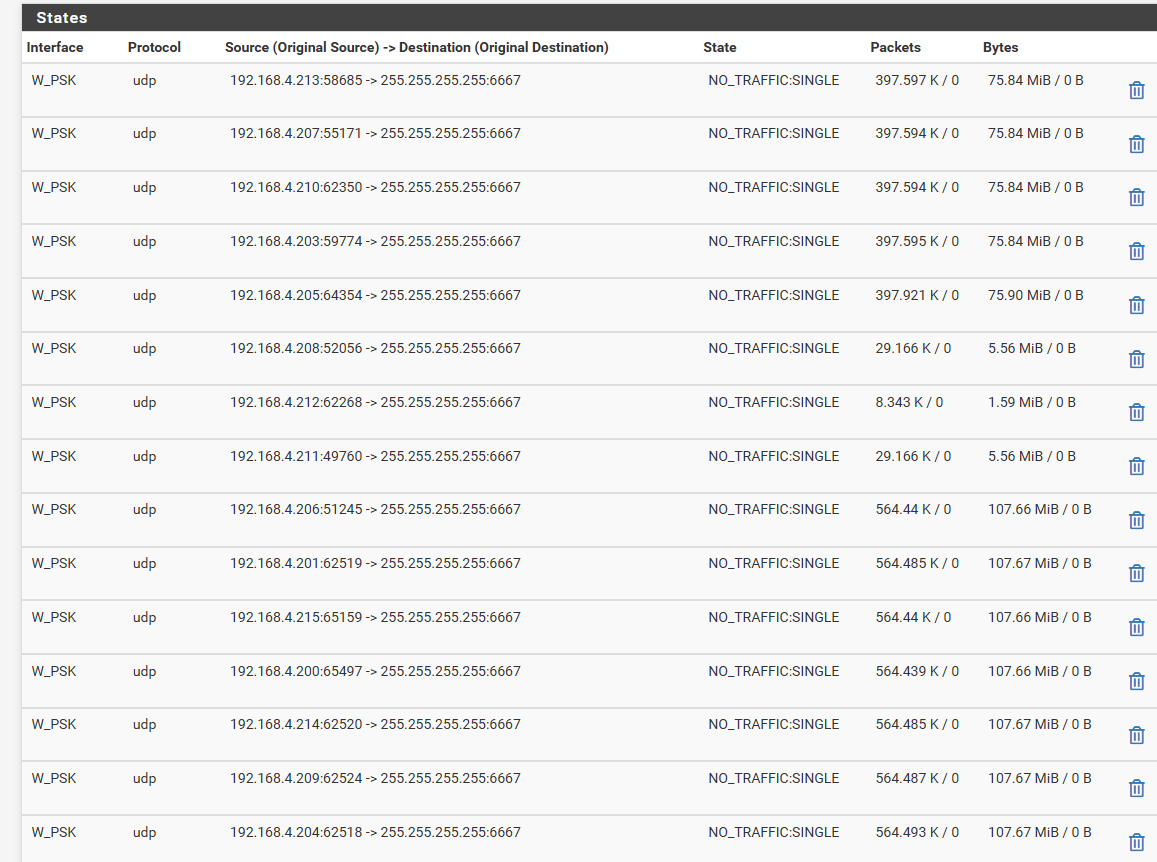
That is some serious amount of broadcast packets ;)
-
Yes I agree, lots of Broadcast traffic. But OK, I block them to call home. Now Philips Hue bridge and bridge for IKEA lights have no access to internet.
From home LAN they communicate via ports 80, 8080 and 443. They discover each other via mDNS with help of Avahi packet in pfSense. If I want to control my light when I am not at home, I can use apple gateway. In my case this is HomePod. Also not most secure way to share data with apple, but still better than Philips and Ikea and dont want even think why my air-condition was talking to some servers in Germany. :/
Next big challenge are my cameras. No idea how should I solve them. They need internet connection for authentication when I open app on my phone. You cant login locally but via vendors server. I use https://us.eufylife.com/collections/all/products/t8410
Nice cameras, if I don't count login via server :) -
@charlie48 said in Block IoT to access Internet:
Next big challenge are my cameras.
At least, with these, you know that what the cameras see, is what some one else, where ever he is, also sees. And with the help of an app, even you can see it (better check if it is real time and not a replay ^^)
Seriously. You are actually using them ??cameras == local storage and if needed, shrink wrapped encrypted and stored elsewhere.
( and why not, I dump screen shots on our companies website, works great )
I create an inbound VPN if I need to see cameras on my phone.