OpenVPN gateway is now local
-
After breaking up pfSense into smaller appliances I had to start almost from scratch, I did get a newer installer image. :)
I got the appliances and VLANs and in-hypervisor DMZs ready and lined up to hot swap them with the old setup when I noticed the new already-connected edge firewall, had the local end of a tunnel as the latter's gateway. This is a new topology, I still had a lot of loose ends with VLANs and rules I was also trying to maintain connectivity with conflicting addresses here and there, it was HARD. That address
didn'tdoesn't make any sense. To be sure there were there were no other routes and this was in fact the gateway being used I started shutting down things but echo requests from deep inside the network at the local computer made it all the way and back but I was now so tired and confused that I kept second guessing what I was watching on screen.These are all the gateways:
1 x ISP gateway (WAN_FIBER_PPPOE)
1 x LAN static route (next stop is the reverse proxy,proxy4)
1 x public VPN gateway (WAN_SURFSHARK_VPNV4)
1 x private VPN gateway (WAN_CLOUDFRONT_VPNV4)
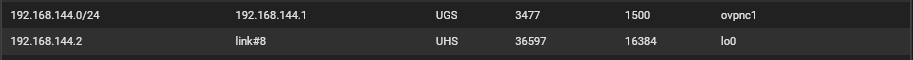
The tunnel uses the network
192.168.144.0/24(expanded from/30to accomodate more clients while replacing the old). This is client-side, it should be192.168.144.1, not.2. The RTT to the datacenter (~2200km/1300mi) of the other firewall is around 30ms, 0.2ms is impossible, even to my ISP or to the immediate device downstream the trip times are higher.I changed things on the remote side several times and reverted to backups but I couldn't make it report the correct gateway again, but it's nevertheless working for some reason. The gateway does make an appearance, briefly so, in the Routes section:
That about it, it's also gone from the interface details:

I tried setting the monitor IP using the correct gateway but it killed it:
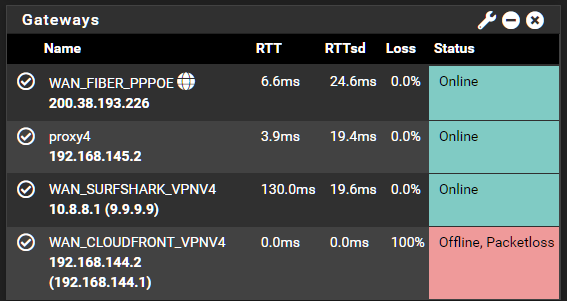
I'm thinking about switching to IKEv2 but it's so confusing when there's NAT. :/ Were there any changes in the software that I missed then got back with a clean image (I was using the betas earlier but the system merged back to stabled when it was released) or did I screw up my configuration plainly?
Thanks

-
I fixed it! Sort of...
There was a OpenVPN client override. The address wasn't complete, I guess I must've missed it. I don't remember setting it at all though, maybe somebody else did.
Upon restoring some areas from the old firewall the outbound NAT was restored without matching the gateway, so that was another problem.
The finally the gateways were correct, the routes were correct but pings would only work one way.. I kept resetting things until neither could ping. I have frequent backups for both firewalls going back for almost a year, I always took them at the same time so settings would match but none seem to work.
Even after adding allow-everything rules on the tunnel I cannot get it to ping, it just stopped. Installed FRR, didn't help.
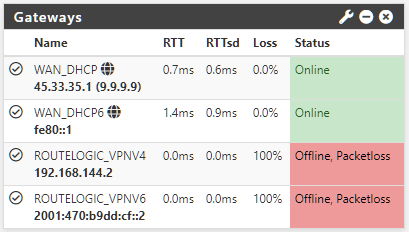
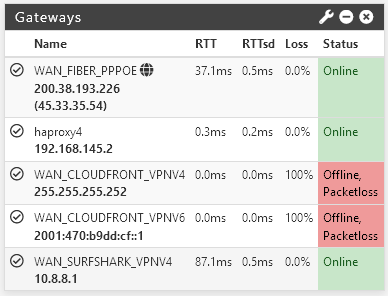
Then I tried playing with the ciphers with some interesting effects, like tanking all connectivity despite the tunnel is no set as the default gateway in either side to the one sided thing.
However, it was when I switched to shared key that I got connectivity back. It had always been as a TLS tunnel, I don't know what's different now.

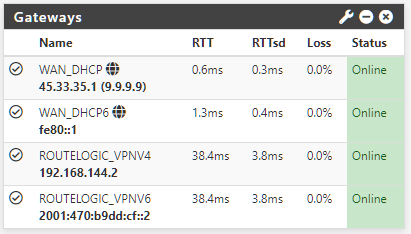
But the tunnel is merely a conduit to have a static public IP disposable at any moment; it's considered as a WAN interfaced and policed as so thus I could care less about encryption security or anything else, I'm just soo grateful it works again. :D
Now I have to close it up 'cause it's still wide-open-firewall as I speak.
I tried IPsec BTW, but it had mismatching numbers, then I tried to "play its game" so to speak so I duplicated one of the P1s so the interface numbers would match. They did, but it still never connected. Since this is heavily dependent on encryption as well as the TLS OpenVPN, I think there might be something wrong with OpenSSL or whatever's behind the scenes there--that's just my highly uneducated guess though. Anyway, maybe this helps somebody else.