OpenVPN client not routing LAN traffic
-
I've got my sg-1100 configured as an OpenVPN client connecting to a server in a data centre. The VPN connection starts OK and from the pfSense shell I can ping the server side of the VPN and other hosts on the remote network so I know that the connection is fine. The top half here is local pfSense client, the bottom the VPN server
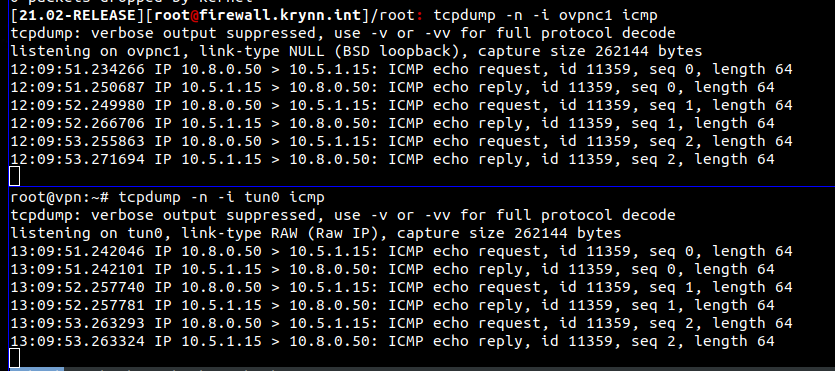
The problem I've got is when hosts on my local LAN try to access hosts on the other side, I can see traffic entering the tunnel but it doesn't come out the other side.
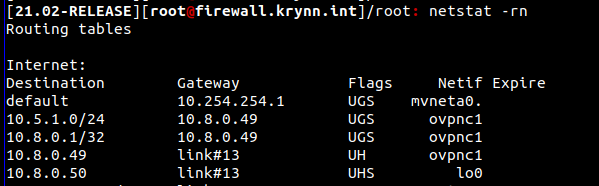
The route appears to be in place correctly.
This used to work when I had a pfSense running on an Alix box, but since I replaced it with the sg-1100 it isn't working so I'm fairly confident that it is the client side that is wrong. I've also tried setting it up with pfSense in a VM and that does the same. I'd love to go back to the Alix to compare configs, but it died and despite many attempts, I can't even get a serial console to show up.
It doesn't look like a firewall rule that is blocking things, I've only got blocking rules on the WAN interface so they shouldn't be interfering here.
I've not set any custom routing up in pfSense, when I tried adding interfaces and routing I lost the ability to ping from the device itself so that always seemed to make things worse rather than better.
I know the problem will be something I've not setup, but I can't see what it is. What have I done wrong or missed?
-
@digininja99
Possibly the remote site is missing the route back to your LAN.If there is no possibility to add it, you can do masquerading on the VPN interface by setting up an outbound NAT rule.
-
@viragomann I'm away from the machine so can't check at the moment, but if the was the case, wouldn't I still see the traffic leaving the tunnel on the VPN side?
Before I changed boxes the routing all worked fine so I don't think that is causing it.
-
@digininja99 said in OpenVPN client not routing LAN traffic:
but if the was the case, wouldn't I still see the traffic leaving the tunnel on the VPN side?
You can see only request packets from your LAN, no replies!
Before I changed boxes the routing all worked fine so I don't think that is causing it.
Possibly you had masqerading ebabled.
-
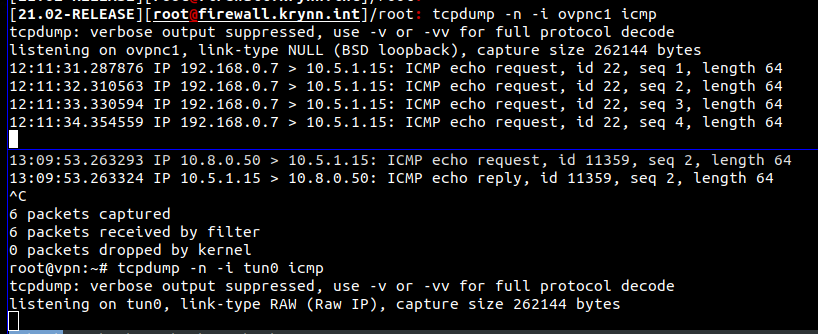
@viragomann The bottom of the second screenshot is the VPN side of the tunnel, nothing is coming out of it. The top is the pfSense box, I see the ICMP packet coming in from the LAN with the destination of a host on the VPN side. I could be looking at completely the wrong thing, but I would expect the traffic to exit the VPN through tun0 even if they then disappear and don't get routed back.
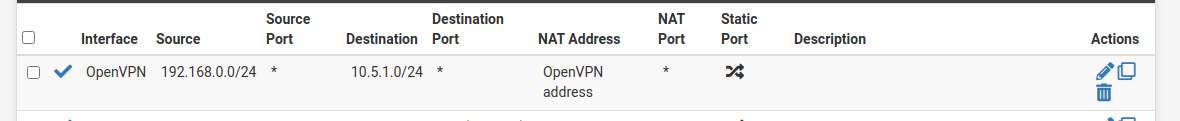
How do I turn masquerading on so I can test if that is the problem?
-
@digininja99 That was it, I've just added this rule on NAT and all is working.
Can anyone explain why the packets didn't come out of the tunnel on the server side? Where were they getting lost?
-
@viragomann said in OpenVPN client not routing LAN traffic:
Possibly the remote site is missing the route back to your LAN.
-
@viragomann What I'm trying to understand is why I don't see the packets coming out of the tunnel on the VPN side and then getting lost. If that box didn't have a route back, wouldn't the ICMP requests come out, and then the responses get routed out of the default gateway?
-
@digininja99
Without an explanation what the IPs are, it's sadly only a panel game. But I assume that 192.168.0.7 is one of your LAN devices.So again, my assumption is that the remote site is missing the route back to this LAN IP and so its not possible to direct its packets correctly into the VPN, instead it will send them out to its default gateway.
Hence you won't see any respond packet from the remote on the VPN interface, but you see only requests.
That's what you get, I think. -
@viragomann the 192 address is my local LAN making the requests.
"So again, my assumption is that the remote site is missing the route back to this LAN IP and so its not possible to direct its packets correctly into the VPN, instead it will send them out to its default gateway."
I agree that if the server side was missing the route back, it wouldn't know what to do with the traffic and how to send it back, but the key bit I'm not getting is that shouldn't I see that traffic emerging from the tunnel on the VPN side, the bottom tcpdump on the second screenshot. I fully get why I don't see any traffic coming back into pfSense from the VPN side, because no traffic is sent back, but I don't get why I don't see the ICMP requests that go in on the top of the screenshot come out on the bottom. Where does that traffic go?
I'm sure you are right with what you are saying, I just want to know where the packets go missing. I thought that if they went into a tunnel they would come out the other side, even if they then got lost and the next hop sent them the wrong direction and out the wrong gateway.