Segmenting OpenVPN Users
-
Hello,
I'm new to OpenVPN, and looking for advice on how to best set it up for use with my scenario...
I've successfully created a OpenVPN server per the wizard, allow remote access to the default (management) LAN. I'm using the local database for auth. I would like to use this for myself to access management and all other nodes as is allowed from the default LAN.
I also have several VLANs in place that isolate client VMs. I would like to be able to give clients VPN access to only their VLAN. Some clients may have multiple VPN users.
To test this, I created another OpenVPN server, set the local networks to match that of the VLAN, and connected. This worked as expected, isolating access to the assigned VLAN network for the VPN user.
However, it seems like this would easily allow for a user to change the port and access the management LAN via the first OpenVPN server I created?
What's the best way to ensure that a particular VPN user(s) can only access a particular OpenVPN server or network?
-
@ashevillewebhosting
If you set up the servers in SSL mode you should use a different CA on each. So users get their users certs from that CA which is used on their assigned server and are only able to connect to this one.I created another OpenVPN server, set the local networks to match that of the VLAN
This is not safe at all. This only adds routes on the client system. But the client can also add routes on his own.
You have to restrict access by source addresses, since each server use it's separate tunnel subnet. -
Can't you simply create other OpenVPN "servers" on different ports for each "segment" then make a firewall rule to block each off to their own segment?
If you notice the OpenVPN you'll see it'll just increment the ports upward for every one you make. We recently did this to do similar segmenting.
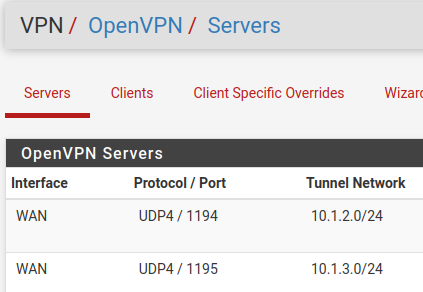
Then under firewall > rules > make a rule to allow them to some services but then deny them from "all" / "any"...
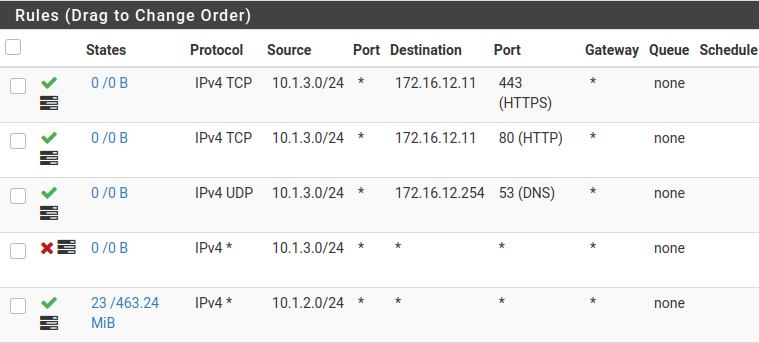
Here we allow them to htps and http plus DNS but then deny them anything else.
I think it is working for us pretty well this way.
Good luck!
-
@ashevillewebhosting said in Segmenting OpenVPN Users:
What's the best way to ensure that a particular VPN user(s) can only access a particular OpenVPN server or network?
I have 3 OVPN "Dial-in" servers , each with their own Root certificate.
All clients must identify via a Certificate signed by the respective OVPN servers Root cert.That way i can control what clients are allowed to what server , and i can also bind the cert to an ip address , making sure that specific clients always gets a specific ip.
/Bingo
-
Thanks all. Just to be clear, here is how I initially set it up (this is being done in a test environment so easy to redo).
In Cert Manager:
- Created a Root CA via Cert Manager.
- Created an Intermediate CA using Root CA as issuer.
In User Manager:
- Create new user + user certificate using Intermediate CA
Using OpenVPN Wizard:
- Select Local DB
- Select Intermediate for CA
- Create new cert for server
- Leave server settings at default, using SSL/TLS + User/Pass for Server Mode
- Create Firewall Rules
- Edit server settings to allow for Client + Intermediate + Server and use Strict User-CN Matching
Using Client Export
- Select desired Remote Access Server
- Export Viscosity Bundle for user.
I followed the same steps again time to create a second OPVN server; this time specifying the Local Network to match that of the VLAN I want the user to have access to.
Regarding Certs: Is using a Root + Intermediate unnecessary? Is creating a new cert for each OPVN server enough, or do I really need to create a new CA for each OPVN server? (I'm not an export on certs so any explanation is appreciated).
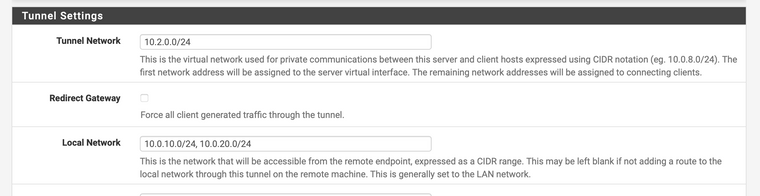
Regarding Routing: So as pictured below, I want users connecting to this server to only access 10.0.10.0/24 and 10.0.20.0/24. But if I understand correctly; setting the local network in the server settings is just pushing the default route via the OPVN config... and can be overridden on the client side? So I'd need to add additional rules limited traffic from the tunnel networks to the VLAN networks as well?
Thanks in advance for the help; hoping to really get a grasp on how OpenVPN works.
-
@ashevillewebhosting said in Segmenting OpenVPN Users:
Regarding Certs: Is using a Root + Intermediate unnecessary? Is creating a new cert for each OPVN server enough, or do I really need to create a new CA for each OPVN server?
No. The users certs are verified against the CA you have set at "Peer Certificate Authority" in the server settings. So these must differ on each server.
Since your first server uses an intermediate cert, you need at least a different intermediate for the second.Regarding Routing: So as pictured below, I want users connecting to this server to only access 10.0.10.0/24 and 10.0.20.0/24. But if I understand correctly; setting the local network in the server settings is just pushing the default route via the OPVN config... and can be overridden on the client side?
Search the web for adding routes to your OS. It's not difficult.
So I'd need to add additional rules limited traffic from the tunnel networks to the VLAN networks as well?
No, you need a proper rule on the OpenVPN interface or OpenVPN tab. The latter one is an interface group indeed.
Users who connect to the vpn server get a virtual IP out of the tunnel network. Since you're are running two servers with different tunnel networks you can use latter to restrict the respective users.
E.g. server1 use 10.2.0.0/24, server2 10.3.0.0/24. So you can add rules to allow the source 10.2.0.0/24 access to VLAN10 and another to allow 10.3.0.0/24 access to VLAN15.
I recommend to add friendly named aliases for the tunnel networks and use these in the rules. -
@viragomann thanks for your response. Just to be clear, here's what I'm taking away from this...
-
I should instead create a new Intermediate CA, as well as a server certificate, that is unique for each OVPN server instance.
-
I need to create a rule on the OpenVPN interface that allows source traffic to the desired VLAN net.
Do I still need to set the Local Network for that server instance? I guess I was assuming that setting the Local Network in the Tunnel Settings was enough to limit access.
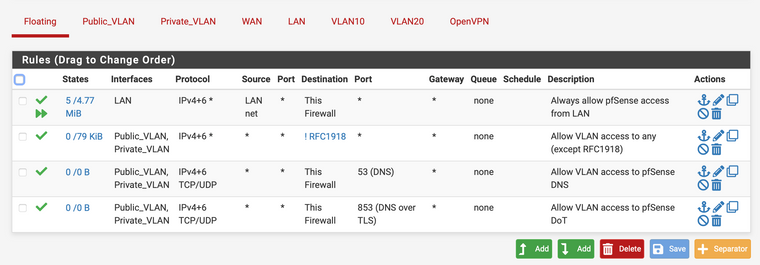
So something like this...
Server 1 Tunnel Settings:
Tunnel Network: 10.1.0.0/24
Local Network: 10.0.10.0/24 (VLAN10)OpenVPN Interface Rule for Server 1:
Source: 10.1.0.0/24
Destination: VLAN10 netI'm using an interface group for VLANs to apply a rule that allows traffic to all except RFC1918 to isolate traffic. This seems to be working, but is that the wrong way to go about it too?
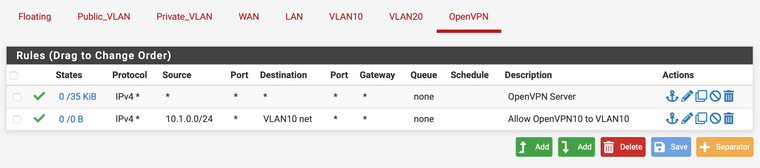
-
-
This post is deleted! -
Just a follow up to this... seems like there are several ways to do this?
Option 1
Setup multiple OpenVPN servers, use new CA for each, remove any allow all rule created on OpenVPN tab and replace with allow rules to restrict traffic by source. For example...- Allow source 10.20.0.0/24 to destination VLAN20 net
- Allow source 10.30.0.0/24 to destination VLAN20 net
Any reason to assign the OpenVPN server interface, or is creating rules under the OpenVPN tab (interface group?) sufficient?
Option 2
Use a single OpenVPN server, and use client specific overrides to segment access as described here: https://docs.netgate.com/pfsense/en/latest/recipes/openvpn-multi-purpose.htmlIs there an advantage to Option 1? Or drawback to Option 2?
-
@ashevillewebhosting said in Segmenting OpenVPN Users:
Any reason to assign the OpenVPN server interface
None I can think of for your purposes.
Is there an advantage to Option 1? Or drawback to Option 2?
Both will fulfil your purposes and if configured properly both are safe.
Setting up CSO for more than a handful clients might be more work than a second server + CA, I think. But since you know both options now, it's on you to choose your favorite. -
@ashevillewebhosting said in Segmenting OpenVPN Users:
Any reason to assign the OpenVPN server interface, or is creating rules under the OpenVPN tab (interface group?) sufficient?
As i have multiple OpenVPN Servers on the same box.
I always assign the OpenVPN server interface , as i think having all OpenVPN rules on the "Master OpenVPN" interface makes a mess.I like to see each of my OpenVPN servers as "A single interface" , makes rule creation similar to my normal interfaces.
/Bingo
-
What I did was:
1 OpenVPN server with /22 subnet
First 512 addresses are dynamically assigned and permitted only to few segments
Next 256 addresses are defined via CCD and have special FW rules
Next 256 addresses are defined via CCD and have also special FW rules
In this way I have full control over all clients on only one VPN server