VLAN and Network Design Help!
-
Hello,
I'm setting up a new pfSense install and looking for some advice on how to best design my network and provide better isolation. If there's a better place for this post, please move and my apologies.
Eample of my basic infrastructure looks like this:
pfSense appliance (10.0.0.1)
Ubiquiti EdgeSwitch (10.0.0.2)
Hyper-V Host (10.0.0.10)
Physical Backup Server(10.0.0.100)Hyper-V configuration:
The Hyper-V host has 2x dual-port NICs, configured in a team. The team adapter is then assigned to the Hyper-V switch. Management OS shares the adapter. VMs on the host use VLAN ID to segment them from the default LAN.psSense configuration:
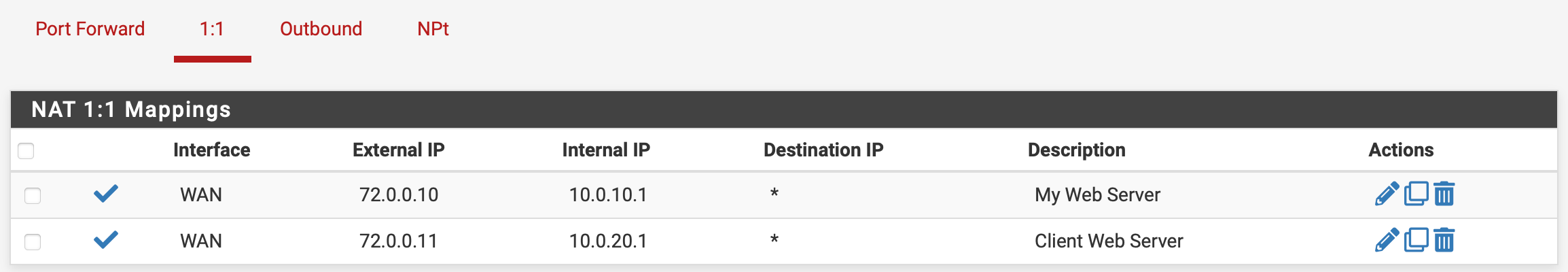
Virtual IPs (/26) via Proxy ARP
Default LAN 10.0.0.0/24 is used for management
VLAN10 (10.0.10.0/24) is used for my web servers
VLAN20 (10.0.20.0/24) is used for client A web servers
VLAN30 (10.0.30.0/24) is used for client A backend serversThe goal:
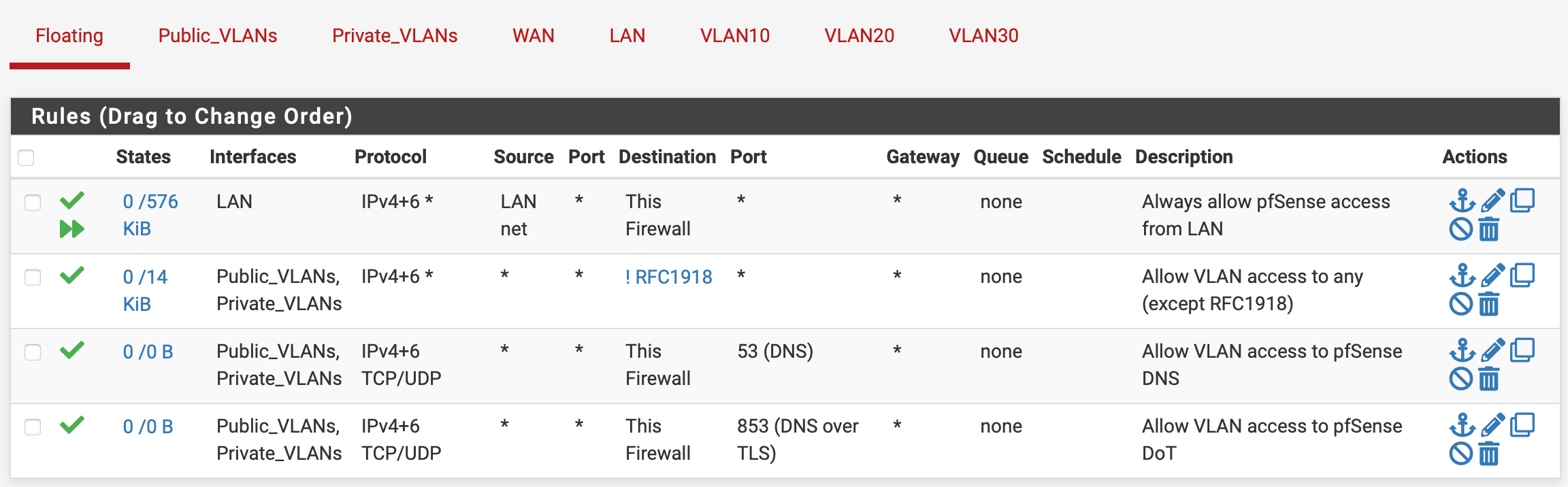
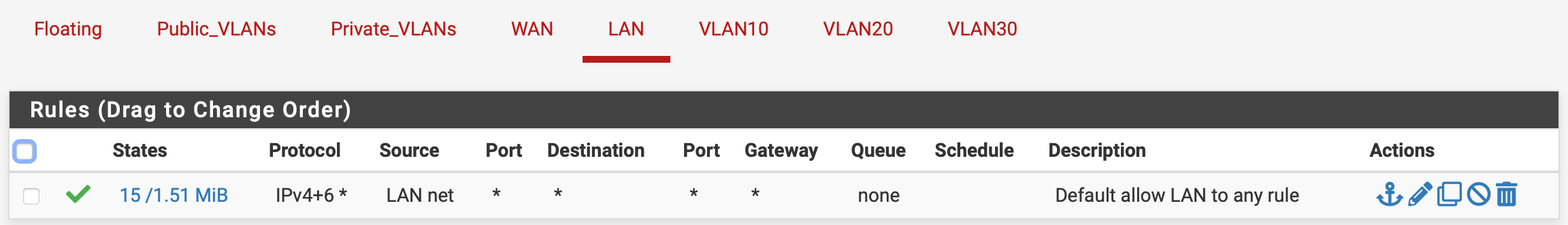
I want to segment my management nodes from my web servers, do the same for client web servers, as well as segment client backend servers like MySQL.LAN Interface: I have a LAN net -> ANY rule, allowing access to the net and all VLANs from the LAN. I suppose it would be more secure to only allow LAN to the internet by default, however, this network is in a data center and only has management nodes connected to it...
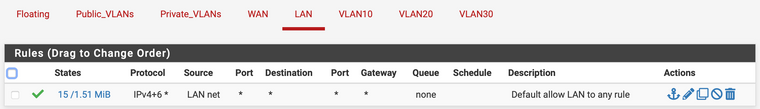
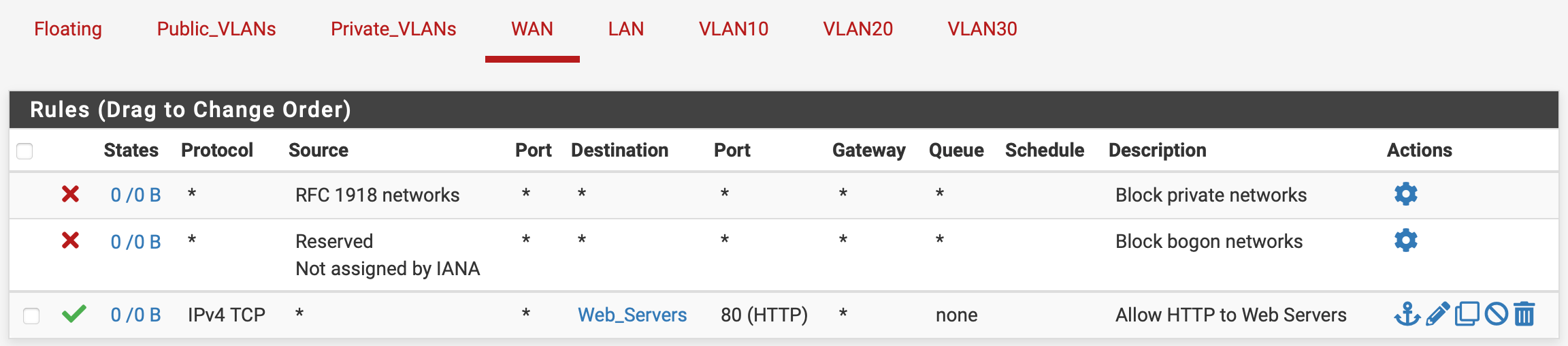
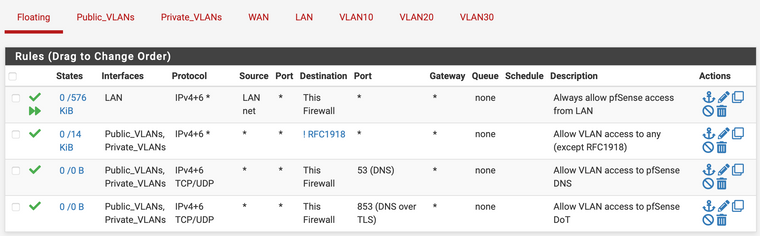
Then I have floating rules applied to a VLAN Interface Group that includes all VLANs, allowing VLANs -> ANY except RFC1918 networks, as well as to pfSense DNS. My thinking is that this should allow VLAN traffic to the web, but deny it access to other VLANs by default...
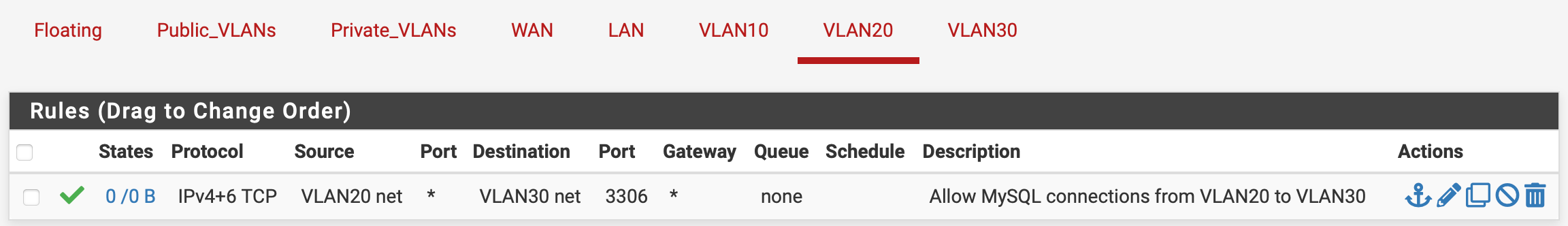
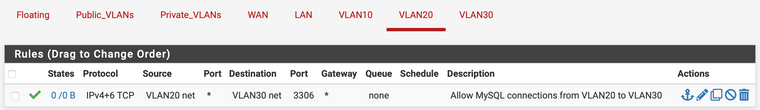
Finally, I have a rule on VLAN20 to allow VLAN20 net over 3306 -> VLAN30 net for MySQL connections...
As for incoming traffic...
Virtual IPs are setup using 1:1 NAT, and then rules defined on WAN to allow traffic as needed...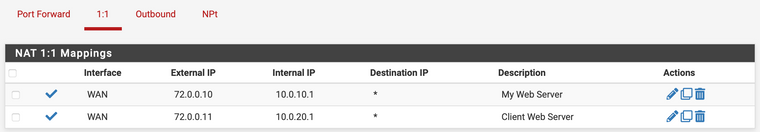
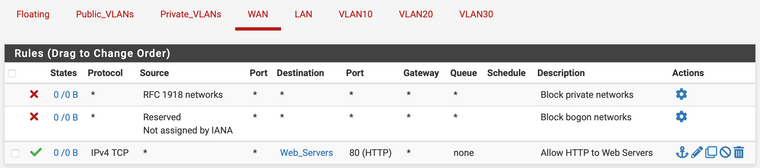
Just to clarify the type of traffic this network will see:
Web Servers are all VMs running Linux/Plesk. Currently, all web servers reside in the same network, but I was thinking I would isolate them per-client using VLANs. However now that I'm thinking about it, if they're all basically the same server type and public facing, maybe that's not really needed and they can just exist on a single VLAN?
I will have a few clients that need isolated backend servers. My thought there was that I'd put those on a per-client private VLAN (like VLAN30 in this example), and route traffic as needed from their web servers like with the MySQL rule above, providing access using OpenVPN servers to their private VLAN network.
Management nodes like pfSense, switches, hyper-v host, would stay on the default LAN, and I would create a separate OpenVPN server to access those remotely.
I would be very appreciative of any wisdom or advice on if I'm approaching this correctly, or if I'm way off. Thank you in advance!!