pfSense 2.5.0 remote to 2.5.1 pfSense server - LAN traffic won't transit
-
New OpenVPN setup. Tunnel is up.
I can ping between: LAN and local VPN GWs (remote and local).
I can not ping remote LAN GW from local LAN GW.This seem like a routing issue to me.
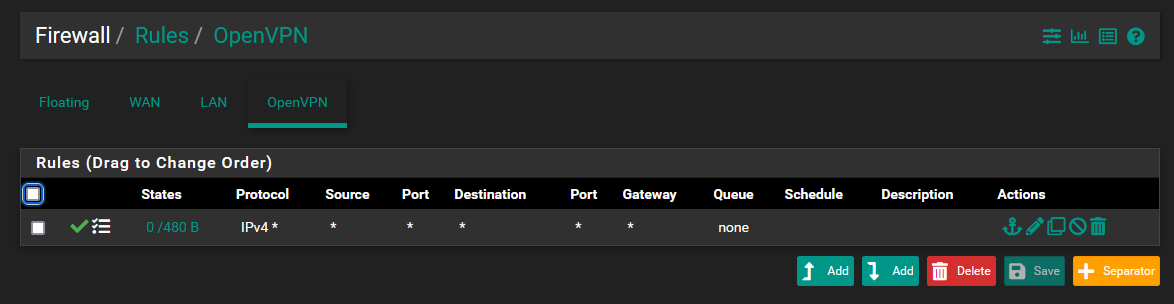
Both sides have an OpenVPN Rule to allow IPv4 * from/to *
Routing on both sides seems correct to me.
Would someone please look over my specs, to spot what I'm doing wrong?
Here is my server config:
dev ovpns2 verb 1 dev-type tun dev-node /dev/tun2 writepid /var/run/openvpn_server2.pid #user nobody #group nobody script-security 3 daemon keepalive 10 60 ping-timer-rem persist-tun persist-key proto udp4 auth SHA256 up /usr/local/sbin/ovpn-linkup down /usr/local/sbin/ovpn-linkdown local 100.100.100.100 tls-server server 10.0.9.0 255.255.255.0 client-config-dir /var/etc/openvpn/server2/csc ifconfig 10.0.9.1 10.0.9.2 tls-verify "/usr/local/sbin/ovpn_auth_verify tls 'example.com' 1" lport 1195 management /var/etc/openvpn/server2/sock unix push "route 192.168.1.0 255.255.255.0" route 192.168.10.0 255.255.255.0 capath /var/etc/openvpn/server2/ca cert /var/etc/openvpn/server2/cert key /var/etc/openvpn/server2/key dh /etc/dh-parameters.2048 tls-auth /var/etc/openvpn/server2/tls-auth 0 data-ciphers AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305:AES-256-CBC data-ciphers-fallback AES-256-CBC allow-compression no persist-remote-ip float topology subnetServer Routes
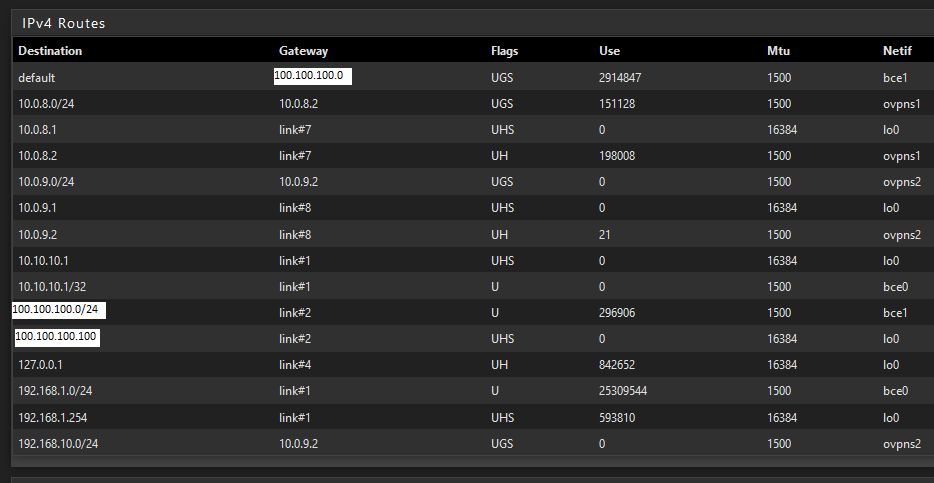
Remote config:
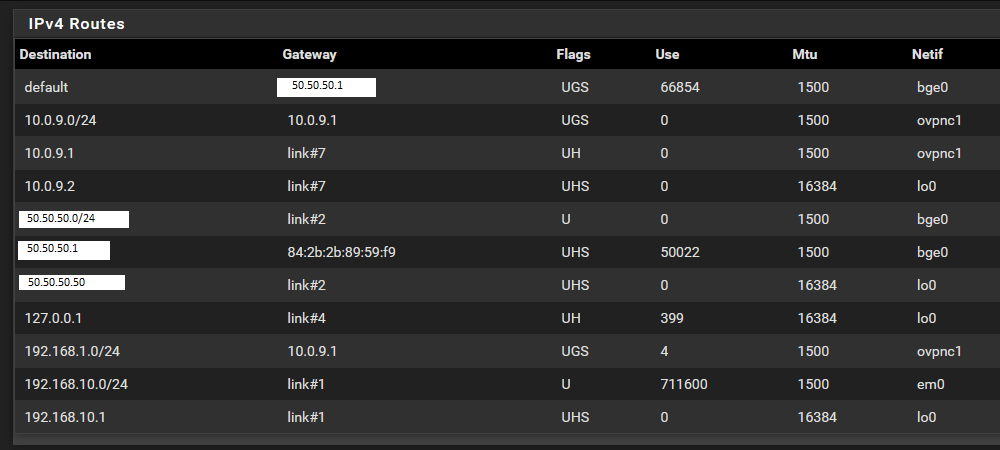
dev ovpnc1 verb 1 dev-type tun dev-node /dev/tun1 writepid /var/run/openvpn_client1.pid #user nobody #group nobody script-security 3 daemon keepalive 10 60 ping-timer-rem persist-tun persist-key proto udp4 auth SHA256 up /usr/local/sbin/ovpn-linkup down /usr/local/sbin/ovpn-linkdown local 50.50.50.50 tls-client client lport 0 management /var/etc/openvpn/client1/sock unix remote 100.100.100.100 1195 udp4 ifconfig 10.0.9.2 10.0.9.1 route 192.168.1.0 255.255.255.0 capath /var/etc/openvpn/client1/ca cert /var/etc/openvpn/client1/cert key /var/etc/openvpn/client1/key tls-auth /var/etc/openvpn/client1/tls-auth 1 ncp-disable cipher AES-256-CBC allow-compression no resolv-retry infinite topology subnetRemote routes:
OpenVPN rules:
Topology:
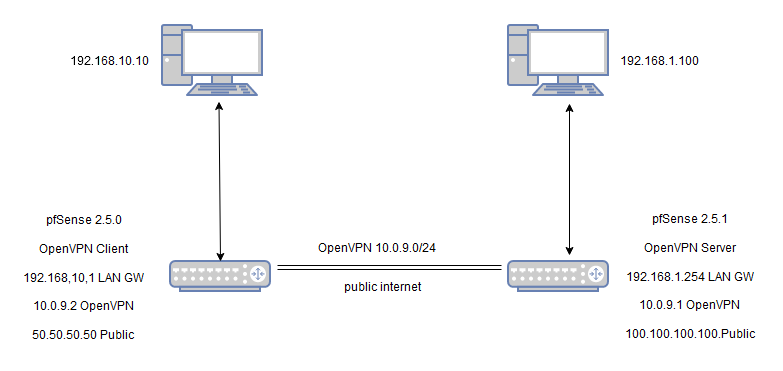
To clarify:
From 192.168.10.1, I can ping 10.0.9.2 and 10.0.9.1 but not 192.168.1.254
From 192.168.1.254, I can ping 10.0.9.1 and 10.0.9.1 but not 192.168.10.1 -
note: Last line should read
From 192.168.1.254, I can ping 10.0.9.1 and 10.0.9.2 but not 192.168.10.1but when I try to correct it, I get
Error Post content was flagged as spam by Akismet.comI also wish I could change the title to:
pfSense 2.5.0 client to 2.5.1 pfSense server - LAN traffic won't transit -
@linuxtracker What does the CSO entry on the server side look like?
Should have an entry matching the CN of the client's certificate with the tunnel NET:10.0.9.0/24 and the client's NET:192.168.10.0/24 -
@divsys You were right. I was missing the Client Specific Override entry.
I created a CSO on the server side, selecting the correct OpenVPN server,
with the Common Name from the client certificate certificate,
my IPv4 Tunnel Network set to 10.0.9.0/24
my IPv4 Local Network/s set to 192.168.1.0/24
my IPv4 Remote Network/s set to 192.168.10.0/24
and my routing fired right up.You are the man.