Need help with firewall rules
-
For all you pros out there this is probably a piece of cake, but I can‘t figure this out:
I have a built in wlan with DHCP running in the 192.168.40.* range and a LAN with DHCP running in the 192.168.20.* range. I need a iPad connected to wlan with IP 192.168.40.101 to be able to access a web GUI running in the LAN network on 192.168.10.5:8088.
Can someone explain to me how set up whatever firewall rule or port forwarding or NAT is needed to make this work. I tried to Figur it out myself by reading the manual and googling, but I guess I’m to dumb to figure this out.Thanks in advance for the help.
-
@macflo1508 said in Need help with firewall rules:
this is probably a piece of cake
Yeah, it's just a simple firewall rule needed. But...
and a LAN with DHCP running in the 192.168.20.* range. ...
...a web GUI running in the LAN network on 192.168.10.5:8088.Now what is your LAN range? Both?
Did you already care that both, client and server, have static IP mappings in the DHCP settings?
-
Yeah with @viragomann is that a typo?
Seems like your lan is 192.168.20, which assume is /24 network? But then you mention something running a web gui on 192.168.10.5?
Are you running a /19?
Which would put your network on lan as?
192.168.0.0 - 192.168.31.255I take it you don't want this wlan to access anything else in the lan?
So for example something like this would work..
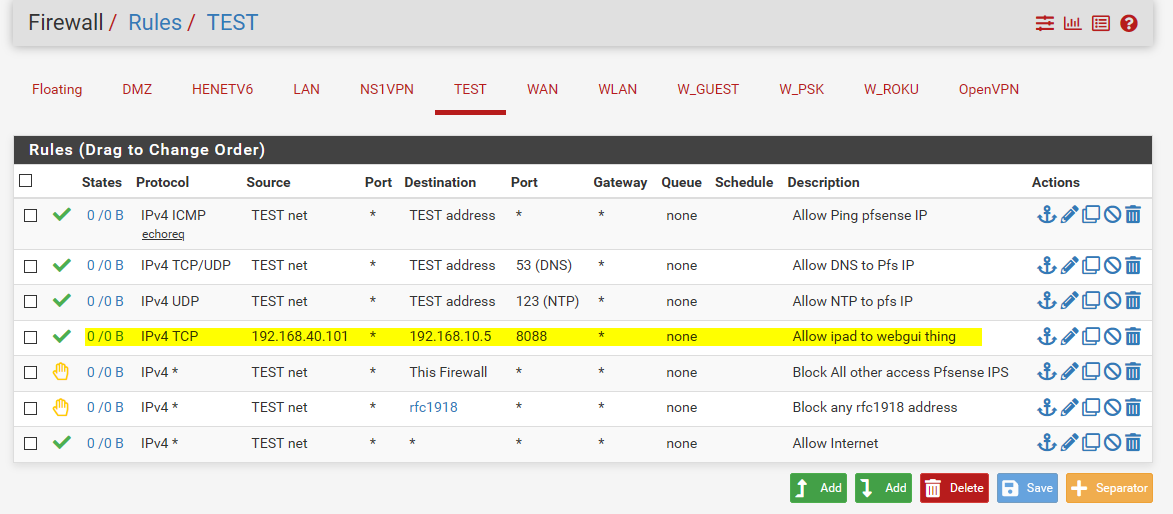
There are a few other rules in there to allow access to dns and ntp on pfsense TEST IP in my example.. This would be your wlan address
And then the 2 rules below that block access to anything else running on the firewall, even the wan IP (to prevent say pfsense webgui access via that IP).. And then the rule with the rfc1918 alias blocks any access to any other vlans you might setup in the future, etc. and would block access to your lan net.
Then the last rule allows access to the internet.
Hope that helps - but should really clarify what is your lan network and what I guess is as typo on the 192.168.10.5 address.
Rules are evaluated top down, first rule to trigger wins, no other rules are evaluated. I have descriptions on this example network I leave setup.. But have any questions ask.
-
@johnpoz
Thank you for the quick help. Sorry; yes that is a typo. The webgui is running at 192.168.20.5
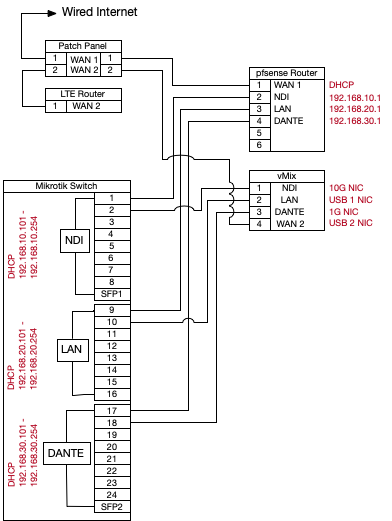
To further clarify: pfsense is running on a hardware with 6 physical ports and wlan. I have a wan on OPT0, a network with DHCP on OPT1 for NDI signals and Internet, a LAN Network on OPT2 for general purpose Internet and LAN and a Network for DANTE on OPT3 that is completely isolated and should just get DHCP service. OPT1 -OPT3 are connected to a 24 port switch running SwitchOS that I enabled port isolation from each other for all 3 network.
OPT1 is 192.168.10.*
OPT2 is 192.168.20*
OPT3 is 192.168.30*
WLAN is 192.168.40*
I need to be able to access a web GUI that is running on a dedicated IP 192.168.20.5:8088 from an iPad, that is connected to WLAn and will get a dynamic IP. I wouldn‘t actually mind if any device on WLAN could connect to devices on LAN. -
@macflo1508 Then show your rules on the interface with 192.168.40.*. It is really easy.
-
@macflo1508 said in Need help with firewall rules:
I wouldn‘t actually mind if any device on WLAN could connect to devices on LAN.
Would really be very interested, what your actual WLAN rule set looks like.
@johnpoz showed you the rule you need for accessing the WebGUI. Only thing to change is the destination address to 192.168.20.5, because of the typo in your first post.
So you need a rule like this:
Interface: WLAN
protocol: TCP
source address: 192.168.40.101
source port: any
destination address: 192.168.20.5
destination port: 8088If you have a rule to block / reject access to other internal subnets you have to put the new rule above of it.
-
@macflo1508 said in Need help with firewall rules:
I enabled port isolation from each other for all 3 network.
What???
So you have vlan capable switch running vlans for those 3 networks? Find to use multiple ulinks.. But they really need to be isolated via vlans on your switch be it pfsense sees tags or not.
Port isolation would be for filtering devices in the same L2 from talking to each other.
-
@johnpoz
No, i didn't configure any vlans on the switch. I i isolated the ports, so it is configured as if they were 3 seperate switches. This was recommended to me because DANTE doesn't like anything else on it's network and NDI on the other hand will always try to load balance if it sees more than one physical connection between to PC's. Might sound a little weird, but it seems to be the only way to keep NDI from using the DANTE Network. -
I'm lost....
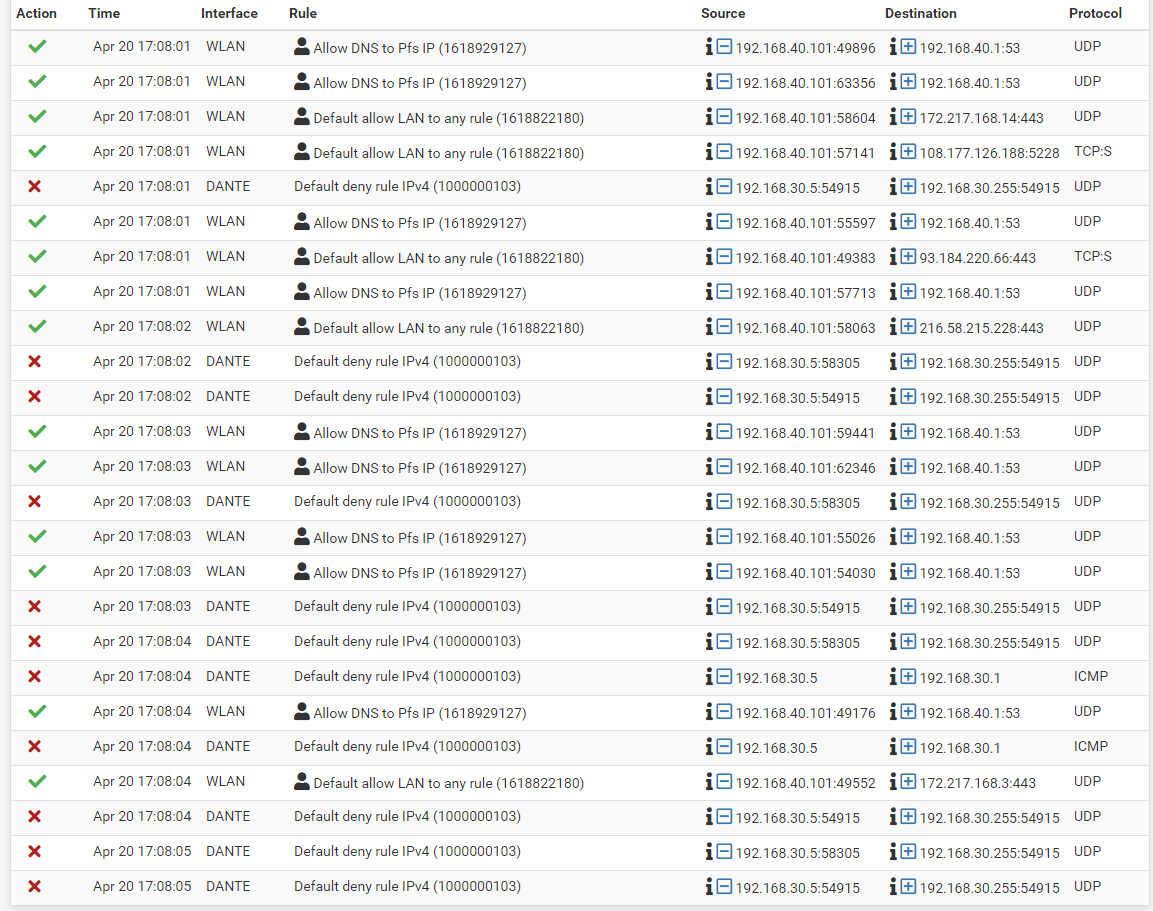
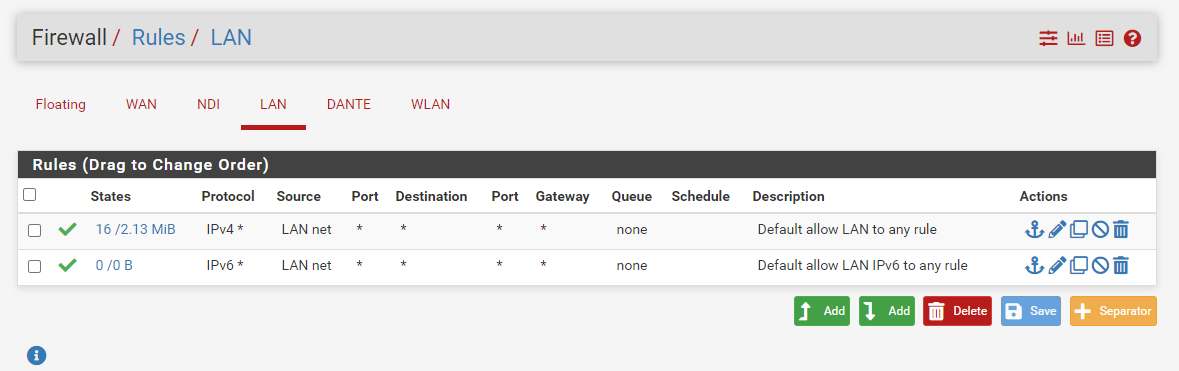
I created the rules as you suggested and it doesn't work. I attached the rules and the log. It looks to me like the log says it passed the traffic, but I get a time out. If I try to connect from a device in the 192.168.20.* range it works fine.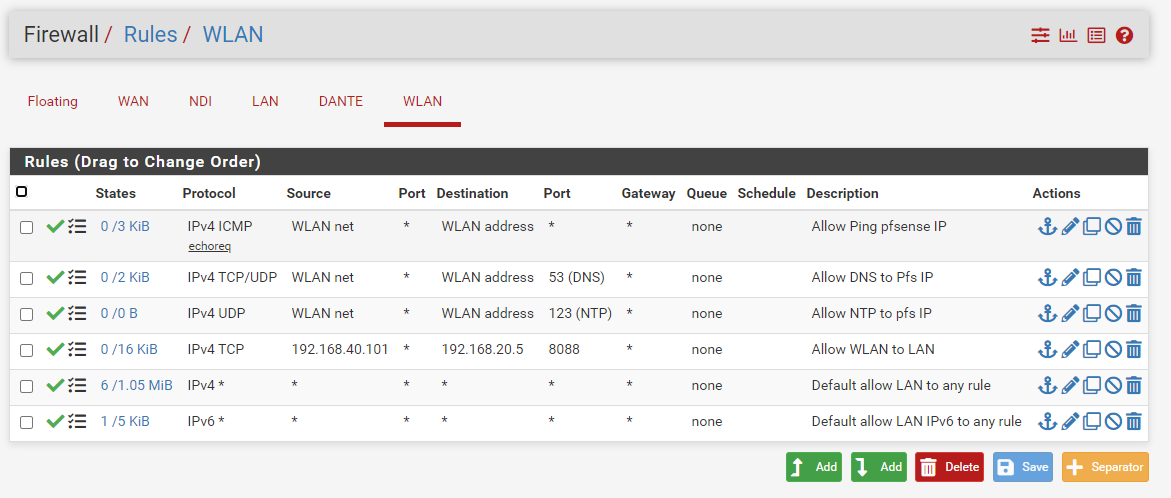
-
@macflo1508
Possibly the destination device blocks the access from other subnets.
If there is a firewall running on the device and you didn't already add any rule to allow the access, this is usually the case.Also consider that your WLAN rules allowe access to any other subnet, since you have copied the default allow rule from LAN.
-
There is nothing in the log you posted for your 8088 port like you stated..
And how you have the rule is completely pointless.. since right below that you have a rule that says any any..
Whatever that is not working has nothing to do with your pfsense rules.
As mentioned - look to your device on lan.. Firewall on it? Not using pfsense for gateway. Not listening on port you think its listening on... I don't see any logs to it on any port. But do see that your rule to port 8088 did get hit for a few KBs of traffic that 0/16 on the rule
But the issue is not firewall rules on wlan that is for sure.All your blocks your showing there are broadcast traffic - so yeah blocked by default, pfsense would never do anything with said traffic anyway. Thee are ways to not have that logged even if you don't like seeing it.
What are you rules on this DANTE interface? You don't allow network to even ping pfsense IP?
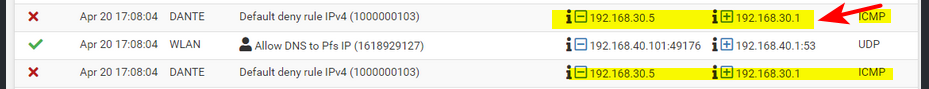
-
@johnpoz @johnpoz Still not working as it should. Since I'm really not a firewall expert, I very likely have some pointless stuff in there.
The "Allow to any" is the default rule from pfsense to let traffic from OPT1 to OPT0.
THe DANTE network doesn't need to do anything outside it's own network, especially no access to internet and it's clock is very delicate. Some people even leave out DHCP and just have fixed IP's and connect the devices to each other through a switch. But DHCP doesn't hurt according to Audinate, so I figured I will give them that. The Dante protocol is for multitrack audio transmission and works with same standards as VOIP.
The receiving device on 192.168.20.5 is a Windows 10 computer, which I also tried to disable the firewall, but it still didn't work.
Here's the updated rules for the DANTE network, which shouldn't have Internet access and no access to any other network: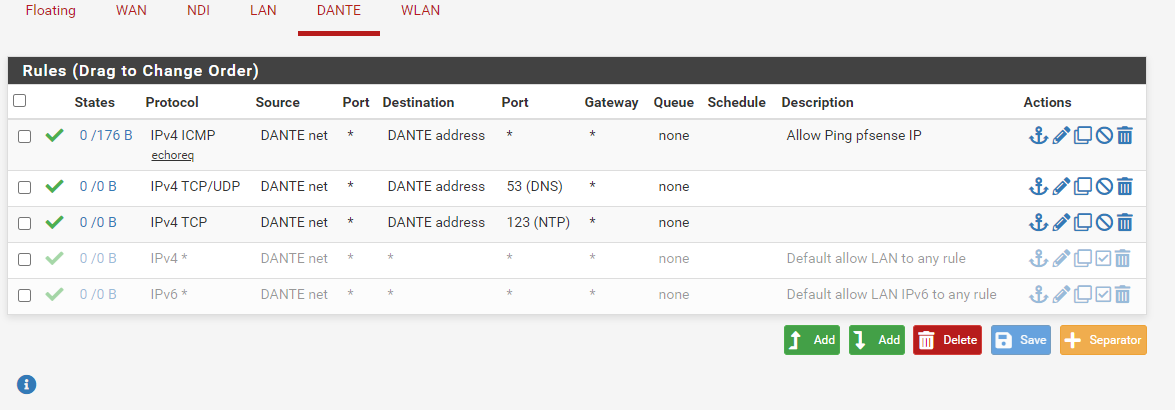
Anybody have an idea on what to do? I'm willing to pay someone for his time if he can fix this via teamviewer.
-
Just to be complete, here are all the rules in pfsense. The IP changed to 192.168.40.102, so I changed the rule accordingly.
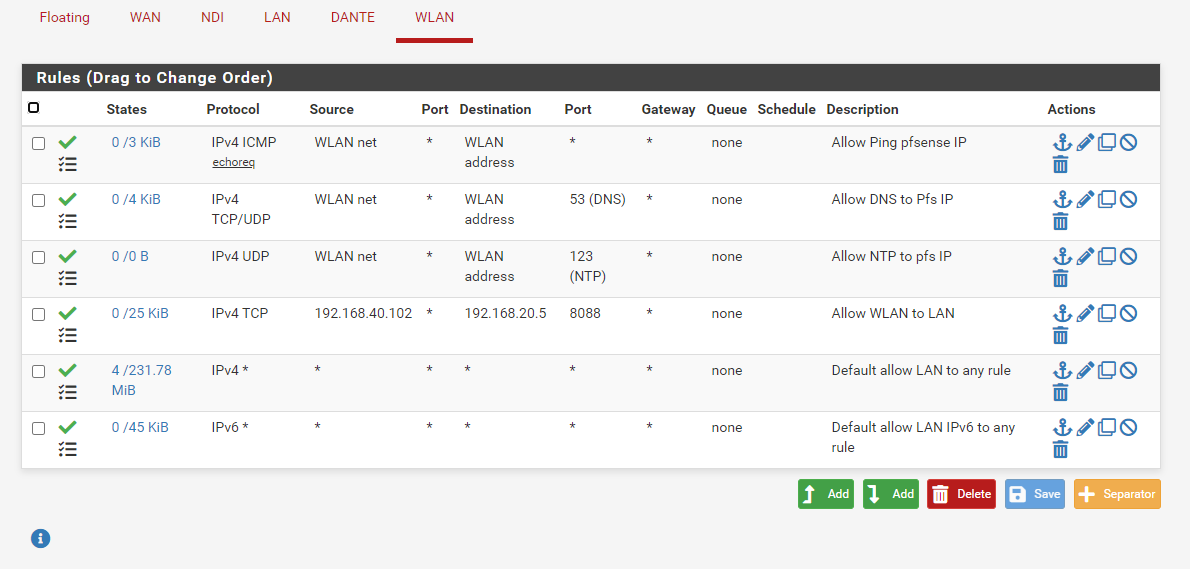
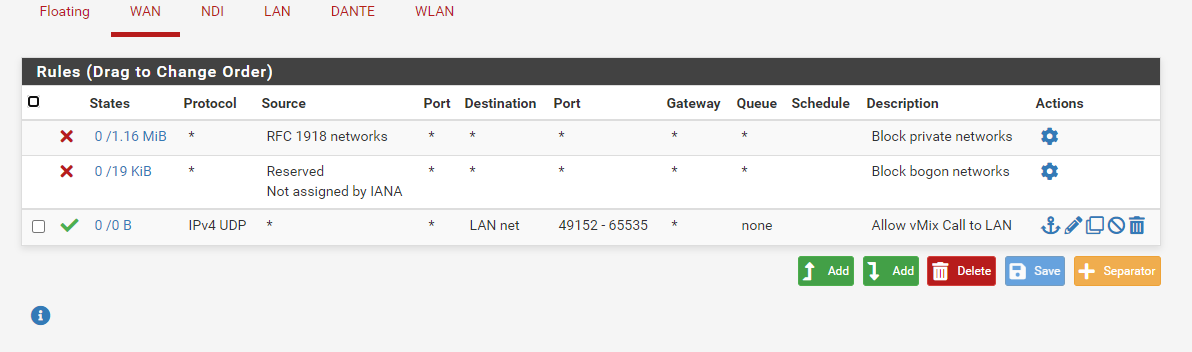
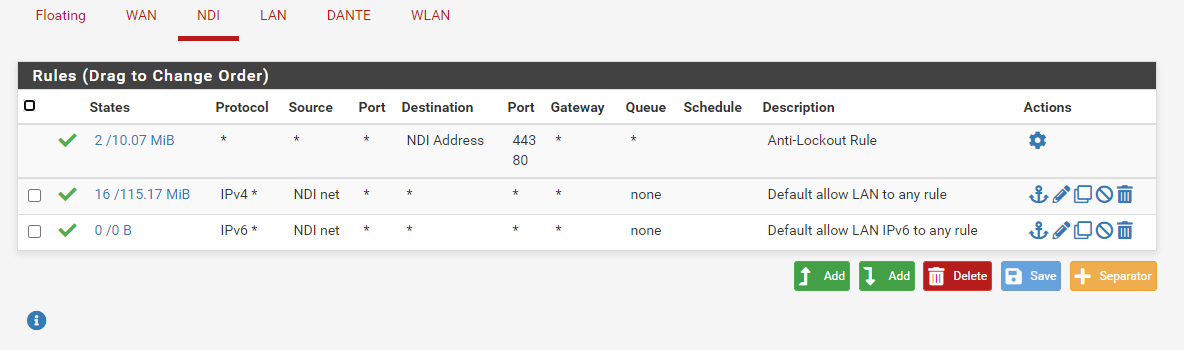
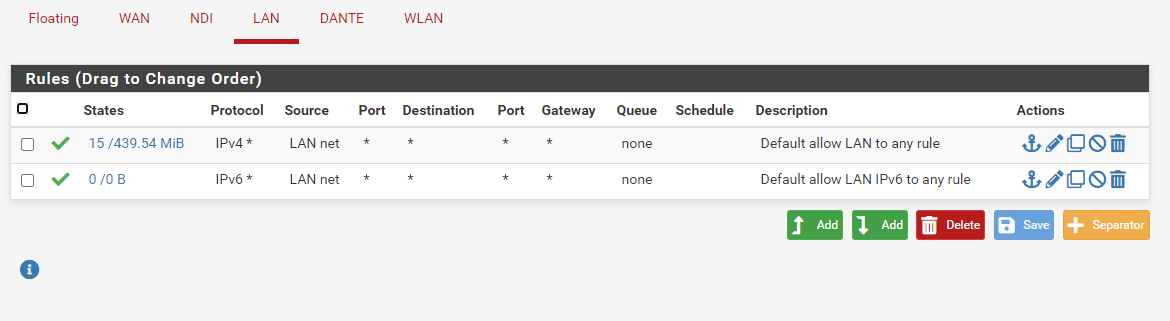
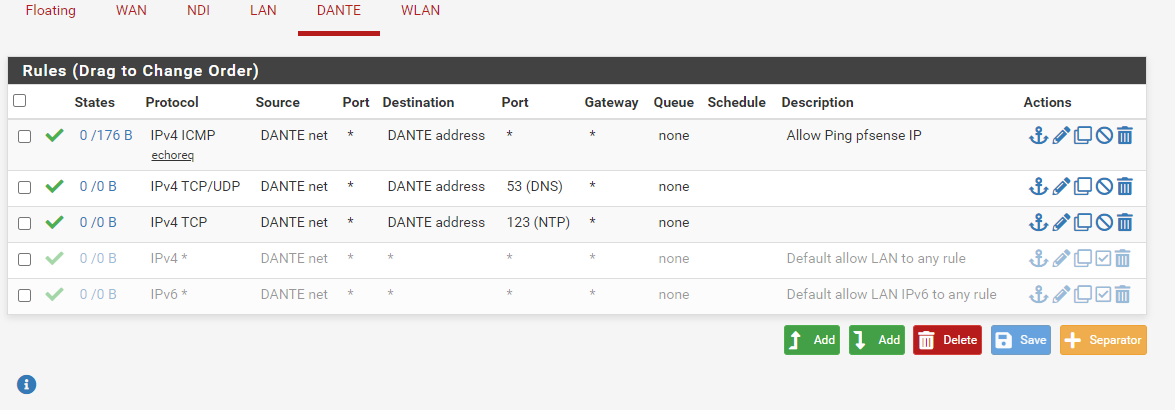
-
Your 8088 rule has no point with those current rules.. Because you have an ANY ANY rule below it..
It serves no purpose. The firewall rules are not your problem with whatever issue your having..
-
And here's the diagram on how it's wired:
-
@johnpoz I wouldn't know where else to look...
Thank's for your patience. You are being very helpful and I appreciate it. -
Well for starters.. Either set that 8088 rule to log so you can actually see traffic that is allowed. Or log all you allowed traffic.
Sniff on pfsense, via the diagnostic menu, packet capture.. Look in your state table.
If you see traffic was sent on to this IP 8080.. And you get no answer, then figure out why. Does the device have a firewall, is it not even listening on 8088? Does it have a different gateway then pfsense, does it have a specific route sending the traffic from that source network to some other gateway?
Looks like to me you have 2 routers, so is where your trying to send traffic even using pfsense as its gateway.
Where is this WLAN on your drawing?
-
@johnpoz Thank's again. You pointed me in the right direction: The Windows machine running at 192.168.20.5 has Speedify installed on it, which resulted in the packages being routed to the wrong place. A NAT rule, saying that anything originating from 192.168.40.0/24 should go to LAN adress solved the issue.
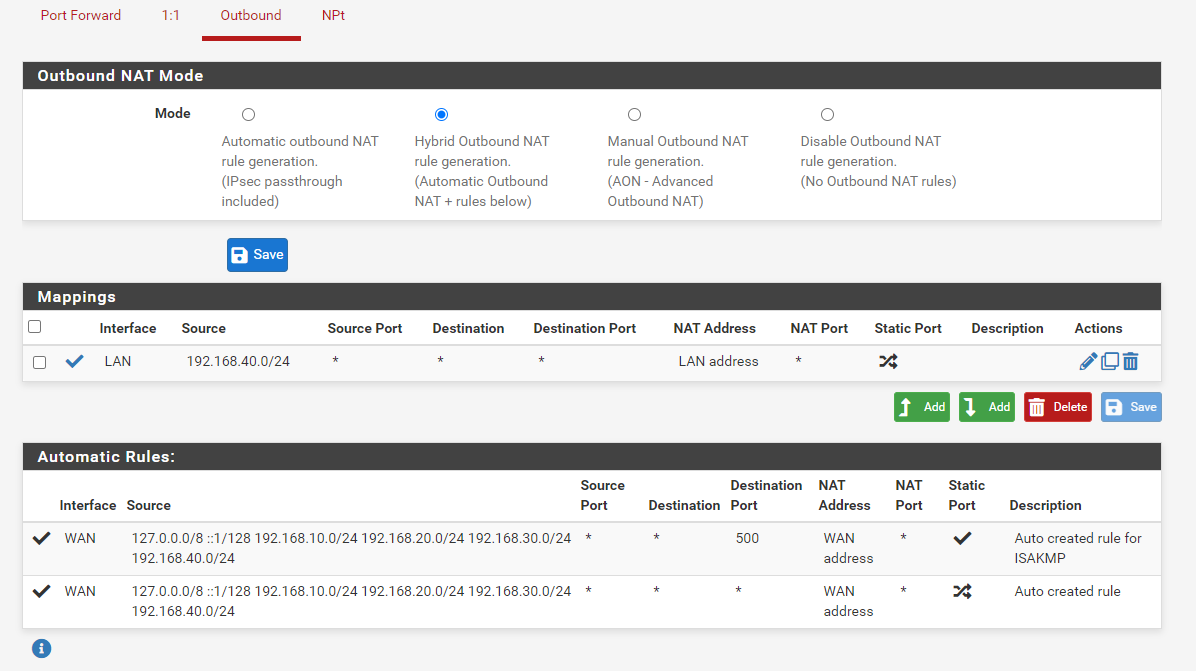
Thank's again everybody for being so helpful with a Noob! Great forum!
-
So you did a source nat from what you posted.
So to lan vs looking like it came from 192.168.40, your source natting it to look like it came from pfsense lan IP.
Not exactly clear on what your doing.. But if you have a vlan of 192.168.40, why would you not just want to route to it, vs natting between 2 rfc1918 networks?
-
@johnpoz That seems to have been the problem. Because of Speedify the receiver didn't know where the packet was sent from, so the packet was routed to WAN.
I don't have a vlan. The 3 networks (LAN, NDI, DANTE) go to the Mikrotik 24 port switch that has port isolation enabled for ports 1-8 (NDI), Ports 9-16 (LAN) and 17-24 (DANTE). This, according to several people that have a lot of experience with DANTE and NDI, is the best way to keep NDI from using the DANTE network.
If this is better practice than creating vlan's, I don't know, but it seems to work the way it should.