So what happens when you IP yourself?
-
Ok let me see if I got this..
Your on your home network IP, laptop is on say 192.168.0.100, 1.2.3.4 is your public..
You setup some dyndns laptop.domainX.tld - which points to 1.2.3.4
Now when you talk to your work (5.6.7.8 public IP) from home, you are coming from 1.2.3.4
You have work firewall that you allow laptop.domainX.tld to access service from internet..
Now you take your laptop into the office and get on the work network, and say get an IP of 192.168.1.100, but your dyndns running on your laptop going to point laptop.domainX.tld to your work public IP 5.6.7.8
So? What does that have to do with anything.. Your on the work laptop, with IP 192.168.1.100, on the LAN side of this firewall.. If you try and access 5.6.7.8 from the lan side you would be coming from 192.168.1.100, and using lan side rules, etc. etc.
Not sure when or how or why laptop.domainX.tld would ever come into play??
-
@johnpoz said in So what happens when you IP yourself?:
Not sure when or how or why laptop.domainX.tld would ever come into play??
Almost, 99% there....
So my concern is not the laptop accessing anything from LAN.What I'm really after is how the firewall interprets outside connections (from anywhere).
After "laptop.domainX.tld" resolves to the office IP (eg 5.6.7.8)
And that becomes part of the firewall NAT rules.Using a single entry in Alias for example.
AliasAllowFTP = laptop.domainX.tld
Firewall WAN Rule = AliasAllowFTP to Port 21After DynDns Resolves laptop.domainX.tld, would be:
AliasAllowFTP = 5.6.7.8
Firewall WAN Rule = AliasAllowFTP to Port 21So in this case the Alias allowing FTP access, now(also) contains IP 5.6.7.8.
Which is the firewall itself.If an external connection comes into Port 21, is there a danger of that connection making it through?
Will PFsense think the connection is coming from itself at anytime and let it pass? -
@jknott said in So what happens when you IP yourself?:
Bringing a laptop, with dyndns will do nothing that the firewall doesn't allow.
That's exactly my concern.
By having DynDNS resolve to the PFsense own external IP.
And letting traffic through -
I'm trying to put this politely, but perhaps you should do some studying on how things work. What you do at one location has absolutely nothing to do with what happens elsewhere. Stop thinking about dyndns, as it has nothing to do with anything. The administrator at the other location will configure the firewall as they desire, to provide the connections they want. All the firewall sees is packets coming to it from whatever address. However, firewalls are much more likely to filter on protocol and destination. That is, if they run a web server on port 80, they will configure the firewall to allow port 80 only to the computer that's running the web server. If you're talking IPv4 and NAT, then port forwarding has to be configured. If they have sufficient addresses, then it's just a matter of allowing the port through to the destination. If you now show up with your computer and plug it in, you will have a different address than that web server and the rules or port forwarding will not be in place to allow connections to it.
Please forget about dyndns, as it has absolutely nothing to do with this.
-
@nz said in So what happens when you IP yourself?:
By having DynDNS resolve to the PFsense own external IP.
And letting traffic throughDoesn't work that way..
-
@jknott said in So what happens when you IP yourself?:
Please forget about dyndns, as it has absolutely nothing to do with this.
Seriously, after all that I explained. That is what your conclusion was.
Putting it politely...you should really read and understand what is being asked.
If you have no clue, it can be made clearer, but don't berate.
Specially when you're way off topic.And Yes it has EVERYTHING to do with Dyndns.
And absolutely nothing to do with NATing from different locations.
Your explanation was for simple firewall NATing.
Which is not what this thread was about. -
Here's what you wrote in your first post:
But one day they decide to come into the office.
The DynDNS client updates to what is now the office IP.
Being the IP of the Firewall.So how does PFsense handle the IP of itself in the firewall rules?
Does that open the door in anyway to other traffic being allowed on that firewall rule, since the firewall IP is being passed to itself?
It's almost a loop onto itself.That you're running dnydns doesn't make a damn bit of difference to what pfsense does. It will do whatever it was configure to do. End of story.
-
@jknott said in So what happens when you IP yourself?:
Here's what you wrote in your first post:
But one day they decide to come into the office.
The DynDNS client updates to what is now the office IP.
Being the IP of the Firewall.So how does PFsense handle the IP of itself in the firewall rules?
Does that open the door in anyway to other traffic being allowed on that firewall rule, since the firewall IP is being passed to itself?
It's almost a loop onto itself.That you're running dnydns doesn't make a damn bit of difference to what pfsense does. It will do whatever it was configure to do. End of story.
Again, you're not getting the point, so what's the point, but ok.
Feels like asking questions on a Microsoft forum.
Sometimes advice is just better unsaid.
But thank you for trying. -
@nz said in So what happens when you IP yourself?:
And Yes it has EVERYTHING to do with Dyndns.
NO IT FREAKING DOESN'T
Make no freaking difference if laptop.domain.tld resolves to the same IP as the pfsense firewall external IP, if your inside the work network.. It DOESN'T
Your not going to have any extra access or blow up pfsense.. Its not going to let some other public IP access these forward, etc..
How would pfsense wan ever see traffic from its own IP to itself.. From some external source? If it did, where would it send the answer - but to itself.
-
I give up!
-
Here's what we do, any external DNS which refers to a corporate internet service is added to a local DNS so when your in an office building you always will resolve locally to local services, the DNS name will never change, only how its resolved.
mydnsname.com -> internet -> internet-DNS -> outside firewall corp -> pass to local service.
mydnsname.com -> inTRAnet -> inTRAnet-DNS -> inside corp -> pass to local service.
(assuming the tcp/udp port used remains the same) -
@NZ :
I have a dyndns - it exists - that I used to contact my NAS :
dig brit.test-domaine.fr +short 82.127.34.254I used this host name with an App in my phone.
I can now access my device from everywhere on the planet.
The host name always to my WAN IP - there is a NAT rule etc etc.When I connect my phone to a local Wifi, an access point n my LAN, my App still works.
My App still uses "brit.test-domaine.fr".
But, because I have control (I admin my pfSense) I can create a host over ride on the Resolver config page, under Host Overrides ::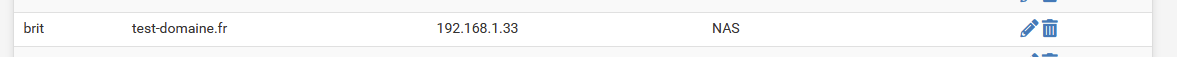
Test on pfSense ::
[2.5.1-RELEASE][root@pfsense.my-network.net]/root: dig brit.test-domaine.fr +short 192.168.1.33and that's correct : my NAS has 192.168.1.33.
So, except for the NAT rule for outside access, no other firewall rules are needed.
For the inside access : a Host Override does the job.