Need help with firewall rules
-
Just to be complete, here are all the rules in pfsense. The IP changed to 192.168.40.102, so I changed the rule accordingly.
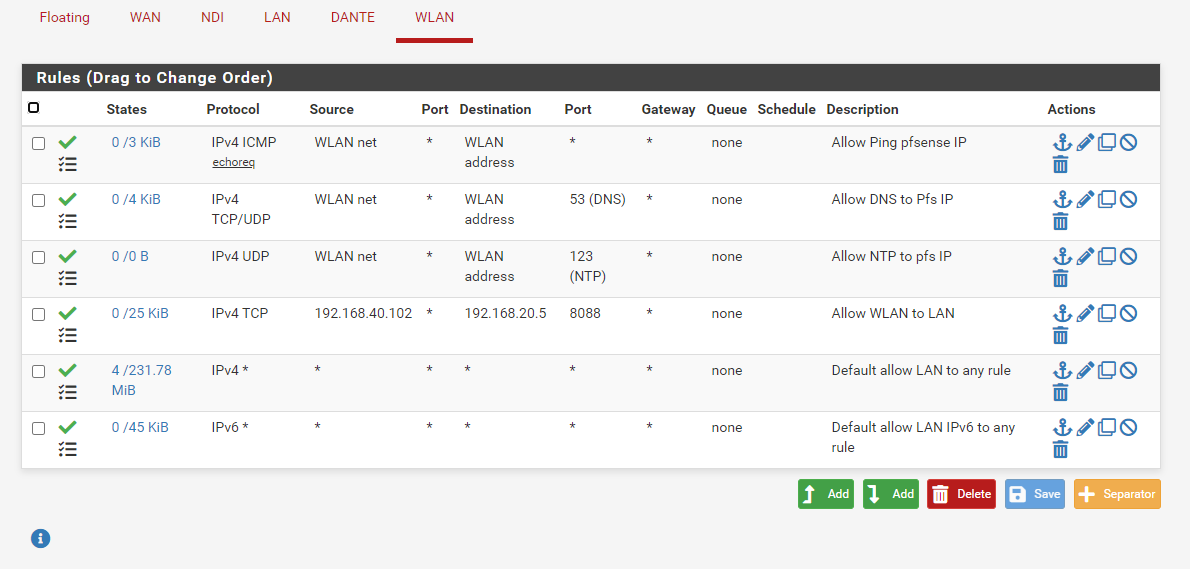
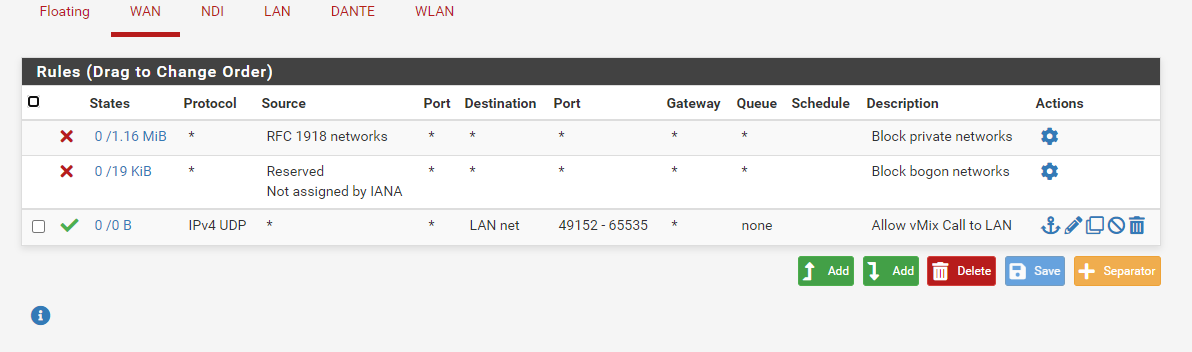
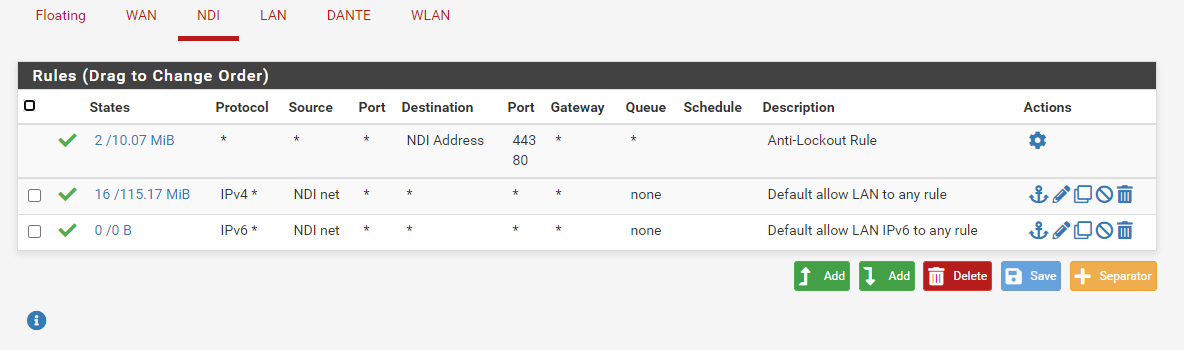
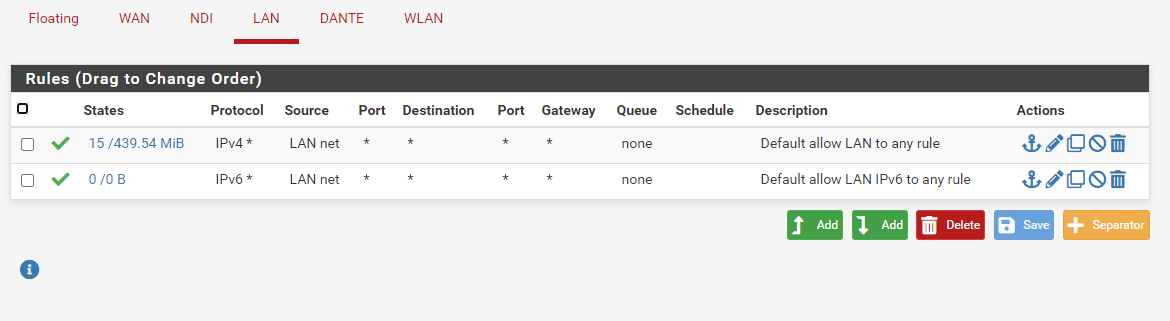
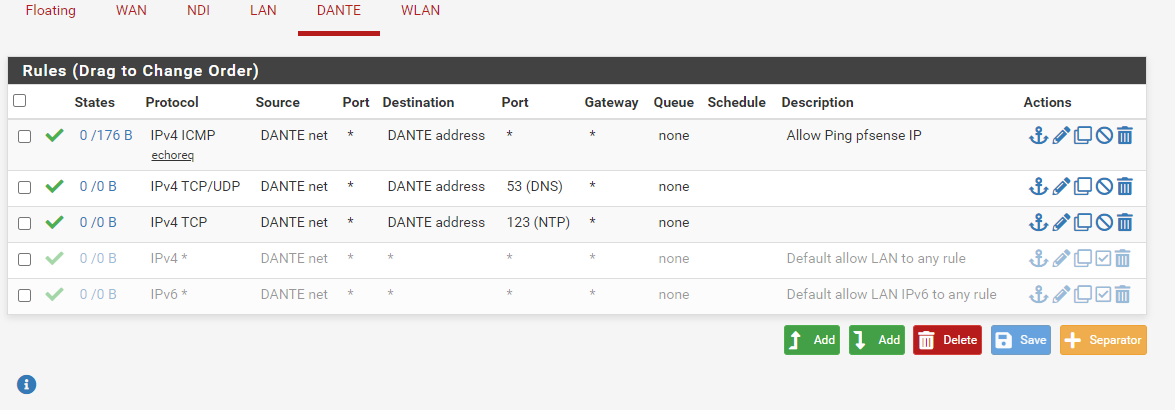
-
Your 8088 rule has no point with those current rules.. Because you have an ANY ANY rule below it..
It serves no purpose. The firewall rules are not your problem with whatever issue your having..
-
And here's the diagram on how it's wired:
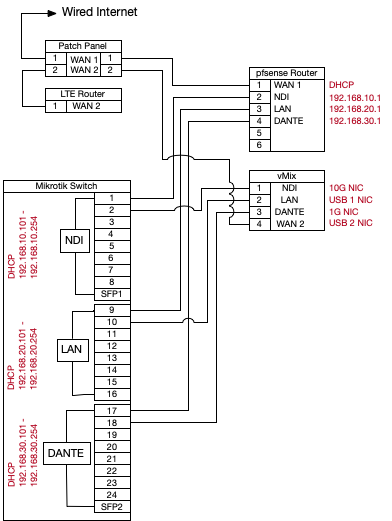
-
@johnpoz I wouldn't know where else to look...
Thank's for your patience. You are being very helpful and I appreciate it. -
Well for starters.. Either set that 8088 rule to log so you can actually see traffic that is allowed. Or log all you allowed traffic.
Sniff on pfsense, via the diagnostic menu, packet capture.. Look in your state table.
If you see traffic was sent on to this IP 8080.. And you get no answer, then figure out why. Does the device have a firewall, is it not even listening on 8088? Does it have a different gateway then pfsense, does it have a specific route sending the traffic from that source network to some other gateway?
Looks like to me you have 2 routers, so is where your trying to send traffic even using pfsense as its gateway.
Where is this WLAN on your drawing?
-
@johnpoz Thank's again. You pointed me in the right direction: The Windows machine running at 192.168.20.5 has Speedify installed on it, which resulted in the packages being routed to the wrong place. A NAT rule, saying that anything originating from 192.168.40.0/24 should go to LAN adress solved the issue.
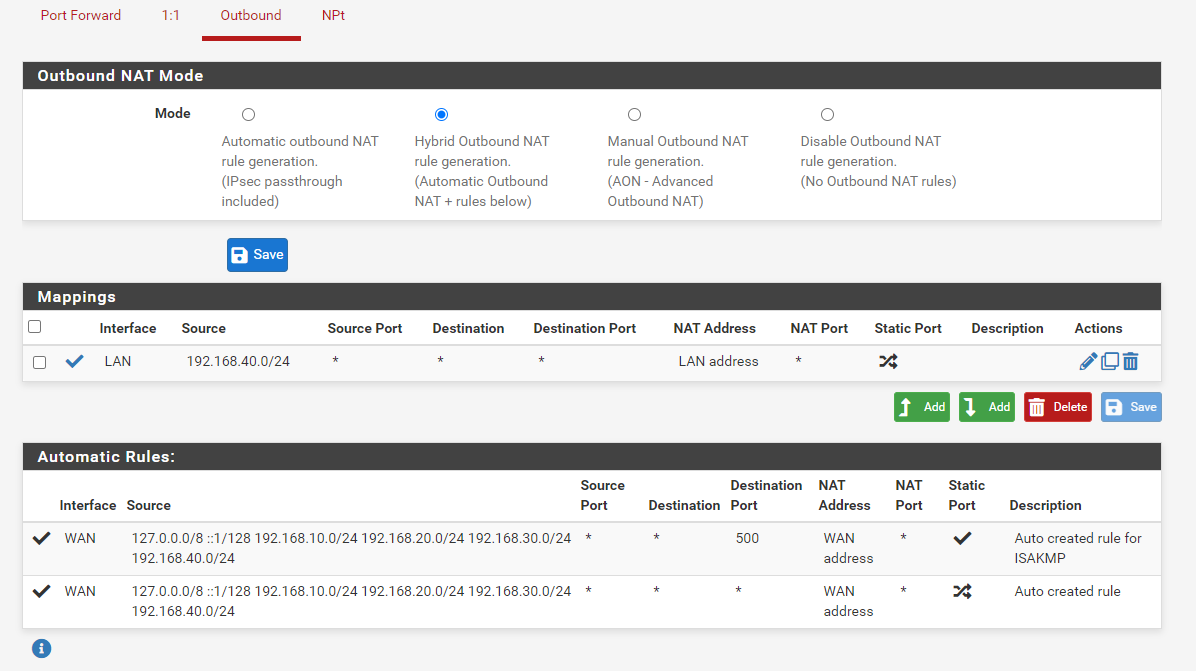
Thank's again everybody for being so helpful with a Noob! Great forum!
-
So you did a source nat from what you posted.
So to lan vs looking like it came from 192.168.40, your source natting it to look like it came from pfsense lan IP.
Not exactly clear on what your doing.. But if you have a vlan of 192.168.40, why would you not just want to route to it, vs natting between 2 rfc1918 networks?
-
@johnpoz That seems to have been the problem. Because of Speedify the receiver didn't know where the packet was sent from, so the packet was routed to WAN.
I don't have a vlan. The 3 networks (LAN, NDI, DANTE) go to the Mikrotik 24 port switch that has port isolation enabled for ports 1-8 (NDI), Ports 9-16 (LAN) and 17-24 (DANTE). This, according to several people that have a lot of experience with DANTE and NDI, is the best way to keep NDI from using the DANTE network.
If this is better practice than creating vlan's, I don't know, but it seems to work the way it should. -
vlan is a interchangeable word with network, be it tagged or not - its a different network. Doesn't really matter if physical and not tagged or just a tagged vlan..
Port isolation - ie your switch virtually isolated layer 2, ie virtual lan ;)
So it doesn't matter if its a vlan or a native network.. Why the need to source nat makes no sense - why are you natting between 2 rfc1918 networks?
So where your sending this traffic has not gateway? That would be the only reason to have to source nat. Or its using a different gateway than pfsense the traffic coming from.
-
@johnpoz My knowledge doesn't go far enough to explain why. I had a friend of mine, that is speciaised in setting up networks with Dante, NDI, etc and that's what he came up with. Since it seems to work fine; I will leave it like this. Although I would like to understand more about this subject, I will have to do some reading first, since my knowledge clearly doesn't go far enough for these types of setup.
Thank's again for the help!