New to openvpn - read the posts -Can't find a solution
-
Hello, I'm coming from the sonicwall world so bare with me, I've setup my pfsense and so far all is good, my nat and firewall rules work and I am able to view my numerous webservers from the outside in, the pfsense is my router and gateway, all my servers and lan stations connect to it and have it's IP as the gateway, I have multiple WAN addresses for my webservers and NAT 1:1 with virtual IP's are assigned and working,
My issue is with openVPN, I've used the wizard and all I am able to do is connect my clients to it, but my clients are unable to use local printers and shares, I am not using the redirect traffic option
Also, on my sonicwall my clients would get an IP from my LAN dhcp server and not from the sonicwall, I have not found this option under pfsense
I've read that I need to use TAP instead of TUN, which I did, but my clients no longer get an IP and stay in limbo waiting
Here's a quick desc :
servers are on 10.1.0.x
switches are on 10.1.1.x (pfsense will be 10.1.1.1)
computers are on 10.1.10.x
printers are on 10.1.4.xin pfsense I added 10.1.0.0/8 under local networks in the tunnel settings
I've read that I also need to add push "route 10.1.0.0 255.255.240.0" in the advanced options, I do see it on my clients but I am still unable to contact any local resources on my lan
I'm at a loss
-
@pjaneiro What are the firewall rules for the VPN? Do you have pass rules to go to the printer computer networks?
-
@jeff3820 Hi ! wouldn't the wizard add the required rules already ?
I've been searching everywhere grabbing some tidbits here and there, but still can't seem to get it right.
What's the point of having a VPN connection if it's not to have access to the internal network you are connecting to ?
Why is this different on pfsense than on other firewalls ? I tried fortinet and right out of the box it's the same as a sonicwall, when you setup a vpn connection you have access to the lan part
what gives ???
-
I don't know how many hours I've spent on this issue, but after seeing soooo many posts having the same issue as I do and having the exact same problem I believe that open vpn is just crap, like how can there so many people having the exact same issue and still not able to get it resolved, I've checked my routes, the config file, i've used the push command, I see my routes being applied on the client side, but I still can't ping or access any lan resources, pinging the pfsense router works, but it stops there
I give up, going back to sonicwall
-
@pjaneiro said in New to openvpn - read the posts -Can't find a solution:
I believe that open vpn is just crap
Not crap. And since march 2020 it became world popular, as half the planet is using it.
There is just one video to see on the Internet to make "it work" : It's from Netgate itself of course.
This one :
is 3 years old, but still very valid.
The next one - the advanced usage is here :
Youtube VideoOpenVPN is not a "click here and there and done". It's probably as complex as is pfSense.
It's open source, so thousands of people have had added 'their' special needs in it.
I advice you also to take a tour on the original openvpn support forum, manual, and FAQ's. -
@gertjan Thanks, but as I've stated, I've read numerous posts, how to's and followed many videos and had help from other people on reddit, using the search on google shows me that sadly I am not the only one having this exact same issue, everything is configured properly, I see my routes being applied on the client side, my rules have been added automatically by the wizard and just to be sure, I also added them manually. problem still persists.
I am only able to ping the pfsense firewall itself and not able to either ping/contact other vpn clients or my lan resources
For the heck of it, I've changed my pfsense lan ip and changed the gateway ip on my lan servers and clients to the new gateway ip, changed my nat and port forwards and everything works from the web side, everything is accessible
OpenVPN will not give me access to my lan resources no matter what I do
The only time I get it going is if i change the IP settings for my lan interface and add itself as the gateway, which then brakes my local lan, but vpn works....euh.....WAAT ?
so yeah, I am frustrated with wasting so much time, I was even thinking in purchasing the support package from netgate but after seeing what kind of service I got for help in choosing what type of hardware they had that would suit my needs I decided against it.
But it all goes back into seeing soo many people with the exact same issue on numerous forums, either all these people are morons like me or there is clearly something broken in OpenVPN
-
if you dont have redirect all traffic then you need to setup the ip ranges that the tunnel has access to under ipv4 local network(s). and then the openvpn interface on your firewall rules should also have access to everything. I just use a source any to any destination. if your still having problems after that, you can also just message me directly and Ill see what I can do to help. its not the easiest to setup but if you do the above steps, it should work exactly like you want. I run tun btw so my vpn clients get their own subnet and then I use firewall rules to restrict it. and are you using dns or ip? its not broken as im using the exact same setup and everything works perfectly.
-
I've given up on TAP for now and just want to get access to my lan resources when connected to vpn
My local LAN setup is like this
servers are on 10.1.0.x
switches are on 10.1.1.x (pfsense is also my router and it's IP is 10.1.1.1)
computers are on 10.1.10.x
printers are on 10.1.4.xright now the only way I got it working vpn side is adding it's own ip as the gateway on the lan interface which makes no sense
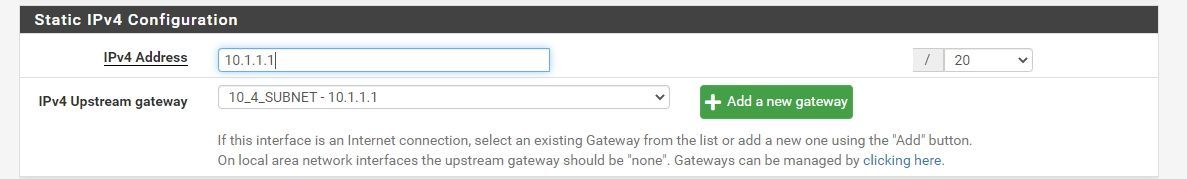
here's the pfsense setup
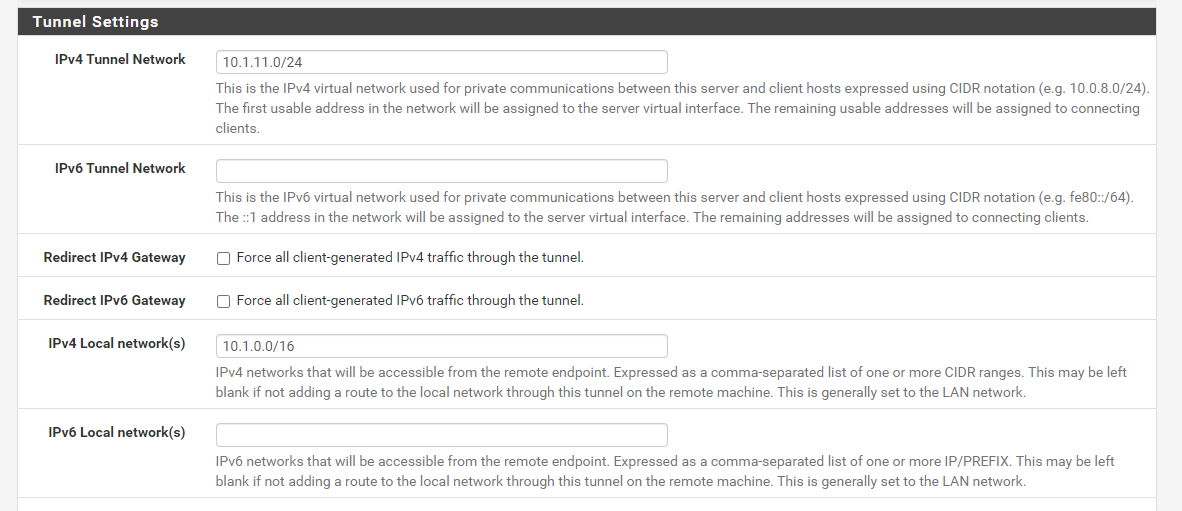
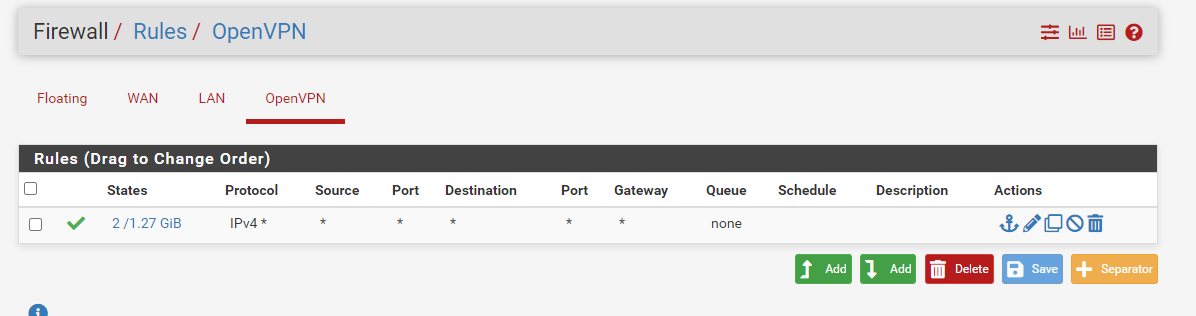
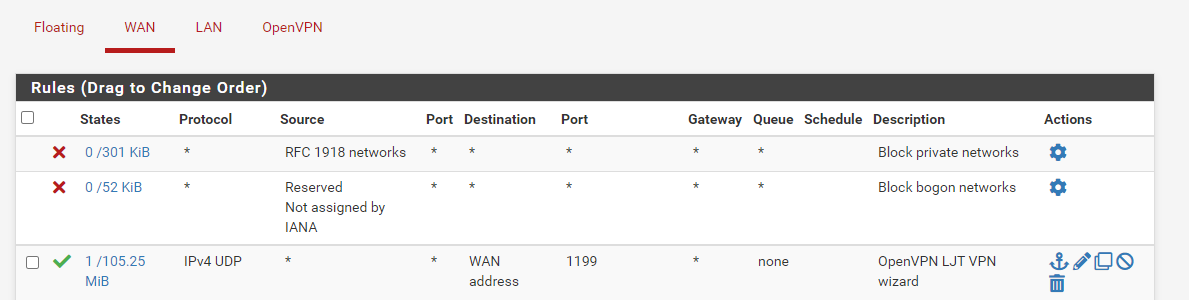
-
@pjaneiro said in New to openvpn - read the posts -Can't find a solution:
But it all goes back into seeing soo many people with the exact same issue on numerous forums, either all these people are morons like me or there is clearly something broken in OpenVPN
My vote goes for Morons. You know why? Because I, like so many other long time pfSense\OpenVPN users started as....you guessed it, Morons. So many pfSense users/admins were familiar with using something else and get frustrated when we can't figure out something new. So I guess the only real morons are the one's that give up and blame the software and not take responsibility for themselves. Yes, networking is HARD. Don't let anyone ever tell you otherwise.
More than likely it is a firewall rule and/or you don't have the IPV4 Remote Network in the OpenVPN Server Configuration.
Typically, in your IPV4 Remote Network of the OpenVPN Server it needs to be whatever you want those clients to be able to hit separated by commas. Looking at what you listed before, if you want OpenVPN clients to see everything it would look like this:
10.1.0.0/8,10.1.1.0/8,10.1.10.0/8.10.1.4.0/8
Keep in mind I'm going with your /8. You do have a /8 network, right? It shouldn't be /24 or something else, right?
I would think your entry under the IPV4 Remote Network of 10.1.0.0/8 would get it. Try putting all of those other networks in there and see what happens.
-
what does a traceroute show? if you can print the routes you get from a client that would be the best. I also suspect openvpn doesnt like using /8 because it doesnt know how to route from multiple interfaces. you probably need to specify it as 10.1.0.0/24, 10.1.10.0/24 and so on. it looks the the firewall is passing the traffic based on your screenshots so now I think we are looking at a routing issue. what does pfsense say for your routing table. does your openvpn show up with a gateway. so mine for example is 10.0.200/28 with a gateway of 10.0.200.2(.2 is my device). also are you using ip address or domain name. if its domain name, you need to make sure you pass your dns server to it as well.
-
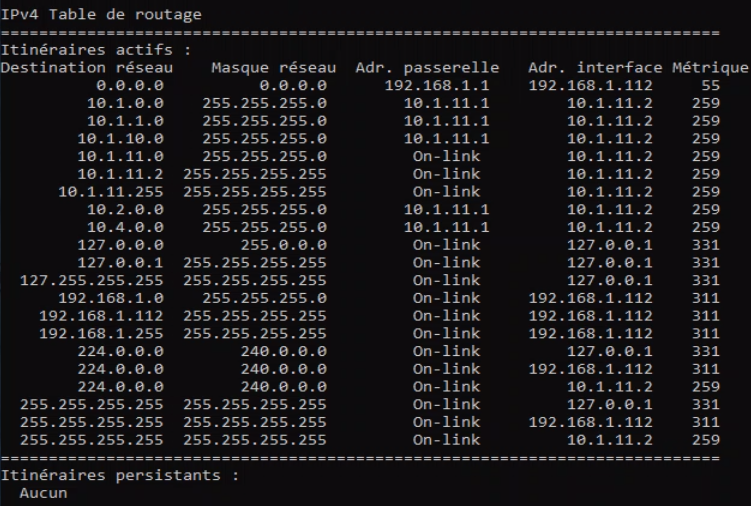
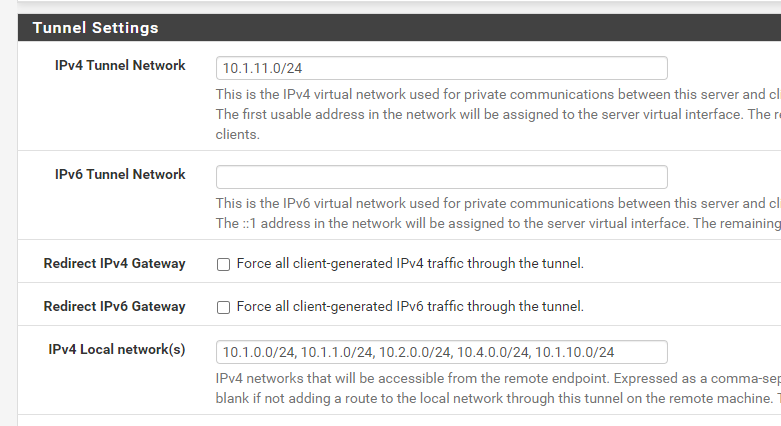
@deboerdn2000 If I try a traceroute it dies at the first step, i can only ping the firewall itself (if i don't add the gateway lan to ) in my gateways it shows all green
I'm getting to the point where I'm thinking of becoming a dishwasher and throw away 25 years of doing this...
I've asked a friend and he's also not experienced with this opensource stuff, but like he says networking is networking, he can't find anything wrong also
instead of having the 10.1.0.0/8 i changed it for separate ones as you mentioned, same thing
here are my routes when i connect openvpn
-
Try this:
- Log into pfSense
- Go to Interfaces-->WAN
- At the bottom, are there checkmarks for Block private networks and loopback addresses and Block bogon networks? If they are, take them out and Save and Apply settings.
- Try pinging something on your LAN.
Note: You may need to reset your firewall states after you make these changes to know for sure if they work. You do this by going to Diagnostics-->States-->Reset States-->Reset the firewall state table (checkbox) and then hit the Reset button. You will lose access to the Internet and pfSense for a few seconds while the states reset,
Lastly, are you testing this stuff over the VPN outside the LAN? Obviously, it's best to test things that way.
-
Yeah, I'm stumped.... I think pfsense is not routing properly, I added a level3 switch in teh mix and changed all my pc's to use that switch ip's as the gateway also added that ip as the lan gateway on pfsense and boom everything works
but obviously i don't want that, i want my pfsense firewall to be the gateway for all the computers
so any ideas ? where i should start to look ?
-
This post is deleted! -
Ok, anyone knows if I were to pay for support netgate would help me on this ?
my LAN dhcp server is assigning adresses from 10.1.10.1 to 10.1.10.255
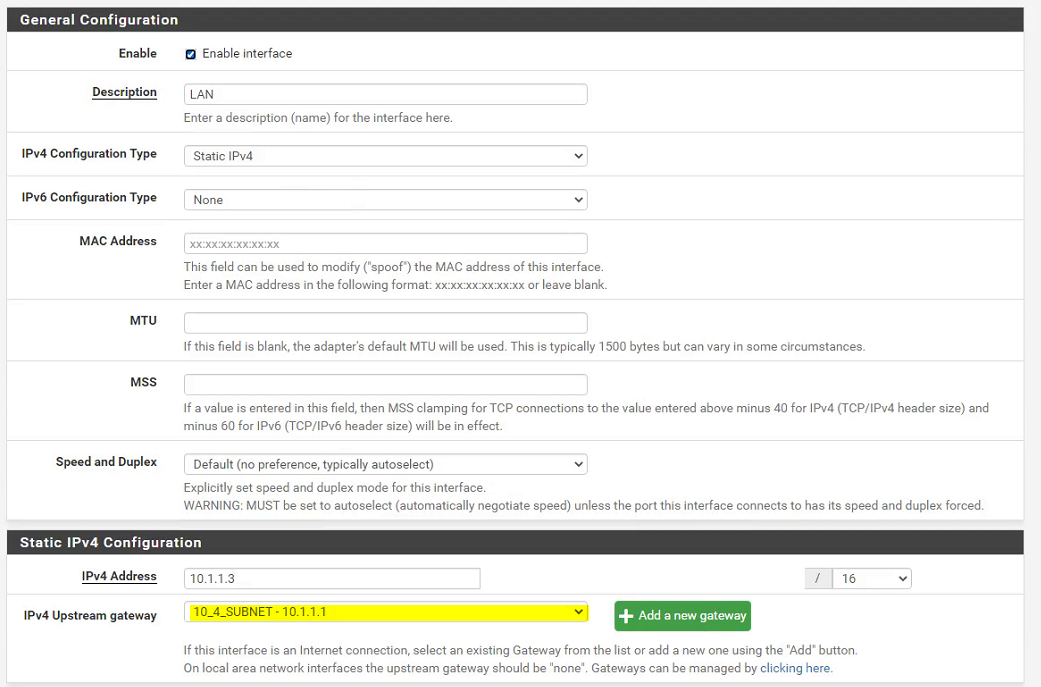
subnet with mask 255.255.0.0 and the gateway 10.1.1.3 (pfsense server)all my lan switches are in the 10.1.1.0 subnet with mask 255.255.0.0 and their gateway is pointing at 10.1.1.3
all my servers are in the 10.1.0.0 subnet and mask 255.255.0.0 and their gateway is pointing at 10.1.1.3
my printers are in the 10.1.4.0 subnet mask 255.255.0.0 and their gateway is pointing at 10.1.1.3
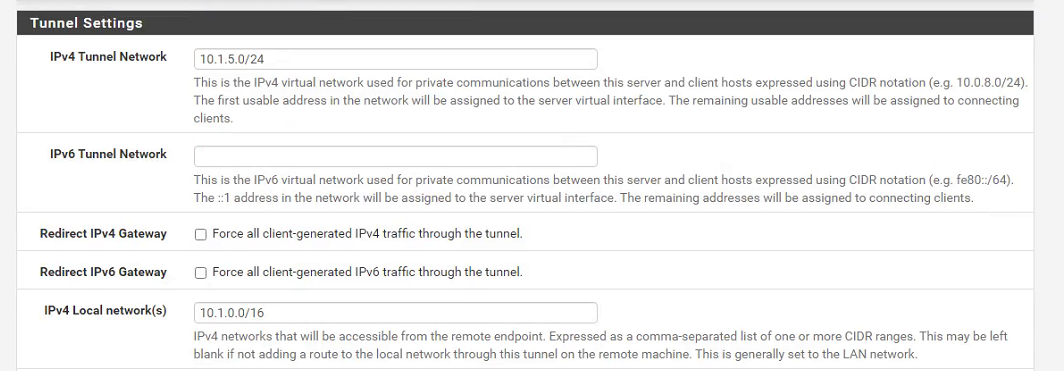
on the openvpn server settings
the ipv4 tunnel network is 10.1.5.0/24 I tried going 10.1.5.0/16 and it would fail to give me an ip adress from the openvpn server
my ipv4 local network(s) is 10.1.0.0/16
as i stated previously, if I don't add a gateway on my pfsense lan adress (10.1.1.1) which is a layer 3 cisco switch I can't connect to my lan ressources from the vpn
I've added more screenshots
In the openvpn status I see the target network being the ip assigned for each user connected, on my sonicwall this would've been my 10.1.0.0/16 network, is this good for openvpn ?
I really would appreciate help on this,