Another different pfSense problem (was "Different WireGuard Problem")
-
Re: A Different WireGuard Problem
I have discovered something very interesting (and troublesome) related to pfSense. I had originally thought it was a WireGuard problem, but now I'm having the same issue using OpenVPN via the same firewall.
I have two pfSense firewalls on two separate public IP addresses. Behind one of them I have a small server running OpenVPN. If I connect an OVPN client to the same LAN behind the server's firewall, everything works well, as expected.
If I connect an OVPN client to the LAN on the other firewall, the initial TLS handshake seems to happen but the tunnel is not instantiated and no traffic flows out to the Internet. This is similar to WireGuard where the initial connection works but then all subsequent traffic goes nowhere.
BUT .... here is the intriguing part .... if I tether that same client to my iPhone over WiFi so traffic goes via my phone's data plan, everything works well.
It seems outbound VPN traffic doesn't make it to the Internet thru pfSense. I should point out that all other traffic is ok. That firewall is my primary Internet connection and everything else works well. Maybe it's the VPN inbound traffic that isn't being allowed.
So .... what could be causing pfSense to not allow VPN traffic (OVPN or WireGuard) to the Internet? Do I need some sort of outbound setting? Currently that firewall is wide open outbound, so it's just a bunch of encrypted packets on a UDP port. The VPN client's inbound port is randomly chosen but that is after the established connection is made.
Any thoughts? Am I doing something stupid?
Thanks in advance, Chuck
-
make sure you set up your outbound NAT if you want to route traffic to the internet via that vpn network.
-
@vajonam said in Another different pfSense problem (was "Different WireGuard Problem"):
make sure you set up your outbound NAT if you want to route traffic to the internet via that vpn network.
Thanks for the reply. In my ignorance I was not aware that this had to be done for a VPN.
I find the Outbound NAT config page to be non-intuitive, so I'm not sure how to correctly set it up.
Detailed settings advice would be very much appreciated .......
OpenVPN clients are on 192.168.10.9/24 using the assigned VPN server's UDP port. Tunnels get IP addresses assigned on subnet 192.168.69.0/24 with randomly chosen UDP return ports.Thanks again!
Chuck -
You need a simple NAT that says for
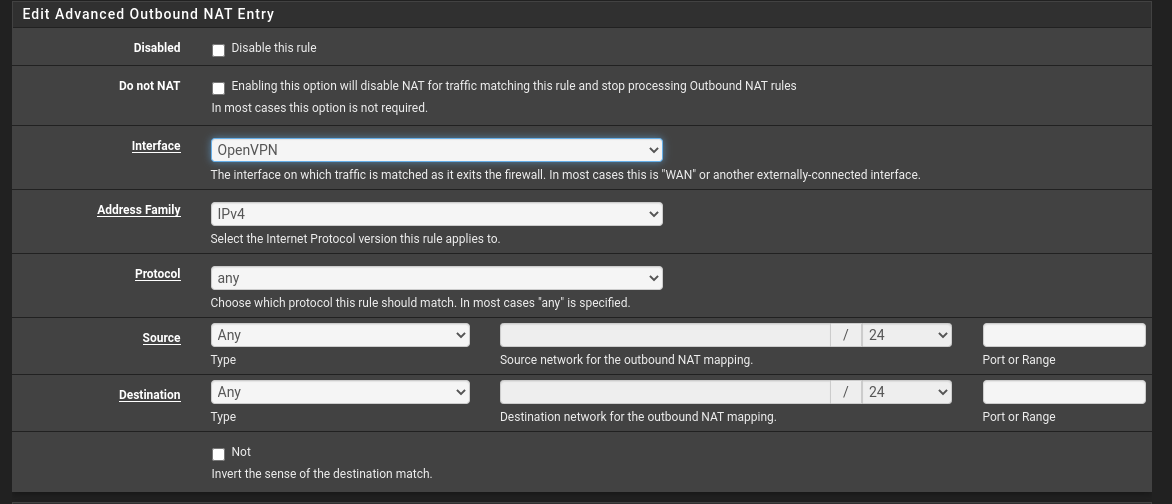
Something like that you can get more restrictitive
Then you will need need to add a firewall rule that says for clients coming in on an interface when reach non local network send out through a specific gateway.
-
Thanks so much for the advice! I was thinking it would be a lot more complex than that :-)
This particular firewall has clients only, the other firewall forwards the OVPN port to its server with no problems.
Another lesson learned, with my appreciation!
Cheers, Chuck