How to disable SSLv3 with Haproxy
-
Hi Sebasb,
Try adding "-servername snihost" on those commands as currently no sni information is send you will end up on the default server every time. Also make sure the backend webserver that is connected over 'mode tcp' properly blocks SSLv3.. As the default bind options for certificates have no use if haproxy doesnt perform the offloading itself.
Are you sure the 'TCPFrontendPort' is forwarded through a backend to the haproxy SSLOffloadingPort ?
Can you share the haproxy.cfg you are using to validate its behavior.?.
Regards,
PiBa-NL -
Hi PiBa,
thank you for your feedback.
I am using TCP mode. The webserver is properly configured to not support SSLv3. When I run sslscan directly on webserver I can see that SSLv3 is properly rejected.
Please find below the complete configuration. I hope it may help to identify where my issue is. Thank you in advance for your help !
global maxconn 50 stats socket /tmp/haproxy.socket level admin uid 80 gid 80 nbproc 1 chroot /tmp/haproxy_chroot daemon tune.ssl.default-dh-param 2048 ssl-default-bind-options no-sslv3 no-tlsv10 ssl-default-bind-ciphers ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!3DES:!MD5:!PSK # Time-to-first-Byte (TTFB) value needs to be optimized based on # the actual public certificate chain see # https://www.igvita.com/2013/10/24 # /optimizing-tls-record-size-and-buffering-latency/ tune.ssl.maxrecord 1370 listen HAProxyLocalStats bind 127.0.0.1:2200 name localstats mode http stats enable stats admin if TRUE stats uri /haproxy/haproxy_stats.php?haproxystats=1 timeout client 5000 timeout connect 5000 timeout server 5000 frontend abc-https-merged bind 192.168.0.223:443 name 192.168.0.223:443 mode tcp log global option socket-stats timeout client 30000 tcp-request inspect-delay 5s acl abc req.ssl_sni -i www.abc.com acl 123 req.ssl_sni -i www.123.com tcp-request content accept if { req.ssl_hello_type 1 } use_backend abc-ki-https_https_ipvANY if abc use_backend abc-ki-https_https_ipvANY if 123 default_backend default-https_https_ipvANY frontend abc-efg-http-merged bind 192.168.0.223:80 name 192.168.0.223:80 mode http log global option socket-stats option http-keep-alive option forwardfor acl https ssl_fc http-request set-header X-Forwarded-Proto http if !https http-request set-header X-Forwarded-Proto https if https timeout client 30000 redirect scheme https code 301 if { hdr(Host) -i www.abc.com } !{ ssl_fc } acl abc hdr(host) -i www.abc.com acl efg hdr(host) -i www.efg.fr acl 456 hdr(host) -i 456.fr acl 123 hdr(host) -i www.123.com use_backend enel-efg-ki-http_http_ipvANY if abc use_backend enel-efg-ki-http_http_ipvANY if efg use_backend 456-http_http_ipvANY if 456 use_backend enel-efg-ki-http_http_ipvANY if 123 default_backend default-http_http_ipvANY backend abc-ki-https_https_ipvANY mode tcp log global balance source timeout connect 30000 timeout server 30000 retries 3 option httpchk OPTIONS / server LINUX01 192.168.153.1:443 check-ssl check inter 60000 verify none backend default-https_https_ipvANY mode tcp log global balance source timeout connect 30000 timeout server 30000 retries 3 option httpchk OPTIONS / server LINUX02 192.168.152.1:443 check-ssl check inter 60000 verify none backend enel-efg-ki-http_http_ipvANY mode http log global balance source timeout connect 30000 timeout server 30000 retries 3 option httpchk OPTIONS / server LINUX01 192.168.153.1:80 check inter 60000 backend 456-http_http_ipvANY mode http log global balance source timeout connect 30000 timeout server 30000 retries 3 option httpchk OPTIONS / server LINUX02 192.168.152.1:80 check inter 60000 backend default-http_http_ipvANY mode http log global timeout connect 30000 timeout server 30000 retries 3 option httpchk OPTIONS / server LINUX02 192.168.152.1:80 check inter 1000Alex
Your setting seems to be the right one.
Ive tried to reproduce your results.. But it seems to block all sslv3 as advertised..You are offloading on haproxy itself? Not passing requests to the backend in tcp mode.?.
I cant tell as the config you show doesn't show the bind on port 443 your testing against..Below my config / results..
[2.3.2-DEVELOPMENT][root@pfSense.localdomain]/root: sslscan --ssl3 192.168.0.133:587 | grep SSLv3 Failed SSLv3 256 bits ECDHE-RSA-AES256-GCM-SHA384 Failed SSLv3 256 bits ECDHE-ECDSA-AES256-GCM-SHA384 Failed SSLv3 256 bits ECDHE-RSA-AES256-SHA384 Failed SSLv3 256 bits ECDHE-ECDSA-AES256-SHA384 Rejected SSLv3 256 bits ECDHE-RSA-AES256-SHA Rejected SSLv3 256 bits ECDHE-ECDSA-AES256-SHA Failed SSLv3 256 bits SRP-DSS-AES-256-CBC-SHA Failed SSLv3 256 bits SRP-RSA-AES-256-CBC-SHA Failed SSLv3 256 bits SRP-AES-256-CBC-SHA Failed SSLv3 256 bits DHE-DSS-AES256-GCM-SHA384 Failed SSLv3 256 bits DHE-RSA-AES256-GCM-SHA384 Failed SSLv3 256 bits DHE-RSA-AES256-SHA256 Failed SSLv3 256 bits DHE-DSS-AES256-SHA256 Rejected SSLv3 256 bits DHE-RSA-AES256-SHA Rejected SSLv3 256 bits DHE-DSS-AES256-SHA Rejected SSLv3 256 bits DHE-RSA-CAMELLIA256-SHA Rejected SSLv3 256 bits DHE-DSS-CAMELLIA256-SHA Rejected SSLv3 256 bits AECDH-AES256-SHA Failed SSLv3 256 bits ADH-AES256-GCM-SHA384 Failed SSLv3 256 bits ADH-AES256-SHA256 Rejected SSLv3 256 bits ADH-AES256-SHA Rejected SSLv3 256 bits ADH-CAMELLIA256-SHA Failed SSLv3 256 bits ECDH-RSA-AES256-GCM-SHA384 Failed SSLv3 256 bits ECDH-ECDSA-AES256-GCM-SHA384 Failed SSLv3 256 bits ECDH-RSA-AES256-SHA384 Failed SSLv3 256 bits ECDH-ECDSA-AES256-SHA384 Rejected SSLv3 256 bits ECDH-RSA-AES256-SHA Rejected SSLv3 256 bits ECDH-ECDSA-AES256-SHA Failed SSLv3 256 bits AES256-GCM-SHA384 Failed SSLv3 256 bits AES256-SHA256 Rejected SSLv3 256 bits AES256-SHA Rejected SSLv3 256 bits CAMELLIA256-SHA Failed SSLv3 256 bits PSK-AES256-CBC-SHA Failed SSLv3 128 bits ECDHE-RSA-AES128-GCM-SHA256 Failed SSLv3 128 bits ECDHE-ECDSA-AES128-GCM-SHA256 Failed SSLv3 128 bits ECDHE-RSA-AES128-SHA256 Failed SSLv3 128 bits ECDHE-ECDSA-AES128-SHA256 Rejected SSLv3 128 bits ECDHE-RSA-AES128-SHA Rejected SSLv3 128 bits ECDHE-ECDSA-AES128-SHA Failed SSLv3 128 bits SRP-DSS-AES-128-CBC-SHA Failed SSLv3 128 bits SRP-RSA-AES-128-CBC-SHA Failed SSLv3 128 bits SRP-AES-128-CBC-SHA Failed SSLv3 128 bits DHE-DSS-AES128-GCM-SHA256 Failed SSLv3 128 bits DHE-RSA-AES128-GCM-SHA256 Failed SSLv3 128 bits DHE-RSA-AES128-SHA256 Failed SSLv3 128 bits DHE-DSS-AES128-SHA256 Rejected SSLv3 128 bits DHE-RSA-AES128-SHA Rejected SSLv3 128 bits DHE-DSS-AES128-SHA Rejected SSLv3 128 bits DHE-RSA-SEED-SHA Rejected SSLv3 128 bits DHE-DSS-SEED-SHA Rejected SSLv3 128 bits DHE-RSA-CAMELLIA128-SHA Rejected SSLv3 128 bits DHE-DSS-CAMELLIA128-SHA Rejected SSLv3 128 bits AECDH-AES128-SHA Failed SSLv3 128 bits ADH-AES128-GCM-SHA256 Failed SSLv3 128 bits ADH-AES128-SHA256 Rejected SSLv3 128 bits ADH-AES128-SHA Rejected SSLv3 128 bits ADH-SEED-SHA Rejected SSLv3 128 bits ADH-CAMELLIA128-SHA Failed SSLv3 128 bits ECDH-RSA-AES128-GCM-SHA256 Failed SSLv3 128 bits ECDH-ECDSA-AES128-GCM-SHA256 Failed SSLv3 128 bits ECDH-RSA-AES128-SHA256 Failed SSLv3 128 bits ECDH-ECDSA-AES128-SHA256 Rejected SSLv3 128 bits ECDH-RSA-AES128-SHA Rejected SSLv3 128 bits ECDH-ECDSA-AES128-SHA Failed SSLv3 128 bits AES128-GCM-SHA256 Failed SSLv3 128 bits AES128-SHA256 Rejected SSLv3 128 bits AES128-SHA Rejected SSLv3 128 bits SEED-SHA Rejected SSLv3 128 bits CAMELLIA128-SHA Rejected SSLv3 128 bits IDEA-CBC-SHA Failed SSLv3 128 bits PSK-AES128-CBC-SHA Rejected SSLv3 128 bits ECDHE-RSA-RC4-SHA Rejected SSLv3 128 bits ECDHE-ECDSA-RC4-SHA Rejected SSLv3 128 bits AECDH-RC4-SHA Rejected SSLv3 128 bits ADH-RC4-MD5 Rejected SSLv3 128 bits ECDH-RSA-RC4-SHA Rejected SSLv3 128 bits ECDH-ECDSA-RC4-SHA Rejected SSLv3 128 bits RC4-SHA Rejected SSLv3 128 bits RC4-MD5 Failed SSLv3 128 bits PSK-RC4-SHA Rejected SSLv3 112 bits ECDHE-RSA-DES-CBC3-SHA Rejected SSLv3 112 bits ECDHE-ECDSA-DES-CBC3-SHA Failed SSLv3 112 bits SRP-DSS-3DES-EDE-CBC-SHA Failed SSLv3 112 bits SRP-RSA-3DES-EDE-CBC-SHA Failed SSLv3 112 bits SRP-3DES-EDE-CBC-SHA Rejected SSLv3 112 bits EDH-RSA-DES-CBC3-SHA Rejected SSLv3 112 bits EDH-DSS-DES-CBC3-SHA Rejected SSLv3 112 bits AECDH-DES-CBC3-SHA Rejected SSLv3 112 bits ADH-DES-CBC3-SHA Rejected SSLv3 112 bits ECDH-RSA-DES-CBC3-SHA Rejected SSLv3 112 bits ECDH-ECDSA-DES-CBC3-SHA Rejected SSLv3 112 bits DES-CBC3-SHA Failed SSLv3 112 bits PSK-3DES-EDE-CBC-SHA Rejected SSLv3 0 bits ECDHE-RSA-NULL-SHA Rejected SSLv3 0 bits ECDHE-ECDSA-NULL-SHA Rejected SSLv3 0 bits AECDH-NULL-SHA Rejected SSLv3 0 bits ECDH-RSA-NULL-SHA Rejected SSLv3 0 bits ECDH-ECDSA-NULL-SHA Failed SSLv3 0 bits NULL-SHA256 Rejected SSLv3 0 bits NULL-SHA Rejected SSLv3 0 bits NULL-MD5And config:
global maxconn 504 log 192.168.0.40 local0 info stats socket /tmp/haproxy.socket level admin gid 80 nbproc 1 chroot /tmp/haproxy_chroot daemon tune.ssl.default-dh-param 1024 log-send-hostname ItsMe lua-load /var/etc/haproxy/luascript_acmeclient ssl-default-bind-options no-sslv3 no-tlsv10 ssl-default-bind-ciphers ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!3DES:!MD5:!PSK # Time-to-first-Byte (TTFB) value needs to be optimized based on # the actual public certificate chain see # https://www.igvita.com/2013/10/24 # /optimizing-tls-record-size-and-buffering-latency/ tune.ssl.maxrecord 1370 listen HAProxyLocalStats bind 127.0.0.1:2200 name localstats mode http stats enable stats refresh 5 stats admin if TRUE stats uri /haproxy/haproxy_stats.php?haproxystats=1 timeout client 5000 timeout connect 5000 timeout server 5000 mailers globalmailers mailer EX 192.168.0.40:25 frontend SMTP-tls-test bind 192.168.0.133:587 name 192.168.0.133:587 ssl crt /var/etc/haproxy/SMTP-tls-test.pem mode tcp log global timeout client 30000 default_backend pb3-smtp_https_ipvANY backend pb3-smtp_https_ipvANY mode tcp log global # use mailers # level debug email-alert mailers globalmailers email-alert level debug email-alert from me@me.tld email-alert to you@you.tld email-alert myhostname HAPmailer timeout connect 30000 timeout server 30000 retries 3 server pb3-smtp 192.168.0.40:25 check inter 1000 weight 1 -
Hi Alex,
As you don't have any certificate configured on haproxy itself, haproxy cannot negotiate ssl, or block certain ciphers/ssl-versions in that process.. Any successful SSLv3 negotiation must be coming from the backend or perhaps the pfSense webgui, but surely not haproxy itself.
Are you sure both backend servers 192.168.153.1:443 and 192.168.152.1:443 are configured to block sslv3 ?
p.s. please put config files inside code block with the # icon :) saves some scrolling through the posts..
Regards,
PiBa-NL -
Hi PiBa,
Thank you very much. You got it ! My other webserver was not properly configured to deny SSLv3.
Once modified, it works fine.However, I do not understand why it has any impact when testing SSLv3 with sslscan on the URL of the other website that was properly configured to deny SSLv3. Would it be possible to let me know ?
Thank you again for your quick and efficient help. :)
Alex
PS : previous post modified to manage code with # icon :)
-
Hi Alex,
Probably the sslscan your using didn't send the sni extension, or for some reason its using a slightly different name than what you have configured in haproxy.. Ive sometimes seen that for example the port is included also when running on 443 , so the sni match would be done like "req.ssl_sni -i www.abc.com:443".
As for your sslscan sending sni extension, if you capture the traffic in wireshark and select the 'clienthello' packet. There should be a field ssl.handshake.extensions_server_name that has the sni servername in readable text, maybe its simply not sending it at all?
Regards,
PiBa-NL -
Hi PiBa,
Thank you. I followed your advice.
I did a Wireshark on client hello packets. Here is the result of what I observed :
- for protocols TLSv1 and TLSv1.2, I can see a "Server Name Indication extension" section with a field "Server Name" defined to the correct URL.
- for SSLv3 protocol, I do not see any entry in SSL section about SNI (see image attached)
Do you think it explains the behavior observed ? Maybe it explains why sslscan do not check the "right" webserver.
Thanks again PiBa.
Alex

-
Hi Alex,
It seems like openssl which is used by sslscan doesnt like to send sni when using SSLv3 (SSLv3 is not really defined to support the extension very well..). http://security.stackexchange.com/a/101424 has a little info about that.
So that indeed would explain why the request would not match the sni hostname acl, and the default backend was used instead.
I assume that it was indeed the default backend that was not configured to block SSLv3?Regards,
PiBa-NL -
Hi PiBa,
Thank you very much for this very clear explanation and the link provided.
You're right, I do confirm that it was the default backend that was still accepting SSLv3.Alex
-
Sorry to bring up an old thread, but there aren't many posts about securing HAProxy in pfsense and disabling tls ssl3/1.0/1.1. I just wanted to add a note how to fix this through the GUI in pfsense 21.02.2, which I didn't see anywhere.
The global setting mentioned above can be edited in the pfsense gui at
Services -> HAProxy ->Settings -> Global Advanced pass thruTo secure the ssl settings, go to https://ssl-config.mozilla.org/ and generate a HAProxy config, then add in to the Global Advanced pass thru settings. My settings looked like this
# intermediate configuration https://ssl-config.mozilla.org/ ssl-default-bind-ciphers ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384 ssl-default-bind-ciphersuites TLS_AES_128_GCM_SHA256:TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256 ssl-default-bind-options prefer-client-ciphers no-sslv3 no-tlsv10 no-tlsv11 no-tls-tickets ssl-default-server-ciphers ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384 ssl-default-server-ciphersuites TLS_AES_128_GCM_SHA256:TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256 ssl-default-server-options no-sslv3 no-tlsv10 no-tlsv11 no-tls-tickets -
I believe all you really need to do to disable ssl3 is this drop down box
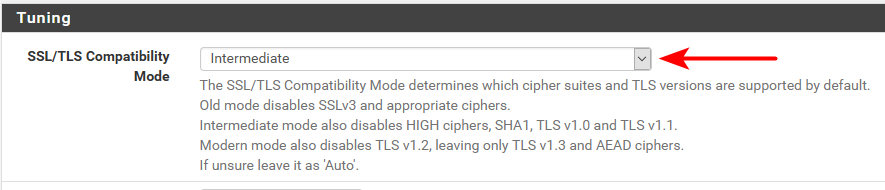
Nothing wrong with tweaking the settings how you want with the manual method. But if all your looking to do is disable the old stuff and leave 1.2 and or just even 1.3 You should be able to just use the drop down.
One thing will tell you is the testing site
https://www.ssllabs.com/ssltest/Will not give you an A+ if only have 1.3 enabled, atleast last time I checked which wasn't all that long ago - there is a thread about getting A+ rating somewhere around here I started.
That was driving me a bit nuts for awhile...
But yeah if your interested/concerned/worried about your settings the above link to testing will give you loads of info about what ciphers, etc. Do you have CAA set, do you have OSCP stapling, HSTS, etc. etc..
-
Where is that tuning setting? When I look in my HAProxy settings I don't have that.
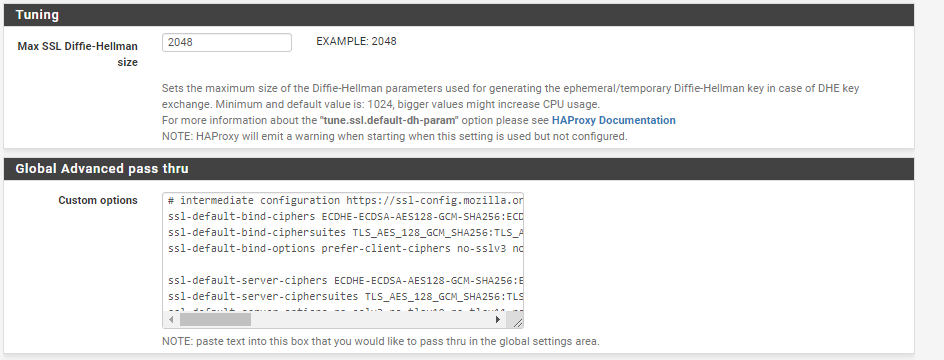
I know about SSL Labs, which is how I saw tls 1.0 and 1.1 were enabled by default (getting a B rating). With the changes I made it only gets a A, but with intermediate settings I used that was expected.
-
What version of haproxy are you using? I'm on haproxy-devel 0.62_3 package that is 2.2.6 of haproxy.
And its listed right there where you looking on mine.
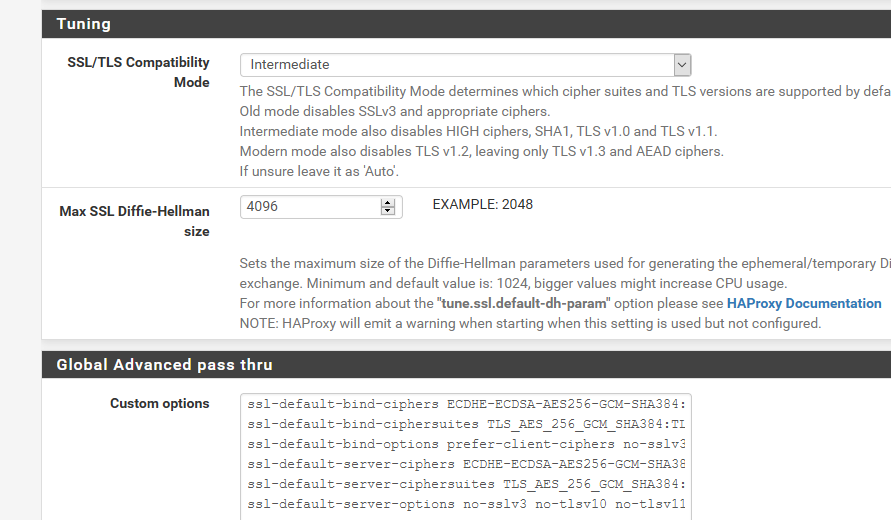
Little tweaking any you can get A+
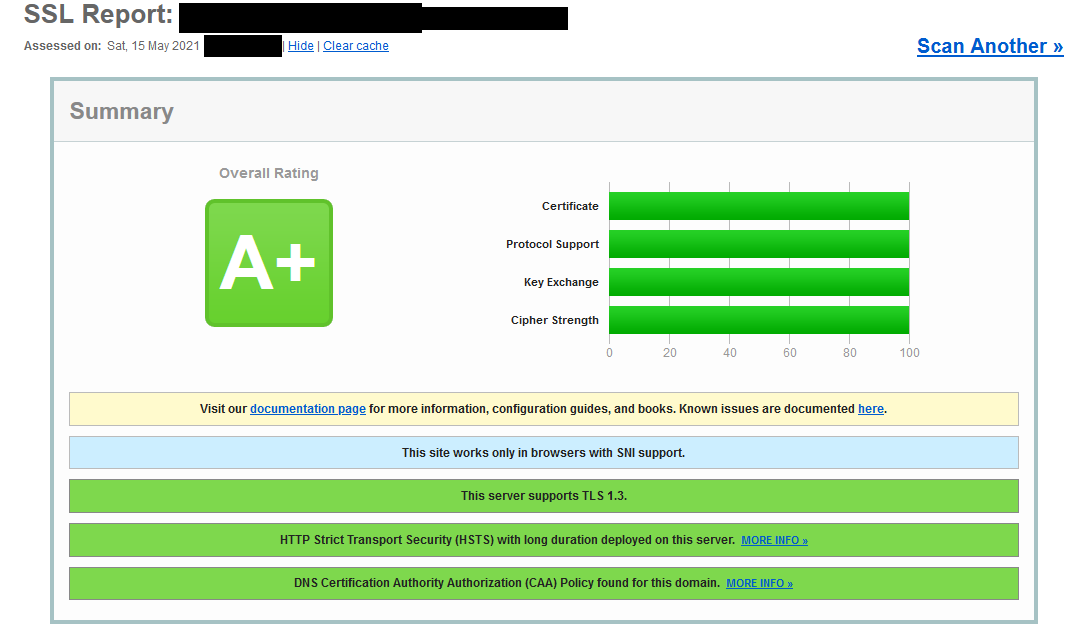
-
I am using the non-devel haproxy 0.61_1, so that is probably the difference. I'd imagine these changes in devel will eventually make it to the non-devel version?
It seems like I could tweak this further without upgrading the haproxy package to devel so I'm going to keep it on the stable release for now, but it is good to know it might be easier in the future. I looked all over today and kept getting back to this post.