VTI and Firewall rules
-
@toto-le-haricot you need to apply Patch ID cb0a23f29237d86fbc40259882bba2b5b9d419f5 for that
see https://docs.netgate.com/pfsense/en/latest/development/system-patches.html
-
@viktor_g
Thank you !
Sorry for the delay, I've been pretty busy during the last month.I've tested the patch on a test device with a dummy VTI, and here is the result:

And here is the output for the apply details/usr/bin/patch --directory=/ -t -p2 -i /var/patches/608faf68dfd81.patch --check --forward --ignore-whitespace Hmm... Looks like a unified diff to me... The text leading up to this was: -------------------------- |From cb0a23f29237d86fbc40259882bba2b5b9d419f5 Mon Sep 17 00:00:00 2001 |From: jim-p |Date: Wed, 10 Feb 2021 13:15:55 -0500 |Subject: [PATCH] Add option to set IPsec filtering mode. Implements #11395 | |User can choose between filtering enc (tunnel+VTI) or filtering on |assigned VTI interface tabs (VTI only, drops all tunnel mode traffic). |See https://redmine.pfsense.org/issues/11395 for details. |--- | src/etc/inc/filter.inc | 16 +++++++++---- | src/etc/inc/globals.inc | 30 ++++++++++++++++++++---- | src/etc/inc/system.inc | 9 ++++++- | src/usr/local/www/vpn_ipsec_settings.php | 26 ++++++++++++++++++++ | 4 files changed, 71 insertions(+), 10 deletions(-) | |diff --git a/src/etc/inc/filter.inc b/src/etc/inc/filter.inc |index aeb79c9c11a..e5cdf9196f6 100644 |--- a/src/etc/inc/filter.inc |+++ b/src/etc/inc/filter.inc -------------------------- Patching file etc/inc/filter.inc using Plan A... Hunk #1 succeeded at 95 (offset -2 lines). No such line 4697 in input file, ignoring Hunk #2 succeeded at 4547 (offset -159 lines). Hmm... The next patch looks like a unified diff to me... The text leading up to this was: -------------------------- |diff --git a/src/etc/inc/globals.inc b/src/etc/inc/globals.inc |index 33578cc30f7..f2cf76700f9 100644 |--- a/src/etc/inc/globals.inc |+++ b/src/etc/inc/globals.inc -------------------------- Patching file etc/inc/globals.inc using Plan A... Hunk #1 succeeded at 149 (offset -12 lines). No such line 310 in input file, ignoring Hunk #2 failed at 307. 1 out of 2 hunks failed while patching etc/inc/globals.inc Hmm... The next patch looks like a unified diff to me... The text leading up to this was: -------------------------- |diff --git a/src/etc/inc/system.inc b/src/etc/inc/system.inc |index 98d978a645e..82c7364dda8 100644 |--- a/src/etc/inc/system.inc |+++ b/src/etc/inc/system.inc -------------------------- Patching file etc/inc/system.inc using Plan A... Hunk #1 succeeded at 98 (offset -4 lines). Hmm... The next patch looks like a unified diff to me... The text leading up to this was: -------------------------- |diff --git a/src/usr/local/www/vpn_ipsec_settings.php b/src/usr/local/www/vpn_ipsec_settings.php |index 9458ae2430f..bd8e34c6ede 100644 |--- a/src/usr/local/www/vpn_ipsec_settings.php |+++ b/src/usr/local/www/vpn_ipsec_settings.php -------------------------- Patching file usr/local/www/vpn_ipsec_settings.php using Plan A... Hunk #1 succeeded at 33 (offset -2 lines). Hunk #2 failed at 47. Hunk #3 succeeded at 163 (offset -78 lines). Hunk #4 failed at 208. Hunk #5 succeeded at 358 (offset -23 lines). 2 out of 5 hunks failed while patching usr/local/www/vpn_ipsec_settings.php doneRegards,
-
@toto-le-haricot said in VTI and Firewall rules:
I've tested the patch on a test device with a dummy VTI, and here is the result:
You need to apply it on the latest stable release - 2.5.1
-
@viktor_g
Will 21.02 work too ? -
-
@viktor_g
The SG-3100 has been updated, but the patch still cannot be applied/usr/bin/patch --directory=/ -t -p2 -i /var/patches/608faf68dfd81.patch --check --forward --ignore-whitespace Hmm... Looks like a unified diff to me... The text leading up to this was: -------------------------- |From cb0a23f29237d86fbc40259882bba2b5b9d419f5 Mon Sep 17 00:00:00 2001 |From: jim-p |Date: Wed, 10 Feb 2021 13:15:55 -0500 |Subject: [PATCH] Add option to set IPsec filtering mode. Implements #11395 | |User can choose between filtering enc (tunnel+VTI) or filtering on |assigned VTI interface tabs (VTI only, drops all tunnel mode traffic). |See https://redmine.pfsense.org/issues/11395 for details. |--- | src/etc/inc/filter.inc | 16 +++++++++---- | src/etc/inc/globals.inc | 30 ++++++++++++++++++++---- | src/etc/inc/system.inc | 9 ++++++- | src/usr/local/www/vpn_ipsec_settings.php | 26 ++++++++++++++++++++ | 4 files changed, 71 insertions(+), 10 deletions(-) | |diff --git a/src/etc/inc/filter.inc b/src/etc/inc/filter.inc |index aeb79c9c11a..e5cdf9196f6 100644 |--- a/src/etc/inc/filter.inc |+++ b/src/etc/inc/filter.inc -------------------------- Patching file etc/inc/filter.inc using Plan A... Ignoring previously applied (or reversed) patch. Hunk #1 ignored at 97. Hunk #2 ignored at 4706. 2 out of 2 hunks ignored while patching etc/inc/filter.inc Hmm... The next patch looks like a unified diff to me... The text leading up to this was: -------------------------- |diff --git a/src/etc/inc/globals.inc b/src/etc/inc/globals.inc |index 33578cc30f7..f2cf76700f9 100644 |--- a/src/etc/inc/globals.inc |+++ b/src/etc/inc/globals.inc -------------------------- Patching file etc/inc/globals.inc using Plan A... Ignoring previously applied (or reversed) patch. Hunk #1 ignored at 161. Hunk #2 ignored at 319. 2 out of 2 hunks ignored while patching etc/inc/globals.inc Hmm... The next patch looks like a unified diff to me... The text leading up to this was: -------------------------- |diff --git a/src/etc/inc/system.inc b/src/etc/inc/system.inc |index 98d978a645e..82c7364dda8 100644 |--- a/src/etc/inc/system.inc |+++ b/src/etc/inc/system.inc -------------------------- Patching file etc/inc/system.inc using Plan A... Ignoring previously applied (or reversed) patch. Hunk #1 ignored at 102. 1 out of 1 hunks ignored while patching etc/inc/system.inc Hmm... The next patch looks like a unified diff to me... The text leading up to this was: -------------------------- |diff --git a/src/usr/local/www/vpn_ipsec_settings.php b/src/usr/local/www/vpn_ipsec_settings.php |index 9458ae2430f..bd8e34c6ede 100644 |--- a/src/usr/local/www/vpn_ipsec_settings.php |+++ b/src/usr/local/www/vpn_ipsec_settings.php -------------------------- Patching file usr/local/www/vpn_ipsec_settings.php using Plan A... Ignoring previously applied (or reversed) patch. Hunk #1 ignored at 35. Hunk #2 ignored at 49. Hunk #3 ignored at 241. Hunk #4 ignored at 286. Hunk #5 ignored at 381. 5 out of 5 hunks ignored while patching usr/local/www/vpn_ipsec_settings.php done -
@toto-le-haricot I can successfully apply this patch on my SG-3100 pfSense 21.02-p2:
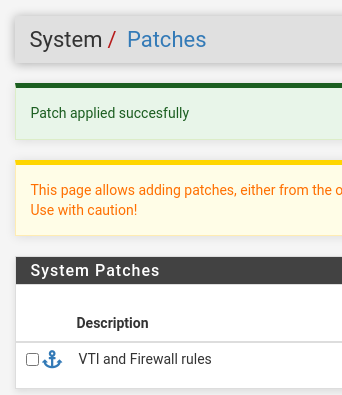
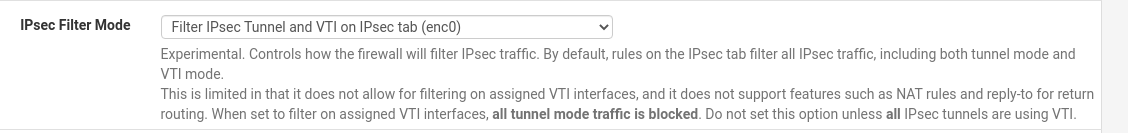
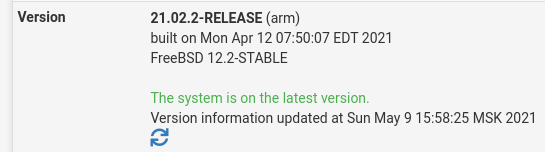
Try to reimage the appliance, maybe something wrong with your previous patches
-
Hello,
Sorry for the delay, I still have troubles applying the patch. What I've done:
- Reseting the SG-3100 to defaults: KO
- Re-image it with 21.02-p1, appliying with a default conf: KO
- Update to 21.02.2: KO
- Trying a brand new one updated from 2.4.5-p1 to 21.02: KO
- Re-image the new one with 21.02-p1 (MD5 OK): KO
What I have to try:
- Testing it with a brand new 21.02.2 image
- Test with different appliances we have: SG-1100, SG-5100, SG-7100
- Test with the CE edition (but I'm pretty sure I won't take this path as we heavily rely on multi-WAN)
Regards,
-
That feature will be in the 21.05 release due out very soon. You may as well wait a couple weeks for that rather than fighting the patch.
-
@jimp
Great ! I will wait then, thank you for reaching out to me ;)