WireGuard lives!
-
@vjizzle yes. There is open pull request to include it into the 2.6.0 ports repository once that happens it will show up.
Likely to be sometime next week.
-
Just to be clear on changes
If you are on 0.0.8 or 0.0.9. Here is list of major changes for 0.1.1
- unbound ACL creation for non assigned interfaces
- service daemonization, reliable startup shutdown eliminate zombie process/services.
- enables smooth upgrade of the kmod when the upstream kmod is updated. because stopping the service unloads the kernel module so it can be upgraded.
- redone status page with show/hide peers
- bug fixes / better validation for initial peer / tunnel setup.
- move away from wg-quick and dependency on bash. better response for enabling / disabling peers and tunnels.
If you are using for just private internet access and there aren't very many changes that affect you.
more importantly on the wiregurad-kmod side
- upgrading to wireguard-kmod-0.0.20210503.txz fixes a kernel panic that I had reported and this was fixed upstream.
@theonemcdonald please feel free to add anything if missed anything.
-
Installed it in Version 2.5.1
works great - thank you for yor work
regards
-
Upgrade to 0.1.1 worked great! Thanks.
But i'm encountering high errors out on the tun_wg interface:
WG_DSHOME Interface (opt3, tun_wg0) Status up IPv4 Address 192.168.166.1 Subnet mask IPv4 255.255.255.240 IPv6 Address fdac:ce55::1 Subnet mask IPv6 64 MTU 1420 In/out packets 2287708/3201934 (486.02 MiB/555.38 MiB) In/out packets (pass) 2287708/3201934 (486.02 MiB/555.38 MiB) In/out packets (block) 1444/0 (208 KiB/0 B) In/out errors 0/3512 Collisions 0i have no idea why and what could be the cause. Any idea or hint what could produce that errors?
-
Not really sure why that happens. I am running this with very few errors maybe 1 or 0. I will keep an eye on it. Just a thought maybe try adjusting the MTU depending on your WAN uplink.
-
@vajonam Its pretty strange. but i'm not using the wan for peers. So it shouldn't be related?
-
@dersch, sorry I just assumed it was over a WAN link. then I am out of ideas sorry.
-
Just upgraded to 2.6.0.a.20210524.0100-DEV:
Crash report details:
PHP Errors:
[24-May-2021 18:48:49 Europe/Rome] PHP Warning: flock() expects parameter 1 to be resource, null given in /usr/local/pkg/wireguard/wg_service.inc on line 324
[24-May-2021 18:48:49 Europe/Rome] PHP Warning: fclose() expects parameter 1 to be resource, null given in /usr/local/pkg/wireguard/wg_service.inc on line 327Installed pfSense v2.6.0-DEV from scratch and configured WG by hand (i.e. no import from old config.xml) after added pkg.
WG is properly working though.
-
@psp I caught this a few days ago. Fix will be in the next release. It is cosmetic.
-
Does this currently, or in future, work on official Netgate hardware eg. SG-5100?
-
@brians update to Pfsense version 21.05 RC and you will have access to the package. Unfortunately it's version 0.0.8 instead of the more current 0.1.1. Unsure why that is.
-
@gabacho4 just manually removed the older package versions and manually reinstalled and all is well. Not as convenient as having a package to select in the package manager, but easy enough still and nice to be on current.
-
@gabacho4 Thanks, I will just wait until official release. Was just curious because the different version numbers with PfSense + and CE.
Having said that, wonder if will support the ARM devices eg. SG3100. -
@brians yup it should support ARM devices, assuming NG will build the WireGuard Kmods for all architectures. the WG pfsense package (ui) really has no dependency on architecture.
-
Wow, I upgraded SG5100 to 21.05 last night, this morning I manually installed WireGuard 0.1.2.
Took me a few minutes of fiddling with my iPhone, and memories of how I setup before. There is a few differences in assigning interface etc. but it very simple and I had no problems except forgetting to add firewall rule on the interface which is probably very common LOL.Later will setup a 2nd SG5100 and do site to site test.
Let's hope this gets updated into official packages in GUI because its still at 0.0.8. I did notice package no longer shows up as available in GUI on my pfSense if I have installed manually, which is a good thing I suppose!
-
@brians said in WireGuard lives!:
except forgetting to add firewall rule on the interface which is probably very common LOL.
This might be a good argument for adding associated pass rule creation as a feature when creating a tunnel, similar to what is done for port forwarding
-
@theonemcdonald I ran into a similar issue and stronly support your thoughts. In my view a good model to follow is that set out for IPSec and openVPN particularly with regard to outbound NAT rules when setting up a server.
Ted Quade
-
@theonemcdonald
But is it possible to even make a rule before the interface is assigned? Don't you still have to go and select/assign it after making the tunnel?
-
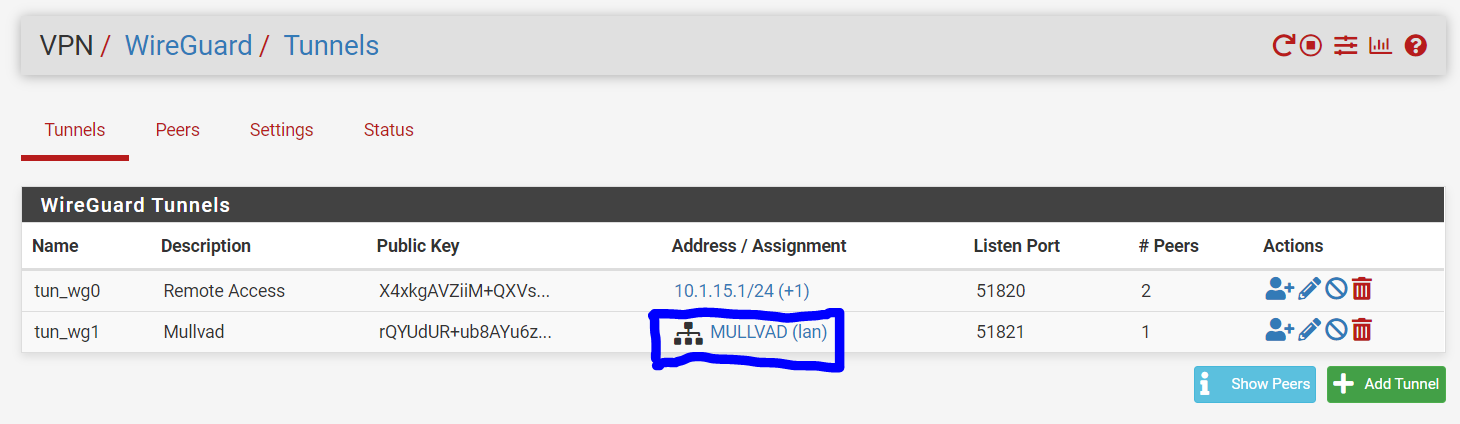
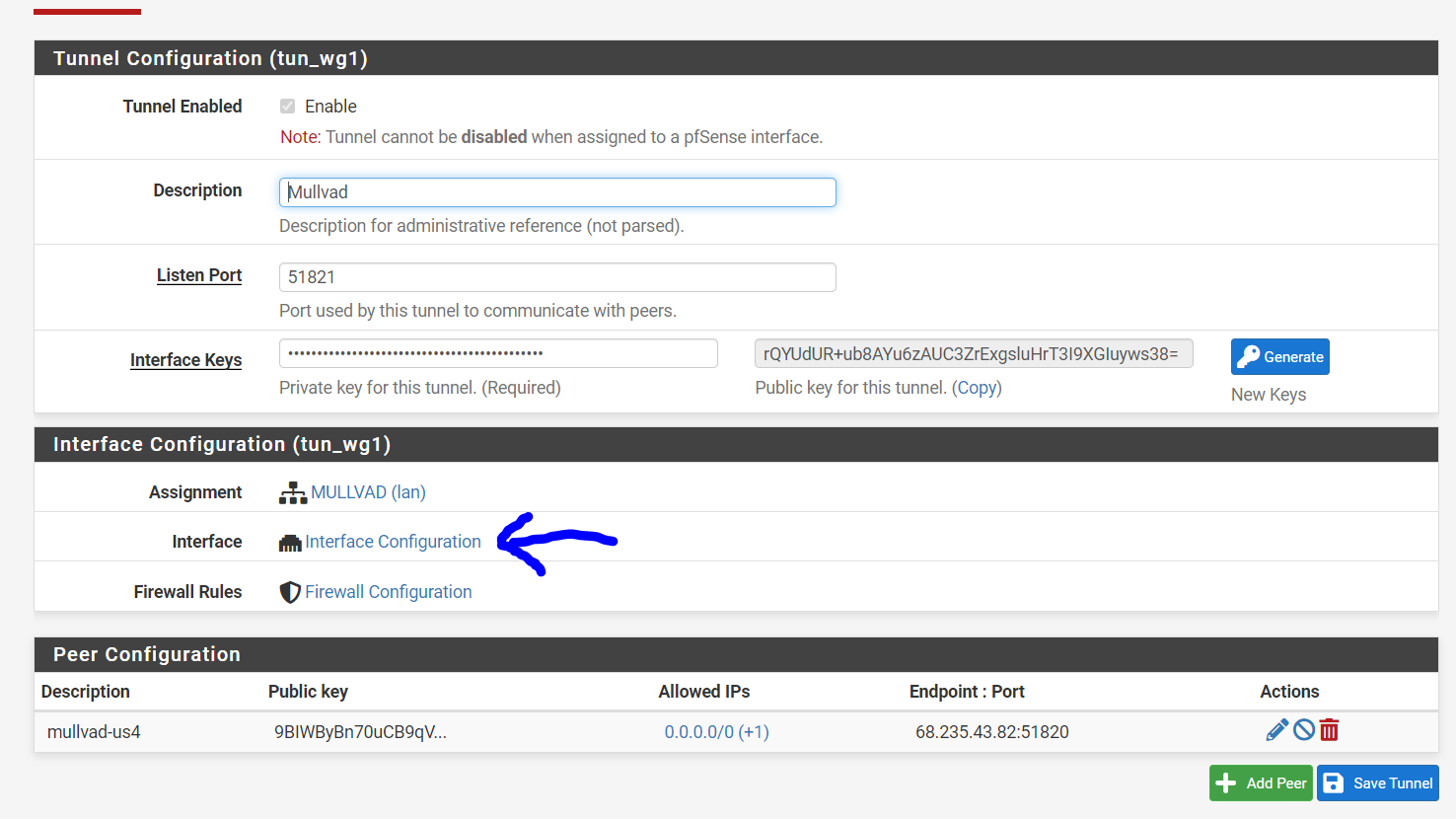
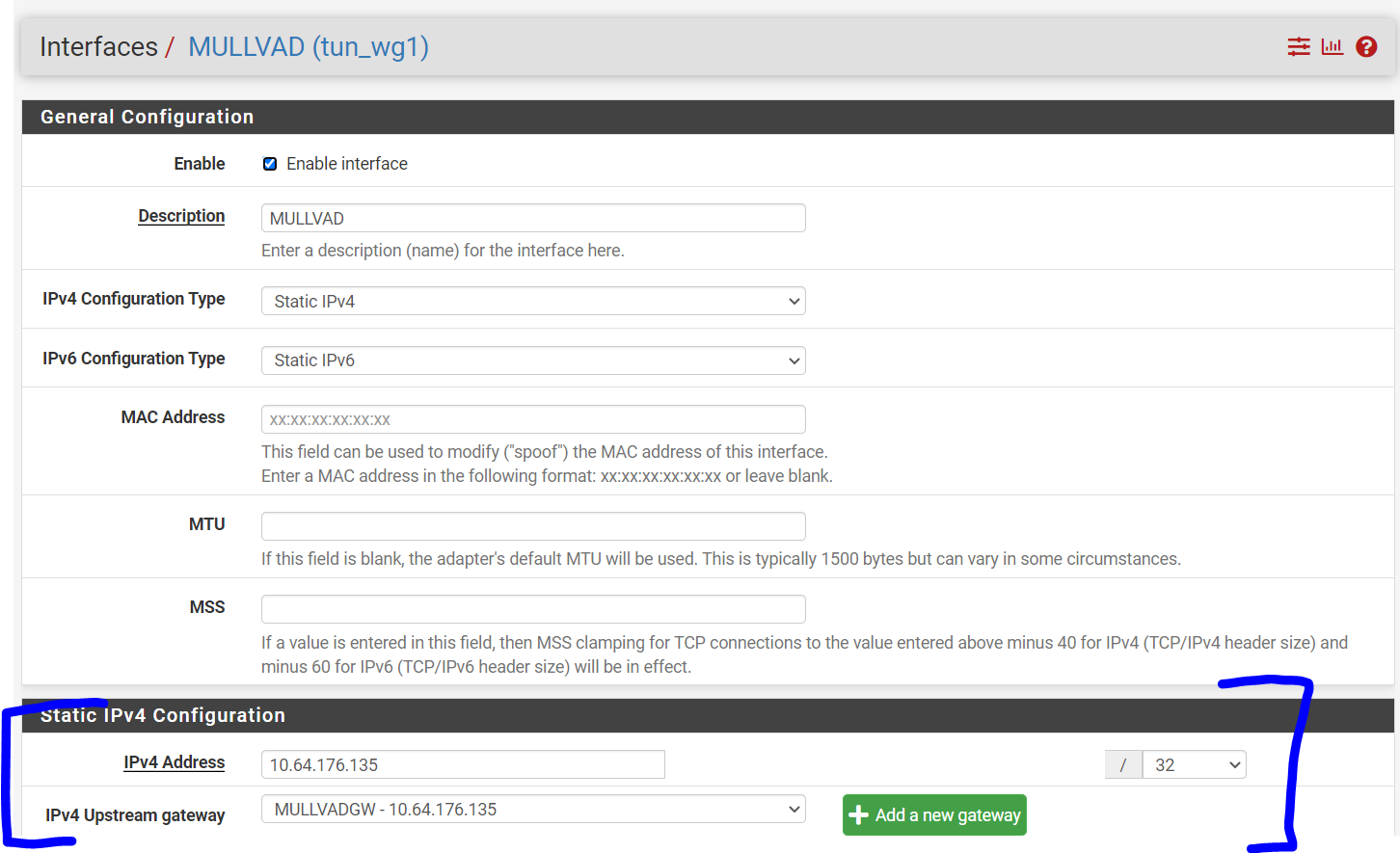
What is the purpose of Interface addresses?
When I assign to an interface I assign the IP address to the interface and the values entered here previously disappear and are not used. If I un-assign they re-appear.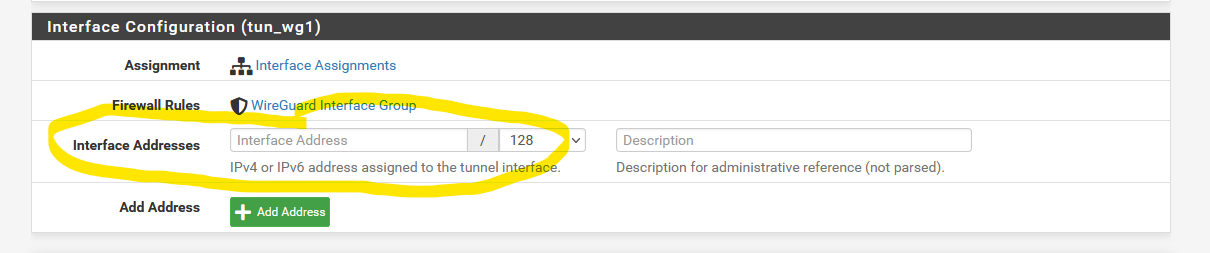
-
@brians said in WireGuard lives!:
What is the purpose of Interface addresses?
When I assign to an interface I assign the IP address to the interface and the values entered here previously disappear and are not used. If I un-assign they re-appear.This is for configuring WireGuard tunnels that are not assigned to a pfSense interface. Yea that is a bit confusing. But basically you can have two different types of WireGuard tunnels, which sort of depend on what you intend to do with them. It is possible to build WireGuard tunnels that aren't associated with a specific pfSense interface. These WireGuard tunnels are filtered using the "WireGuard" interface group. The addresses for unassigned tunnels are configured through the WireGuard UI. However, once you assign a WireGuard tunnel to a pfSense interface, pfSense takes over the address assignment, so the WireGaurd UI changes to reflect that...and instead you're left with a link to the native pfSense UI for configuring addresses:
We do this because we don't want to step on pfSense's toes when it comes to things that it should be handling.