site-to-site connected but can not ping after vpn in
-
@svpnv said in site-to-site connected but can not ping after vpn in:
Diagnostics->Ping works on both sites.
To which destination?
From which source?Change to source to LAN and try again.
@svpnv said in site-to-site connected but can not ping after vpn in:
if I vpn to server,
You are running an additional access server?
You have to provide some more details.
-
@viragomann I've also configured my site-to-site server as a vpn server.
I can connect to the other lan from pfsense on server and client site.
i.e, Diagnostics->Ping from server site pfsense to client network works, from client site pfsense to server lan also works.Status->Openvpn on server side:
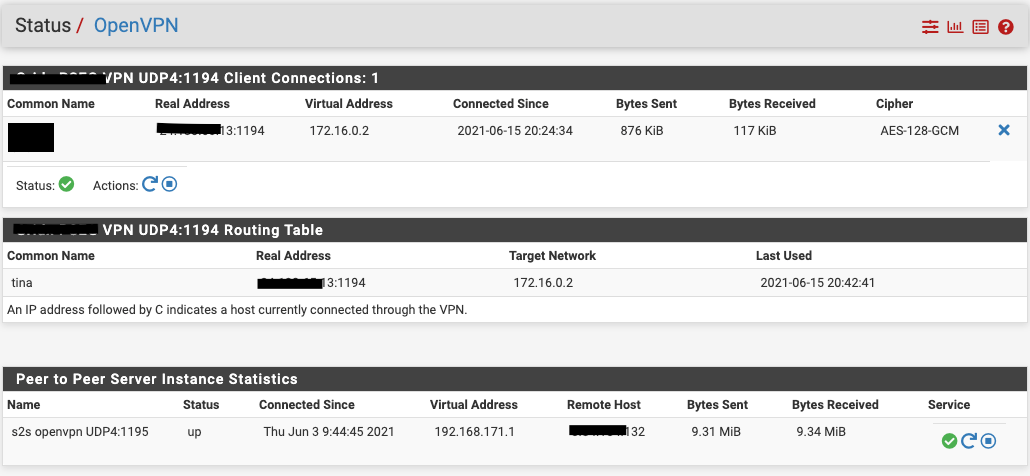
Status->Openvpn on client side:
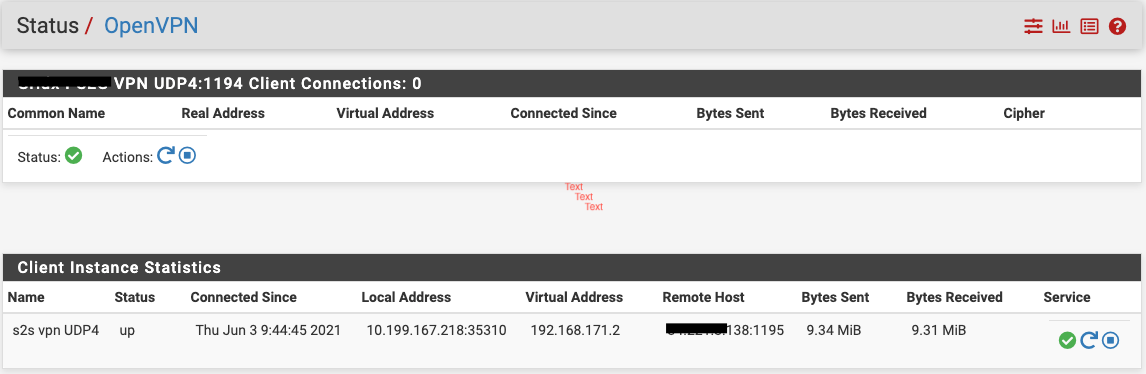
-
@svpnv
For correct routing you have to- add the s2s clients LAN network to the "Local Networks" in the access server settings to push the route to the connected clients.
- on the s2s client add the access server tunnel network to the "Remote networks" to direct the traffic to the server.
-
@viragomann I have those settings. The problem is the connected clients are not getting the route. Do I need to add pushing route in the Advanced Configuration->custom options?
-
@svpnv
No, if you have networks added in the "Local Networks" box the routes are pushed to the clients. However, the client OS can prohibit adding route by the OpenVPN client, maybe due to insufficient privileges.
But if this is the case, there should be some notes in the client log file and adding the routes manually to the clients config might be fail as well.
So best to check the client log first. -
@viragomann Client log does not show problem adding any route. It added route to my s2s server lan 10.100.0.0/16, but nothing shows in the log about the client lan 10.199.0.0/16, which is set in the server as "Remote Network".
s2s server:
Tunnel Network: 192.168.171.0/30
Local network(s): 10.100.0.0/16
Remote network(s): 10.199.0.0/16s2s client:
Tunnel Network: 192.168.171.0/30
Remote network(s): 10.100.0.0/16 -
@svpnv said in site-to-site connected but can not ping after vpn in:
s2s client:
Tunnel Network: 192.168.171.0/30
Remote network(s): 10.100.0.0/16I'm missing the access server tunnel network here.
-
@viragomann Do you mean vpn access server tunnel network? That's 172.16.0.0/24
-
@svpnv
Yes, that's what I already stated above. Two simple points for setting the routes correctly.
Since you didn't provide the details as requested, I didn't know the correct tunnel network range, so I was not able to specify it. -
@viragomann Thanks for helping. But I'm not sure what details you need. Can you make it clear? How to set the routes correctly?
-
@svpnv
https://forum.netgate.com/topic/164448/site-to-site-connected-but-can-not-ping-after-vpn-in/4Simply make these to points.
If that doesn't work provide the IPv4 routing tables from both pfSense and from the client device as well as the clients OpenVPN log, please.
Which vpn client are you using? -
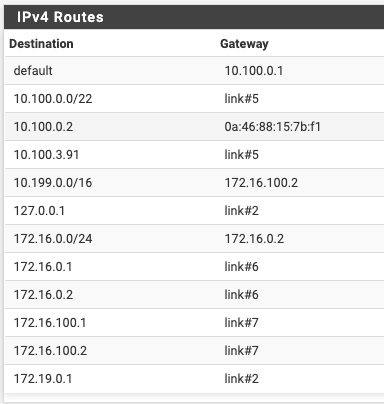
@viragomann I'm using Tunnelblick. I've already had all those in the config. Here is the routing tables:
Server:
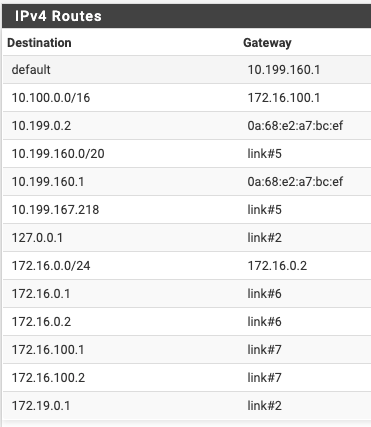
Client:
There is no problem to ping the remote and local networks from both server and client. The problem only exists when I try to ping the client network from my desktop. For your information, our whole infrastructure is on AWS. We're using pfSense Plus for AWS version 21.02.2
-
@svpnv
These screens absolutely miss-matches the OpenVPN status you've posted above!
The status show 192.168.171.1/2 as the client and servers virtual IP. None of these exists in the routing tables.
So what??Without knowing your true vpn configuration there is no way to give any help.
-
@viragomann I changed the Tunnel network from 192.168.171.0/30 to 172.16.100.0/30 yesterday after I posted the config. That's why the mismatch. It's the true configuration
-
Thanks to viragomann, the problem is solved. The problem is that the default gateway for devices in the client lan is not pfSense, we need to setup NAT mapping as a work around. Really appreciate the help @viragomann !